During the implementation of SSL Forward Proxy decryption, an administrator imports the company's Enterprise Root CA and Intermediate CA certificates onto the firewall. The company's Root and Intermediate CA certificates are also distributed to trusted devices using Group Policy and GlobalProtect. Additional device certificates and/or Subordinate certificates requiring an Enterprise CA chain of trust are signed by the company's Intermediate CA.
Which method should the administrator use when creating Forward Trust and Forward Untrust certificates on the firewall for use with decryption?
An engineer is configuring a firewall with three interfaces:
• MGT connects to a switch with internet access.
• Ethernet1/1 connects to an edge router.
• Ethernet1/2 connects to a visualization network.
The engineer needs to configure dynamic updates to use a dataplane interface for internet traffic. What should be configured in Setup > Services > Service Route Configuration to allow this traffic?
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed.
What is one way the administrator can meet this requirement?
An administrator needs to evaluate a recent policy change that was committed and pushed to a firewall device group. How should the administrator identify the configuration changes?
A company has recently migrated their branch office's PA-220S to a centralized Panorama. This Panorama manages a number of PA-7000 Series and PA-5200 Series devices All device group and template configuration is managed solely within Panorama
They notice that commit times have drastically increased for the PA-220S after the migration
What can they do to reduce commit times?
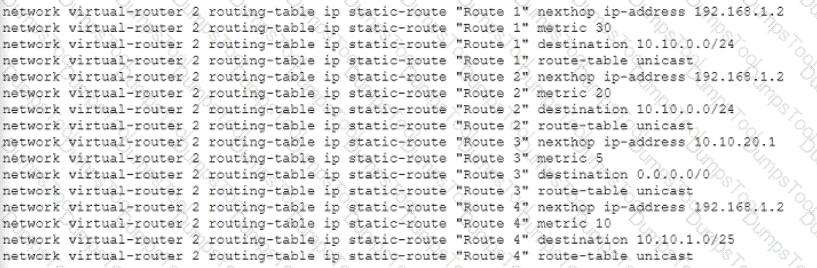
Given the following configuration, which route is used for destination 10 10 0 4?
What happens, by default, when the GlobalProtect app fails to establish an IPSec tunnel to the GlobalProtect gateway?
A company needs to preconfigure firewalls to be sent to remote sites with the least amount of reconfiguration. Once deployed, each firewall must establish secure tunnels back to multiple regional data centers to include the future regional data centers.
Which VPN configuration would adapt to changes when deployed to the future site?
An administrator needs to assign a specific DNS server to an existing template variable. Where would the administrator go to edit a template variable at the device level?
Which tool can gather information about the application patterns when defining a signature for a custom application?
A standalone firewall with local objects and policies needs to be migrated into Panorama. What procedure should you use so Panorama is fully managing the firewall?
What does the User-ID agent use to find login and logout events in syslog messages?
An administrator wants to add User-ID information for their Citrix MetaFrame Presentation Server (MPS) users.
Which option should the administrator use?
Which sessions does Packet Buffer Protection apply to when used on ingress zones to protect against single-session DoS attacks?
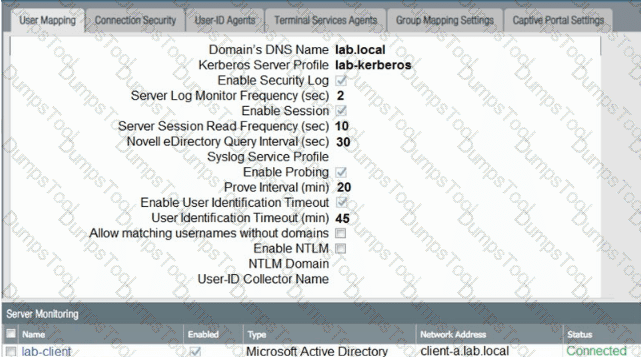
Based on the graphic which statement accurately describes the output shown in the Server Monitoring panel?
A firewall engineer creates a new App-ID report under Monitor > Reports > Application Reports > New Applications to monitor new applications on the network and better assess any Security policy updates the engineer might want to make.
How does the firewall identify the New App-ID characteristic?
A firewall engineer at a company is researching the Device Telemetry feature of PAN-OS. Which two aspects of the feature require further action for the company to remain compliant with local laws regarding privacy and data storage? (Choose two.)
An administrator has been tasked with configuring decryption policies,
Which decryption best practice should they consider?
The UDP-4501 protocol-port is to between which two GlobalProtect components?
