A Mule API receives a JSON payload and updates the target system with the payload. The developer uses JSON schemas to ensure the data is valid.
How can the data be validation before posting to the target system?
Refer to the exhibit.
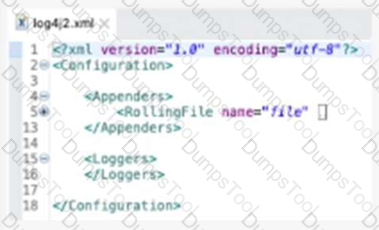
What action must be performed to log all the errors raised by the VM Connector?
A Mule application deployed to multiple Cloudhub 2.0 replicas needs to temporarily persist large files over 10MB between flow executions, and routinely needs to query whether the file data exists on separate executions.
How can this be achieved?
Refer to the exhibit.
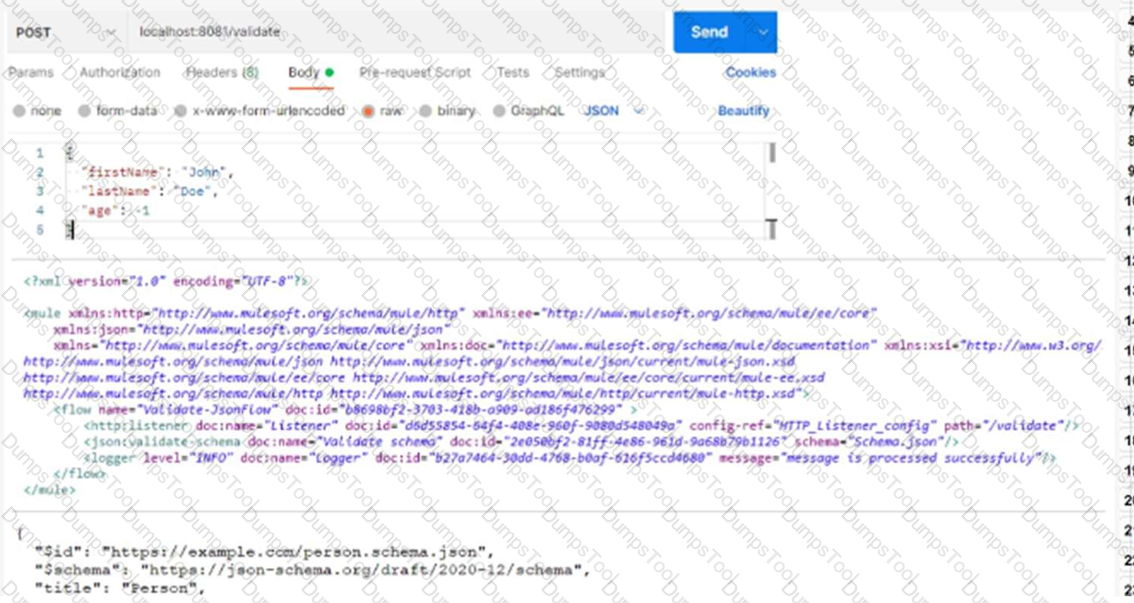
Based on the code snippet, schema,json file, and payload below, what is the outcome of the given code snippet when a request is sent with the payload?
Multiple individual Mute application need to use the Mule Maven plugin to deploy to CloudHub.
The plugin configuration should .. reused where necessary and anything project, specific should be property-based.
Where should the Mule Maven details be configured?
A Mule application contain two policies Policy A and Policy A has order1, and Policy B has order 2. Policy A Policy B, and a flow are defined by he configuration below.

When a HTTP request arrives at the Mule application’s endpoint, what will be the execution order?
When implementing a synchronous API where the event source is an HTTP Listener, a developer needs to return the same correlation ID back to the caller in the HTTP response header.
How can this be achieved?
What is the MuleSoft recommended method to encrypt sensitive property data?
Refer to the exhibit.
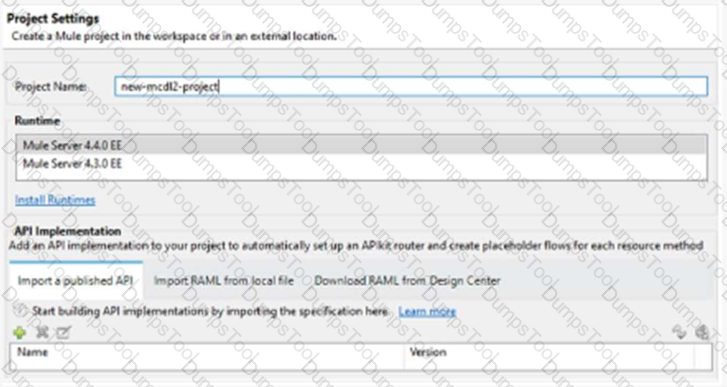
When creating a new project, which API implementation allows for selecting the correct API version and scaffolding the flows from the API specification?
A Mule application need to invoice an API hosted by an external system to initiate a process. The external API takes anywhere between one minute and 24 hours to compute its process.
Which implementation should be used to get response data from the external API after it completes processing?
A company deploys 10 public APIs to CloudHub. Each API has its individual health endpoint defined. The platform operation team wants to configure API Functional Monitoring to monitor the health of the APIs periodically while minimizing operational overhead and cost.
How should API Functional Monitoring be configured?
The Center for Enablement team published a common application as a reusable module to the central Nexus repository.
How can the common application be included in all API implementations?
A developer is working on a project that requires encrypting all data before sending it to a backend application. To accomplish this, the developer will use PGP encryption in the Mule 4 Cryptography module.
What is required to encrypt the data before sending it to the backend application?