Refer to the exhibit.
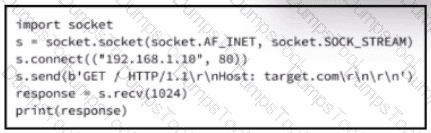
A cybersecurity analyst is presented with the snippet of code used by the threat actor and left behind during the latest incident and is asked to determine its type based on its structure and functionality. What is the type of code being examined?
Refer to the exhibit.
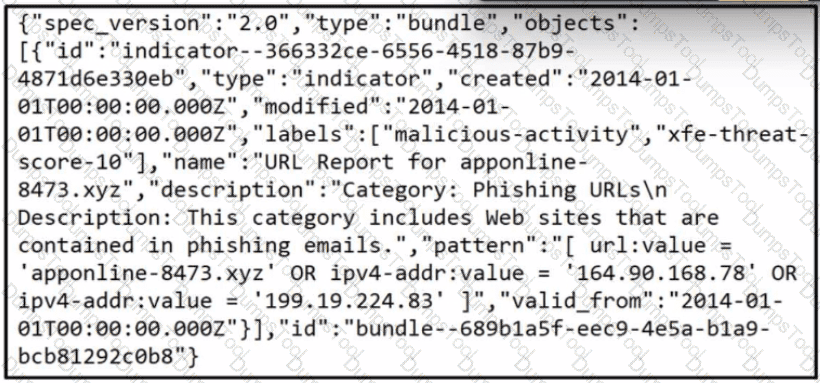
Which two actions should be taken as a result of this information? (Choose two.)
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
A malware outbreak revealed that a firewall was misconfigured, allowing external access to the SharePoint server. What should the security team do next?
An engineer received a report of a suspicious email from an employee. The employee had already opened the attachment, which was an empty Word document. The engineer cannot identify any clear signs of compromise but while reviewing running processes, observes that PowerShell.exe was spawned by cmd.exe with a grandparent winword.exe process. What is the recommended action the engineer should take?
A threat actor has successfully attacked an organization and gained access to confidential files on a laptop. What plan should the organization initiate to contain the attack and prevent it from spreading to other network devices?
Refer to the exhibit.
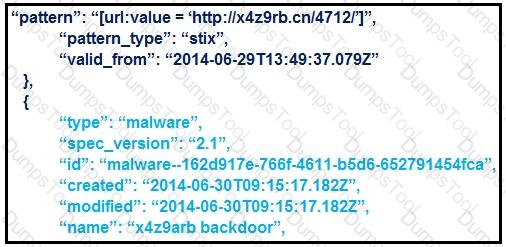
What is the IOC threat and URL in this STIX JSON snippet?
Refer to the exhibit.
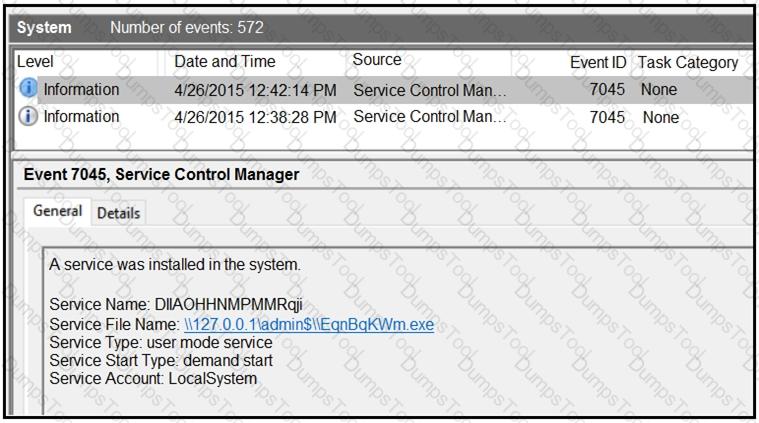
An HR department submitted a ticket to the IT helpdesk indicating slow performance on an internal share server. The helpdesk engineer checked the server with a real-time monitoring tool and did not notice anything suspicious. After checking the event logs, the engineer noticed an event that occurred 48 hours prior. Which two indicators of compromise should be determined from this information? (Choose two.)
Snort detects traffic that is targeting vulnerabilities in files that belong to software in the Microsoft Office suite. On a SIEM tool, the SOC analyst sees an alert from Cisco FMC. Cisco FMC is implemented with Snort IDs. Which alert message is shown?
A security team needs to prevent a remote code execution vulnerability. The vulnerability can be exploited only by sending '${ string in the HTTP request. WAF rule is blocking '${', but system engineers detect that attackers are executing commands on the host anyway. Which action should the security team recommend?
Refer to the exhibit.