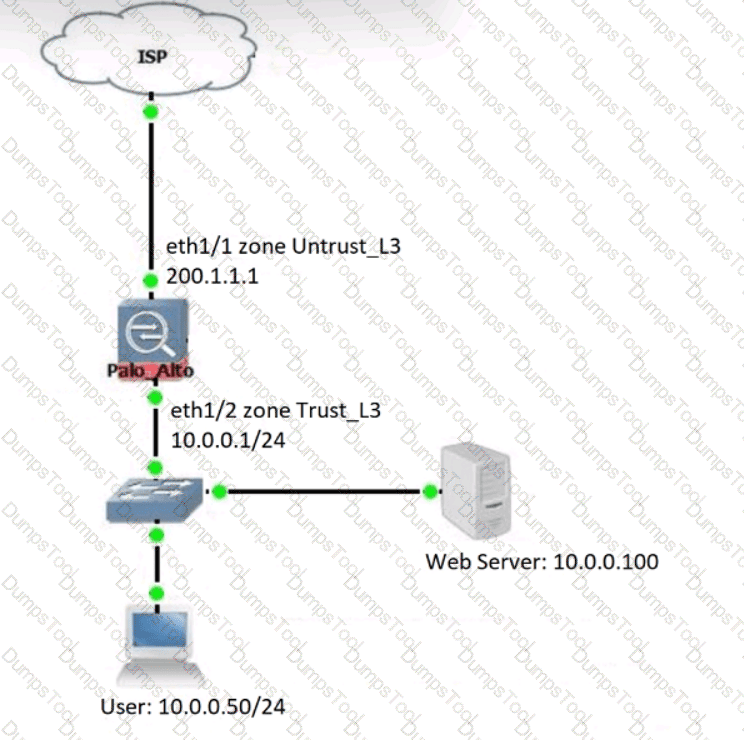
An engineer configures a destination NAT policy to allow inbound access to an internal server in the DMZ. The NAT policy is configured with the following values:
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
Refer to Exhibit:
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
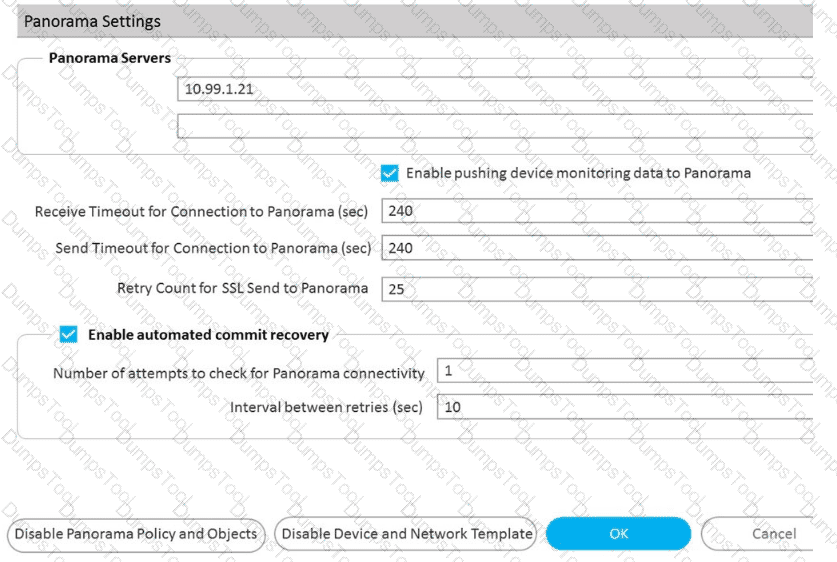
A)
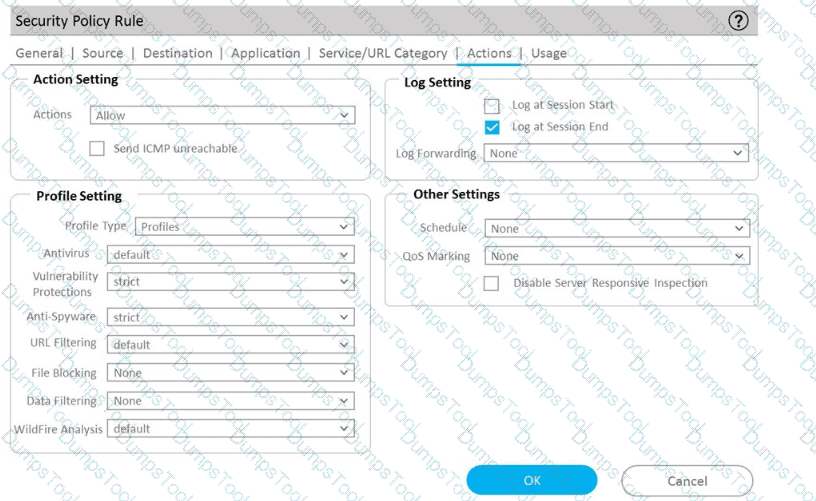
B)
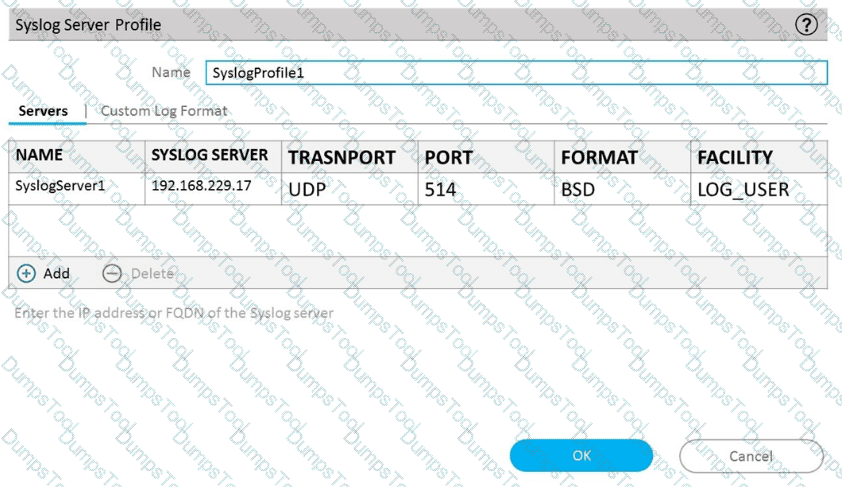
C)
