Which of the following statements regarding MPLS label encapsulation format are true? (Multiple Choice)
Which of the following statements regarding Network Address and Port Translation (NAFT) and No Port Translation (No-PAT) is true?
MPLS is a label forwarding technology, Which of the following MPLS statements is false?
For interzone packet filtering, which of following traffic is not transmitted in the outbound direction?
A 32-bit MPLS header consists of a 20-bit label used for packet forwarding; A 3-bit EXP field that identifies the IP packet priority; A 1-bit bottom-of-stack flag that identifies the last label; And an 8-bitTTL field. Which statement regarding the TTL field is true?
On the traditional IP network, the BE mode cannot distinguish communication types or meet requirements of applications. The emergence of QoS technology is committed to solving this problem.
With the development of the ASIC technology, MPLS is no longer show obvious advantages in improving the forwarding speed. However, MPLS is still widely used causes for what? (Multiple Choice)
In the SDN network architecture, which device is used to calculate the path and deliver the flow table?
A DDoS attack indicates that an attacker controls many botnet hosts to send a large number of constructed attack packets. As a result, the attacked device rejects request of authorized users.
When hosts and servers in the same zone communicate with each other, NAT is not required.
DHCP snooping is a security feature that can be used to defend against various attacks, including: (Multiple Choice)
BFD (bidirectional forwarding detection) is a fast detection technology but is complex, It needs to be supported by special devices.
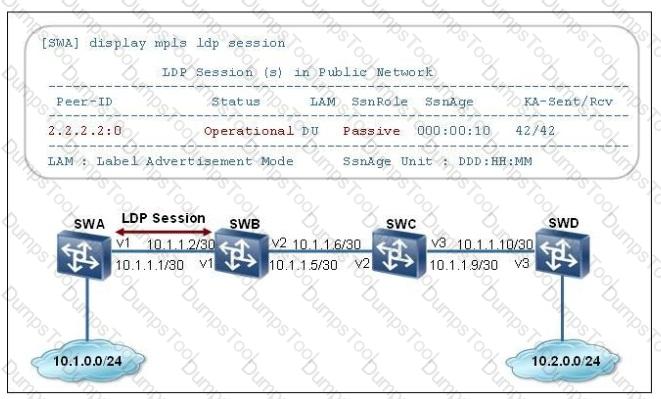
The following figure shows a network running MPLS and LDP session information displayed on SWA. Which of the following statements is false? (Multiple Choice)
When the IP address of an interface on a firewall is pinged/ ping packets are processed by the internal module of the firewall but are not forwarded,
Which of the following statements regarding the firewall interzone security policy is true?
During QoS deployment, you can use PBR to perform traffic classification and marking. The ACL rule (source IP address, destination IP address, protocol type, and port number) and packet length can be used for classification. The DSCP priority or IP precedence of data packets can be modified.
MPLS is short for Multiprotocol Label Switching, so the core technology of MPLS is label switching.
MPLS forwards data packets based on labels. How is IP packets passing through the MPLS domain forwarded if they do not carry any label?
A flow mirroring port can transmit the specified service flows on the mirroring port to the monitoring device for analysis and monitoring.
Which of the following are label distribution control modes in the MPLS system? (Multiple Choice)
FIFO can allocates different weights to different services and has good control of delay and jitter.
The LDP session establishment process will go through the opensent status. Which state will the opensent state change to after the device receives an Initialization message and sends a Keepalive message?
Which of the following statements regarding different types of firewalls is false?
When configuring source NAT with no-pat configuration parameters, which of the following statements is true?
Information security technology problems are mainly technical problems. Information security work can be done well only by using latest technologies and deploying high-performance devices
Which remote alarm notification modes are supported by eSight? (Multiple Choice)
Which of the following statements regarding Huawei eSight network management software is false?
Which of the following statements regarding buffer overflow attacks is false?
SDN technology advocate layered open architecture, then which organization advocate and defines the centralized architecture and OpenFlow?
Which of the following statements regarding United Security of the Agile Controller are true? (Multiple Choice)
In most cases, an IP address that is dynamically assigned by a DHCP server has a lease. Which of the following statements regarding the IP address lease is false?
Which of the following statements regarding the commands used by a PC to obtain an IP address from the DHCP server are true? (Multiple Choice)