Database user SCOTT requires the privilege to select from all tables and you decide to configure this using a global role.
You have not yet configured the database with Enterprise User Security.
You plan to perform these steps:
1. create role GLOBAI._ROI.E identified globally;
2. grant select any table to GLODAL_COLE;
3. grant GLOBAL_ROLE to SCOTT;
What is the result?
Examine these commands and the output used to configure Real Application Security:
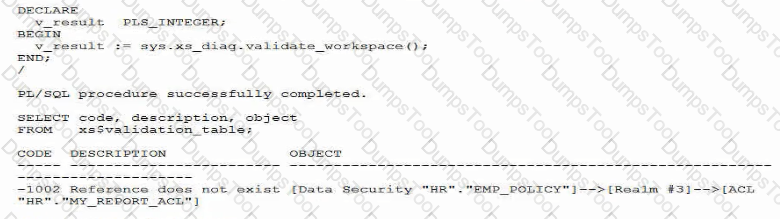
What does this output mean?
Which two configurations can be used to protect sensitive data In a database?