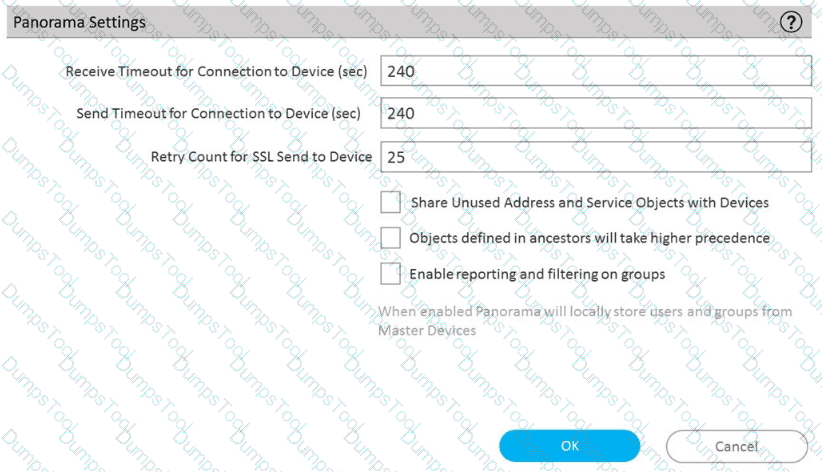
D)
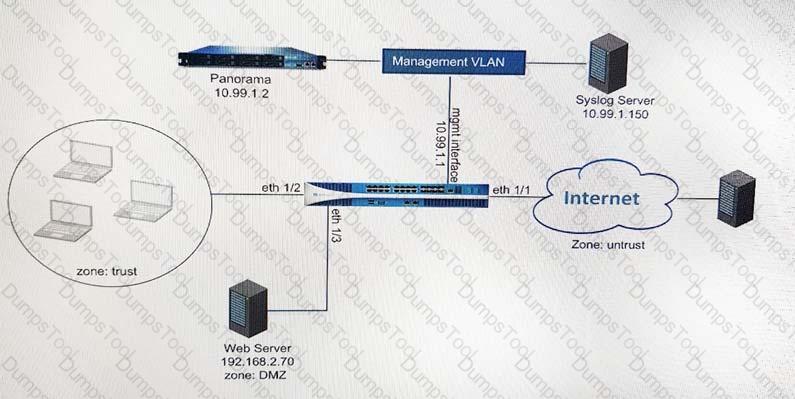
An enterprise Information Security team has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a recent phishing campaign against the organization has prompted Information Security to look for more controls that can secure access to critical assets. For users that need to access these systems. Information Security wants to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA.
