Refer to the exhibits,
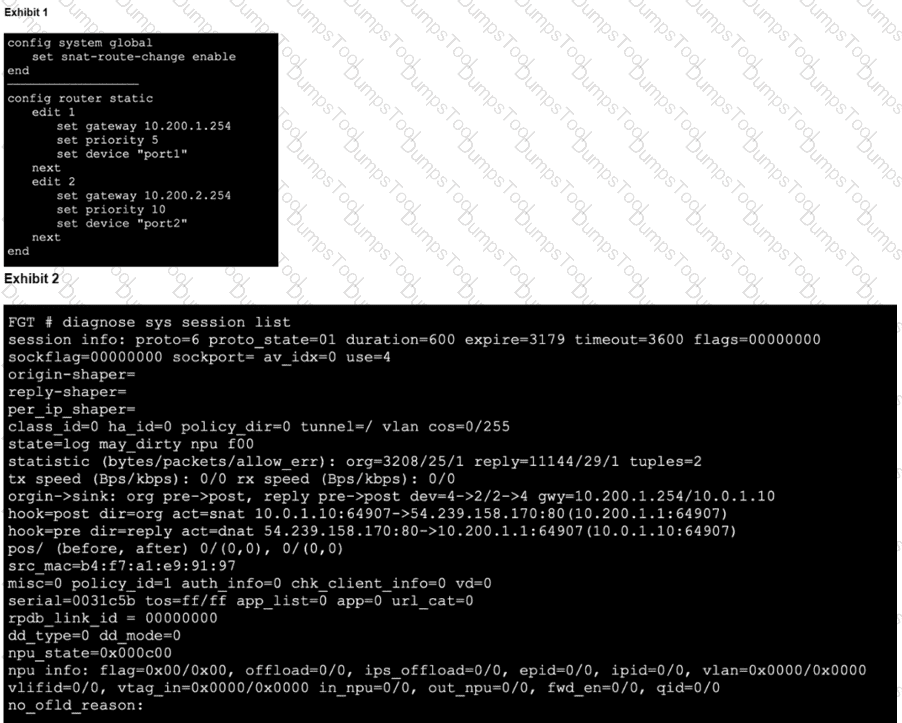
which show the configuration on FortiGate and partial session information for internet traffic from a user on the internal network. If the priority on route ID 2 were changed from 10 to 0, what would happen to traffic matching that user session? (Choose one answer)
Exhibit.
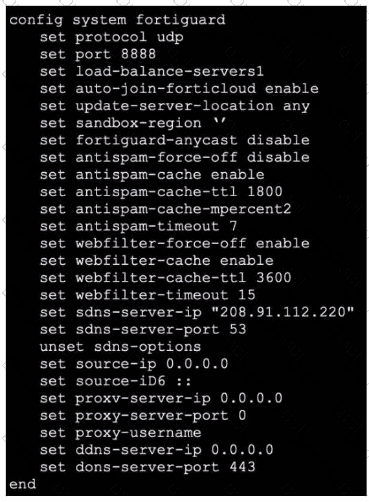
Refer to the exhibit, which shows a FortiGate configuration.
An administrator is troubleshooting a web filter issue on FortiGate. The administrator has configured a web filter profile and applied it to a policy; however the web filter is not inspecting any traffic that is passing through the policy.
What must the administrator do to fix the issue?
Exhibit.
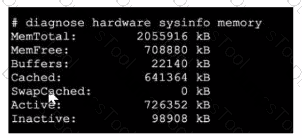
Refer to the exhibit, which shows a partial output of diagnose hardware aysinfo memory.
Which two statements about the output are true? (Choose two.)
Refer to the exhibit, which shows the output of a debug command.
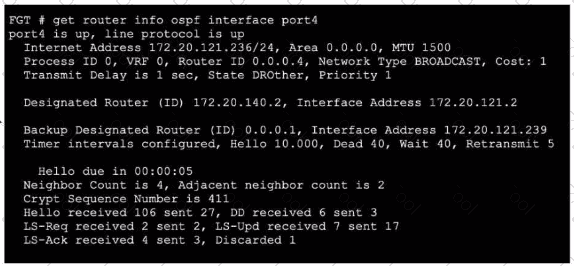
Which two statements about the output are true? (Choose two.)
