Refer to the exhibit.
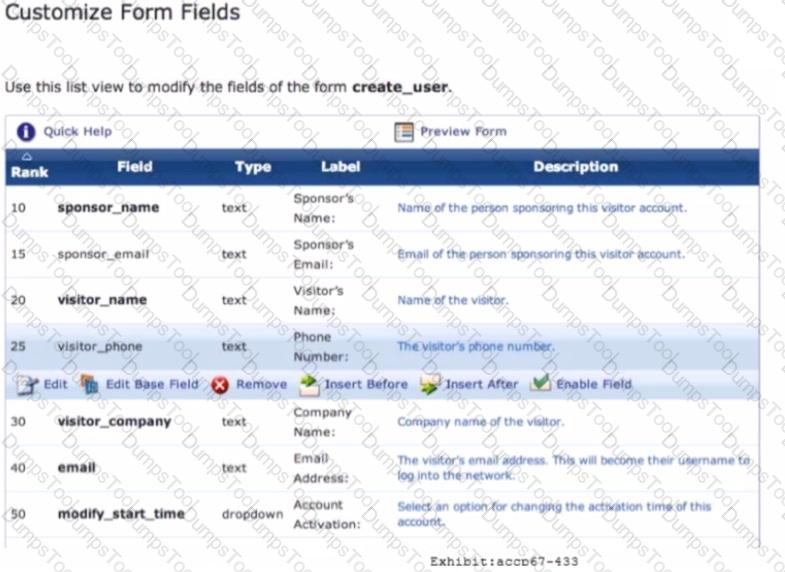
Based on the configuration of me create_user form shown, which statement accurately describes the status?
Refer to the exhibit.
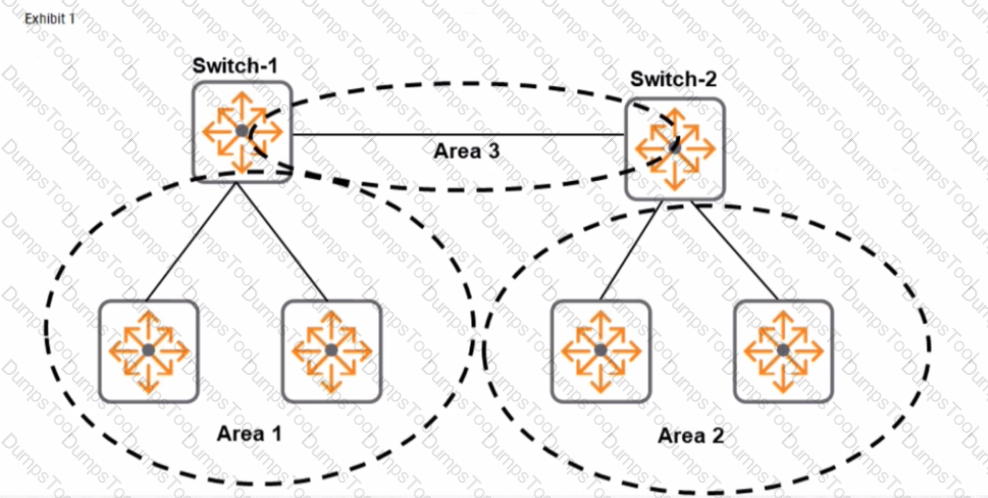
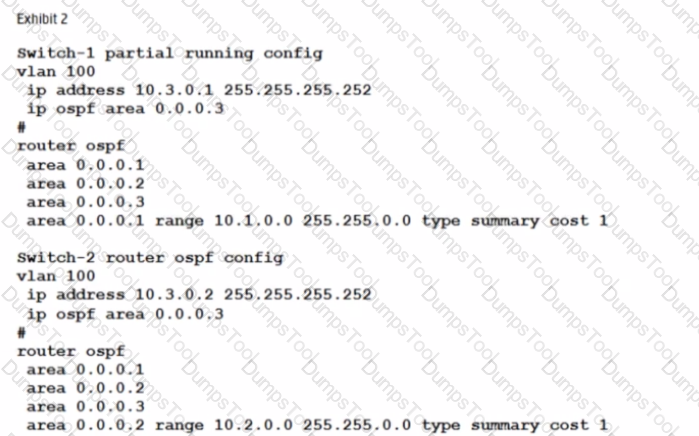
A company has attempted to implement OSPF without success. The devices in Area I need to be able to reach Area 2. Routes should be aggregated for advertisementinother areas. What must be changed to meet these requirements?
in a VPN that uses certificate-based authentication, which component must be configured on the Mobility Master (MM) to allow a RAP to successfully connect to a Mobility Controller (MC)
Refer to the exhibit.
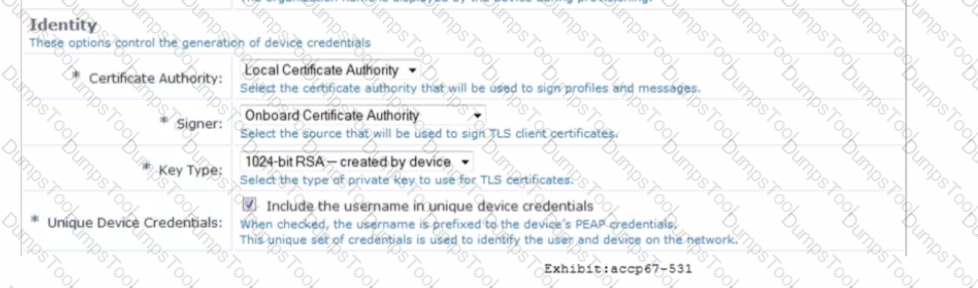
Based on the configuration for the client's certificate private key as shown, which statements accurately describe the settings? (Select two.)