Which of the following command is used to view iptables logs on Ubuntu and Debian distributions?
Jennifer, a SOC analyst, initiates an investigation after receiving an alert about potential unauthorized activity on Marcus's workstation. She starts by retrieving EDR logs from the endpoint, analyzing network traffic patterns in the Security Information and Event Management (SIEM) system, and inspecting email gateway logs for signs of malicious attachments. Her objective is to determine whether this alert represents a legitimate security incident. In which phase of the Incident Response process is Jennifer currently operating?
Identify the event severity level in Windows logs for the events that are not necessarily significant, but may indicate a possible future problem.
TechSolutions, a software development firm, discovered a potential data leak after an external security researcher reported finding sensitive customer data on a public code repository. Level 1 SOC analysts confirmed the presence of the data and escalated the issue. Level 2 analysts traced the source of the leak to an internal network account. The incident response team has been alerted, and the CISO demands a comprehensive analysis of the incident, including the extent of the data breach and the timeline of events. The SOC manager must decide whom to assign to the in-depth investigation. To accurately determine the timeline, extent, and root cause of the data leak, which SOC role is critical in gathering and analyzing digital evidence?
David is a SOC analyst in Karen Tech. One day an attack is initiated by the intruders but David was not able to find any suspicious events.
This type of incident is categorized into?
An organization with a complex IT infrastructure is planning to implement a SIEM solution to improve its threat detection and response capabilities. Due to the scale and complexity of its systems, the organization opts for a phased deployment approach to ensure a smooth implementation and reduce potential risks. Which of the following should be the first phase in their SIEM deployment strategy?
Which of the following tool can be used to filter web requests associated with the SQL Injection attack?
A SOC team notices malware-related incidents increased over the past six months, primarily targeting endpoints through phishing campaigns. They need to present a report to security leadership to justify investing in advanced email filtering and end-user security training. Which SOC report best supports their case?
Mark Reynolds, a SOC analyst at a healthcare organization, is monitoring the SIEM system when he detects a potential security threat: a series of unusual login attempts targeting critical patient data servers. After investigating the alerts and collaborating with the incident response team, the SOC determines that the threat has a “Likely” chance of occurring and could cause “Significant” damage, including operational disruptions, financial loss due to data breaches, and regulatory penalties under HIPAA. Using a standard Risk Matrix, how would this risk be categorized in terms of overall severity?
You are part of a team of SOC analysts in a multinational organization that processes large volumes of security logs from various sources, including firewalls, IDS, and authentication servers. Your team is having difficulty detecting incidents because logs from different systems are analyzed in isolation, making it harder to link related events. What approach should you implement for future investigations to automatically match related log events based on predefined rules?
Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below.
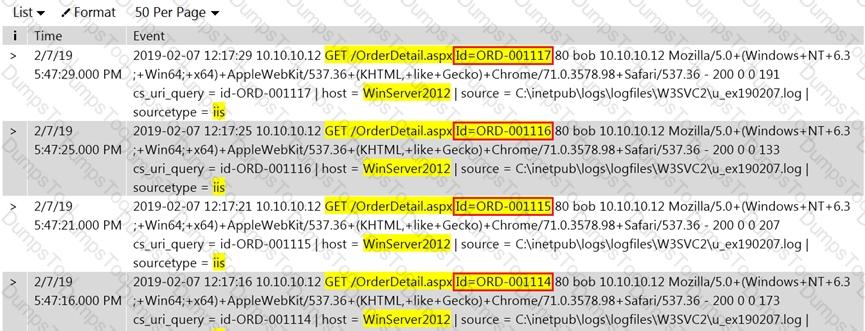
What does this event log indicate?
Global Bank relies heavily on Microsoft Azure to host critical banking applications and services. The SOC must ensure continuous monitoring, compliance, and real-time threat detection across Azure resources. They need a comprehensive solution to collect, analyze, and visualize telemetry from cloud resources, VMs, storage, and applications, and integrate with security tools to detect anomalies and monitor performance. Which Azure service is best suited?
An attacker attempts to gain unauthorized access to a secure network by repeatedly guessing login credentials. The SIEM is configured to generate an alert after detecting 10 consecutive failed login attempts within a short timeframe. However, the attacker successfully logs in on the 9th attempt, just before the threshold is reached, bypassing the alert mechanism. The security team only becomes aware of the incident after detecting suspicious activity post-login, highlighting a gap in the SIEM’s detection rules. What type of alert classification does this represent?
