During deployment of a long-distance point-to-point RF communication link, what is the distance between the receive and transmit antennas when impact of the Earth curvature should be considered?
On a layer 2 WLAN, in which modes can an AP discover the AC? (Multiple Choice)
When a large-scale enterprise deploys a WLAN Layer 3 network, you need to configure the Option 43 field on the Windows 2003 DHCP server to notify the AP of the IP address of the AC. The IP address of the AC is 10.23.100.1. Which of the following is required in the Option 43 field on the DHCP server?
As shown in the figure, the following is the load sharing mode of the dual-system hot backup solution?
In AP-based load balancing, what is the correct description of dynamic load balancing?
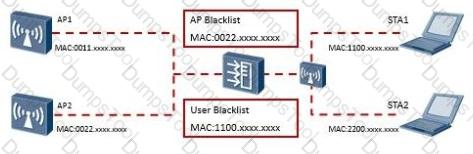
In public places where WLAN services are available, such as banks and airports, users can connect to the WLANs after associating with corresponding SSIDs. If a rogue AP is deployed and provides bogus SSIDs the same as or similar to authorized SSIDs, users may connect to the rogue AP, which brings security risks. Which of the following functions can solve this problem?
Which are the correct procedures for a Mesh node going online through an AC? (Multiple Choice)
After AP online configuration is complete on a Layer 3 WLAN, APs cannot go online. What are the possible causes? (Multiple Choice)
For small businesses, we generally recommend which feature of WIDS/WIPS is enabled to secure WLAN networks?
In a WLAN network, when the AP is in the monitoring mode, which packet does the AP use to determine the device type?
When priorities of the active and standby ACs are configured in dual-link HSB mode, a larger priority value indicates a higher priority.
The following is the correct command for creating a static load balancing group?
The following is a description of the AC roaming group. What is wrong with the statement?
An enterprise needs to upgrade the AC. Which of the following methods is relatively secure to upload upgrade files to the AC?
Which of the following methods is recommended to differentiate enterprise employees from guests in wireless admission control scenarios?
As shown in the figure, in a large enterprise WLAN network, the network administrator of the company recently discovered that the WLAN network traffic is abnormal, and the ping gateway has a delay or a large amount of packet loss. After excluding other possibilities, it is suspected that an illegal network attack has occurred. Which kind of illegal attack is the most likely?
Globally, the AC runs the () and () algorithms based on the neighbor relationship, interference, and load information to generate the new transmit power and working channel of the AP.
Which of the following APs and STAs cannot communicate with each other? (Multiple Choice)
The APs that enable the load balancing function do not need to be connected to the same AC, but the wireless terminal can scan the SSIDs of APs that are load balanced with each other.
As shown in the figure, in the Mesh networking, what is required to enable the STP spanning tree protocol?
In the Portal authentication, what parameters must be configured on the AC6005?
Which of the following statements is TRUE about the Agile Controller admission control model? (Multiple Choice)
An engineer sets synchronization type to user group-based synchronization, but no information is synchronized to the Agile Controller. The AD directory server works properly, and user and user group information is correct. What may cause the synchronization failure? (Multiple Choice)
When the engineer adjusted the directional antenna, it was found that when the antenna was placed away from the other antenna, the signal would drop and the signal would increase slightly. What caused the increase of this signal?
As shown in the figure, in the dual-link load balancing hot standby network, AP1 is a new online AP, and both ACs have access configuration. Which AC does AP1 choose to access?
As shown in the figure, in the dual-link cold backup load balancing network, as shown in the figure, the two SSIDs of the Huawei and the guest are configured on the AC1, and the SSID of the Huawei is configured on the AC2. The same SSID configuration is the same, and AP1 is online. AC1 and AP1 establish the primary line first. After the AP1 is disconnected from the AC1 link and the active/standby switchover is sent, what is the service status of the user accessed by the Guest SSID?
When a neighbor passively detects, what information does the legal AP need to collect and report to the AC?
When the STA uses the WPA2-802.1x security policy and supports fast roaming, the STA only needs to perform key negotiation, but does not need to pass 802.lx authentication again during roaming.
To enable STAs to roam between two APs, which of the following conditions must be met? (Multiple Choice)
Although the Fresnel zone exists in all RF communication scenarios, its impact is mainly considered in which of the following communications?
Which of the following processing methods are TRUE, to solve the packet congestion on the tunnel?
(Multiple Choice)
To quickly obtain information about the AC from which an STA goes online, the online status of al ACs in the roaming group and STAs must be saved on each AC.
Which of the following statements about Option 43 in the N+l backup networking are TRUE? (Multiple Choice)
In the load balancing mode, what is the correct way for each server to handle hot standby?
Rogue device prevention is a function that prevents access from rogue APs or STAs using a blacklist,
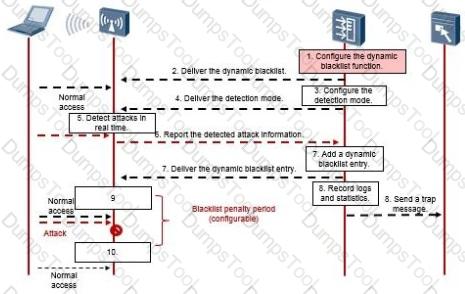
This figure shows the WIDS attack detection process. After the dynamic blacklist is delivered to an AP, how does the AP process different data traffic during the punish period?
Regarding the precautions for configuring the dual-system hot backup function, the following statement is wrong?
After channel switching without service interruption is configured on an AP, when the AP channel needs to be switched, the AP will notify associated STAs in advance and switch to the new channel with STAs at the same time without interrupting services.
