6
Which three options are the remote log storage options you can configure on FortiGate? (Choose three.)
If Internet Service is already selected as Destination in a firewall policy, which other configuration object can be selected for the Destination field of a firewall policy?
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 fails to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
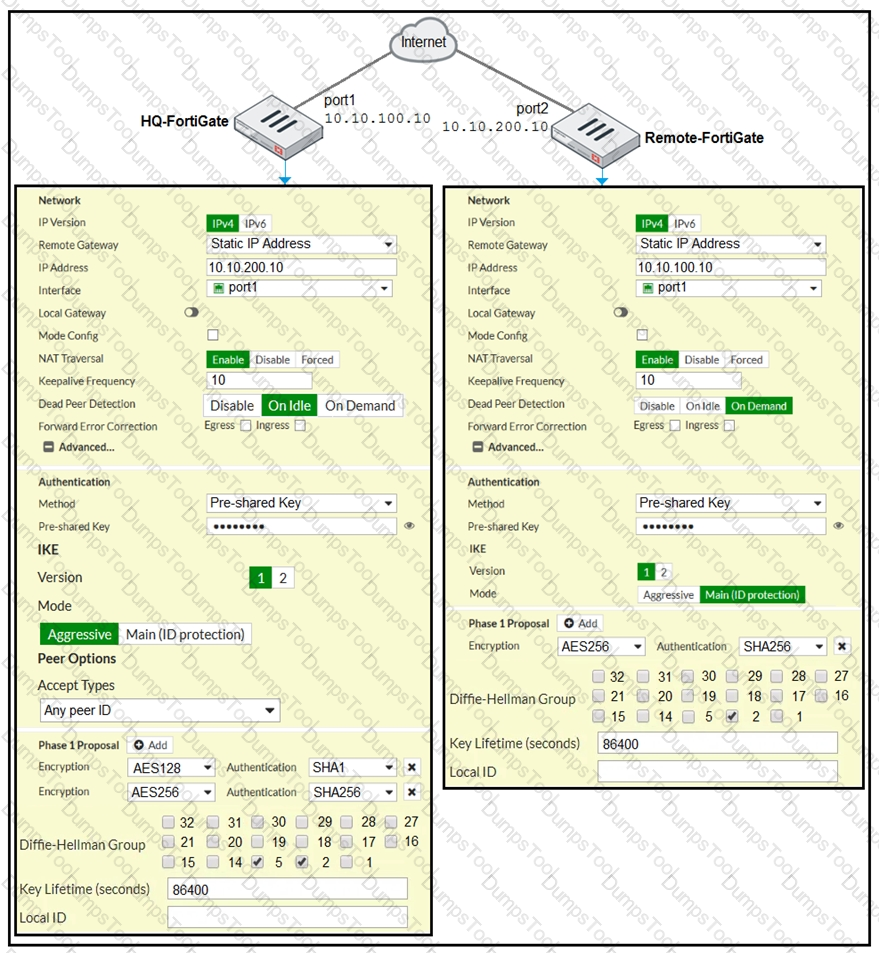
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes will bring phase 1 up? (Choose two.)
94
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
Refer to the exhibit.
The exhibit shows the output of a diagnose command.
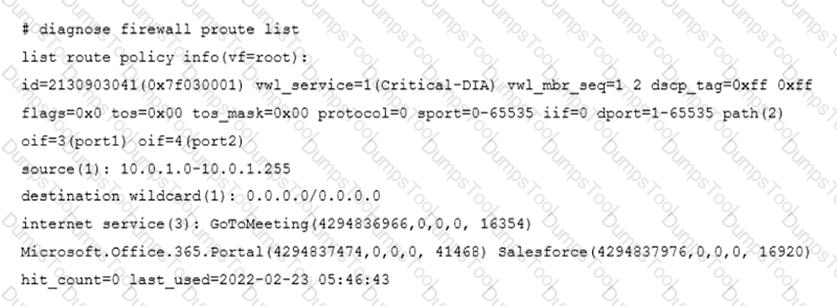
What does the output reveal about the policy route?
108
Which statement about the IP authentication header (AH) used by IPsec is true?
