What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
Which type of logs on FortiGate record information about traffic directly to and from the FortiGate management IP addresses?
Which security feature does FortiGate provide to protect servers located in the internal networks from attacks such as SQL injections?
Refer to the exhibit.
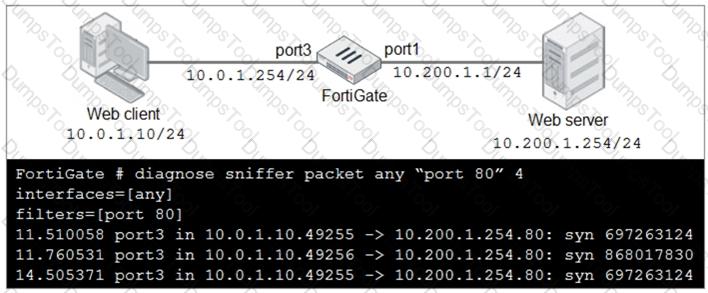
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output as shown in the exhibit.
What should the administrator do next to troubleshoot the problem?
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
Which two statements about IPsec authentication on FortiGate are correct? (Choose two.)
Refer to the exhibit, which contains a static route configuration.
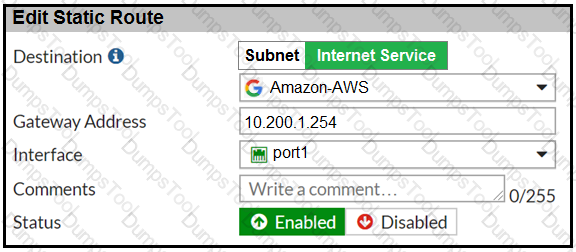
An administrator created a static route for Amazon Web Services.
What CLI command must the administrator use to view the route?
Which Security rating scorecard helps identify configuration weakness and best practice violations in your network?
When browsing to an internal web server using a web-mode SSL VPN bookmark, which IP address is used as the source of the HTTP request?
Refer to the exhibits.
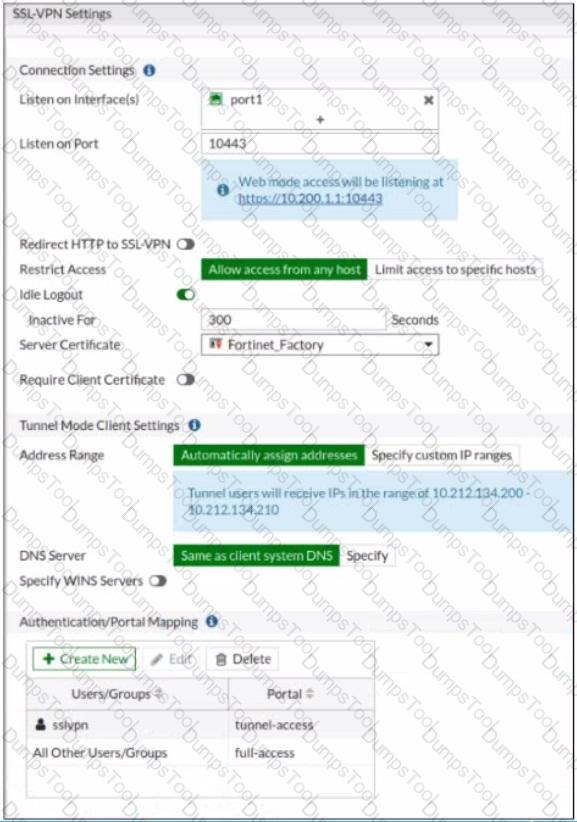
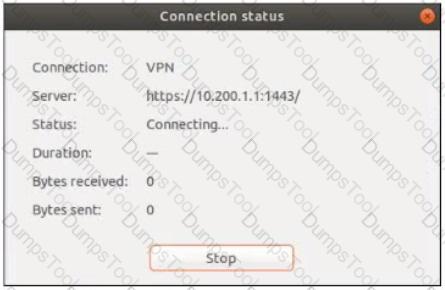
The SSL VPN connection fails when a user attempts to connect to it. What should the user do to successfully connect to SSL VPN?