What should the enterprise do to use PAN-OS MFA?
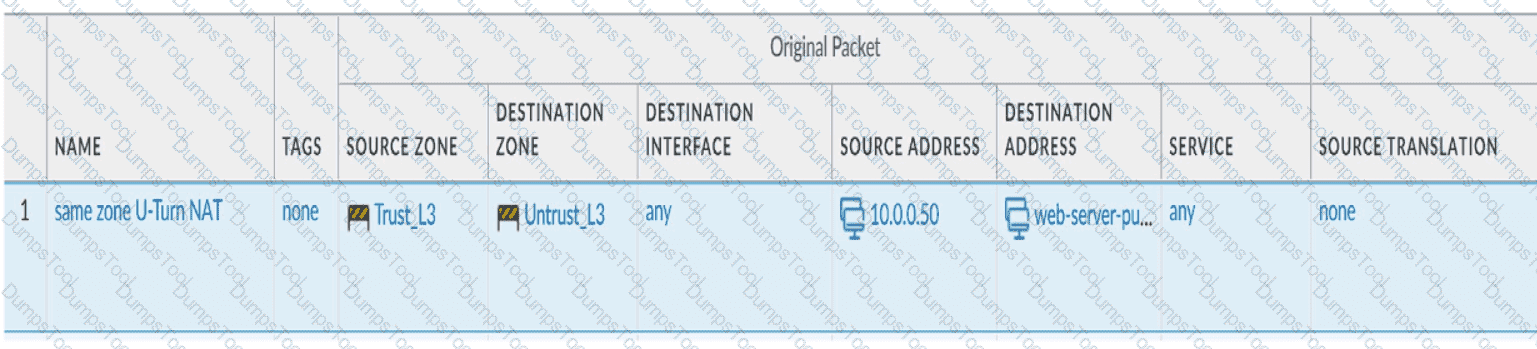
Review the information below. A firewall engineer creates a U-NAT rule to allow users in the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as expected?
An administrator plans to install the Windows User-ID agent on a domain member system.
What is a best practice for choosing where to install the User-ID agent?
A network security administrator has an environment with multiple forms of authentication. There is a network access control system in place that authenticates and restricts access for wireless users, multiple Windows domain controllers, and an MDM solution for company-provided smartphones. All of these devices have their authentication events logged.
Given the information, what is the best choice for deploying User-ID to ensure maximum coverage?
A firewall engineer creates a source NAT rule to allow the company's internal private network 10.0.0.0/23 to access the internet. However, for security reasons, one server in that subnet (10.0.0.10/32) should not be allowed to access the internet, and therefore should not be translated with the NAT rule.
Which set of steps should the engineer take to accomplish this objective?
A new firewall has the Threat Prevention subscription, but the Antivirus does not appear in Dynamic Updates.
What must occur to have Antivirus signatures update?
A network security administrator has been tasked with deploying User-ID in their organization.
What are three valid methods of collecting User-ID information in a network? (Choose three.)
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory. What must be configured in order to select users and groups for those rules from Panorama? The Security rules must be targeted to a firewall in the device group and have Group Mapping configured.
An engineer troubleshoots a Panorama-managed firewall that is unable to reach the DNS servers configured via a global template. As a troubleshooting step, the engineer needs to configure a local DNS server in place of the template value.
Which two actions can be taken to ensure that only the specific firewall is affected during this process? (Choose two )
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
A network security engineer needs to ensure that virtual systems can communicate with one another within a Palo Alto Networks firewall. Separate virtual routers (VRs) are created for each virtual system.
In addition to confirming security policies, which three configuration details should the engineer focus on to ensure communication between virtual systems? (Choose three.)
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow Upon opening the newly created packet capture, the administrator still sees traffic for the previous fitter What can the administrator do to limit the captured traffic to the newly configured filter?
Which two policy components are required to block traffic in real time using a dynamic user group (DUG)? (Choose two.)
If a URL is in multiple custom URL categories with different actions, which action will take priority?
An engineer is deploying multiple firewalls with common configuration in Panorama.
What are two benefits of using nested device groups? (Choose two.)
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed. What is one way the administrator can meet this requirement?
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
An engineer configures a specific service route in an environment with multiple virtual systems instead of using the inherited global service route configuration.
What type of service route can be used for this configuration?
