You need to ensure that all the sales department users can authenticate successfully during Project1and Project2.
Which authentication strategy should you implement for the pilot projects?
You have a Microsoft 365 subscription that uses an Azure Directory (Azure AD) tenant named Contoso.com. The tenant contains the users shown in the following table.
You add another user named user5 to the User administrator role.
You need to identify which management tasks User5 can perform.
Which two tasks should you identify? Each correct answer presents a complete solution.
You are evaluating the required processes for Project1.
You need to recommend which DNS record must be created before you begin the project.
Which DNS record should you recommend?
You have a Microsoft 365 tenant that contains 300 users.
The users have Domestic and International Calling Plan licenses.
What is the maximum user phone numbers and toll-free service phone numbers can you acquire? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

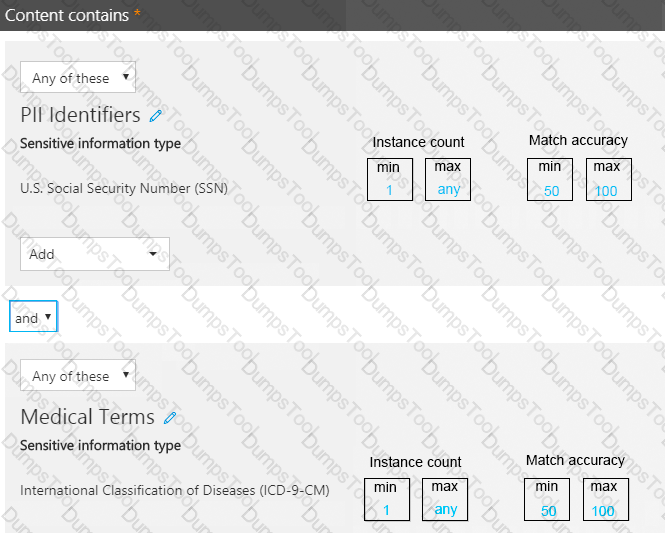
You have a data loss prevention (DLP) policy.
You need to increase the likelihood that the DLP policy will apply to data that contains medical terms from the International Classification of Diseases (ICD-9-CM). The solution must minimize the number of false positives.
Which two settings should you modify? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
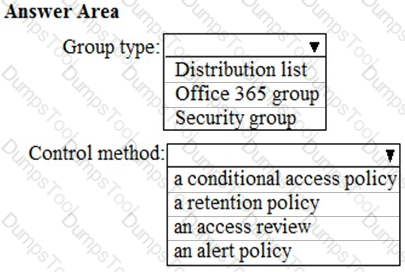
You need to create the UserLicenses group. The solution must meet the security requirements.
Which group type and control method should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has a Microsoft Office 365 tenant.
You suspect that several Office 365 features were recently updated.
You need to view a list of the features that were recently updated in the tenant.
Solution: You use Monitoring and reports from the Compliance admin center.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
* Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
* User passwords must be 10 characters or more.
Solution: Implement pass-through authentication and modify the password settings from the Default Domain Policy in Active Directory.
Does this meet the goal?
You need to prepare the environment for Project1.
You create the Microsoft 365 tenant.
Which three actions should you perform in sequence next? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You need to meet the application requirements for the Office 365 ProPlus applications.
You create an XML files that contains the following settings.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

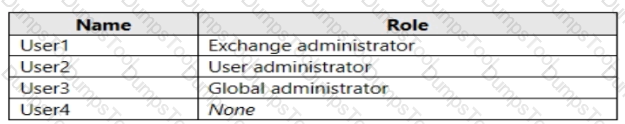
You have a Microsoft 365 subscription that contains the users shown in the following table.
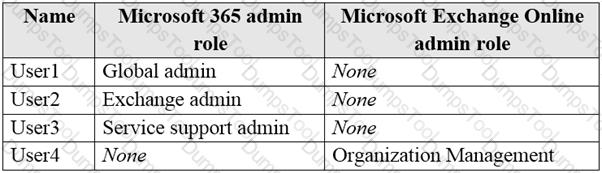
You plan to use Exchange Online to manage email for a DNS domain.
An administrator adds the DNS domain to the subscription.
The DNS domain has a status of incomplete setup.
You need to identify which user can complete the setup of the DNS domain. The solution must use the principle of least privilege.
Which user should you identify?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a hybrid deployment of Microsoft 365 that contains the objects shown in the following table.