Which three common FortiGate-to-collector-agent connectivity issues can you identify using the FSSO real-time debug? (Choose three.)
Refer to the exhibit.
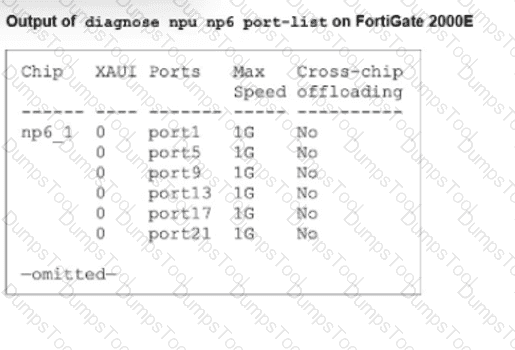
A partial output of diagnose npu up6 port-list on FortiGate 2000E is shown.
An administrator is unable to analyze traffic flowing between port1 and port17 using the diagnose sniffer command.
Which two commands allow the administrator to view the traffic? (Choose two.)
A)
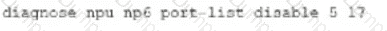
B)
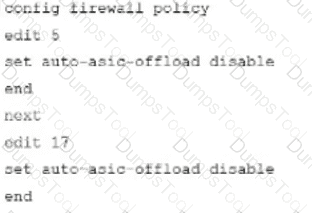
C)
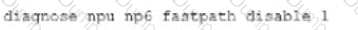
D)

Refer to the exhibit, which shows the partial output of FortiOS kernel slabs.
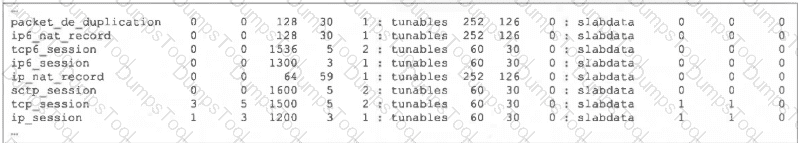
Which statement is true?
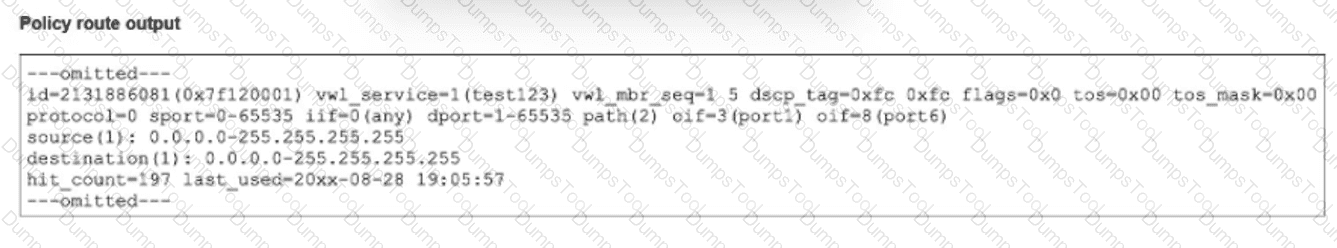
The output of a policy route table entry is shown.
Which type of policy route does the output show?
Refer to the exhibit.
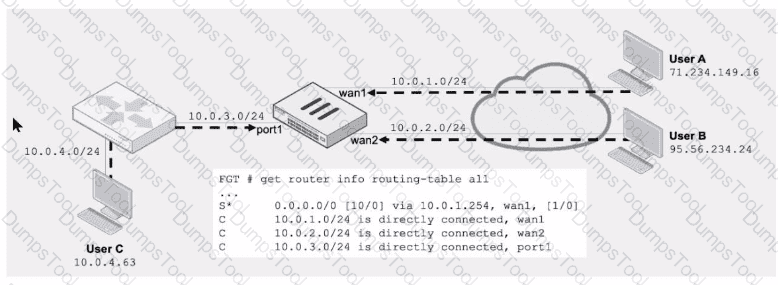
Assuming a default configuration, which three statements are true? (Choose three.)