A firewall administrator to have visibility on one segment of the company network. The traffic on the segment is routed on the Backbone switch. The administrator is planning to apply security rules on segment X after getting the visibility. There is already a PAN-OS firewall used in L3 mode as an internet gateway, and there are enough system resources to get extra traffic on the firewall. The administrator needs to complete this operation with minimum service interruptions and without making any IP changes. What is the best option for the administrator to take?
A company has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a phishing campaign against the organization prompts a search for more controls to secure access to critical assets. For users who need to access these systems, the company decides to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA.
What must the company do in order to use PAN-OS MFA?
An administrator has been asked to configure active/active HA for a pair of Palo Alto Networks NGFWs. The firewall use Layer 3 interfaces to send traffic to a single gateway IP for the pair.
Which configuration will enable this HA scenario?
A company has a PA-3220 NGFW at the edge of its network and wants to use active directory groups in its Security policy rules. There are 1500 groups in its active directory. An engineer has been provided 800 active directory groups to be used in the Security policy rules.
What is the engineer's next step?
A firewall engineer creates a NAT rule to translate IP address 1.1.1.10 to 192.168.1.10. The engineer also plans to enable DNS rewrite so that the firewall rewrites the IPv4 address in a DNS response based on the original destination IP address and translated destination IP address configured for the rule. The engineer wants the firewall to rewrite a DNS response of 1.1.1.10 to 192.168.1.10.
What should the engineer do to complete the configuration?
A system administrator runs a port scan using the company tool as part of vulnerability check. The administrator finds that the scan is identified as a threat and is dropped by the firewall. After further investigating the logs, the administrator finds that the scan is dropped in the Threat Logs.
An engineer troubleshoots a high availability (HA) link that is unreliable.
Where can the engineer view what time the interface went down?
Which two profiles should be configured when sharing tags from threat logs with a User-ID agent? (Choose two.)
Which three statements accurately describe Decryption Mirror? (Choose three.)
An engineer is configuring Packet Buffer Protection on ingress zones to protect from single-session DoS attacks.
Which sessions does Packet Buffer Protection apply to?
A firewall engineer is investigating high dataplane CPU utilization. To decrease the load on this CPU, what should be reduced?
A company is deploying User-ID in their network. The firewall team needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules.
How can this be achieved?
Which CLI command is used to simulate traffic going through the firewall and determine which Security policy rule, NAT translation, static route, or PBF rule will be triggered by the traffic?
Which link is responsible for synchronizing sessions between high availability (HA) peers?
An engineer is designing a deployment of multi-vsys firewalls.
What must be taken into consideration when designing the device group structure?
An administrator needs to validate that policies that will be deployed will match the appropriate rules in the device-group hierarchy. Which tool can the administrator use to review the policy creation logic and verify that unwanted traffic is not allowed?
An administrator needs to gather information about the CPU utilization on both the management plane and the data plane. Where does the administrator view the desired data?
An administrator wants to use LDAP, TACACS+, and Kerberos as external authentication services for authenticating users. What should the administrator be aware of regarding the authentication sequence, based on the Authentication profile in the order Kerberos LDAP, and TACACS+?
Given the following snippet of a WildFire submission log, did the end user successfully download a file?
An engineer is reviewing policies after a PAN-OS upgrade What are the two differences between Highlight Unused Rules and the Rule Usage Hit counters immediately after a reboot?
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
What should an administrator consider when planning to revert Panorama to a pre-PAN-OS 10.1 version?
A firewall engineer has determined that, in an application developed by the company's internal team, sessions often remain idle for hours before the client and server exchange any data. The application is also currently identified as unknown-tcp by the firewalls. It is determined that because of a high level of trust, the application does not require to be scanned for threats, but it needs to be properly identified in Traffic logs for reporting purposes.
Which solution will take the least time to implement and will ensure the App-ID engine is used to identify the application?
A firewall engineer is tasked with defining signatures for a custom application. Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
A security engineer wants to upgrade the company's deployed firewalls from PAN-OS 10.1 to 11.0.x to take advantage of the new TLSvl.3 support for management access.
What is the recommended upgrade path procedure from PAN-OS 10.1 to 11.0.x?
Which GloDalProtecI gateway setting is required to enable split-tunneting by access route, destination domain and application?
An administrator is informed that the engineer who previously managed all the VPNs has left the company. According to company policies the administrator must update all the IPSec VPNs with new pre-shared keys Where are the pre-shared keys located on the firewall?
What is the best description of the Cluster Synchronization Timeout (min)?
