An administrator initially performed a cluster Foundation using a flat switch without any VLAN configuration. After the Foundation, the administrator moved the dual 25Gb data ports and single 1Gb IPMI port to the actual switches with the below network configurations:
. All VLANs are tagged
. VLAN 1000 for CVM\Hypervisor traffic
· VLAN 1001 for User VM traffic
. VLAN 100 for IPMI traffic
After moving the IPMI network links, the administrator can no longer ping the IPMI IPs.
Which two changes does the administrator need to make? (Choose two.)
A configuration is single domain, single forest, and does not use SSL.
Which port number should be used to configure LDAP?
An administrator has been alerted to a VM that has high I/O latency and wants to determine if there are any other factors, such as insufficient network or memory resources that correlate, as part of a troubleshooting process.
Which type of chart should the administrator create to allow all relevant data to be easily exported to CSV for later analysis?
Which three cluster operations require an administrator to reclaim licenses?(Choose three)
A two-node ROBO cluster is configured with a witness VM.
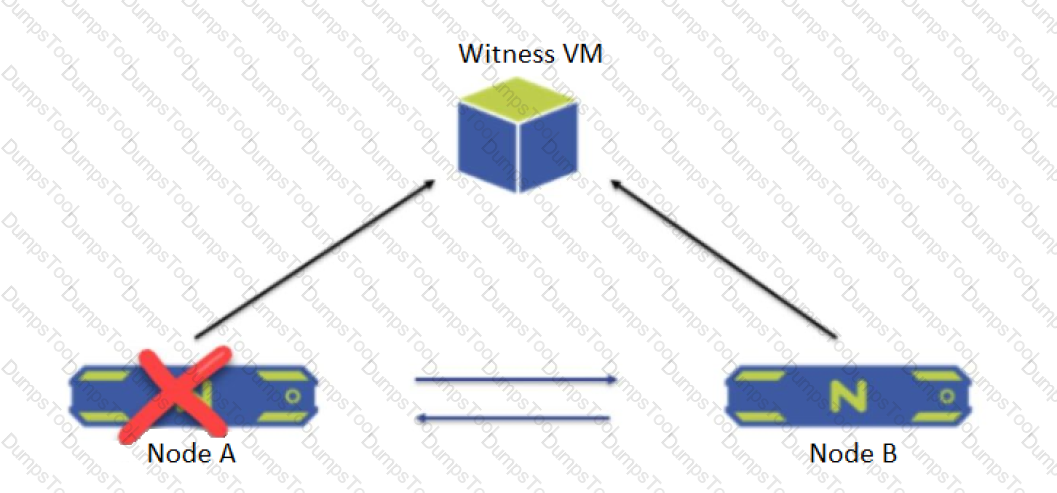
What happens when Node A goes down?
Prism Central will be installed manually on an AHV cluster.
Which three disk images must be downloaded from the portal for the Prism Central VM? (Choose three.)
An administrator is commissioning a Nutanix Enterprise Cloud. Once the user VMs have been deployed and are running, the administrator finds that VMs on the same host are able to communicate, but are unable to communicate between hosts.
What must be changed to enable full inter-VM communications?
Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?
Async DR is configured between two sites. A network outage occurs at the primary site.
Which steps must the administrator perform to bring the VMs back into service at the backup site?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements. Not all procedures are valid. Identify any invalid procedures using the drop-down option.

An administrator has created a Nutanix managed it a VLAN ID of 512.
Several VMs have been created, and the administrator notices that the can successfully communicate with other VMs on that VLAN.
Provided they are on the host, but cannot communicate with VMs that reside on different hosts in the cluster.
What is most likely thee cause of this issue?
How should an administrator configure a custom alert for a specific VM in Prism?
In the event of a disk failure, which process will immediately ad automatically scans Cassandra to find all data previously hosted on the failed disk, and all disks in that node?
A customer has a 24-node cluster with all containers configured with RF3. Two different nodes have incurred a simultaneous HDD failure.
What is the result?
An administrator manages a cluster and notices several failed components shown in the exhibit.

