Click the Exhibit button.
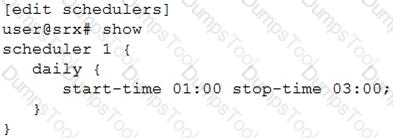
You have configured the scheduler shown in the exhibit to prevent users from accessing certain websites from 1:00 PM to 3:00 PM Monday through Friday. This policy will remain in place until further notice. When testing the policy, you determine that the websites are still accessible during the restricted times.
In this scenario, which two actions should you perform to solve the problem? (Choose two.)
Which two statements describe superflows in Juniper Secure Analytics? (Choose two.)
Which solution should you use if you want to detect known attacks using signature-based methods?
You are asked to convert two standalone SRX Series devices to a chassis cluster deployment. You must ensure that your IPsec tunnels will be compatibla with the new deployment.
In this scenario, which two interfaces should be used when binding your tunnel endpoints? (Choose two.)
You must fine tune an IPS security policy to eliminate false positives. You want to create exemptions to the normal traffic examination for specific traffic.
Which two parameters are required to accomplish this task? (Choose two.)
Click the Exhibit button.
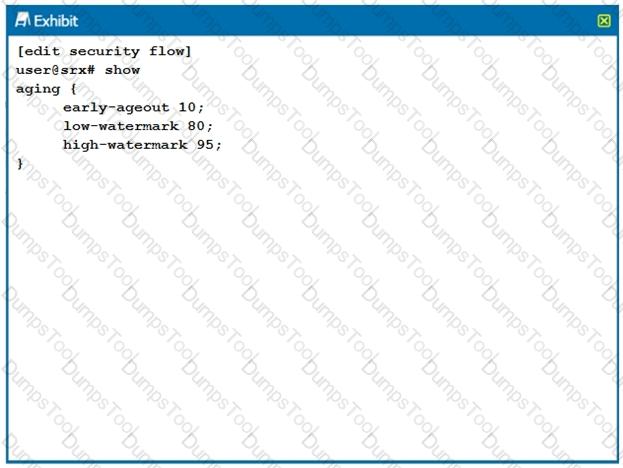
Which two statements are true about the configuration shown in the exhibit? (Choose two.)
What information does JIMS collect from domain event log sources? (Choose two.)