An administrator wanted to configure an IPS sensor to block traffic that triggers the signature set number of times during a specific time period. How can the administrator achieve the objective?
Refer to the exhibit.
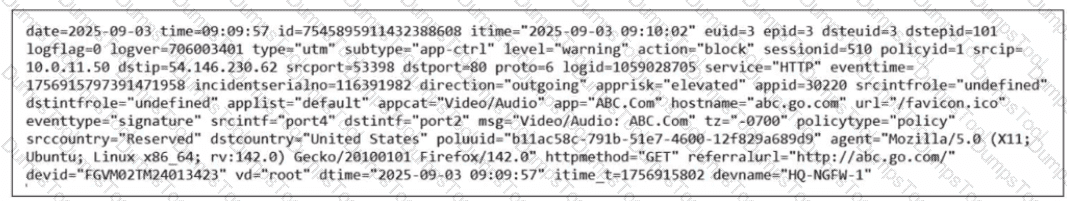
Which two ways can you view the log messages shown in the exhibit? (Choose two.)
Refer to the exhibits.
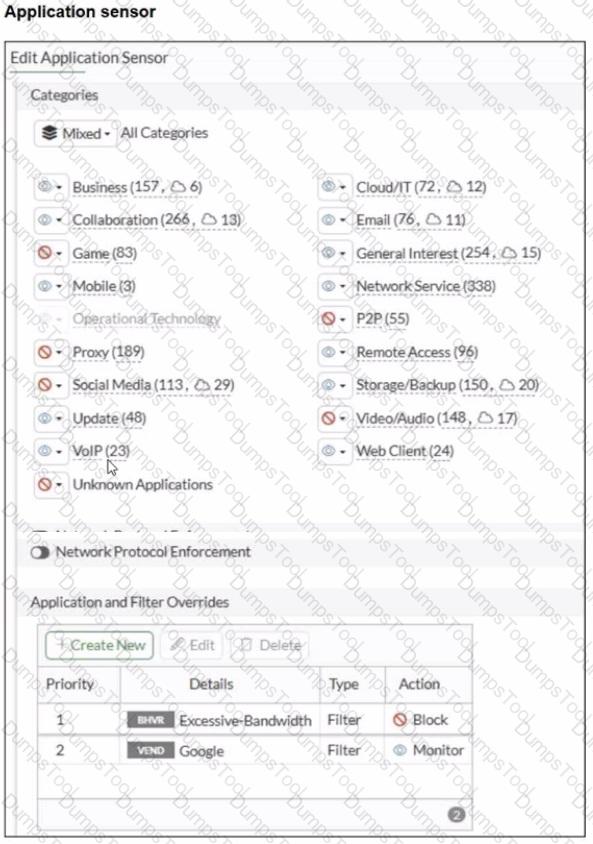
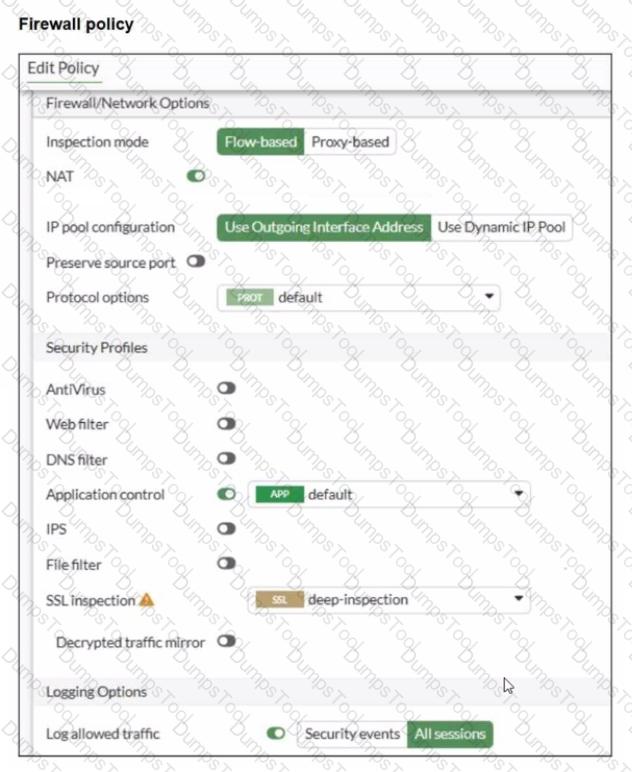
You have implemented the application sensor and the corresponding firewall policy as shown in the exhibits.
