The following is a description of the trapping technique The correct ones are which women's multiple choices).
The server can set or read the information contained in the cookie This maintains state in the user's session with the server.
A5RUE
B. FALSE
The following is a description of FW's audit conduct. Which one is correct? (single selection).
What are the following descriptions of cybertrapping techniques that are wrong? (multiple selection).
Each element of the audit policy can be flexibly configured, which is convenient for users to classify, classify audit and response, so how many elements the audit strategy includes
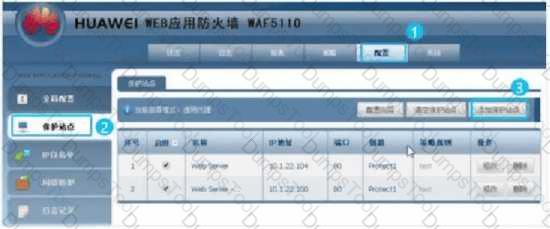
With the prevalence of e-commerce, online banking, e-government The business value of WEB servers is getting higher and higher, and the security threats faced by web servers are also increasing, and the defense against the web application layer has become an inevitable trend, WAF (WebApplication Firewall WEB APPLICATION FIREWALL) PRODUCTS BEGAN TO BECOME POPULAR. As shown in the figure The firewall uses the deployment mode of transparent proxy About the deployment mode of WAF using transparent proxy Which of the following options is described incorrectly.
Regarding ECA probe carrier entities, which of the following cannot be ECA probe carrier entities?
With the following description of the difference between stored XSS and reflected XSS, what are the correct items? (multiple selection).
Which of the following attacks can be detected by a point device. (Single selection)
Configure the source NAT policy for the campus network egress firewall to use the internal network users to access the external network, if you need to use security policies to block access to the external network The source IP address matched in the security policy is the private IP address of the user.
The following is a description of FW's DNS filtering feature What are the correct options? (multiple selection).
There are many firewall security policies in the data center network, and the administrator enables the policy backup acceleration function, and the source address matching conditions of the security policy are modified It can be effective immediately.
By default, the firewall authenticates traffic that passes through itself.
The following describes the configuration contents of the firewall file filtering feature Which one is wrong, (single selection).
Digital certificates can ensure the credibility of the public key of the communicating partner in the process of data transmission.
The following description of information security training Which items are correct? (multiple selection).
In the following description of the principles of network trapping defense, which are correct? (multiple selection).
The following suggestions for deploying heartbeats between firewalls with hot standby on both devices, which are correct?
PT (Advanced Persistent Threat) attacks are stealthy and persistent computer intrusion processes, usually orchestrated by certain personnel For specific goals.
A5RUE
B. FALSE
What is correct in the following description of the capabilities of cybertrapping techniques? (multiple selection).
In the WAF defense-in-depth system, which of the following security checks is used to protect against CC attacks? (single selection).
Which of the following options is part of the business security resiliency (multiple choices)?
Which of the following can be used as a Huawei IPS device to determine intrusion behavior? (single selection).
The following describes the authorization of the log license Which is correct? (single selection).
DNS Request Flood for DNS authoritative servers If TC source authentication is used The client device does not support using TCP to send DNS requests, how to verify the identity of the client? (single selection).
Take the following description of safety measures Which one is wrong? (single selection).
In the Anti-DDos system, the function of cleaning devices is to detect anomalous traffic in the network and escalate to the management centre (single selection).
One of the reasons why traditional passive defense does not protect against APT attacks is that traditional defense methods cannot correlate and analyze threats.
After you deploy HUAWEI CLOUD ANTI-DDoS Pro or Anti-DDoS Premium (DDoS Pro) or Anti-DDoS Pro, whether or not a DDoS attack occurs All access traffic is sent directly to the origin server IPo
XSS vulnerabilities are injection vulnerabilities formed by sending invalid database commands
Take the following about
1、Icx.exe-slave 192.168.122.111:4444 192.168.122.128:3389
2、lex -listen 3456 3789
What is the correct understanding? (Multiple selection)
The following describes the network scanning defense technology Which one is wrong? (single selection).
Which of the following options fall under the Security Manager requirements in Graded Protection 2.0? A Grading and filing
B. System administration
C. Audit management
D. Centralized control