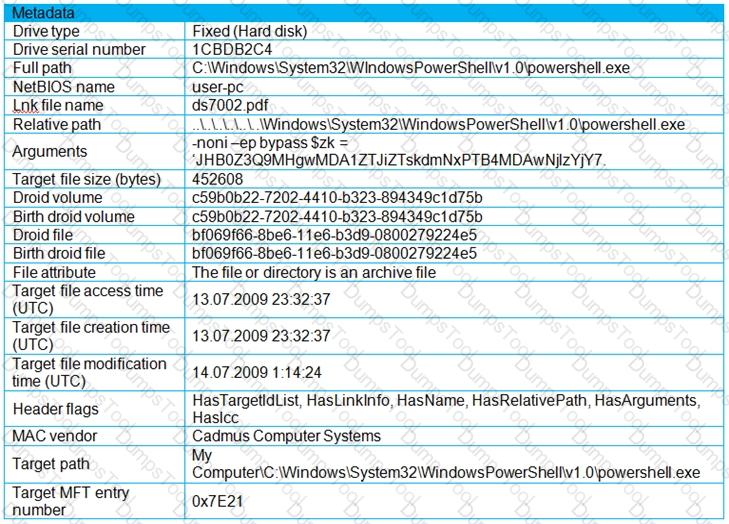
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?
Refer to the exhibit.

A security analyst is reviewing alerts from the SIEM system that was just implemented and notices a possible indication of an attack because the SSHD system just went live and there should be nobody using it. Which action should the analyst take to respond to the alert?
A security team receives reports of multiple files causing suspicious activity on users’ workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
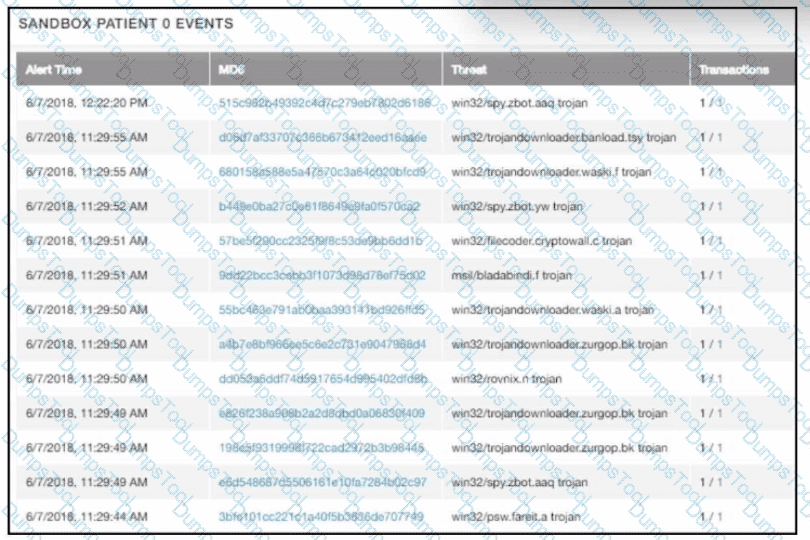
multiple machines behave abnormally. A sandbox analysis reveals malware. What must the administrator determine next?
A security team is notified from a Cisco ESA solution that an employee received an advertising email with an attached .pdf extension file. The employee opened the attachment, which appeared to be an empty document. The security analyst cannot identify clear signs of compromise but reviews running processes and determines that PowerShell.exe was spawned by CMD.exe with a grandparent AcroRd32.exe process. Which two actions should be taken to resolve this issue? (Choose two.)
An organization experienced a ransomware attack that resulted in the successful infection of their workstations within their network. As part of the incident response process, the organization's cybersecurity team must prepare a comprehensive root cause analysis report. This report aims to identify the primary factor or factors responsible for the successful ransomware attack and to formulate effective strategies to prevent similar incidents in the future. In this context, what should the cybersecurity engineer emphasize in the root cause analysis report to demonstrate the underlying cause of the incident?
What is a concern for gathering forensics evidence in public cloud environments?
A cybersecurity analyst is analyzing a complex set of threat intelligence data from internal and external sources. Among the data, they discover a series of indicators, including patterns of unusual network traffic, a sudden increase in failed login attempts, and multiple instances of suspicious file access on the company's internal servers. Additionally, an external threat feed highlights that threat actors are actively targeting organizations in the same industry using ransomware. Which action should the analyst recommend?
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
A cybersecurity analyst detects fileless malware activity on secure endpoints. What should be done next?
Which issue is associated with gathering evidence from virtualized environments provided by major cloud vendors?
An engineer is analyzing a ticket for an unexpected server shutdown and discovers that the web-server ran out of useable memory and crashed.
Which data is needed for further investigation?
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload. Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
An engineer is analyzing a DoS attack and notices that the perpetrator used a different IP address to hide their system IP address and avoid detection. Which anti-forensics technique did the perpetrator use?
A cybersecurity analyst is examining a complex dataset of threat intelligence information from various sources. Among the data, they notice multiple instances of domain name resolution requests to suspicious domains known for hosting C2 servers. Simultaneously, the intrusion detection system logs indicate a series of network anomalies, including unusual port scans and attempts to exploit known vulnerabilities. The internal logs also reveal a sudden increase in outbound network traffic from a specific internal host to an external IP address located in a high-risk region. Which action should be prioritized by the organization?
A company had a recent data leak incident. A security engineer investigating the incident discovered that a malicious link was accessed by multiple employees. Further investigation revealed targeted phishing attack attempts on macOS systems, which led to backdoor installations and data compromise. Which two security solutions should a security engineer recommend to mitigate similar attacks in the future? (Choose two.)