Which types of algorithm does a web application firewall use for zero-day DDoS protection?
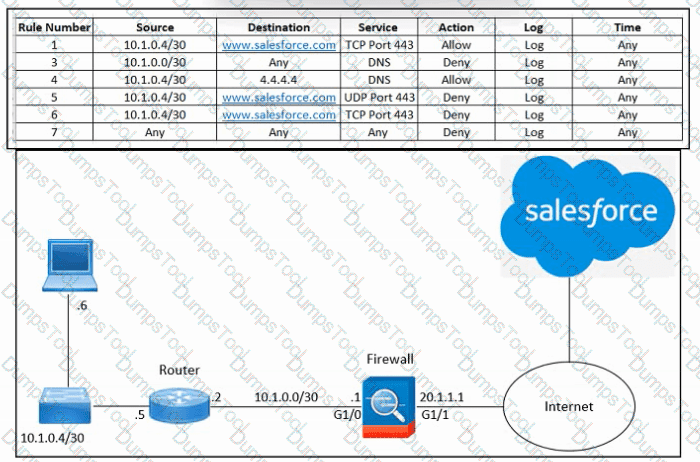
Refer to the exhibit. An engineer must configure the Cisco ASA firewall to allow the client with IP address 10.1.0.6 to access the Salesforce login page at https://www.salesforce.com. The indicated configuration was applied to the firewall and public DNS 4.4.4.4 is used for name resolution; however, the client still cannot access the URL. What should be done to meet the requirements?
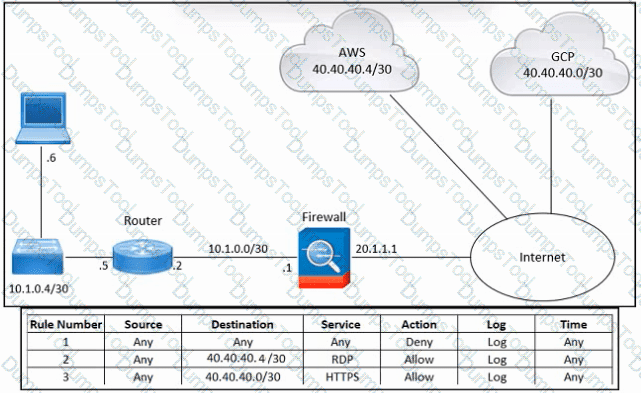
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?

Refer to the exhibit. An engineer must configure a global allow list in Cisco Umbrella for the cisco.com domain. All other domains must be blocked. After creating a new policy and adding the cisco.com domain, the engineer attempts to access a site outside of cisco.com and is successful. Which additional Security Settings action must be taken to meet the requirement?
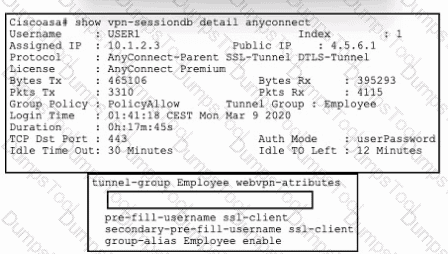
Refer to the exhibit. An engineer must implement a remote access VPN solution that provides user and device verification. The company uses Active Directory for user authentication and ID certificates for device identity. Users are currently able to connect using only a valid username and password, even if their computer is missing the required certificate.
Which command from the Cisco ASA tunnel-group completes the requirement of verifying device identity in addition to user identity?
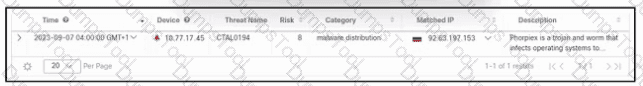
Refer to the exhibit. A security engineer deployed Cisco Secure XDR, and during testing, the log entry shows a security incident. Which action must the engineer take first?
