The certificate used for decryption was installed as a trusted toot CA certificate to ensure communication between the Cortex XDR Agent and Cortex XDR Management Console. What action needs to be taken if the administrator determines the Cortex XDR Agents are not communicating with the Cortex XDR Management Console?
Which two troubleshooting steps should be taken when an integration is failing to connect? (Choose two.)
A customer has purchased Cortex XDR and requires 24/7 monitoring of the platform. However, the customer only has staff available during business hours.
Which Palo Alto Networks offering would best meet this requirement?
A customer wants the main Cortex XSOAR server installed in one site and wants to integrate with three other technologies in a second site.
What communications are required between the two sites if the customer wants to install a Cortex XSOAR engine in the second site?
How does Cortex XSOAR automation save time when a phishing incident occurs?
Which technology allows a customer to integrate Cortex Xpanse with third-party applications or services, assets, and IP ranges while leveraging investigation capabilities?
Which solution profiles network behavior metadata, not payloads and files, allowing effective operation regardless of encrypted or unencrypted communication protocols, like HTTPS?
Which statement applies to the differentiation of Cortex XDR from security information and event management (SIEM)?
Cortex XDR can schedule recurring scans of endpoints for malware. Identify two methods for initiating an on-demand malware scan (Choose two )
Which Cortex XDR capability prevents running malicious files from USB-connected removable equipment?
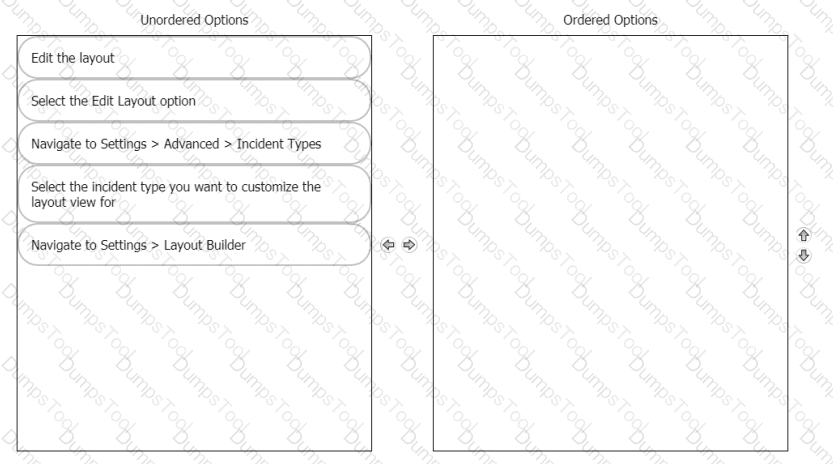
Rearrange the steps into the correct order for modifying an incident layout.
What method does the Traps agent use to identify malware during a scheduled scan?
Which feature in Cortex XSIAM extends analytics detections to all mapped network and authentication data?
How does the integration between Cortex Xpanse and Cortex XSOAR benefit security teams?
When running a Cortex XSIAM proof of value (POV), why is it important to deploy the Cortex XDR agent?
In the DBotScore context field, which context key would differentiate between multiple entries for the same indicator in a multi-TIP environment?
When preparing the golden image in a Cortex XDR Virtual Desktop Infrastructure (VDI) deployment, which step is required?
Which service helps uncover attackers wherever they hide by combining world-class threat hunters with Cortex XDR technology that runs on integrated endpoint, network, and cloud data sources?
A Cortex Xpanse customer receives an email regarding an upcoming product update and wants to get more information on the new features.
In which resource can the customer access this information?
An administrator of a Cortex XDR protected production environment would like to test its ability to protect users from a known flash player exploit.
What is the safest way to do it?
In Cortex XDR Prevent, which three matching criteria can be used to dynamically group endpoints? (Choose three )
A customer has 2700 endpoints. There is currently concern about recent attacks in their industry and threat intelligence from a third-party subscription. In an attempt to be proactive, phishing simulations have been prioritized, but the customer wants to gain more visibility and remediation capabilities specific to their network traffic.
Which Cortex product provides these capabilities?
A Cortex XSIAM customer is unable to access their Cortex XSIAM tenant.
Which resource can the customer use to validate the uptime of Cortex XSIAM?
Which consideration should be taken into account before deploying Cortex XSOAR?
The prospect is deciding whether to go with a phishing or a ServiceNow use case as part of their POC We have integrations for both but a playbook for phishing only Which use case should be used for the POC?
Why is it important to document notes from the Proof of Value (POV) for post-sales hand off?
A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
On a multi-tenanted v6.2 Cortex XSOAR server, which path leads to the server.log for "Tenant1"?
What allows the use of predetermined Palo Alto Networks roles to assign access rights to Cortex XDR users?
Which integration allows searching and displaying Splunk results within Cortex XSOAR?
Which deployment type supports installation of an engine on Windows, Mac OS. and Linux?
Which Cortex XDR Agent capability prevents loading malicious files from USB-connected removable equipment?