Jackson & Co., a mid-sized law firm, is concerned about web-based cyber threats. The IT team implements a solution that serves as an intermediary for all HTTP and HTTPS requests. This allows the SOC to inspect, filter, and control web traffic to detect and block malicious websites, phishing attempts, and other online threats before they reach users. Which containment method is the organization using to gain visibility and control over web traffic?
SecureTech Inc. operates critical infrastructure and applications in AWS. The SOC detects suspicious activities such as unexpected API calls, unusual outbound traffic from instances, and DNS requests to potentially malicious domains. They need a fully managed AWS security service that continuously monitors for malicious activity, analyzes CloudTrail logs, VPC Flow Logs, and DNS query logs, leverages machine learning and threat intelligence, and provides actionable findings. Which AWS service best fits?
A major financial institution has strict policies preventing unauthorized data transfers. As a SOC analyst, during routine log analysis you detect an anomaly: an employee workstation initiates large file transfers outside business hours, involving highly sensitive customer financial records. You discover remote access from an unfamiliar IP address and an unauthorized USB device connection on the workstation. Given the likelihood of data exfiltration, what should be your first step in responding?
Which of the following process refers to the discarding of the packets at the routing level without informing the source that the data did not reach its intended recipient?
A leading e-commerce company relies on backend servers for processing customer transactions. You are working with their cybersecurity team as a SOC analyst. One morning, you notice a sharp increase in CPU utilization on one of your backend servers. Your team scans and monitors the server and finds that an unknown process is running, consuming excessive resources. You further perform detailed forensic analysis and identify the presence of an unrecognized scheduled task that triggers a PowerShell script connecting to an unknown IP address. What should you do to confirm whether this is an active attack?
Robin, a SOC engineer in a multinational company, is planning to implement a SIEM. He realized that his organization is capable of performing onlyCorrelation, Analytics, Reporting, Retention, Alerting, and Visualization required for the SIEM implementation and has to take collection and aggregation services from a Managed Security Services Provider (MSSP).
What kind of SIEM is Robin planning to implement?
In which phase of Lockheed Martin's – Cyber Kill Chain Methodology, adversary creates a deliverable malicious payload using an exploit and a backdoor?
A large financial organization has experienced an increase in sophisticated cyber threats, including zero-day attacks and APTs. Traditional detection relies heavily on signatures and manual intervention, causing delays. The CISO is exploring AI-driven solutions that can automatically analyze large datasets, detect anomalies, and adapt to evolving threats in real time—identifying suspicious activity without predefined signatures and with minimal human oversight. Which key AI technology should the organization focus on?
A multinational cybersecurity firm wants to enhance its threat intelligence capabilities by integrating real-time threat feeds into Microsoft Sentinel. These feeds include malicious IPs, domains, file hashes, and attack patterns. The firm requires a standardized protocol that allows automated threat intelligence sharing so Sentinel continuously receives updated indicators from external sources in a structured format. Which Microsoft Sentinel data connector should be implemented to integrate threat intelligence feeds using an industry-standard protocol?
A financial services company implements a SIEM solution to enhance cybersecurity. Despite deployment, it fails to detect known attacks or suspicious activities. Although reports are generated, the team struggles to interpret them. Investigation shows that critical logs from firewalls, IDS, and endpoint devices are not reaching the SIEM. What is the reason the SIEM is not functioning as expected?
Identify the type of attack, an attacker is attempting on www.example.com website.
A SIEM alert is triggered due to unusual network traffic involving NetBIOS. The system log shows: “The TCP/IP NetBIOS Helper service entered the running state.” Concurrently, Windows Security Event ID 4624 (“An account was successfully logged on”) appears for multiple machines within a short time frame. The logon type is 3 (Network logon). Which of the following security incidents is the SIEM detecting?
You are a Level 1 SOC analyst at a critical infrastructure provider. Threat actors infiltrated the network and exfiltrated sensitive system blueprints. Before detection, they executed commands that altered system logs, wiped forensic artifacts, and modified timestamps to mimic normal activity. They also manipulated security monitoring tools to prevent unusual login events from being recorded. Which APT lifecycle phase does this represent?