Azure AD Connect has the following settings:
You need to add User2 to Group 2.
Solution: From Azure PowerShell, you run the Set-AzureADGroup cmdlet.
Does this meet the goal?
You have a Microsoft 365 tenant that contains a Microsoft SharePoint Online site named Projects. You need to get a list of documents in the Documents library by using the Microsoft Graph API. How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Your network contains an on-premises Active Directory domain.
You have a Microsoft 365 subscription.
You implement a directory synchronization solution that uses pass-through authentication.
You configure Microsoft Azure Active Directory (Azure AD) smart lockout as shown in the following exhibit.
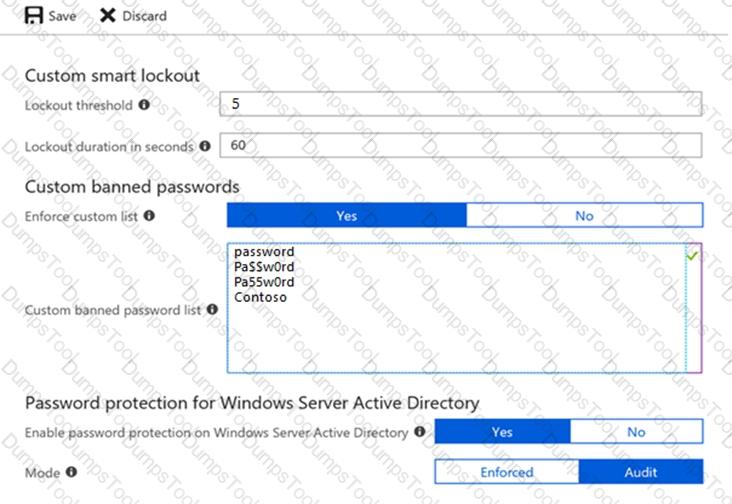
You discover that Active Directory users can use the passwords in the custom banned passwords list.
You need to ensure that banned passwords are effective for all users.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You view the Service health Overview as shown in the following exhibit.

You need to ensure that a user named User1 can view the advisories to investigate service health issues. Which role should you assign to User1?
You have a Microsoft 365 FS subscription that uses Microsoft Intune.
You have the devices shown in the following table.
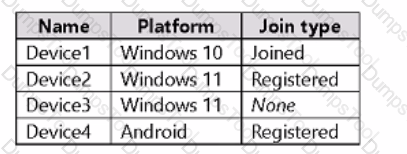
You plan to use Endpoint analytics to monitor device health and user experience.
Which devices can you monitor?
This question requires that you evaluate the underlined text to determine if it is correct-In Microsoft Word on Windows, before you can sideload a Microsoft Office Add-in, you must firs: upload the manifest to Microsoft OneDrive instructions: Review the underlined text. If it makes the statement correct select "No change is needed," If the statement is incorrect select the answer choice that makes the statement correct
You have a Microsoft 365 tenant.
You have a line-of-business application named App1 that users access by using the My Apps portal.
After some recent security breaches, you implement a conditional access policy for App1 that uses Conditional Access App Control.
You need to be alerted by email if impossible travel is detected for a user of App1. The solution must ensure
that alerts are generated for App1 only.
What should you do?
You have a Microsoft 365 subscription that contains a user named User1.
You need to ensure that User1 receives Microsoft 365 feature and service updates before the updates are
released to all users.
What should you do in the Microsoft 365 admin center?
Your network contains an on-premises Active Directory domain.
Your company has a security policy that prevents additional software from being installed on domain
controllers.
You need to monitor a domain controller by using Microsoft Azure Advanced Threat Protection (ATP).
What should you do? More than once choice may achieve the goal. Select the BEST answer.
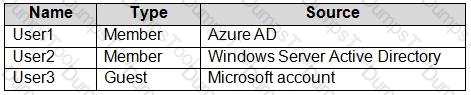
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.

Multi-factor authentication (MFA) is configured to use 131.107.50/24 for trusted IPs.
The tenant contains the named locations shown in the following table.
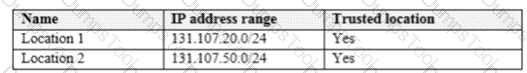
You create a conditional access policy that has the following configurations:
For each of the following statements, select Yes if the statement is true. otherwise, select No.
NOTE: Each correct selection is worth one point.

You have an on-premises Microsoft SharePoint Server 2016 environment.
You create a Microsoft 365 tenant.
You need to migrate some of the SharePoint sites to SharePoint Online. The solution must meet the following requirements:
When users search for a document by using keywords, the results must include online and on-premises results.
From the SharePoint Hybrid Configuration Wizard, you select the following features:
Which two requirements are met by using the SharePoint Hybrid Configuration Wizard features? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You need to add additional onmicrosoft.com domains to the subscription. The additional domains must be assignable as email addresses for users.
What is the maximum number of onmicrosoft.com domains the subscription can contain?
Your company uses a legacy on-premises LDAP directory that contains 100 users.
The company purchases a Microsoft 365 subscription.
You need to import the 100 users into Microsoft 365 by using the Microsoft 365 admin center.
Which type of file should you use and which properties are required? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a hybrid deployment of Microsoft 365 and an Azure Active Directory (Azure AD) tenant. The tenant contains the users shown in the following table.
Password protection in Azure AD is configured as shown in the following exhibit.