82
Consider the topology:
Application on a Windows machine <--{SSL VPN} -->FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
Refer to the exhibit, which contains a static route configuration.
An administrator created a static route for Amazon Web Services.
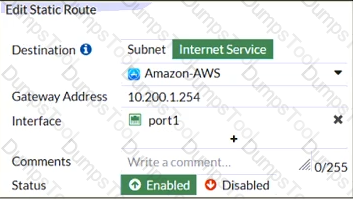
Which CLI command must the administrator use to view the route?
Refer to the exhibits.
Exhibit A shows a network diagram. Exhibit B shows the firewall policy configuration and a VIP object configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The administrator disabled the WebServer firewall policy.
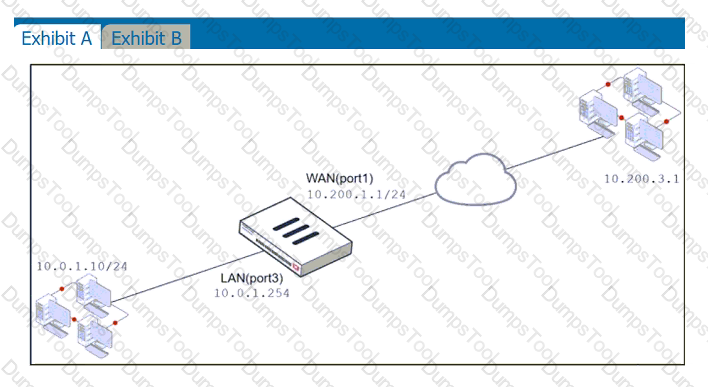
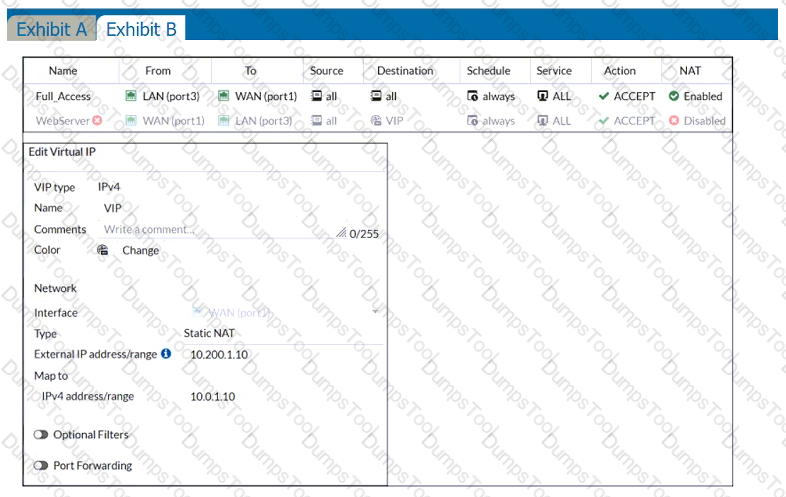
Which IP address will be used to source NAT the traffic, if a user with address 10.0.1.10 connects over SSH to the host with address 10.200.3.1?
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
24
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on
which device?
Refer to the exhibit.
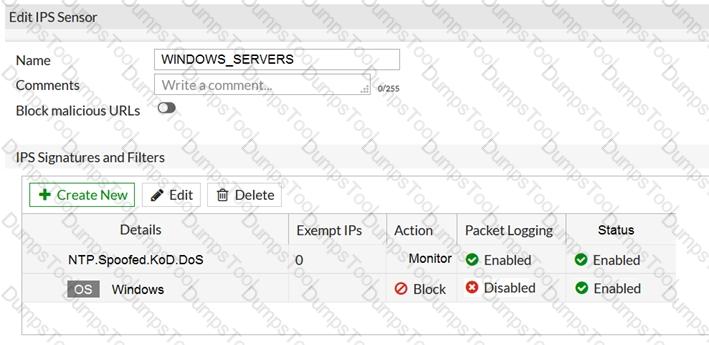
The exhibit shows the IPS sensor configuration.
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
Which three security features require the intrusion prevention system (IPS) engine to function? (Choose three.)