What two options does the administrator have to run all NCC checks manually? (Choose two.)
Refer to Exhibit:
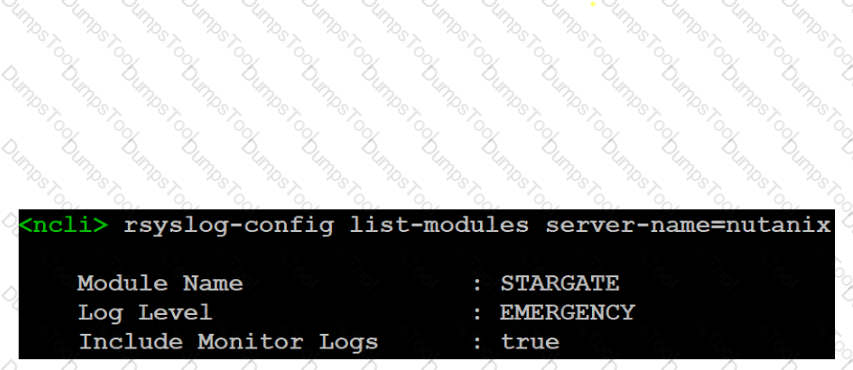
After configuring modules for a Remote Syslog Server, the settings are as shown. The administrator notices that even though the level parameter is set to EMERGENCY, that all monitor logs are being sent.
What is the likely cause of this issue?
An administrator needs to configure Prism to send encrypted messages to a set of recipients.
Which setting must be applied?
When configuring Prism Central, which two log modules are able to forward messages to an external syslog server? (Choose two.
A newly-hired Nutanix administrator was tasked by the CIO to create a single VM on a test network. The network administrator stated that a native VLAN was used on the Cisco TOR switches with the following parameters:
IP address:172,16.1.2
Network Mask: 255.255.255.0
Default gateway: 172.16.1.1
VLAN:1
The same parameters were used to create a network profile on Nutanix, but the when the VM was on …
What should the Nutanix administrator do to fix this issue?
The customer is seeing high memory utilization on a mission critical VM. Users report that the application is unavailable. The guest OS does not support hot add components.
How should the administrator fix this issue?
An administrator needs to deploy an application with a large amount of data connected via Nutanix volumes.
Which two actions should the administrator take when designing the Volume Group? (Choose two.)
In which two scenarios is an automated live migration likely to occur? (Choose two)
Which two capabilities does IPAM provide in a Nutanix networking configuration? (Choose two.)
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
C)

D)

An administrator needs to relocate an AHV cluster to a new datacenter during a maintenance window. The cluster will use the same IPs in the new datacenter.
Which two steps should be taken to prepare for this task? (Choose two.)
An administrator has created several custom alert policies, which are applied to the same entities. Prism Central displays a message that a similar policy exists.
In what order of precedence are overlapping policies evaluated?

An administrator needs to bring down a host in a Nutanix Cluster for maintenance reasons. The administrator puts the host in maintenance mode.
What should the administrator do to perform an orderly shutdown of the CVM?
What Nutanix feature provides effective caching optimization In VDI environments?
A user is complaining about slowness of a mission-critical MSSQL Server. The administrator logs into Prism Element to investigate the VM performance and observes what is shown in the diagram.
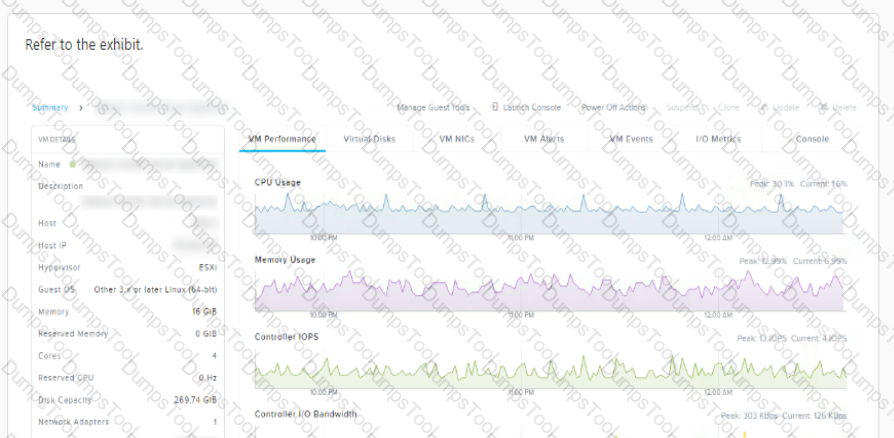
Which action would best improve VM performance?
Which best practice should be followed when creating a bond in a Nutanix cluster?
Which two types of granular RBAC does Nutanix provide for AHV hosts? (Choose two.)
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic regardless of direction, between two groups of VMs identified by their category.
Which policy should be used to meet this requirement?
When a configuring a syslog server in Prism Central, what two pieces information are required? (Choose two.)
The administrator wants a container to be displayed and limited to 1TB in the hypervisor.
What advanced container setting must the administrator set?
An administrator wants to receive an environment summary report when a host failure occurs.
Which action would address the administrator’s need?
An administrator is configuring data protection and DR for a multi-tier application. All VMs must be protected at the same time.
What must the administrator do to meet this requirement?
A system administrator needs to add more VMs to their Nutanix cluster.
Which two actions should the administrator perform to determine if the current cluster can accommodate the new VMs? (Choose two)
A cluster has RF2. The cluster loses two drives on different nodes in the same storage tier.
What is the effect on the replicas of the VMs?
How should an administrator correct an SSL error when connecting to a Nutanix cluster?
An administrator adds a node with older generation processors to an existing AHV cluster with newer generation processors. What is the effect on live migration?