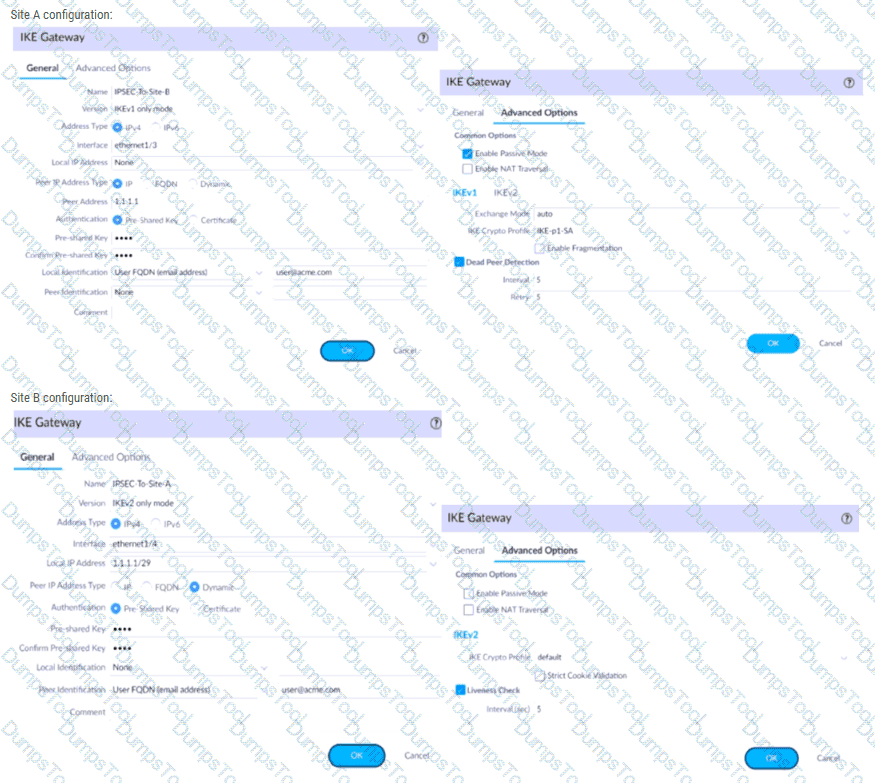
A firewall administrator is configuring an IPSec tunnel between Site A and Site B. The Site A firewall uses a DHCP assigned address on the outside interface of the firewall, and the Site B firewall uses a static IP address assigned to the outside interface of the firewall. However, the use of dynamic peering is not working.
Refer to the two sets of configuration settings provided. Which two changes will allow the configurations to work? (Choose two.)
Site A configuration:
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall. Which certificate is the best choice to configure as an SSL Forward Trust certificate?
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an interal syslog server. Where can the firewall engineer define the data to be added into each forwarded log?
You are auditing the work of a co-worker and need to verify that they have matched the Palo Alto Networks Best Practices for Anti-Spyware Profiles.
For which three severity levels should single-packet captures be enabled to meet the Best Practice standard? (Choose three.)
Which log type would provide information about traffic blocked by a Zone Protection profile?
Refer to the exhibit.
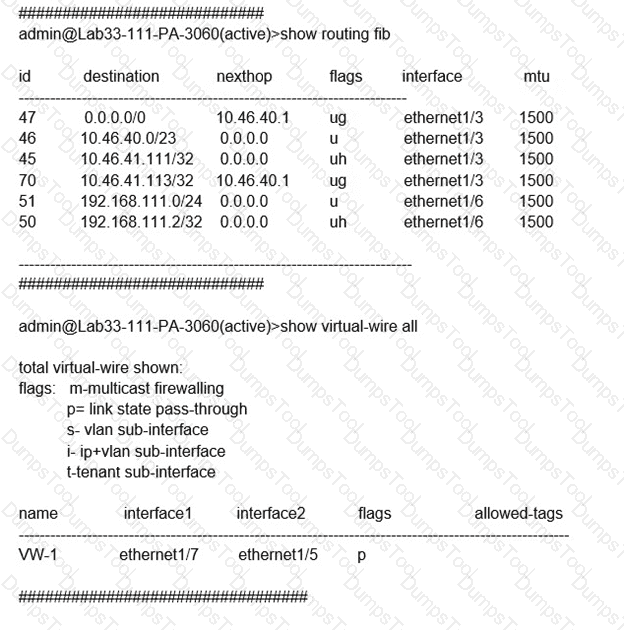
Which will be the egress interface if the traffic's ingress interface is ethernet1/7 sourcing from 192.168.111.3 and to the destination 10.46.41.113?