113
What inspection mode does FortiGate use if it is configured as a policy-based next-generation firewall (NGFW)?
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
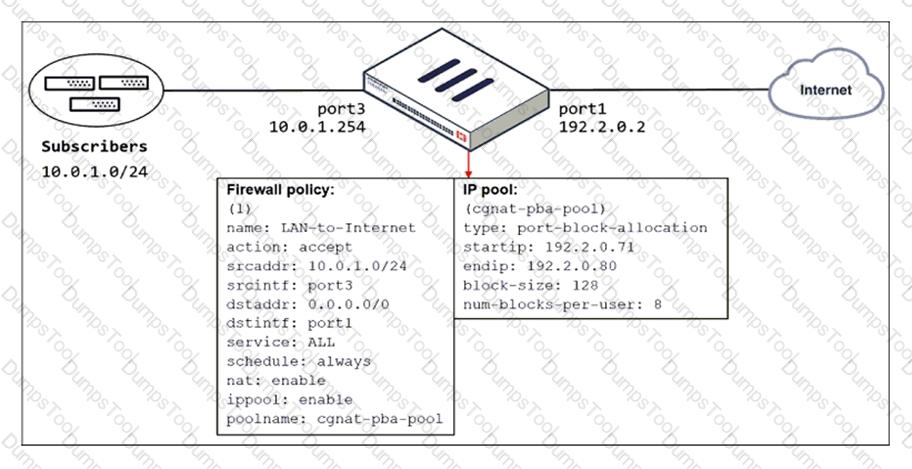
Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
29
Which two statements are correct about a software switch on FortiGate? (Choose two.)
Refer to the exhibit.
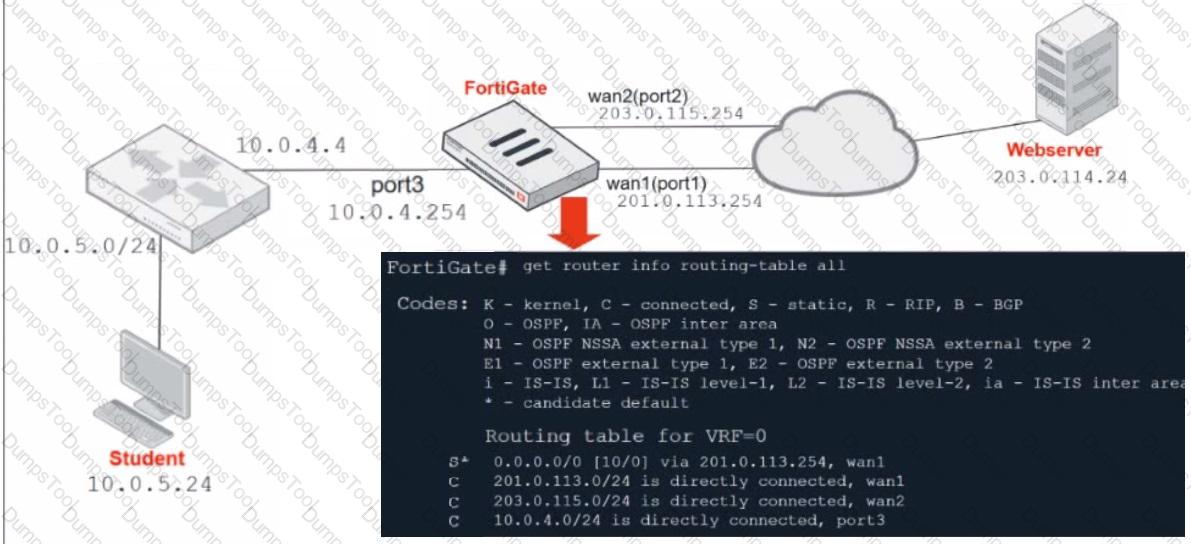
Which contains a network diagram and routing table output.
The Student is unable to access Webserver.
What is the cause of the problem and what is the solution for the problem?
31
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
Refer to the exhibit.