Which users will be prevented from using the word “Contoso” as part of their password?
You have a Microsoft 365 subscription
You have an Azure AD tenant that contains the users shown in the following table.
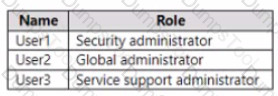
You configure Tenant properties as shown in the following exhibit

Which users will be contacted by Microsoft if the tenant experiences a data breach?
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@M365x981607.onmicrosoft.com
Microsoft 365 Password: *yfLo7Ir2&y-
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 10811525
You need to prevent the users in your organization from establishing voice calls from Microsoft Skype for Business to external Skype users.
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@LODSe426243.onmicrosoft.com
Microsoft 365 Password: 3&YWyjse-6-d
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 10887751
You plan to provide an external user named fabrikamuser@fabrikam.com with access to several resources in your Microsoft 365 tenant.
You need to ensure that the external user can be added to Office 365 groups.
You have a Microsoft 365 subscription that contains the domains shown in the following exhibit.

Which domain name suffixes can you use when you create users?
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online
In the mailbox of a user named User, you need to preserve a copy of all the email messages that contain the word ProjectX.
What should you do first?
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
An external user has a Microsoft account that uses an email address of user1@outlook.com.
An administrator named Admin1 attempts to create a user account for the external user and receives the error message shown in the following exhibit.

You need to ensure that Admin1 can add the user.
What should you do from the Azure Active Directory admin center?
You have a Microsoft 365 subscription.
All users are assigned Microsoft 365 Apps for enterprise licenses.
You need to ensure that reports display the names of users that have activated Microsoft 365 apps and on how many devices
What should you modify in the Microsoft 365 admin center?
You need to configure Microsoft Teams to support the technical requirements tor collaborating with A. Datum What should you configure in the Microsoft Teams admin center?
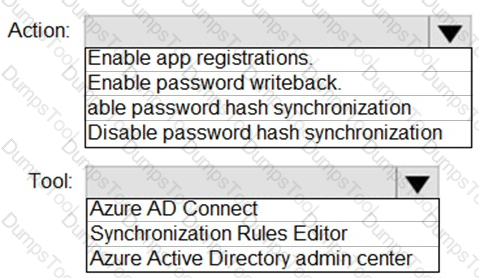
You need to ensure that Admin4 can use SSPR.
Which tool should you use, and which action should you perform? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
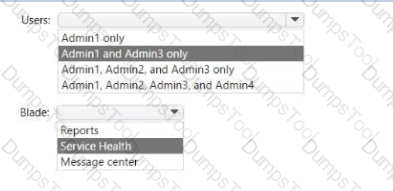
You need to ensure that the Microsoft 365 incidents and advisories are reviewed monthly.
Which users can review the incidents and advisories, and which blade should the users use? To answer, select the appropriate options in the answer area
NOTE: Each correct selection is worth one pant
You are evaluating the use of multi-factor authentication (MFA).
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Security Reader role.
From the Exchange admin center, you assign User2 the Help Desk role.
Does this meet the goal?
You need to configure just in time access to meet the technical requirements.
What should you use?
You need to configure HRApp to enable users to search for specific jobs by using chat in Microsoft Teams. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You need to provide users with access to SalesApp. The solution must meet the technical requirements What should you include in the solution?
You need to recommend which API object the SharePoint Framework (SPFx) intranet components will use to access the research department s project management solution. What should you recommend?
You need to ensure that users can initiate private conversations with HRBot. The solution must meet the technical requirements for HRApp. How should you configure the HRApp manifest?
You need to recommend the development environment and tools for the development of SalesApp.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to modify the HRApp manifest to provide a tab that supports querying the third-party HR system.
Which section of the manifest should you modify, and which value should you set as the scope? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
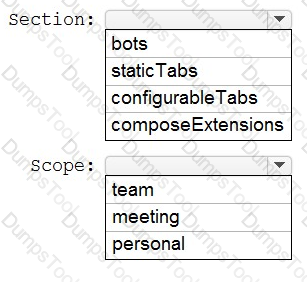
You need to recommend which type of Office Add-in must be used for SalesApp.
What should you recommend?
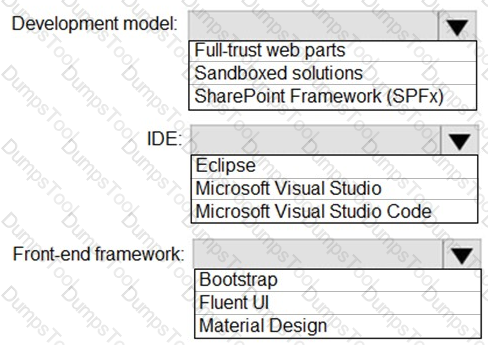
You need to recommend the development environment and tools for the redesign of the research department’s SharePoint Online sites.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a model for the expense claims solution. What should you recommend?
You need to assign User2 the required roles to meet the security requirements and the technical requirements.
To which two roles should you assign User2? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Note This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Security Administrator role. From the Exchange admin center, you add User2 to the View-Only Management role.
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Security Reader role. From the Exchange admin center, you assign User2 the Compliance Management role.
Does this meet the goal?
You need to meet the security requirement for the vendors.
What should you do?
You need to meet the security requirement for the vendors.
What should you do?
You need to Add the custom domain name* to Office 36S K> support the planned changes as quickly as possible.
What should you create to verify the domain names successfully?
To which Azure AD role should you add User4 to meet the security requirement?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals- Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As m result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirement.
Solution: From the Office 36S admin center, you assign User2 the Records Management role. From the Exchange 3dmm center, you assign User2 the Help Desk role.
Does that meet the goal?
You have a Microsoft 365 tenant that contains the users shown in the following table.

