You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
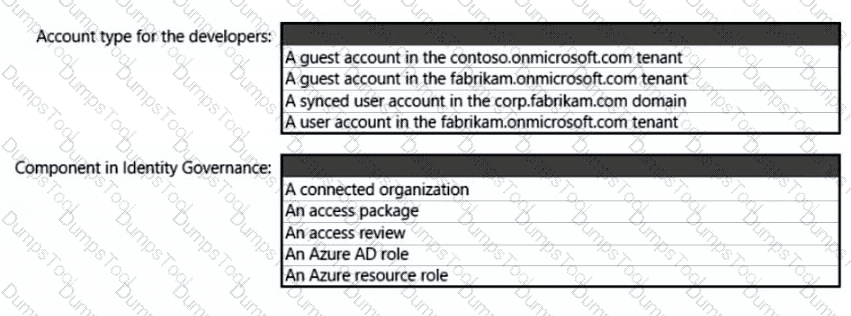
You have a Microsoft Entra tenant named contoso.com.
You have an external partner that has a Microsoft Entra tenant named fabrikam.com.
You need to recommend an identity governance solution for contoso.com that meets the following requirements:
Enables the users in contoso.com and fabrikam.com to communicate by using shared Microsoft Teams channels.
Manages access to shared Teams channels in contoso.com by using groups in fabrikam.com.
Supports single sign-on (SSO).
Minimizes administrative effort.
Maximizes security.
What should you include in the recommendation?
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
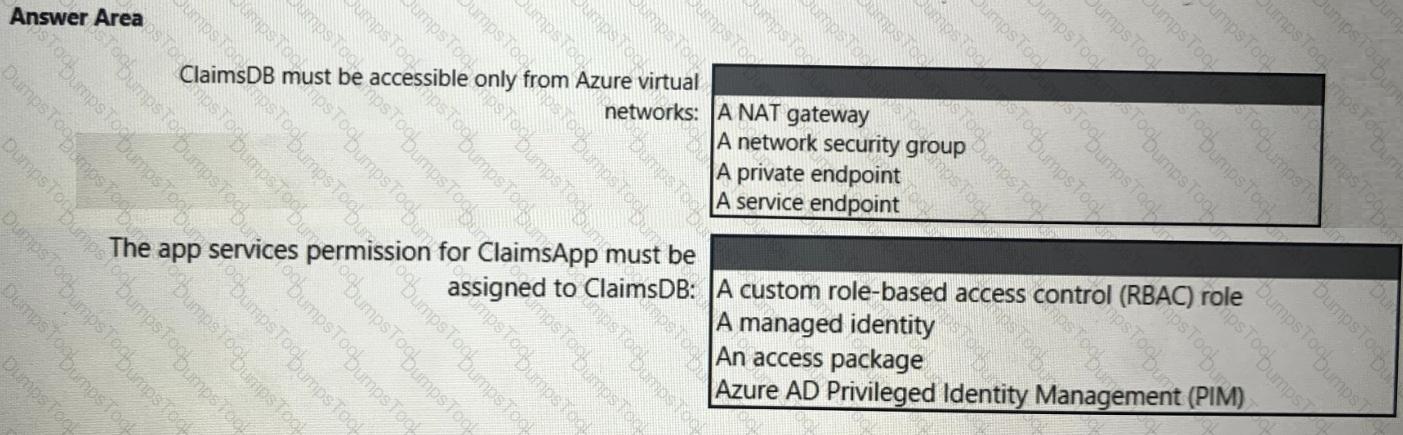
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
What should you create in Azure AD to meet the Contoso developer requirements?
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
You have a Microsoft 365 subscription that contains 1,000 users. Each user is assigned a Microsoft 365 E5 license.
The subscription uses sensitivity labels to classify corporate documents. All the users have Windows 11 devices that are onboarded to Microsoft Defender for Endpoint and are configured to sync files to Microsoft OneDrive.
You need to prevent the users from uploading the documents from OneDrive to external websites.
What should you include in the solution?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For Azure SQL databases, you recommend Transparent Data Encryption (TDE) that uses Microsoft-managed keys.
Does this meet the goal?
You have an Azure DevOps organization that is used to manage the development and deployment of internal apps to multiple Azure subscriptions.
You need to implement a DevSecOps strategy based on Microsoft Cloud Adoption Framework for Azure principles. The solution must meet the following requirements:
• All pull requests must be enforced.