When configuring the connection between the Agile Controller and WLAN, we need to configure a port number if we want to enable Portal, as shown in the following configuration. The default port number is 2000. What is the function of this port number? [AC] web-auth-server listening-port 2000
To improve reliability of the CAPWAP link between the AP and AC on a large WLAN, users can set a higher DSCP priority for CAPWAP management packets.
To remain the existing wired network architecture, an enterprise deploys the AC in bypass mode. Considering the large data traffic on the WLAN and needs for AC capacity expansion in the future, it is recommended that the tunnel forwarding mode be used to transmit WLAN services.
In the wireless access authentication, which of the following servers does the Agile Controller have?
An enterprise building has a large number of employees and they usually connect to the company WLAN in the lobby when arriving at the company. As they move to their work locations, their mobile terminals roam to the current network coverage areas. To ensure that each terminal obtains a fixed IP address, which of the following configurations is recommended?
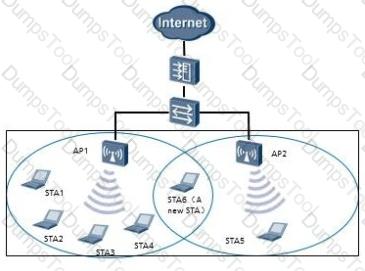
As shown in the figure, four STAs (STA1 to STA4) are associated with API and STA5 is associated with AP2. The start threshold for load balancing is set to 5. API and AP2 each allow a maximum of 10 STAs and the load difference threshold is set to 10%. When STA6 sends an association request to API for the first time, which of the following statements is TRUE?
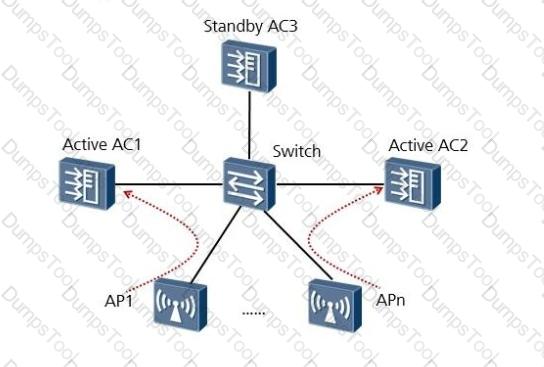
On the N+1 backup network, AC3 is configured with the global priority of 5, and AC1 and AC2 are configured with the global priority of 6. The AC1 priority is set to 3 on AC1 and the AP3 priority is set to 3 on AC1 and AC2. When AC3 is unloaded, which AC device will AP1, AP2, AP3, and AP4 access?
A large enterprise needs to deploy a WLAN network. The Huawei chassis switch (S77 / 97 / 127) is available on the current network. To reduce the space resources occupied by devices in the equipment room and facilitate the expansion of the WLAN network in the future, users can insert the switch in the frame switch. Insert the AC card into the WLAN network. Which of the following types of ACs can be inserted into the frame switch?
In the hot standby, the following statement about the HSB backup channel is wrong?
A company needs to construct a large WLAN. Since the company has a large number of employees, the service traffic is large. The company may need to expand the WLAN capacity in the future. Which of the following statements are TRUE? (Multiple Choice)
In the N+1 backup networking shown in the figure, AC3 is the standby AC of AC1 and AC2. The number of online APs on active AC1 is 1024 and the configured maximum number of online APs allowed on AC1 is 2048. The number of online APs on active AC2 is 512 and the configured maximum number of online APs allowed on AC2 is 512. What is the minimum number of APs allowed to connect to AC3 under normal circumstances, and what is the minimum number of online APs allowed to be configured on AC3?
Regarding the MP in the Mesh network, is the following description correct?
In the WLAN network with WIDS enabled, which of the following statements about device information is wrong?
In the Agile Controller admission control scenario, is the correct description of the role of the RADIUS server/client?
When the WLAN network supports inter-AC roaming, multiple ACs establish a full connection through the inter-AC tunnel. If the user of the Layer 3 roaming to other ACs can still receive broadcast packets from the original subnet and simply broadcast the broadcast packets to other ACs through the roaming tunnel, a broadcast loop may be formed.
On a WLAN network, the AP group name is ap-group and the WIDS template is wids. Now you need to enable the WIDS device counter-function and counter the counterfeit SSID=huawei AP. As shown in the figure, the following configuration is correct?
Regarding the Agile Controller admission model, what is the correct description below?
What is the correct description of load balancing between dual frequencies?
After CAC based on channel usage is configured to control user access on an AP, if the current channel usage exceeds the configured threshold, the AP will reject access requests of new STAs and force STAs to log out until the channel usage is lower than the threshold.
Which of the following statements about the three backup modes are TRUE? (Multiple Choice)
From the roaming process, which of the following processes does roaming need to go through?
As shown in the figure, different companies on adjacent floors of an office building use multiple SSIDs. If a company enables WIDS rogue device countermeasure, APs of other companies will be affected. Which of the following functions can solve this problem?
The following is a description of the wrong description of the chain network in the Mesh network?
In the indoor environment, signal reflection, refraction, diffraction, and scattering of walls and other obstacles are main factors affecting the link quality. The Fresnel zone is also an important factor.
When the user uses the WPA2-802.1x security policy and the STA supports the fast roaming technology, the user does not need to complete the 802.1x authentication process during the roaming process.
As shown in the figure, for the partial RF tuning configuration process, regarding the configuration process of RF tuning, what is the correct sorting?