An administrator wants to block HTTP uploads. Examine the exhibit, which contains the proxy address created for that purpose.
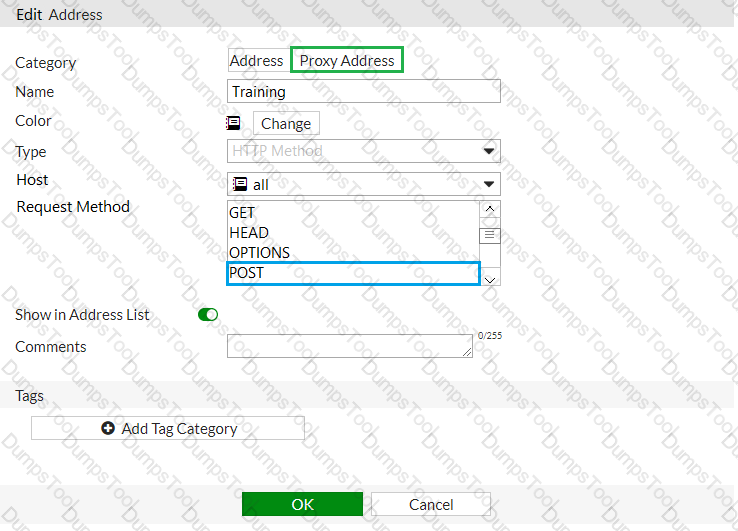
Where must the proxy address be used?
Which configuration objects can be selected for the Source field of a firewall policy? (Choose two.)
An administrator has configured two VLAN interfaces:
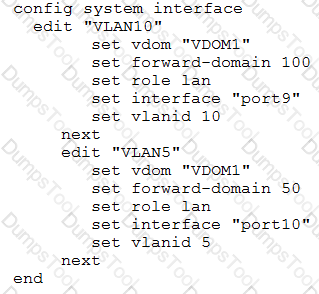
A DHCP server is connected to the VLAN10 interface. A DHCP client is connected to the VLAN5 interface. However, the DHCP client cannot get a dynamic IP address from the DHCP server. What is the cause of the problem?
If the Services field is configured in a Virtual IP (VIP), which of the following statements is true when central NAT is used?
An administrator needs to strengthen the security for SSL VPN access. Which of the following statements are best practices to do so? (Choose three.)
Examine the network diagram shown in the exhibit, and then answer the following question:
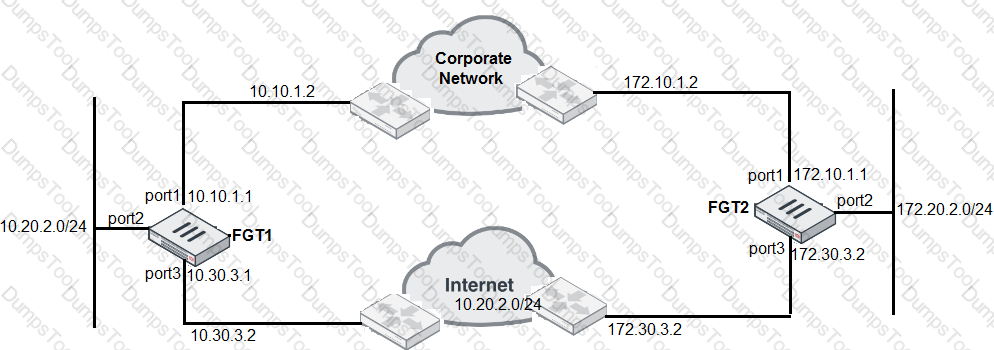
A firewall administrator must configure equal cost multipath (ECMP) routing on FGT1 to ensure both port1 and port3 links are used at the same time for all traffic destined for 172.20.2.0/24. Which of the following static routes will satisfy this requirement on FGT1? (Choose two.)
A FortiGate is operating in NAT mode and configured with two virtual LAN (VLAN) sub interfaces added to the physical interface.