• All deployments to production must be approved.
What should you include in the solution for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have an Azure subscription that contains 100 virtual machines. The virtual machines are accessed by using Azure Bastion.
You need to recommend a solution to ensure that only specific users in specific locations can access the virtual machines. The solution must meet the following requirements:
• Restrict access to the virtual machines based on an originating IP address or a connection request by using just-in-time (JIT) VM access network-based controls.
• Restrict access to the virtual machines based on role-based access control (RBAC) role assignments by using JIT VM access authorization controls.
Which Microsoft cloud services should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

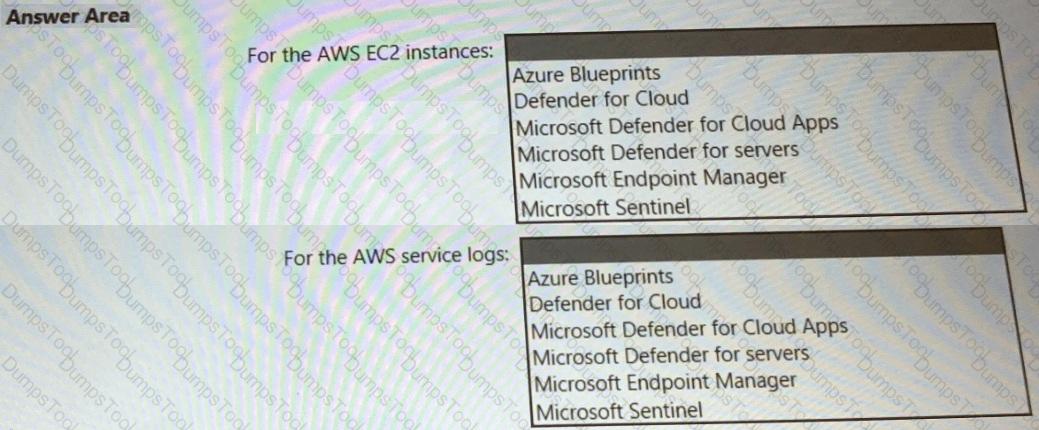
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
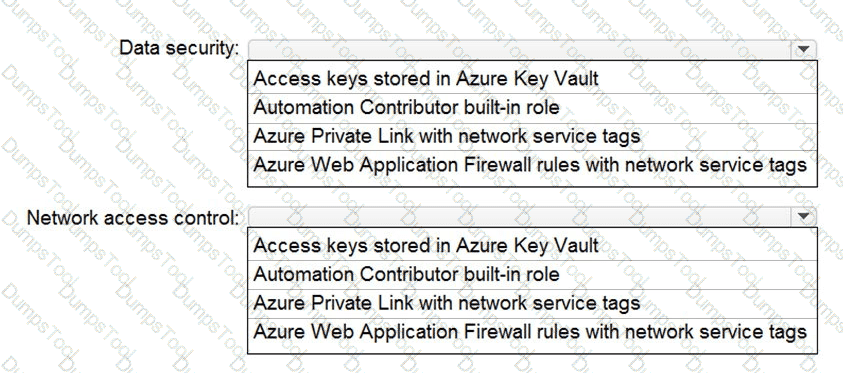
You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2.
You need to recommend a solution to secure the components of the copy process.
What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud.