Refer to the exhibit.
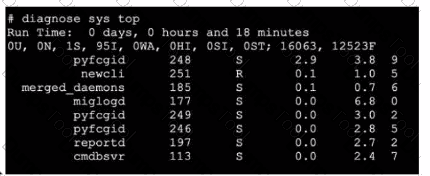
Which three pieces of information does the diagnose sys top command provide? (Choose three.)
Refer to the exhibit, which shows a partial output of the fssod daemon real-time debug command.

What two conclusions can you draw from the output? (Choose two.)
Consider the scenario where the server name indication (SNI) does not match either the common name (CN) or any of the subject alternative names (SAN) in the server certificate.
Which action will FortiGate take when using the default settings for SSL certificate inspection?
Refer to the exhibit, which shows a truncated output of a real-time LDAP debug.
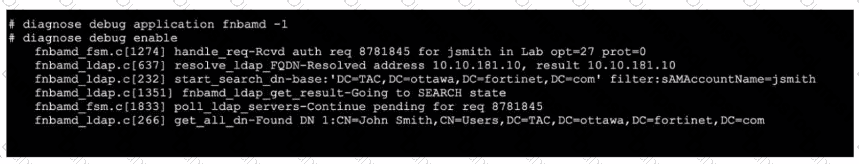
What two conclusions can you draw from the output? (Choose two.)
Which three common FortiGate-to-collector-agent connectivity issues can you identify using the FSSO real-time debug? (Choose three.)
While troubleshooting a FortiGate web filter issue, users report that they cannot access any websites, even though those sites are not explicitly blocked by any web filter profiles that are applied to firewall policies.
What are the three most likely reasons for this behavior? (Choose three answers)
Refer to the exhibit.
Partial output of diagnose sys session stat command is shown.
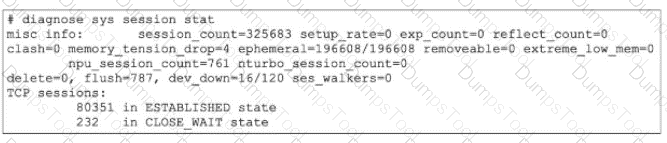
An administrator has noticed unusual behavior from FortiGate. It appears that sessions are randomly removed. Which two reasons could explain this? (Choose two.)
Refer to the exhibit.
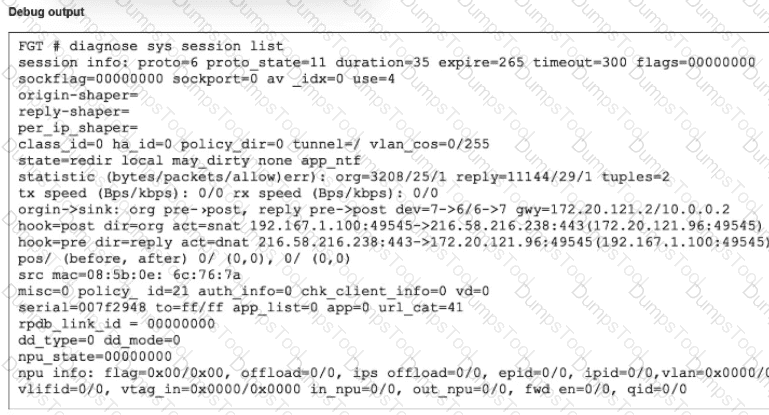
Which Iwo statements about FortiGate behavior relating to this session are correct? (Choose two.)
Which Iwo actions does FortiGate take after an administrator enables the auxiliary session selling? (Choose two.)
When FortiGate enters conserve mode because of memory pressure, which action can FortiGate perform to preserve memory?
Refer to the exhibit, which shows a partial output of a real-time LDAP debug.
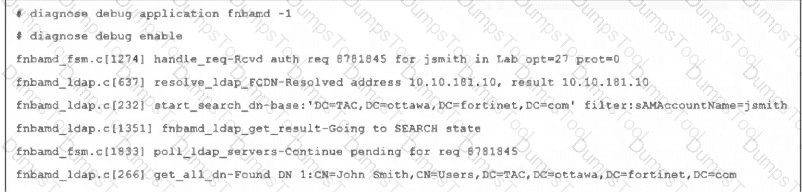
What two conclusions can you draw from the output? (Choose two.)
