Which two statements about SRX Series device chassis clusters are correct? (Choose two.)
You need to deploy an SRX Series device in your virtual environment.
In this scenario, what are two benefits of using a CSRX? (Choose two.)
Which two statements are correct about the fab interface in a chassis cluster? (Choose two.)
Exhibit
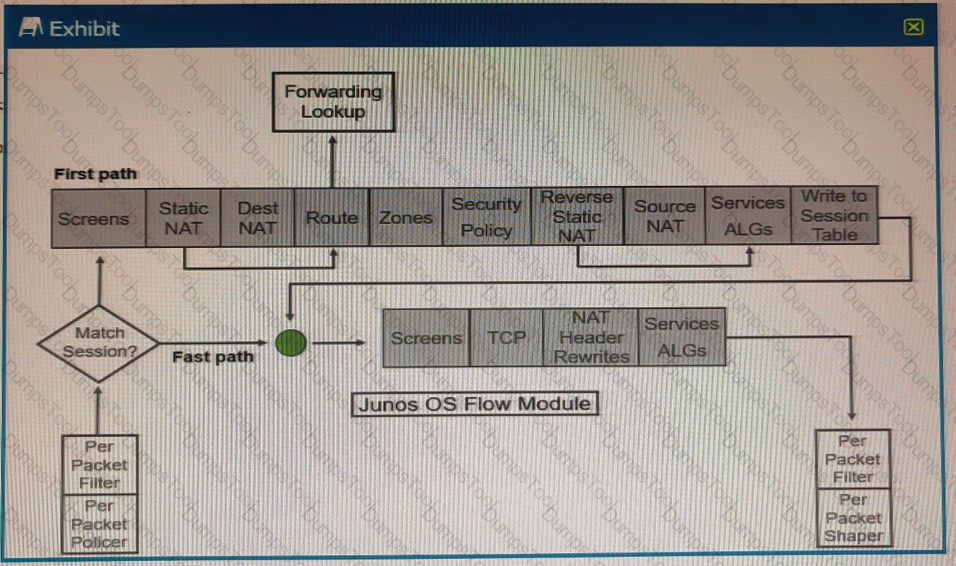
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
You want to control when cluster failovers occur.
In this scenario, which two specific parameters would you configure on an SRX Series device? (Choose two.)
While working on an SRX firewall, you execute the show security policies policy-name
Which function does this command accomplish?
Exhibit
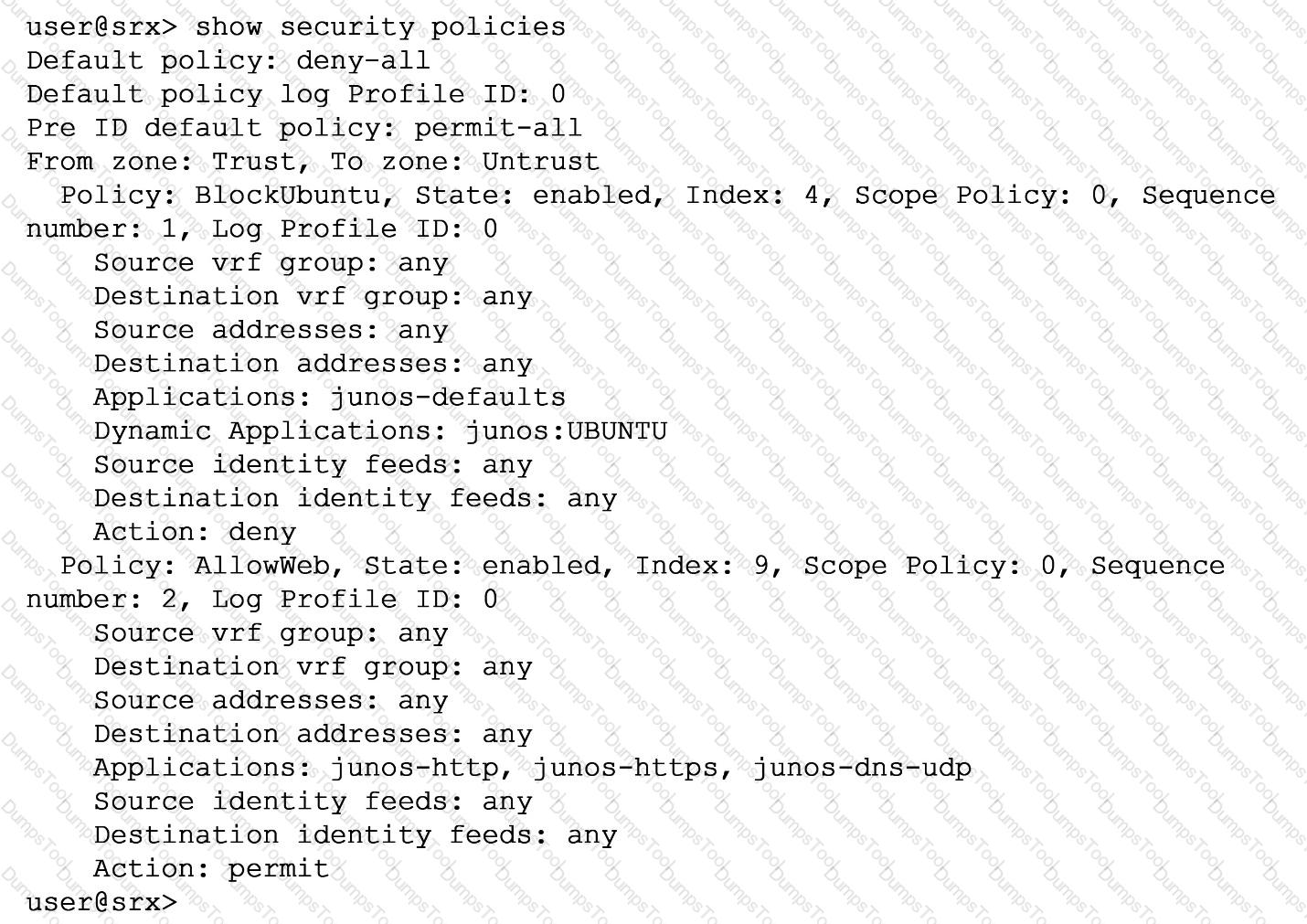
You are asked to ensure that servers running the Ubuntu OS will not be able to update automatically by blocking their access at the SRX firewall. You have configured a unified security policy named Blockuburrtu, but it is not blocking the updates to the OS.
Referring to the exhibit which statement will block the Ubuntu OS updates?
Which two statements are true about the fab interface in a chassis cluster? (Choose two.)
Your manager asks you to provide firewall and NAT services in a private cloud.
Which two solutions will fulfill the minimum requirements for this deployment? (Choose two.)
You are asked to find systems running applications that increase the risks on your network. You must ensure these systems are processed through IPS and Juniper ATP Cloud for malware and virus protection.
Which Juniper Networks solution will accomplish this task?
Which statement regarding Juniper Identity Management Service (JIMS) domain PC probes is true?