Information Security is enforcing group-based policies by using security-event monitoring on Windows User-ID agents for IP-to-User mapping in the network. During the rollout, Information Security identified a gap for users authenticating to their VPN and wireless networks.
Root cause analysis showed that users were authenticating via RADIUS and that authentication events were not captured on the domain controllers that were being monitored Information Security found that authentication events existed on the Identity Management solution (IDM). There did not appear to be direct integration between PAN-OS and the IDM solution
How can Information Security extract and learn iP-to-user mapping information from authentication events for VPN and wireless users?
After configuring an IPSec tunnel, how should a firewall administrator initiate the IKE phase 1 to see if it will come up?
For company compliance purposes, three new contractors will be working with different device-groups in their hierarchy to deploy policies and objects.
Which type of role-based access is most appropriate for this project?
An organization conducts research on the benefits of leveraging the Web Proxy feature of PAN-OS 11.0.
What are two benefits of using an explicit proxy method versus a transparent proxy method? (Choose two.)
Following a review of firewall logs for traffic generated by malicious activity, how can an administrator confirm that WildFire has identified a virus?
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
When using certificate authentication for firewall administration, which method is used for authorization?
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL.
When creating a new rule, what is needed to allow the application to resolve dependencies?
Which conditions must be met when provisioning a high availability (HA) cluster? (Choose two.)
Phase two of a VPN will not establish a connection. The peer is using a policy-based VPN configuration.
What part of the configuration should the engineer verify?
Which two key exchange algorithms consume the most resources when decrypting SSL traffic? (Choose two.)
An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing.
What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
What must be configured to apply tags automatically based on User-ID logs?
A customer requires that virtual systems with separate virtual routers can communicate with one another within a Palo Alto Networks firewall. In addition to confirming Security policies, which three configurations will accomplish this goal? (Choose three)
Which interface type should a firewall administrator configure as an upstream to the ingress trusted interface when configuring transparent web proxy on a Palo Alto Networks firewall?
A firewall engineer is migrating port-based rules to application-based rules by using the Policy Optimizer. The engineer needs to ensure that the new application-based rules are future-proofed, and that they will continue to match if the existing signatures for a specific application are expanded with new child applications. Which action will meet the requirement while ensuring that traffic unrelated to the specific application is not matched?
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
An administrator has two pairs of firewalls within the same subnet. Both pairs of firewalls have been configured to use High Availability mode with Active/Passive. The ARP tables for upstream routes display the same MAC address being shared for some of these firewalls.
What can be configured on one pair of firewalls to modify the MAC addresses so they are no longer in conflict?
Refer to exhibit.
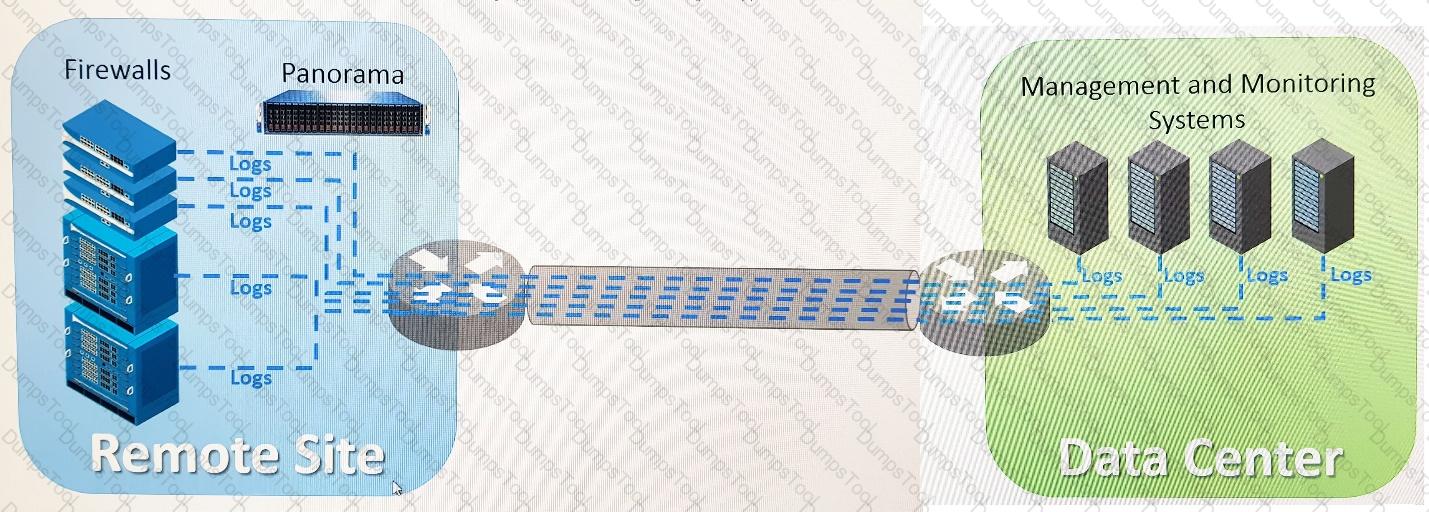
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms. The network team has reported excessive traffic on the corporate WAN.