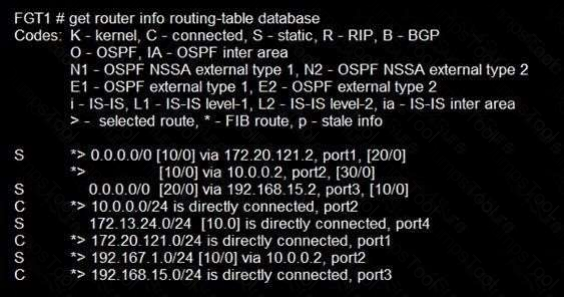
Given the routing database shown in the exhibit, which two statements are correct? (Choose two.)
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
Refer to the exhibit.
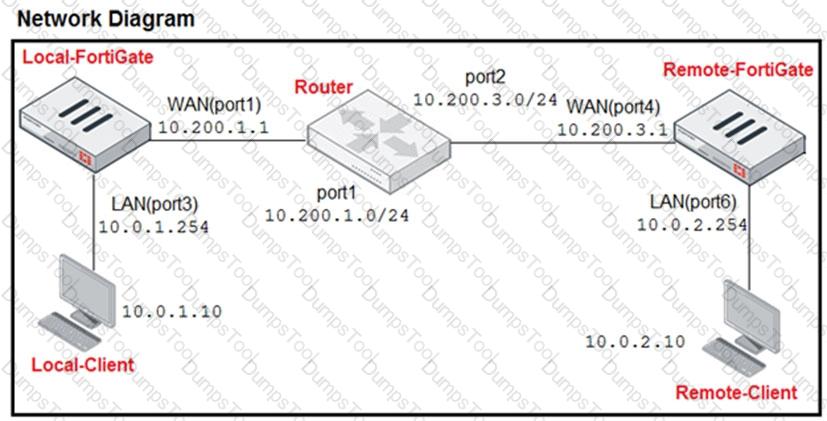
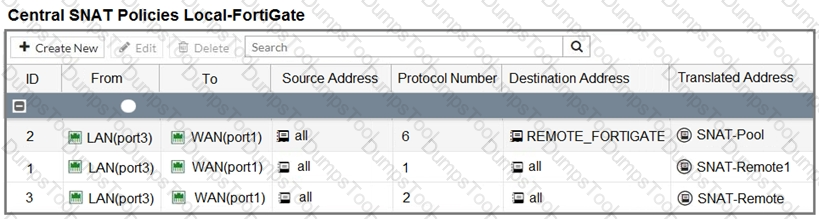
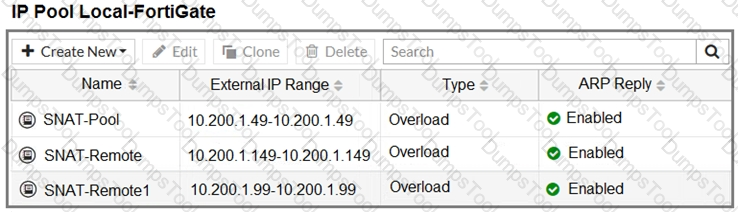
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200. 1. 1/24.
The LAN (port3) interface has the IP address 10.0. 1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0. 1. 10) pings the IP address of Remote-FortiGate (10.200.3. 1)?
Refer to the exhibit.
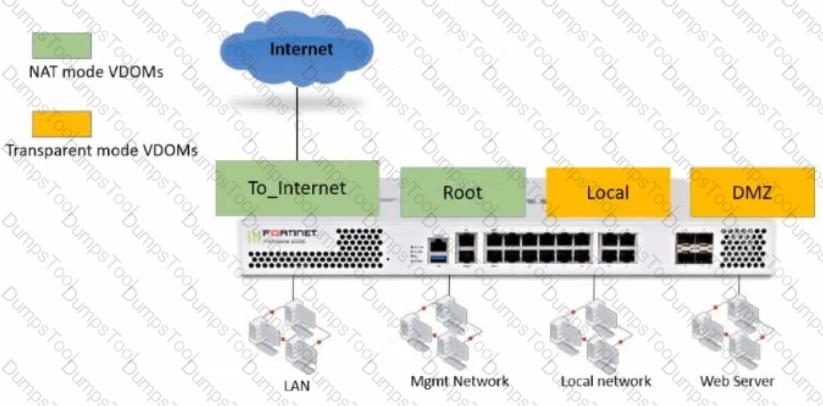
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem .
