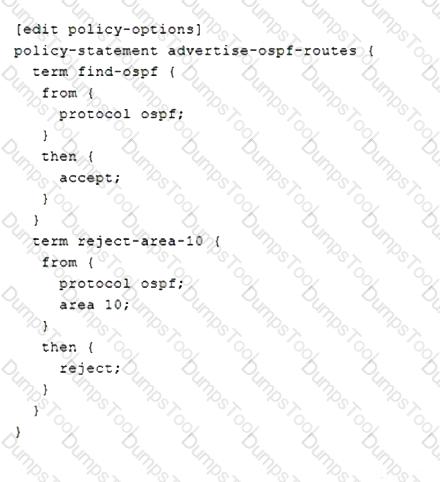
You recently committed a change to a router to reject OSPF routes sourced from area 10. However, you are still seeing area 10 routes in the routing table.
Referring to the exhibit, which statement is correct?
You are deploying IP phones in your enterprise network that must receive their power through their Ethernet connection. You are using your EX Series switch's PoE ports that support IEEE 802.3af.
In this scenario, what is the maximum amount of power allocated to each interface?
Your organization has recently acquired another company. You must carry all of the company’s existing VLANs across the corporate backbone to the existing branch locations without changing addressing and with minimal configuration.
Which technology will accomplish this task?
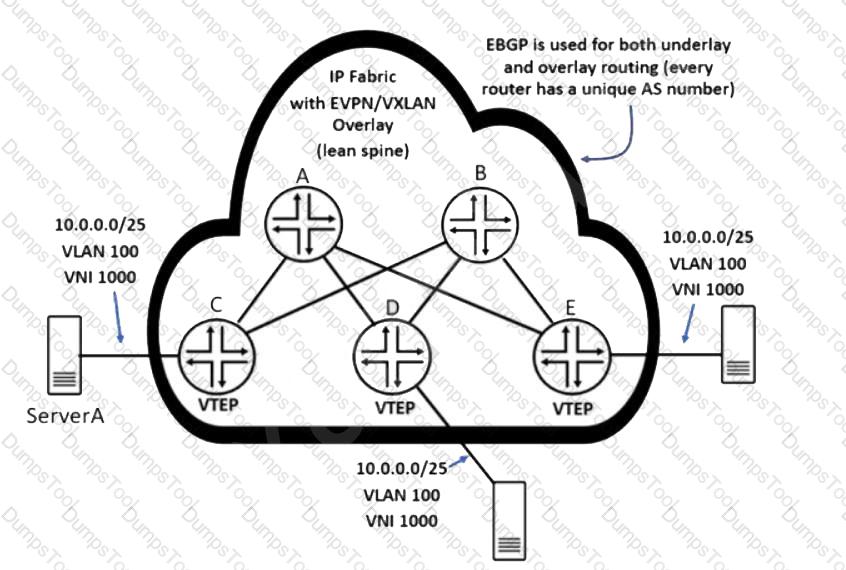
Referring to the exhibit, ServerA sends a single IP packet destined to 10.0.0.127.
Which two statements correctly describe the behavior of the resulting outbound VXLAN packets that contain the original packet destined to 10.0.0.127? (Choose two.)
Your EX Series switch has IP telephones and computers connected to a single switch port. You are considering implementing the voice VLAN feature to help with this setup.
In this scenario, which two statements are correct? (Choose two.)
A Layer 2 connection does not expend across data centers. The IP subnet in a Layer 2 domain is confined within a single data center.
Which EVPN route type is used to communicate prefixes between the data centers?
Your enterprise network uses routing instances to support multitenancy. Your Junos devices use BGP to peer to multiple BGP devices. You must ensure that load balancing is achieved within the routing instance.
Which two statements would accomplish this task? (Choose two.)
You are asked to configure 802.1X on your access ports to allow only a single device to authenticate.
In this scenario, which configuration would you use?
You are deploying new Juniper EX Series switches in a network that currently is using Cisco’s Per-VLAN spanning tree plus (PVST+) and you must provide compatibility with this environment.
Which spanning tree protocol do you deploy in this scenario?
Your enterprise network is running BGP VPNs to support multitenancy. Some of the devices with which you peer BGP do not support the VPN NLRI. You must ensure that you do not send BGP VPN routes to the remote peer.
Which two configuration steps will satisfy this requirement? (Choose two.)
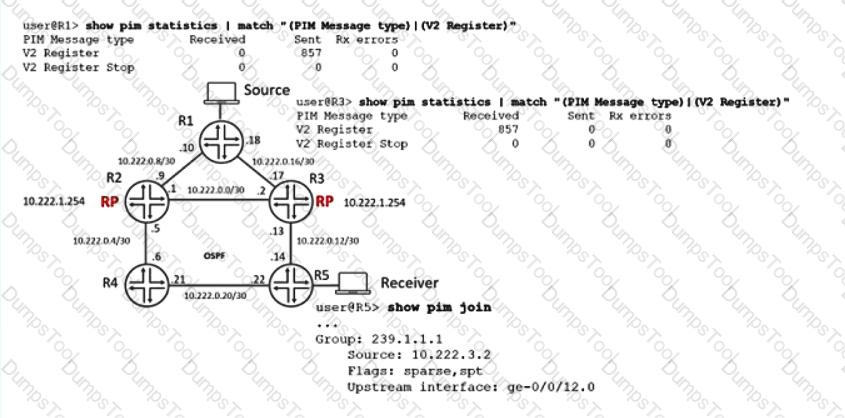
Referring to the exhibit, anycast RP is implemented to ensure multicast service availability. The source is currently sending multicast traffic using group 239.1.1.1 and R3 is receiving PIM register messages, but R2 does not have active source information.
In this scenario, what are two methods to receive the active source information on R2? (Choose two.)
Which two statements are correct about the deployment of EVPN-VXLAN on QFX Series devices? (Choose two.)