Microsoft Exchange Online has the mail flow rules shown in the following table

Rule1 has the following settings:

You need to meet the technical requirements for the user licenses.
Which two properties should you configure for each user? To answer, select the appropriate properties in the answer area.
NOTE: Each correct selection is worth one point.
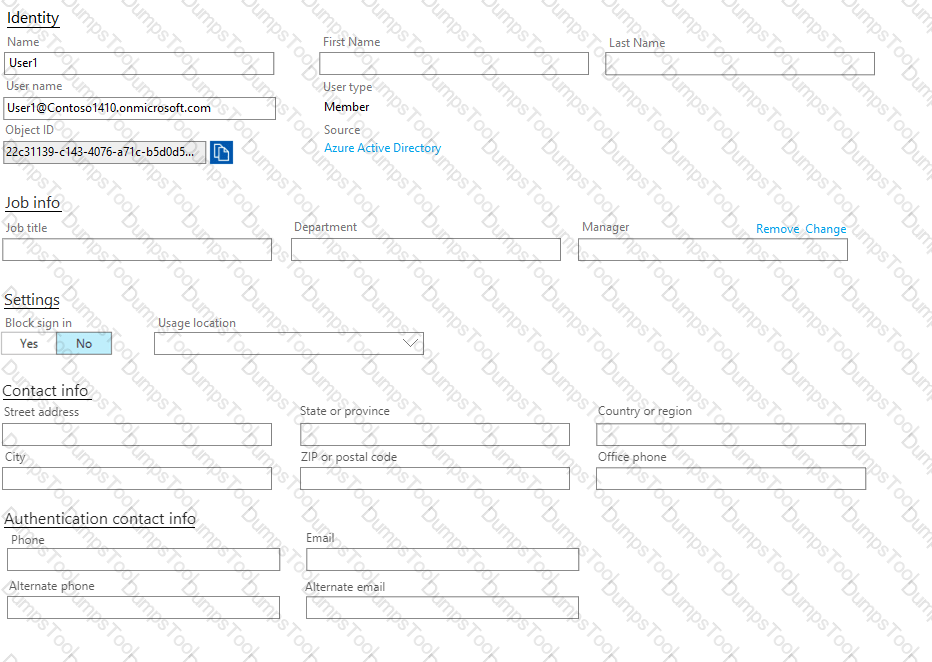
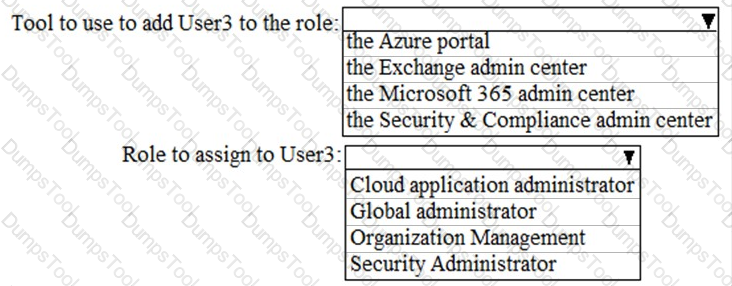
You need to meet the security requirements for User3. The solution must meet the technical requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.