With this configuration, which statement is true?
93
Which two statements are correct regarding FortiGate HA cluster virtual IP addresses? (Choose two.)
Refer to the exhibit, which contains a session diagnostic output.
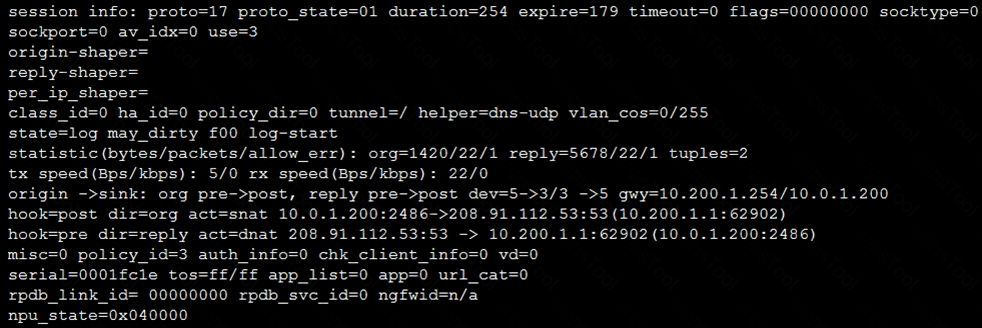
Which statement is true about the session diagnostic output?
On FortiGate, which type of logs record information about traffic directly to and from the FortiGate management IP addresses?
Refer to the exhibit.
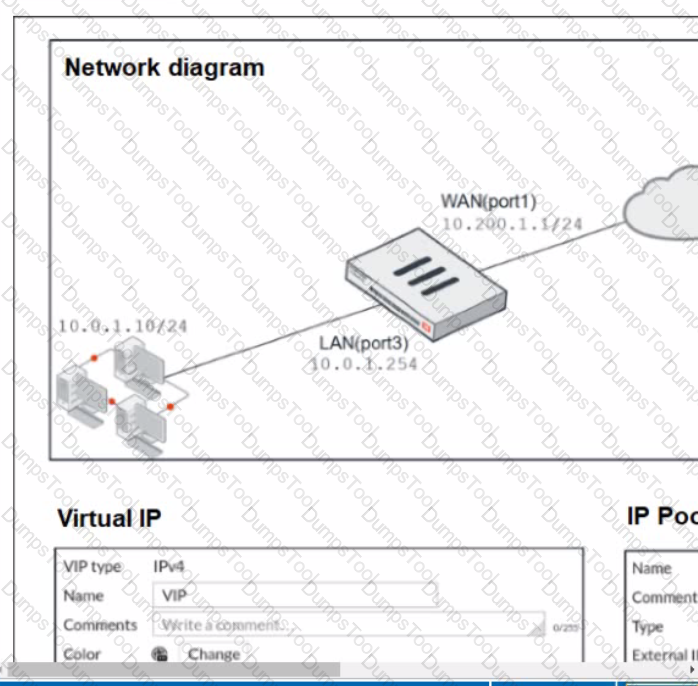
The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration.
The WAN (port1) interface has the IP address 10.200. 1. 1/24.
The LAN (port3) interface has the IP address 10 .0.1.254. /24.
The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP address 10.0. 1. 10?
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
84
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
An administrator wants to configure timeouts for users. Regardless of the userTMs behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?
Which statement is correct regarding the use of application control for inspecting web applications?
In an explicit proxy setup, where is the authentication method and database configured?
58
Refer to the exhibit.
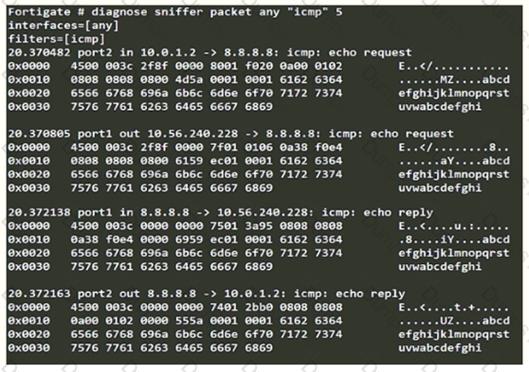
An administrator is running a sniffer command as shown in the exhibit.