How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all existing monitoring/ security platforms?
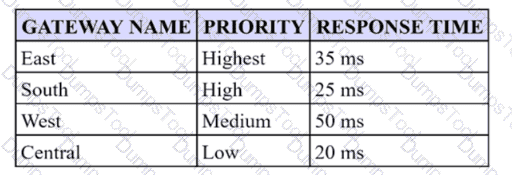
A security engineer has configured a GlobalProtect portal agent with four gateways Which GlobalProtect Gateway will users connect to based on the chart provided?
An engineer is reviewing the following high availability (HA) settings to understand a recent HAfailover event.
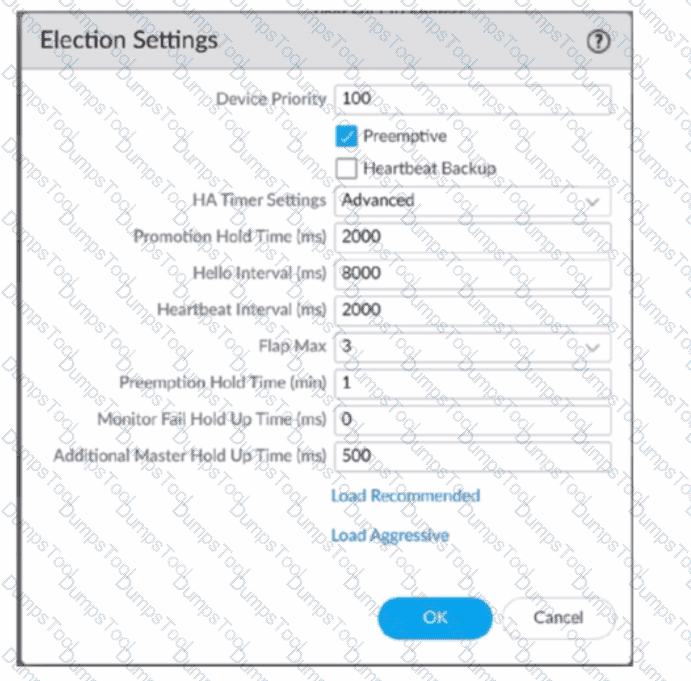
Which timer determines the frequency between packets sent to verify that the HA functionality on the other HA firewall is operational?
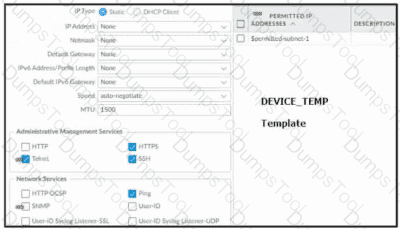
Based on the images below, and with no configuration inside the Template Stack itself, what access will the device permit on its management port?

Review the screenshot of the Certificates page.
An administrator for a small LLC has created a series of certificates as shown, to use for a planned Decryption roll out. The administrator has also installed the self-signed root certificate in all client systems.
When testing, they noticed that every time a user visited an SSL site, they received unsecured website warnings.
What is the cause of the unsecured website warnings?
An engineer has been asked to limit which routes are shared by running two different areas within an OSPF implementation. However, the devices share a common link for communication. Which virtual router configuration supports running multiple instances of the OSPF protocol over a single link?
A network administrator notices a false-positive state after enabling Security profiles. When the administrator checks the threat prevention logs, the related signature displays the following:
threat type: spyware category: dns-c2 threat ID: 1000011111
Which set of steps should the administrator take to configure an exception for this signature?
The server team is concerned about the high volume of logs forwarded to their syslog server, it is determined that DNS is generating the most logs per second. The risk and compliance team requests that any Traffic logs indicating port abuse of port 53 must still be forwarded to syslog. All other DNS. Traffic logs can be exclude from syslog forwarding. How should syslog log forwarding be configured?