Refer to the exhibit.
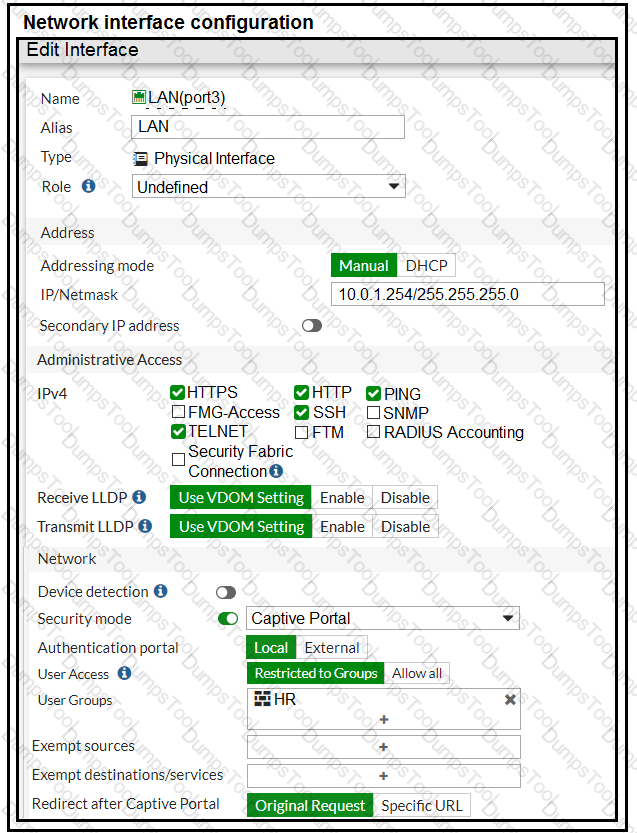
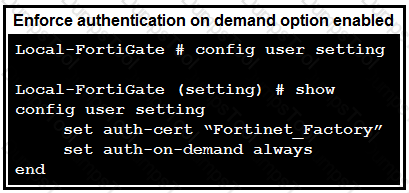
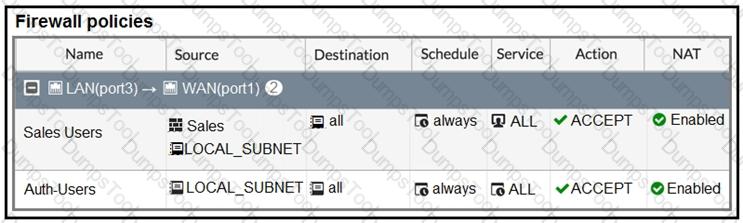
The exhibit contains a network interface configuration, firewall policies, and a CLI console configuration.
How will FortiGate handle user authentication for traffic that arrives on the LAN interface?