Which three pieces of information are included in the sniffer output? (Choose three.)
Which two types of traffic are managed only by the management VDOM? (Choose two.)
Which two types of traffic are managed only by the management VDOM? (Choose two.)
53
Which of the following conditions must be met in order for a web browser to trust a web server certificate signed by a third-party CA?
Refer to the exhibit showing a debug flow output.
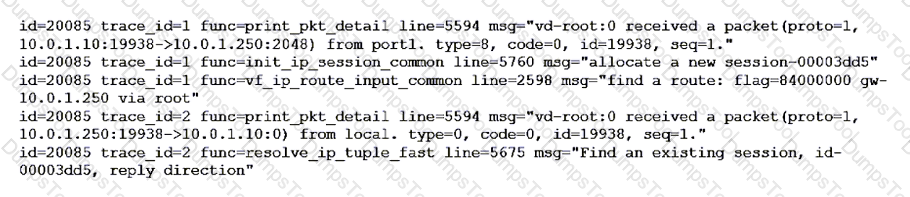
What two conclusions can you make from the debug flow output? (Choose two.)
Refer to the exhibit.
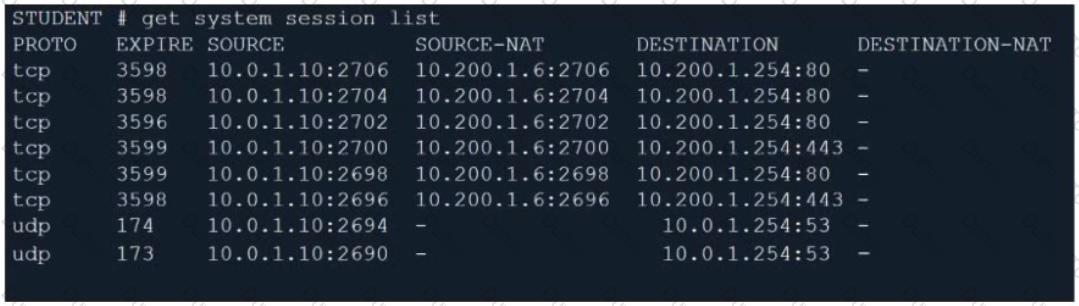
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