Which statements about the VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
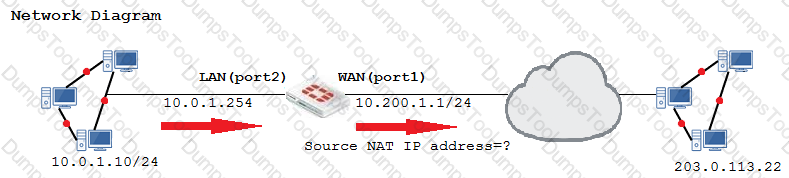
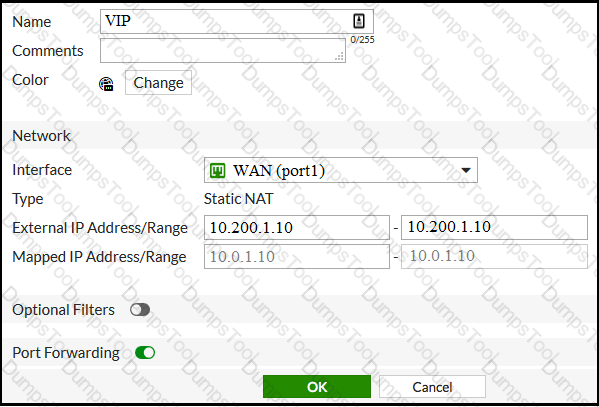
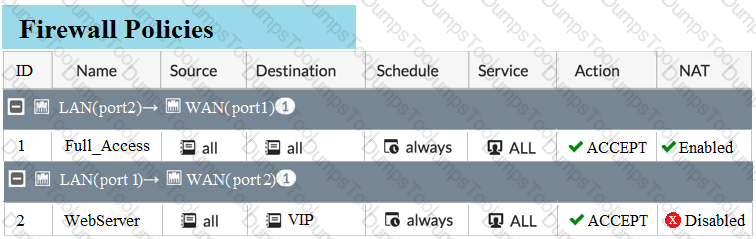
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
View the exhibit:
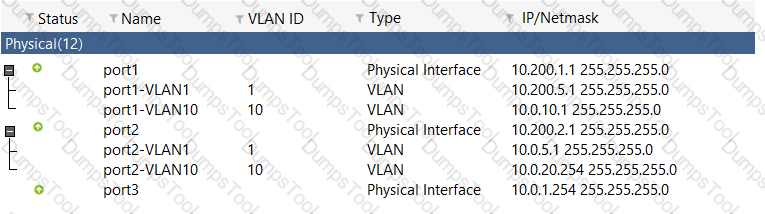
Which the FortiGate handle web proxy traffic rue? (Choose two.)
Examine the two static routes shown in the exhibit, then answer the following question.
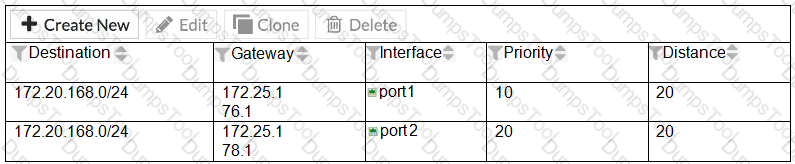
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
Which of the following statements about backing up logs from the CLI and downloading logs from the GUI are true? (Choose two.)
In a high availability (HA) cluster operating in active-active mode, which of the following correctly describes the path taken by the SYN packet of an HTTP session that is offloaded to a secondary FortiGate?
Examine the exhibit, which shows the partial output of an IKE real-time debug.
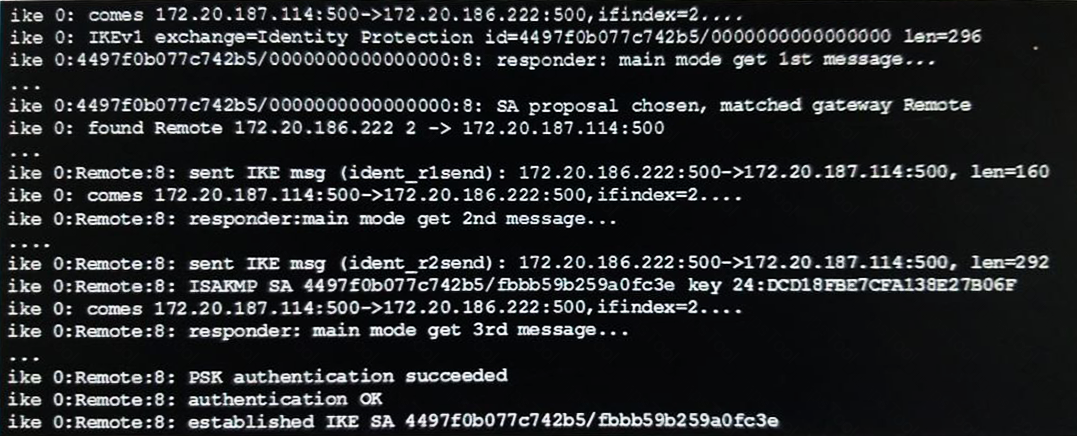
Which of the following statement about the output is true?