You receive the following recommendations in Defender for Cloud
• Access to storage accounts with firewall and virtual network configurations should be restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
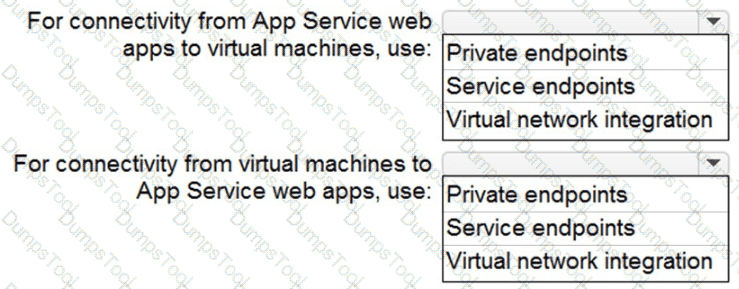
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
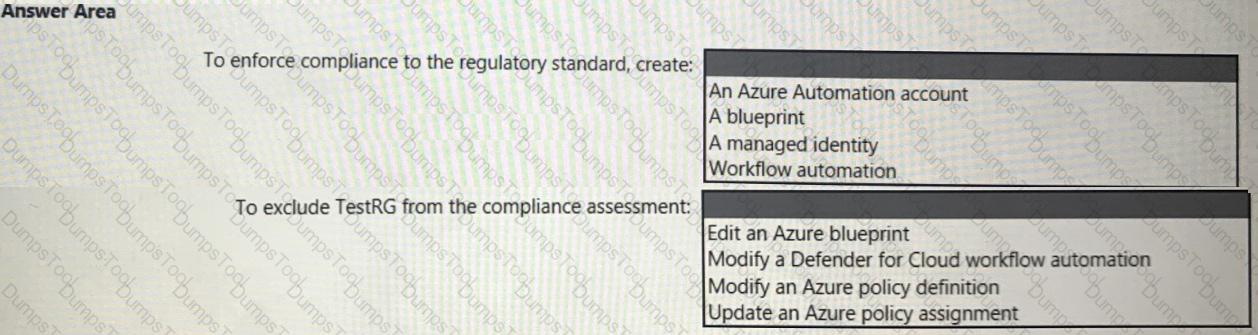
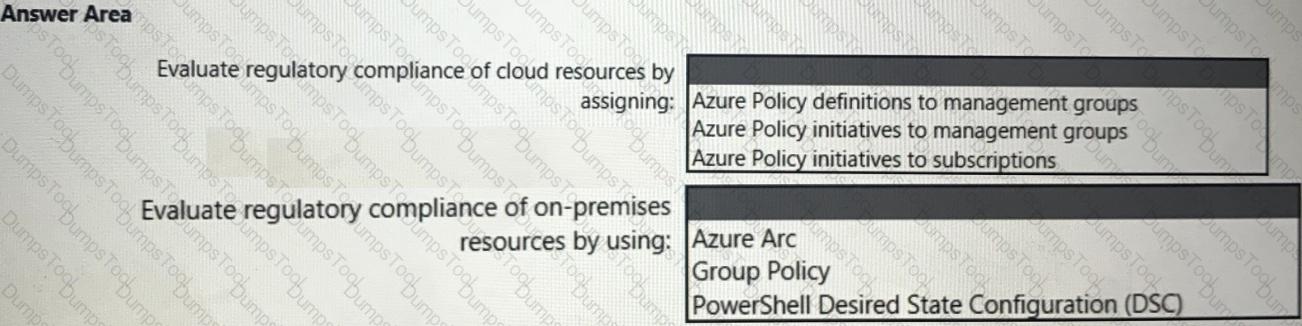
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?
You are designing the security standards for a new Azure environment.
You need to design a privileged identity strategy based on the Zero Trust model.
Which framework should you follow to create the design?
You have an Azure subscription
You plan to deploy multiple containerized microservice-based apps to Azure Kubemetes Service (AKS)
You need to recommend a solution that meets the following requirements:
• Manages secrets
• Provides encryption
• Secures service-to-service communication by using mTLS encryption
• Minimizes administrative effort
What should you include in the recommendation?
You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys.
You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications.
What should you include in the recommendation?
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription.
All the on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend configurations to meet the following requirements:
• Ensure that the security operations team can access the security logs and the operation logs.
• Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two configurations can you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
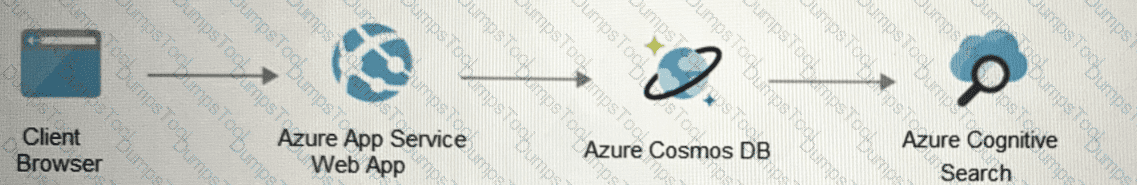
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF).
Does this meet the goal?
You have an Azure subscription.
You plan to deploy Azure App Services apps by using Azure DevOps.
You need to recommend a solution to ensure that deployed apps maintain compliance with Microsoft cloud security benchmark (MCSB) recommendations.
What should you include in the recommendation?
You have an Azure subscription that contains a resources group named RG1. RG1 contains multiple Azure Files shares.