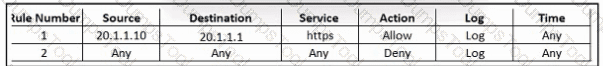
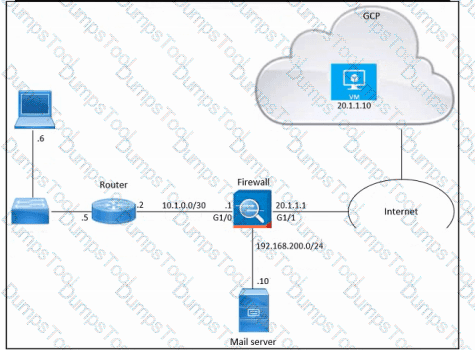
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
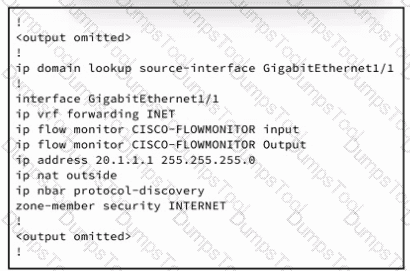
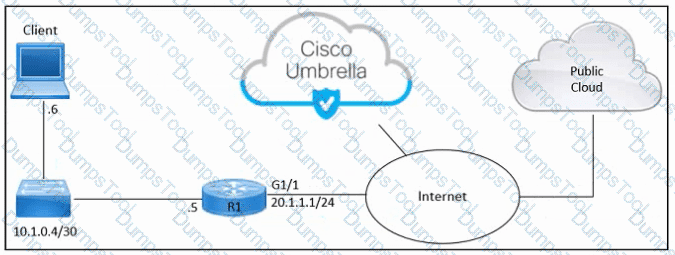
Refer to the exhibit. An engineer must connect an on-premises network to the public cloud using Cisco Umbrella as a Cloud Access Security Broker. The indicated configuration was applied to router R1; however, connectivity to Umbrella fails with this error: %OPENDNS-3-DNS_RES_FAILURE. Which action must be taken on R1 to enable the connection?
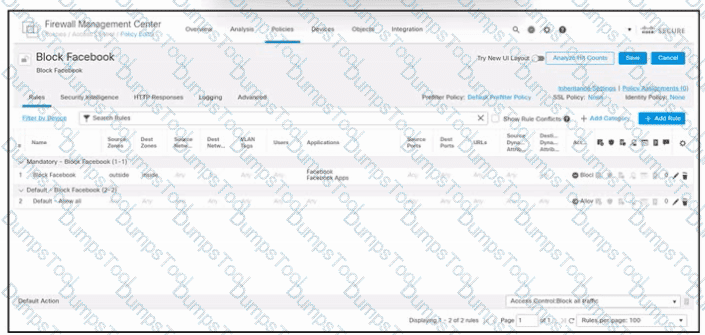
Refer to the exhibit. An engineer must block internal users from accessing Facebook and Facebook Apps. All other access must be allowed. The indicated policy was created in Cisco Secure Firewall Management Center and deployed to the internet edge firewall; however, users still can access Facebook. Which two actions must be taken to meet the requirement? (Choose two.)
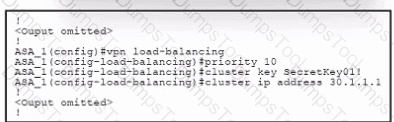
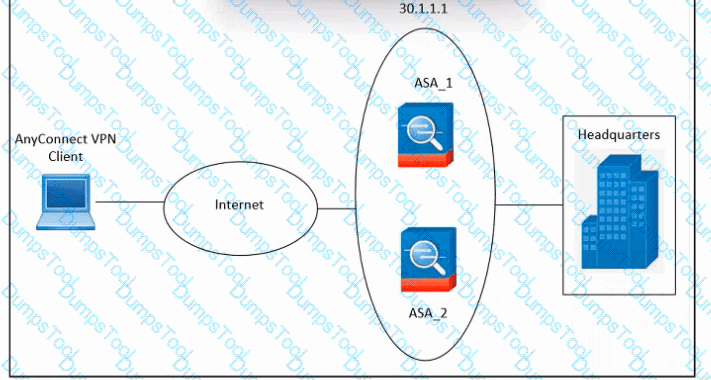
Refer to the exhibit. An engineer must configure VPN load balancing across two Cisco ASA. The indicated configuration was applied to each firewall; however, the load-balancing encryption scheme fails to work. Which two commands must be run on each firewall to meet the requirements? (Choose two.)
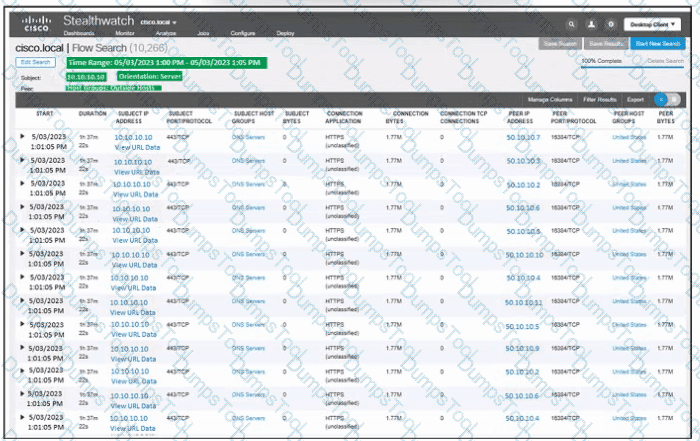
Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?
According to the MITRE ATT&CK framework, which approach should be used to mitigate exploitation risks?