Refer to the exhibit.
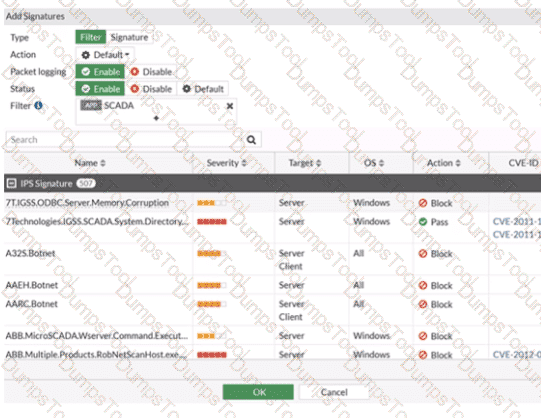
The IPS profile is added on all of the security policies on FortiGate.
For an OT network, which statement of the IPS profile is true?
Refer to the exhibit
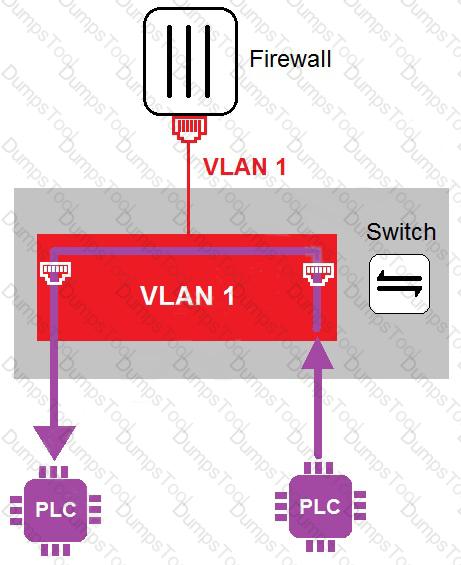
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
When you create a user or host profile, which three criteria can you use? (Choose three.)
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
What is the primary objective of implementing SD-WAN in operational technology (OT) networks'?
As an OT network administrator you are managing three FortiGate devices that each protect different levels on the Purdue model To increase traffic visibility you are required to implement additional security measures to detect protocols from PLCs
Which security sensor must you implement to detect protocols on the OT network?
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
Refer to the exhibit.
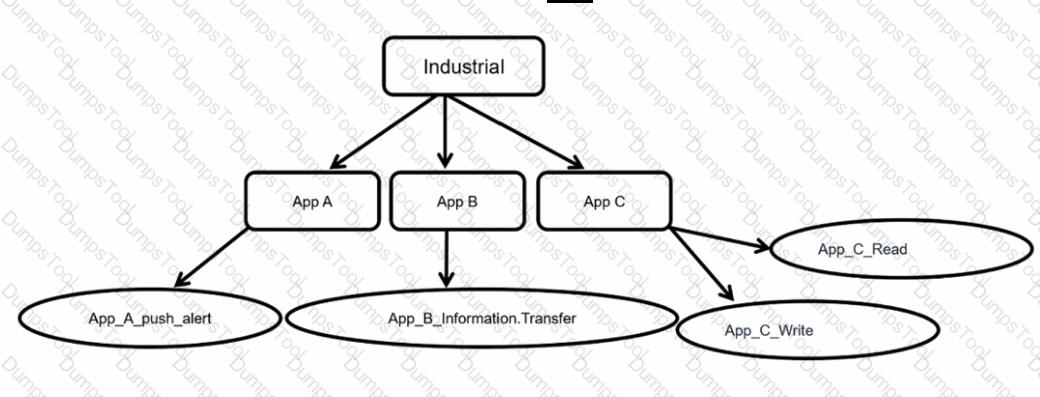
Which statement is true about application control inspection?
Refer to the exhibit.
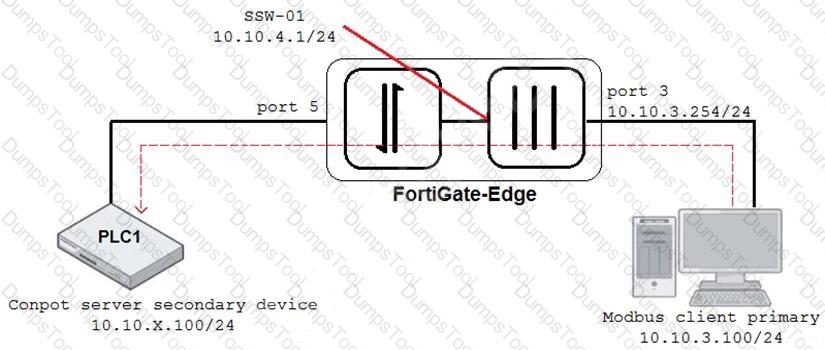
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
Which two statements are true when you deploy FortiGate as an offline IDS? (Choose two.)
An OT supervisor needs to protect their network by implementing security with an industrial signature database on the FortiGate device.
Which statement about the industrial signature database on FortiGate is true?