You need to recommend a solution to deploy a backup solution for the shares. The solution must meet the following requirements:
• Prevent the deletion of backups and the vault used to store the backups.
• Prevent privilege escalation attacks against the backup solution.
• Prevent the modification of the backup retention period.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Your company has Microsoft 365 E5 licenses and Azure subscriptions.
The company plans to automatically label sensitive data stored in the following locations:
• Microsoft SharePoint Online
• Microsoft Exchange Online
• Microsoft Teams
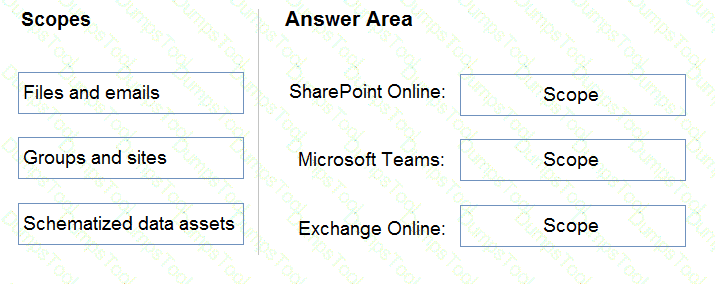
You need to recommend a strategy to identify and protect sensitive data.
Which scope should you recommend for the sensitivity label policies? To answer, drag the appropriate scopes to the correct locations. Each scope may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You have an on-premises server that runs Windows Server and contains a Microsoft SQL Server database named DB1.
You plan to migrate DB1 to Azure.
You need to recommend an encrypted Azure database solution that meets the following requirements:
• Minimizes the risks of malware that uses elevated privileges to access sensitive data
• Prevents database administrators from accessing sensitive data
• Enables pattern matching for server-side database operations
• Supports Microsoft Azure Attestation
• Uses hardware-based encryption
What should you include in the recommendation?
You have an Azure subscription.
You plan to deploy Azure Kubernetes Service (AKS) clusters that will be used to host web services. You need to recommend an ingress controller solution that will protect the hosted web services. What should you include in the recommendation?
Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States.
You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attach surface.
What should you include in the recommendation?
You have legacy operational technology (OT) devices and loT devices.
You need to recommend best practices for applying Zero Trust principles to the OT and loT devices based on the Microsoft Cybersecurity Reference Architectures (MCRA). The solution must minimize the risk of disrupting business operations.
Which two security methodologies should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point
Your company plans to move all on-premises virtual machines to Azure. A network engineer proposes the Azure virtual network design shown in the following table.
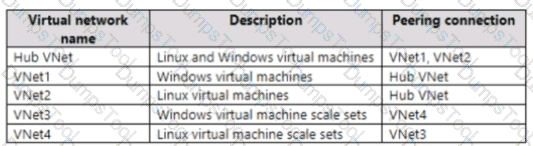
You need to recommend an Azure Bastion deployment to provide secure remote access to all the virtual machines. Based on the virtual network design, how many Azure Bastion subnets are required?
Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. The subscription contains 500 devices that are enrolled in Microsoft Intune. The subscription contains 500 users that connect to external software as a service (SaaS) apps by using the devices.
You need to implement a solution that meets the following requirements:
• Allows user access to SaaS apps that Microsoft has identified as low risk.
• Blocks user access to Saas apps that Microsoft has identified as high risk.
Solution: From Microsoft Defender for Cloud Apps, you configure SaaS security posture management (SSPM) and create an access policy.
Does this meet the goal?
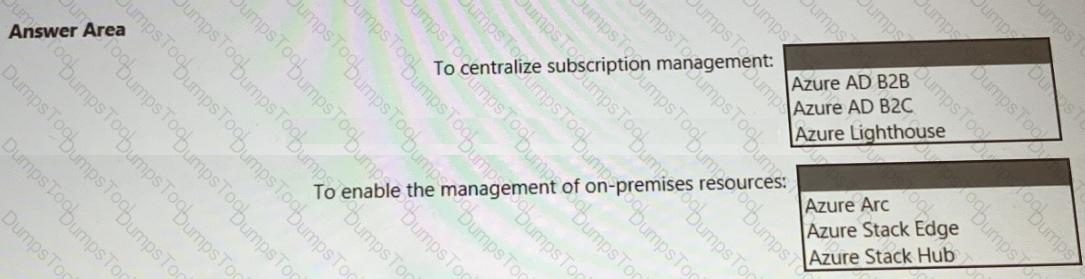
You are designing a privileged access strategy for a company named Contoso, Ltd. and its partner company named Fabrikam, Inc. Contoso has a Microsoft Entra tenant named contoso.com. Fabrikam has a Microsoft Entra tenant named fabrikam.com. Users at Fabrikam must access the resources in contoso.com.
