Alice, a Server Administrator (Tomcat), wants to ensure that Tomcat can be shut down only by the user who owns the Tomcat process. Select the appropriate setting of the CATALINA_HOME/conf in server.xml that will enable him to do so.
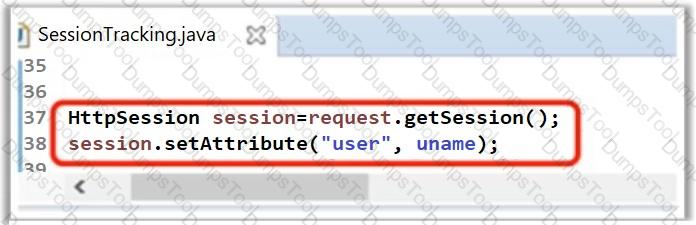
A developer has written the following line of code to handle and maintain session in the application. What did he do in the below scenario?
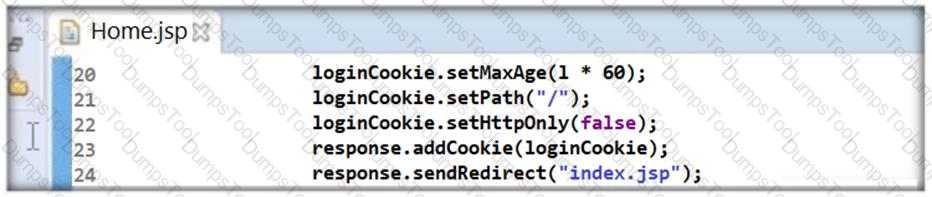
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of the consequences of insecure coding. One day, he wrote code as shown in the following screenshot. He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.
Alice, a security engineer, was performing security testing on the application. He found that users can view the website structure and file names. As per the standard security practices, this can pose a serious security risk as attackers can access hidden script files in your directory. Which of the following will mitigate the above security risk?
The developer wants to remove the HttpSessionobject and its values from the client' system.
Which of the following method should he use for the above purpose?
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
Ted is an application security engineer who ensures application security activities are being followed during the entire lifecycle of the project. One day, he was analyzing various interactions of users depicted in the use cases of the project under inception. Based on the use case in hand, he started depicting the scenarios where attacker could misuse the application. Can you identify the activity on which Ted is working?