Which two VPNtypes can a FortiClientendpoint user inmate from the Windows command prompt? (Choose two)
Refer to the exhibits.
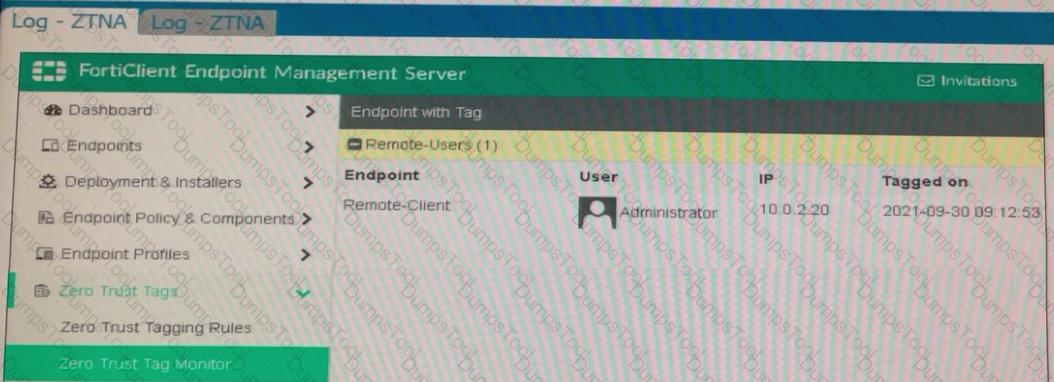
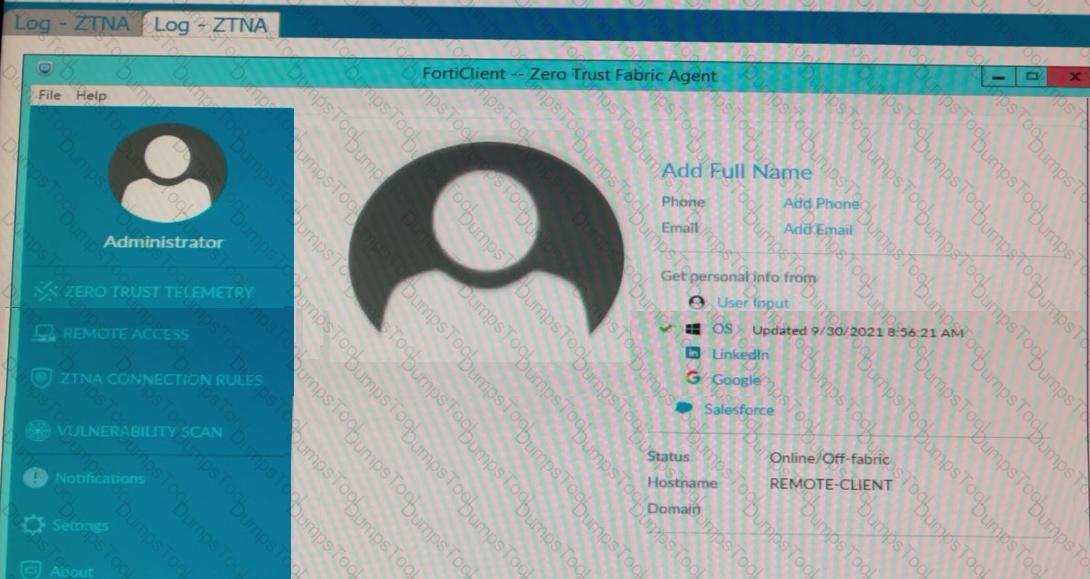
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
Which component or device shares device status information through ZTNA telemetry?
Which security fabric component sends a notification io quarantine an endpoint after IOC detection "n the automation process?
Which statement about FortiClient comprehensive endpoint protection is true?
An administrator has lost web access to the FortiClient EMS console, and the web page to access to the console is timing out.
How can the administrator gather information to investigate the issue? (Choose one answer)
Which three types of antivirus scans are available on FortiClient? (Choose three )
An administrator configures ZTNA configuration on the FortiGate. Which statement is true about the firewall policy?
An administrator needs to connect FortiClient EMS as a fabric connector to FortiGate What is the prerequisite to get FortiClient EMS lo connect to FortiGate successfully?
Refer to the exhibit.
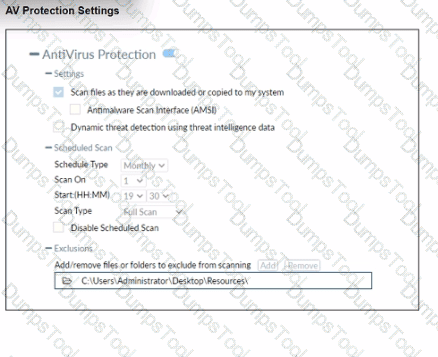
Based on The settings shown in The exhibit, which statement about FortiClient behaviour is Hue?
Refer to the exhibit.
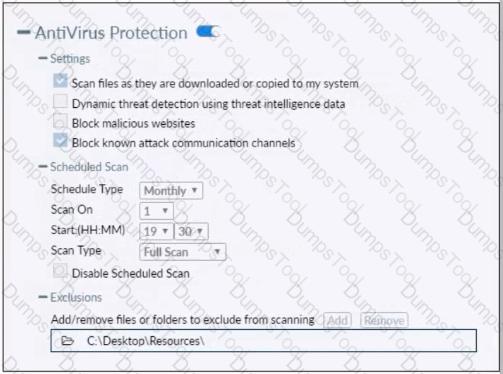
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
A company must integrate the FortiClient EMS with their existing identity management infrastructure for user authentication, and implement and enforce administrative access with multi-factor authentication (MFA). Which two authentication methods can they use in this scenario? (Choose two answers)
What action does FortiClient anti-exploit detection take when it detects exploits?