You need to provide the Fabrikam users with access to the Contoso resources by using access packages. The solution must meet the following requirements:
• Ensure that the Fabrikam users can use the Contoso access packages without explicitly creating guest accounts in contoso.com.
• Allow non-administrative users in contoso.com to create the access packages.
What should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You have an Azure SQL database named DB1 that contains customer information.
A team of database administrators has full access to DB1.
To address customer inquiries, operators in the customer service department use a custom web app named App1 to view the customer information.
You need to design a security strategy for D81. The solution must meet the following requirements:
• When the database administrators access DB1 by using SQL management tools, they must be prevented from viewing the content of the Credit Card attribute of each customer record.
• When the operators view customer records in App1, they must view only the last four digits of the Credit Card attribute.
What should you include in the design? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

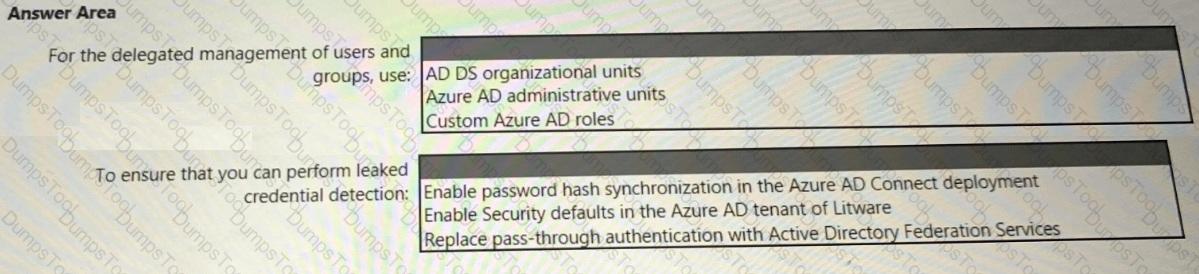
Your on-premises network contains an Active Directory Domain Services (AD DS) domain named corpxontoso.com and an AD DS-integrated application named App1.
Your perimeter network contains a server named Server1 that runs Windows Server.
You have a Microsoft Entra tenant named contoso.com that syncs with corp.contoso.com.
You plan to implement a security solution that will include the following configurations:
• Manage access to App1 by using Microsoft Entra Private Access.
• Deploy a Microsoft Entra application proxy connector to Server1.
• Implement single sign-on (SSO) for App1 by using Kerberos constrained delegation.
• For Server1, configure the following rules in Windows Defender Firewall with Advanced Security:
o Rule1: Allow TCP 443 inbound from a designated set of Azure URLs.
o Rule2: Allow TCP 443 outbound to a designated set of Azure URLs.
o Rule3: Allow TCP 80 outbound to a designated set of Azure URLs.
o Rule4: Allow TCP 389 outbound to the domain controllers on corp.contoso.com.
You need to maximize security for the planned implementation. The solution must minimize the impact on the connector.
Which rule should you remove?
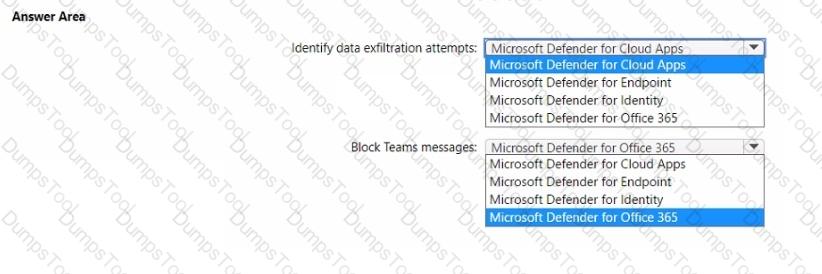
You have a Microsoft 365 tenant.
You need to recommend a Microsoft 365 Defender solution to enhance security for the tenant. The solution must meet the following requirements:
• Identify users that are downloading an unusually high number of files from Microsoft SharePoint Online sites and are possibly involved in a data exfiltration attempt.
• Block Microsoft Teams messages that contain potentially malicious content by using zero-hour auto purge (ZAP).
What should you recommend for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.