What Is the maximum number of criteria blocks with an OR condition that can be configured in a single file pool policy?
When reconciling permissions (or clients using UNIX as well as Microsoft Windows systems, what describes the scope of the permissions?
A Job Engine is running in low space mode and no jobs are in the running state. What is the OneFS8.2 behavior if the AutoBalance job is initiated?
An Isilon administrator is receiving “permission denied” while accessing a file on a cluster that an end-user created through an SMB share. The end-user is unable to access the share from their UNIX server.
The end-user “mydomain.com\win_user1” as the login name to access the Microsoft Windows share and then used an LDAP account name of “ux_user1” to access the UNIX mount. The Isilon cluster is joined to the “mydomain.com” Active Directory domain. In additional, the cluster has an LDAP provider attached to it while the on-disk identity is set as “Native”.
What is a possible cause for this permission issue?
A company wants to re-use HD400 nodes into a new cluster with OneFS 8.2.0. What is the minimum number of HD400 nodes required?
What is the recommended number of delegations for a SmartConnect zone name for each SmarConnect zone alias on a cluster?
When configuring NTP on a 16-node Gen 6 cluster, how many chimer nodes are automatically configured on the duster?
In a Dell PowerScale environment, what is a requirement to join multiple, untrusted Active Directory (AD) authentication sources to an access zone?
A Dell PowerScale cluster has (our H500 nodes. Data protection Is set to N+ 1 and access is set to random.
How many drives will be used across the disk pool to protect a 1 MB file?
An administrator wants to enable quotas on a group directory in their Dell PowerScale cluster. In addition, they want to monitor and limit the disk usage.
Which type of quotas need to be configured?
Which is statistics subcommand is used to display the most commonly accessed flics and directories in a file system?
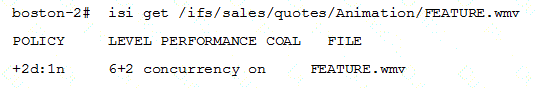
Based on the exhibit, what is the actual protection level of the FEATURE.wmv file?
What Is a use case for running HealthCheck on a Dell PowerScale cluster running OneFS 9.0?
What is the maximum supported node limit with a Dell PowerScale Gen 6 cluster running OneFS 9.4?
What is the minimum storage space needed on a datastore to hold InsightIQ?
An Isilon administrator has four H600 nodes and eight A2000 nodes in the cluster. The file pool policy is configured to have all new data written to the H600 nodes. After a few weeks, the administrator has some concerns about the available capacity on the H600 nodes.
Which feature should be configured to accept writes, even after the H600 nodes become full?
Which data access pattern makes the prefetch caching algorithm to be highly aggressive?