CEH-001 Question Includes: Single Choice Questions: 804, Multiple Choice Questions: 74,
Cyber Criminals have long employed the tactic of masking their true identity. In IP spoofing, an attacker gains unauthorized access to a computer or a network by making it appear that a malicious message has come from a trusted machine, by "spoofing" the IP address of that machine.
How would you detect IP spoofing?
Maintaining a secure Web server requires constant effort, resources, and vigilance from an organization. Securely administering a Web server on a daily basis is an essential aspect of Web server security.
Maintaining the security of a Web server will usually involve the following steps:
1. Configuring, protecting, and analyzing log files
2. Backing up critical information frequently
3. Maintaining a protected authoritative copy of the organization's Web content
4. Establishing and following procedures for recovering from compromise
5. Testing and applying patches in a timely manner
6. Testing security periodically.
In which step would you engage a forensic investigator?
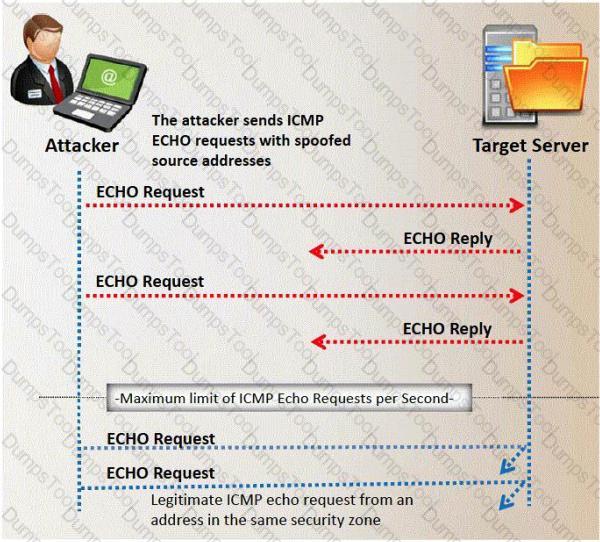
Which of the following statement correctly defines ICMP Flood Attack? (Select 2 answers)
A common technique for luring e-mail users into opening virus-launching attachments is to send messages that would appear to be relevant or important to many of their potential recipients. One way of accomplishing this feat is to make the virus-carrying messages appear to come from some type of business entity retailing sites, UPS, FEDEX, CITIBANK or a major provider of a common service.
Here is a fraudulent e-mail claiming to be from FedEx regarding a package that could not be delivered. This mail asks the receiver to open an attachment in order to obtain the FEDEX tracking number for picking up the package. The attachment contained in this type of e-mail activates a virus.

Vendors send e-mails like this to their customers advising them not to open any files attached with the mail, as they do not include attachments.
Fraudulent e-mail and legit e-mail that arrives in your inbox contain the fedex.com as the sender of the mail.
How do you ensure if the e-mail is authentic and sent from fedex.com?
What is the problem with this ASP script (login.asp)?

Customers Passed
GAQM CEH-001
Average Score In Real
Exam At Testing Centre
Questions came word by
word from this dump
DumpsTool Practice Questions provide you with the ultimate pathway to achieve your targeted GAQM Exam CEH-001 IT certification. The innovative questions with their interactive and to the point content make your learning of the syllabus far easier than you could ever imagine.
DumpsTool Practice Questions are information-packed and prove to be the best supportive study material for all exam candidates. They have been designed especially keeping in view your actual exam requirements. Hence they prove to be the best individual support and guidance to ace exam in first go!
GAQM Certified Ethical Hacker CEH CEH-001 PDF file of Practice Questions is easily downloadable on all devices and systems. This you can continue your studies as per your convenience and preferred schedule. Where as testing engine can be downloaded and install to any windows based machine.
DumpsTool Practice Questions ensure your exam success with 100% money back guarantee. There virtually no possibility of losing GAQM Certified Ethical Hacker CEH CEH-001 Exam, if you grasp the information contained in the questions.
DumpsTool professional guidance is always available to its worthy clients on all issues related to exam and DumpsTool products. Feel free to contact us at your own preferred time. Your queries will be responded with prompt response.
DumpsTool tires its level best to entertain its clients with the most affordable products. They are never a burden on your budget. The prices are far less than the vendor tutorials, online coaching and study material. With their lower price, the advantage of DumpsTool CEH-001 Certified Ethical Hacker (CEH) Practice Questions is enormous and unmatched!
DumpsTool products focus each and every aspect of the CEH-001 certification exam. You’ll find them absolutely relevant to your needs.
DumpsTool’s products are absolutely exam-oriented. They contain CEH-001 study material that is Q&As based and comprises only the information that can be asked in actual exam. The information is abridged and up to the task, devoid of all irrelevant and unnecessary detail. This outstanding content is easy to learn and memorize.
DumpsTool offers a variety of products to its clients to cater to their individual needs. DumpsTool Study Guides, CEH-001 Exam Dumps, Practice Questions answers in pdf and Testing Engine are the products that have been created by the best industry professionals.
The money back guarantee is the best proof of our most relevant and rewarding products. DumpsTool’s claim is the 100% success of its clients. If they don’t succeed, they can take back their money.
DumpsTool CEH-001 Testing Engine delivers you practice tests that have been made to introduce you to the real exam format. Taking these tests also helps you to revise the syllabus and maximize your success prospects.
Yes. DumpsTool’s concentration is to provide you with the state of the art products at affordable prices. Round the year, special packages and discounted prices are also introduced.