56
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
Which two statements about FortiGate FSSO agentless polling mode are true? (Choose two.)
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
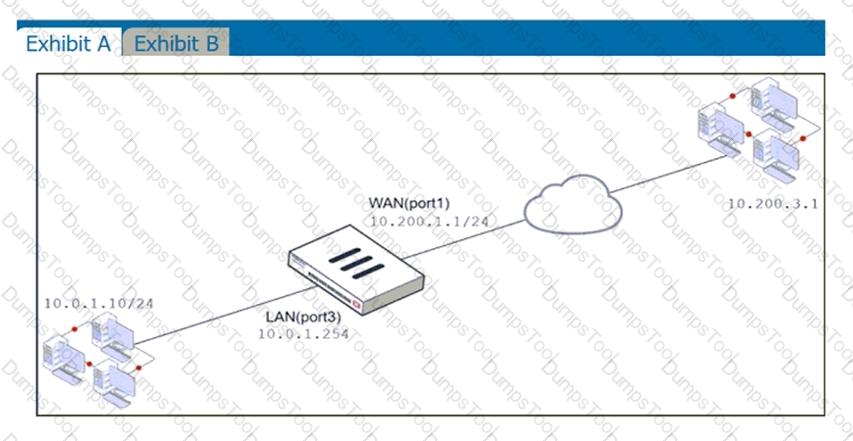
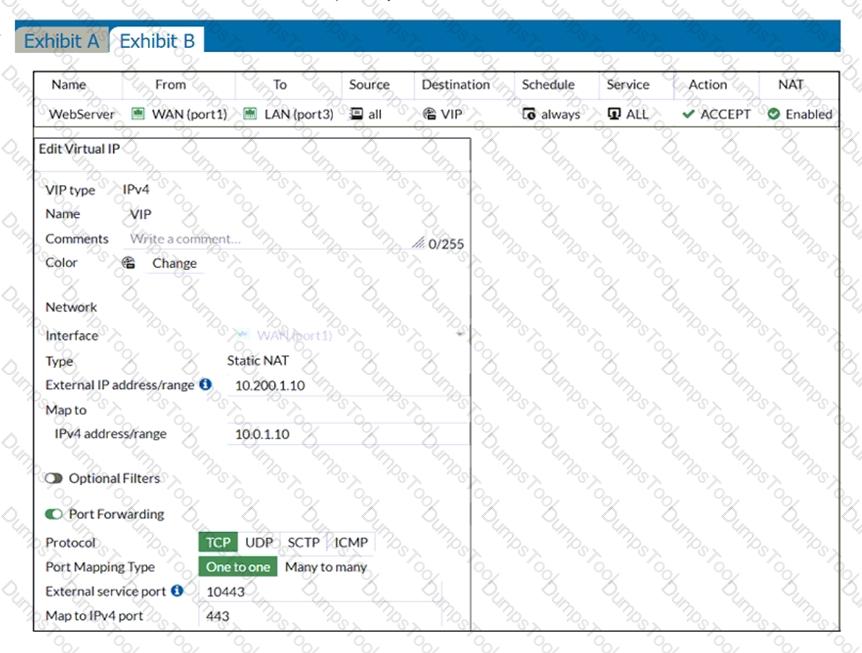
The WAN (port1) interface has the IP address 10.200. 1. 1/24. The LAN (port2) interface has the IP address 10.0. 1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address. Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0. 1. 10/24?
Refer to the exhibit.
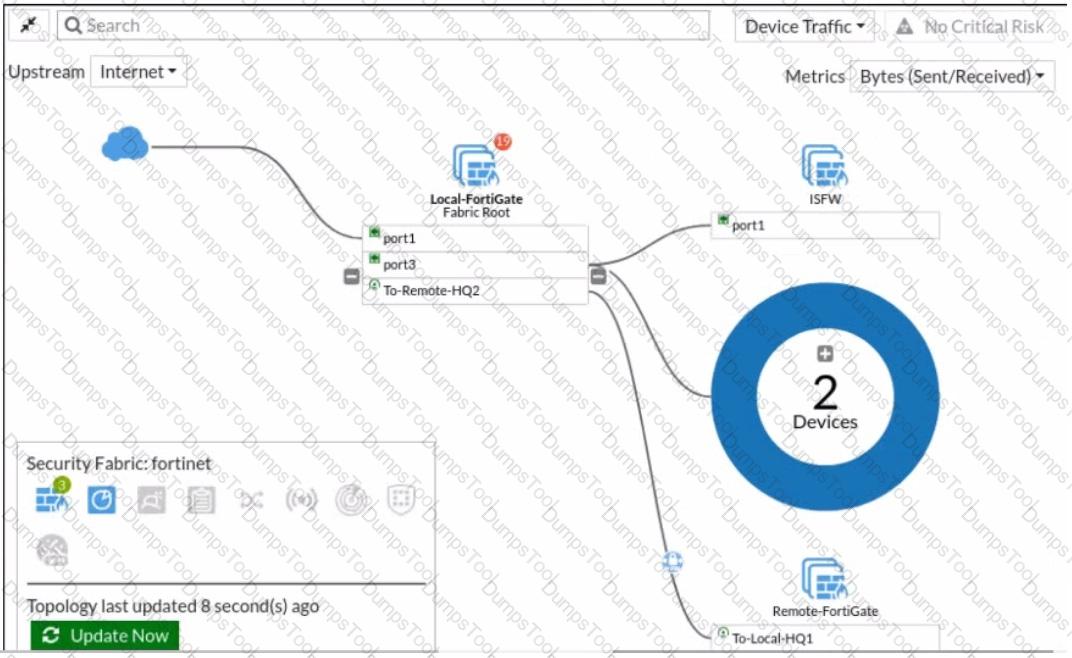
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)