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
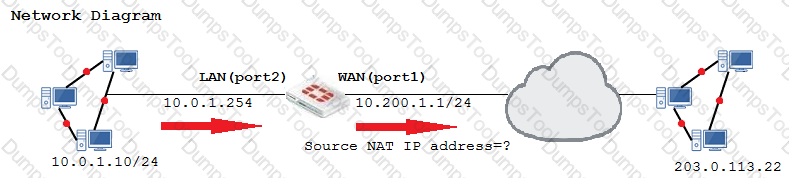
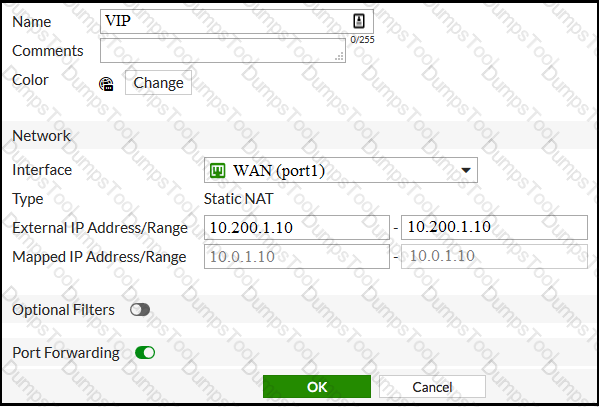
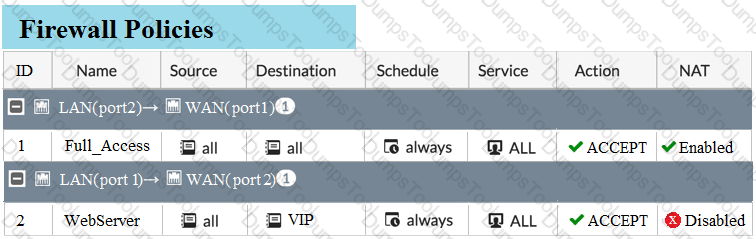
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
In an explicit proxy setup, where is the authentication method and database configured?
Which of the following conditions must be met in order for a web browser to trust a web server certificate signed by a third-party CA?
Refer to the exhibits.
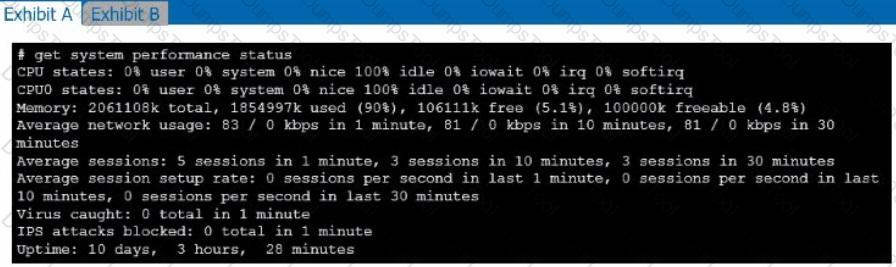
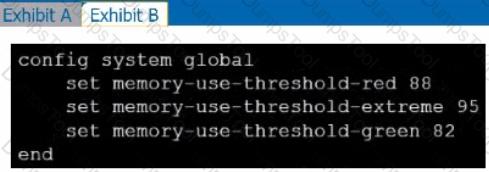
Exhibit A shows system performance output. Exhibit B shows a FortiGate configured with the default configuration of high memory usage thresholds. Based on the system performance output, which two statements are correct? (Choose two.)
An administrator wants to configure Dead Peer Detection (DPD) on IPSEC VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when no traffic is observed in the tunnel.
Which DPD mode on FortiGate will meet the above requirement?
Refer to the exhibit, which contains a session diagnostic output.
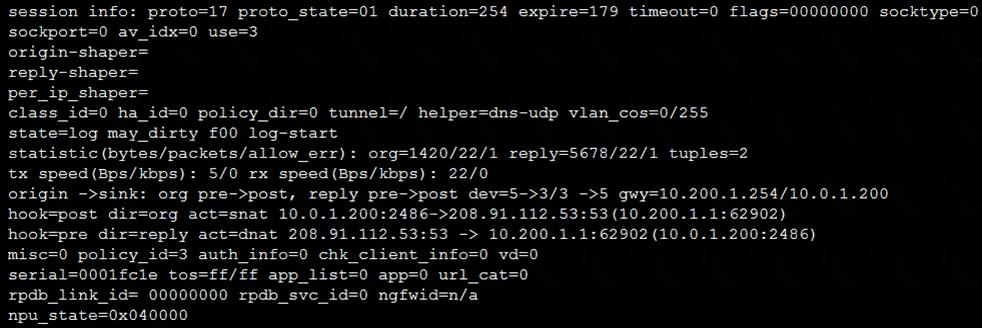
Which statement is true about the session diagnostic output?