Exhibit
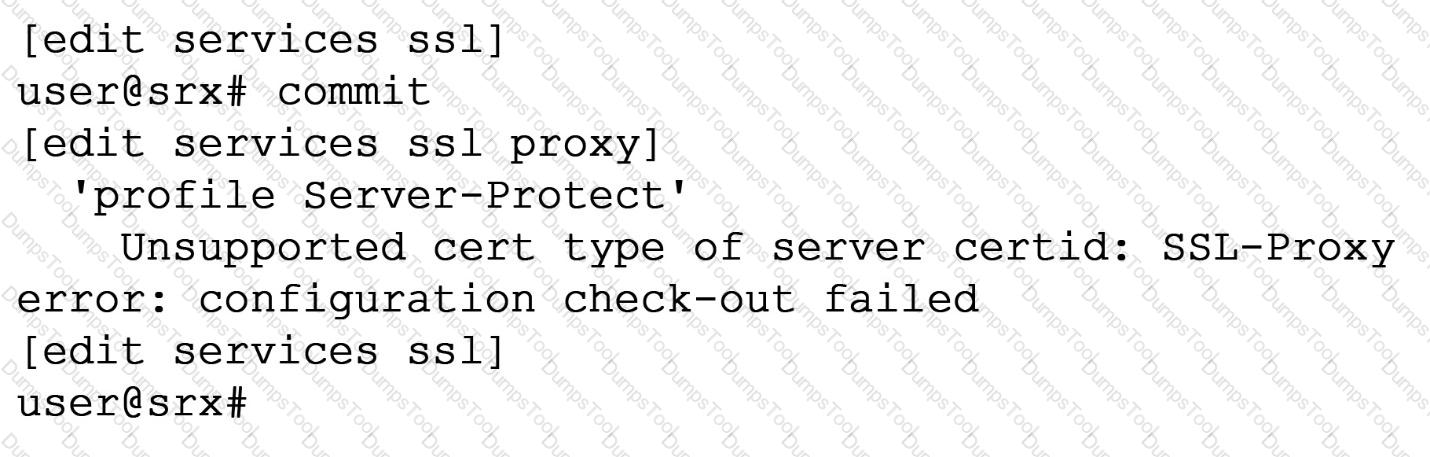
When trying to set up a server protection SSL proxy, you receive the error shown. What are two reasons for this error? (Choose two.)
You are preparing a proposal for a new customer who has submitted the following requirements for a vSRX deployment:
-- globally distributed,
-- rapid provisioning,
-- scale based on demand,
-- and low CapEx.
Which solution satisfies these requirements?
Which two statements about unified security policies are correct? (Choose two.)
What are two benefits of using a vSRX in a software-defined network? (Choose two.)
Click the Exhibit button.
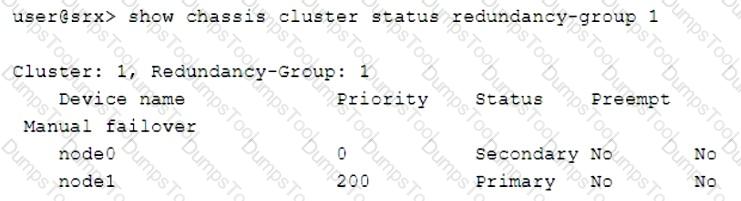
Which two statements describe the output shown in the exhibit? (Choose two.)
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
Which two statements are correct about security policy changes when using the policy rematch feature? (Choose two.)
You want to manually failover the primary Routing Engine in an SRX Series high availability cluster pair.
Which step is necessary to accomplish this task?
You are asked to create an IPS-exempt rule base to eliminate false positives from happening.
Which two configuration parameters are available to exclude traffic from being examined? (Choose two.)
Exhibit
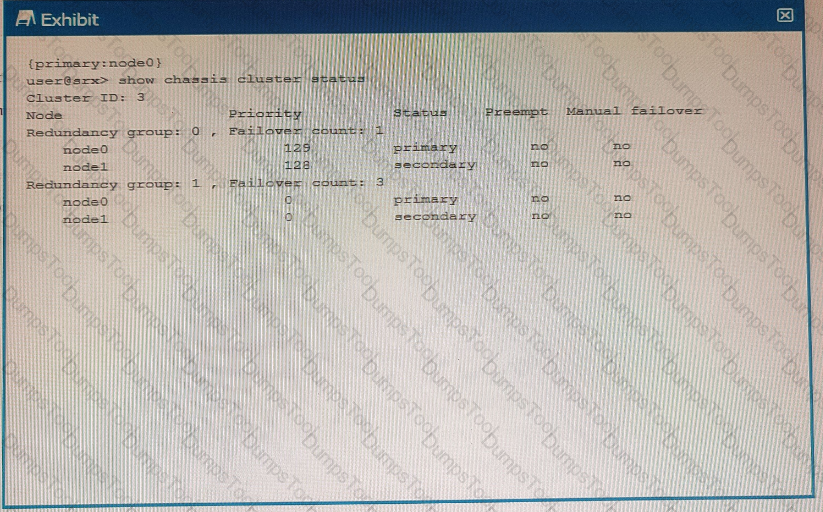
Using the information from the exhibit, which statement is correct?