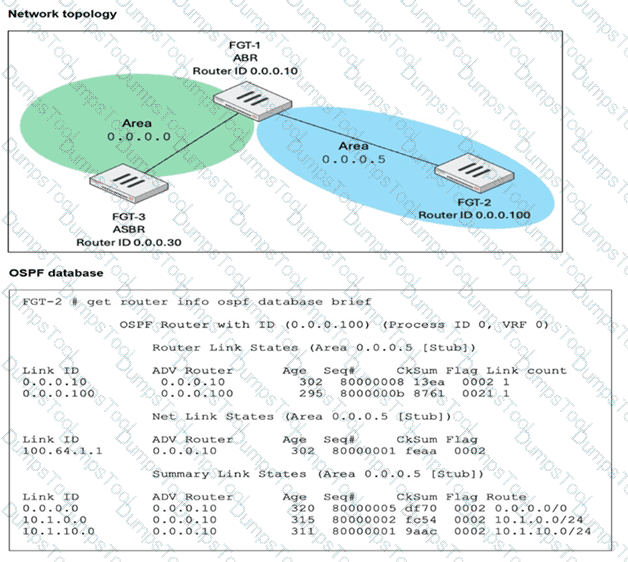
Refer to the exhibit, which a network topology and a partial routing table.
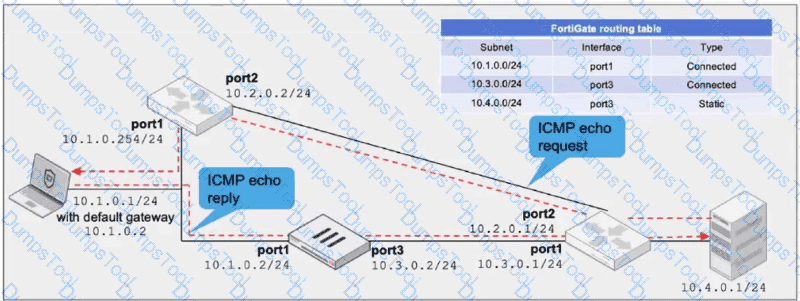
FortiGate has already been configured with a firewall policy that allows all ICMP traffic to flow from port1 to port3.
Which changes must the administrator perform to ensure the server at 10.4.0.1/24 receives the echo reply from the laptop at 10.1.0.1/24?
Exhibit.
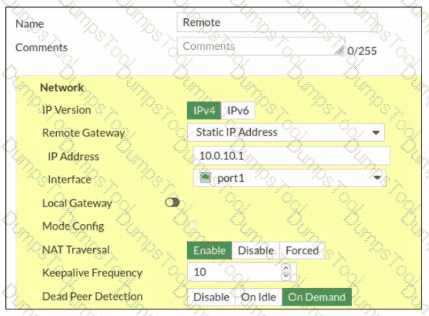
Refer to the exhibit, which contains a screenshot of some phase 1 settings.
The VPN is not up. To diagnose the issue, the administrator enters the following CLI commands on an SSH session on FortiGate:
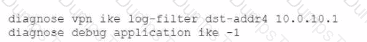
However, the IKE real-time debug does not show any output. Why?
Which two statements are true regarding heartbeat messages sent from an FSSO collector agent to FortiGate? (Choose two.)
Refer to the exhibit, which shows the output of a policy route table entry.
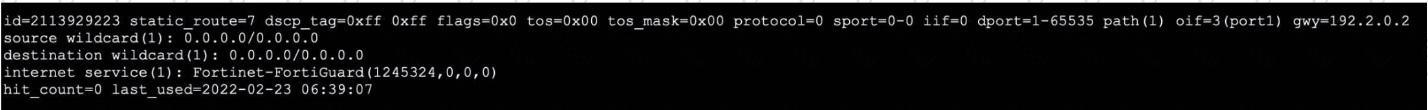
Which type of policy route does the output show?
Refer to the exhibit, which shows the partial output of command diagnose debug rating.

In this exhibit, which FDS server will the FortiGate algorithm choose?