Which two factors can you observe from these configurations? (Choose two.)
Refer to the exhibit.
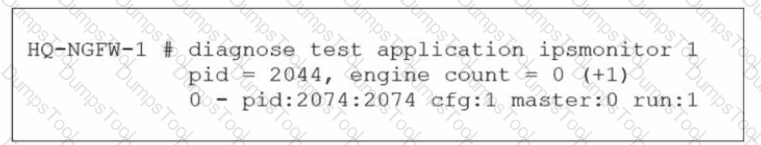
As an administrator you have created an IPS profile, but it is not performing as expected. While testing you got the output as shown in the exhibit What could be the possible reason of the diagnose output shown in the exhibit?
Refer to the exhibits.
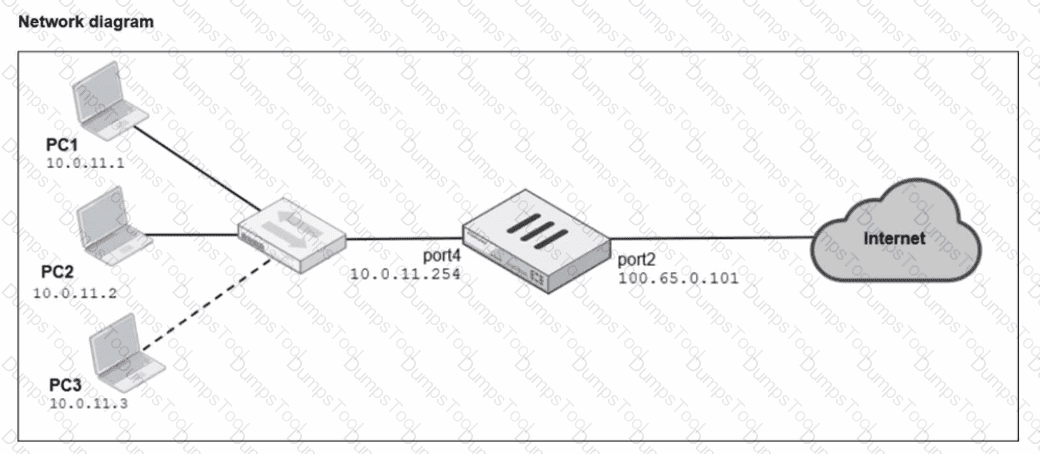
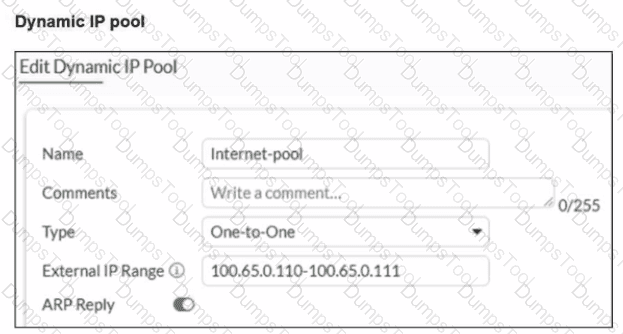
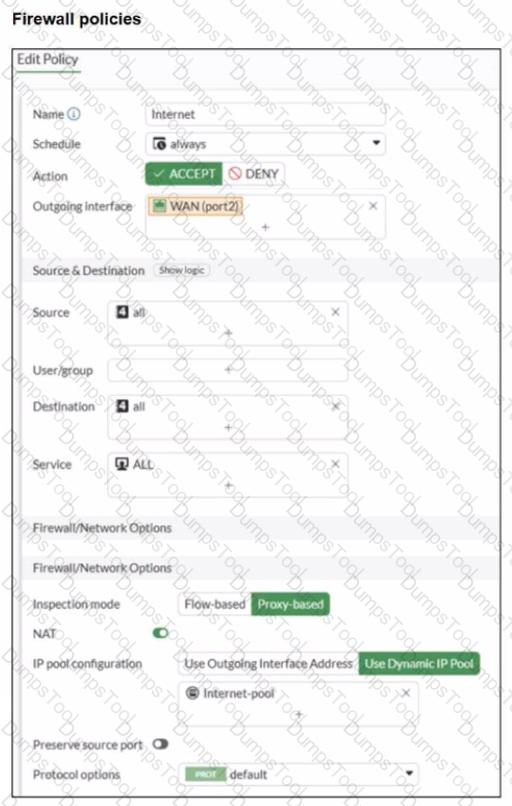
A diagram of a FortiGate device connected to the network, as well as the firewall policy and IP pool configuration on the FortiGate device are shown.
Two PCs. PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.
Based on the information shown in the exhibit, which two configuration options can the administrator use to fix the connectivity issue for PC3? (Choose two.)
An administrator manages a FortiGate model that supports NTurbo
How does NTurbo acceleration enhance antivirus performance?
Refer to the exhibit.
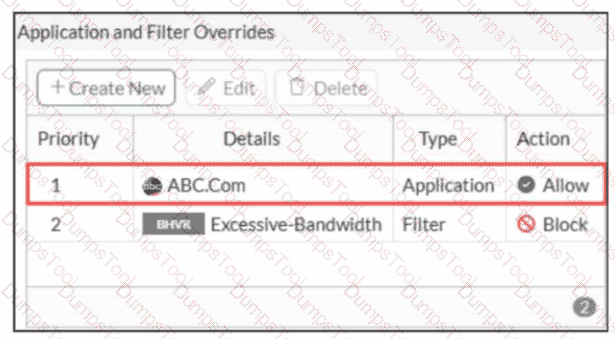
An administrator has configured an Application Overrides for the ABC.Com application signature and set the Action to Allow This application control profile is then applied to a firewall policy that is scanning all outbound traffic. Logging is enabled in the firewall policy. To test the configuration, the administrator accessed the ABC.Com web site several times.
Why are there no logs generated under security logs for ABC.Com?
How does FortiExtender connect to FortiSASE in a site-based, remote internet access method?
A new administrator is configuring FSSO authentication on FortiGate using DC Agent Mode. Which step is not part of the expected process?
Refer to the exhibit.
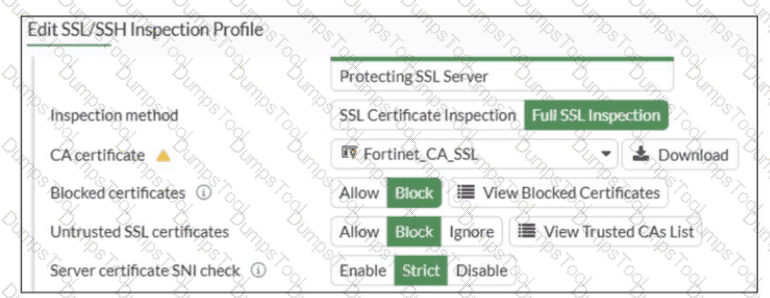
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
Refer to the exhibit.

Based on this partial configuration, what are the two possible outcomes when FortiGate enters conserve mode? (Choose two.)
What are two features of FortiGate FSSO agentless polling mode? (Choose two.)