A SOC analyst receives an alert indicating that the system time on a critical Windows server was changed at 3:00 AM. There are no scheduled maintenance tasks at this time. Unauthorized time changes can be used to evade security controls, such as altering timestamps to obscure malicious activity. The analyst must identify the relevant event codes that log system time modifications and related suspicious behavior. Which of the following Windows Security Event Codes should the analyst review to investigate potential tampering?
CyberBank has experienced phishing, insider threats, and attempted data breaches targeting customer financial records. The bank operates across multiple regions and needs a solution offering continuous security monitoring, rapid threat detection, and centralized visibility across all branches. Which solution will provide automated alerting, digital forensics capabilities, and active threat hunting?
You are working at Tech Solutions, a global technology firm. Your team detects an adversary attempting to bypass authentication controls and escalate privileges within the enterprise network. To counter the threat, you implement credential encryption, behavioral analytics, and process isolation. Your approach follows a structured framework that systematically maps defensive techniques to known adversarial tactics, allowing you to anticipate and mitigate evolving cyber threats. Which framework did you choose to apply in this scenario?
A large web hosting service provider, Web4Everyone, hosts multiple major websites and platforms. You are a Level 1 SOC analyst responsible for investigating web server logs for potential malicious activity. Recently, your team detected multiple failed login attempts and unusual traffic patterns targeting the company’s web application. To efficiently analyze the logs and identify key details such as remote host, username, timestamp, requested resource, HTTP status code, and user-agent, you need a structured log format that ensures quick and accurate parsing. Which standardized log format will you choose for this scenario?
A large financial institution receives thousands of security logs daily from firewalls, IDS systems, and user authentication platforms. The SOC uses an AI-driven SIEM system with Natural Language Processing (NLP) capabilities to streamline threat detection. This enables faster response times, reduces manual rule creation, and helps detect advanced threats that traditional systems might overlook. Which option best illustrates the advantage of NLP in SIEM?
A SOC analyst is responsible for designing a security dashboard that provides real-time monitoring of security threats. The organization wants to avoid overwhelming analysts with excessive information and focus on the most critical security alerts to ensure timely responses to potential threats. Which principle should guide the design of the dashboard?
Emmanuel is working as a SOC analyst in a company named Tobey Tech. The manager of Tobey Tech recently recruited an Incident Response Team (IRT) for his company. In the process of collaboration with the IRT, Emmanueljust escalated an incident to the IRT.
What is the first step that the IRT will do to the incident escalated by Emmanuel?
Where will you find the reputation IP database, if you want to monitor traffic from known bad IP reputation using OSSIM SIEM?
Which of the following technique protects from flooding attacks originated from the valid prefixes (IP addresses) so that they can be traced to its true source?
At GlobalTech, the SOC team detects a suspicious ransomware outbreak affecting multiple endpoints. After successfully isolating the infected systems from the network, the Digital Forensics team begins their investigation. They deploy a forensics workstation to acquire RAM dumps, extract Windows Event Logs, and collect network PCAP files from the compromised hosts. Which phase of the Incident Response lifecycle is currently underway?
What type of event is recorded when an application driver loads successfully in Windows?
Properly applied cyber threat intelligence to the SOC team help them in discovering TTPs.
What does these TTPs refer to?
The SOC analyst at a national cybersecurity agency detected unusual system behavior on critical infrastructure servers. Initial scans flagged potential malware activity. Due to the sophisticated nature of the suspected attack, including registry modifications, process injection, and unauthorized tasks, the case was escalated to the forensic team. The forensic team suspects the malware is designed for stealthy data exfiltration. To assess the compromise, they captured system snapshots before and after suspected infection to identify unauthorized changes and anomalies. Which process are they following by capturing and comparing system snapshots to detect unauthorized changes?
Identify the attack when an attacker by several trial and error can read the contents of a password file present in the restricted etc folder just by manipulating the URL in the browser as shown:
http://www.terabytes.com/process.php./../../../../etc/passwd
A multinational financial institution notices unusual network activity during a routine security audit. The SOC detects multiple failed login attempts, followed by a successful access attempt using an administrator's credentials from an unrecognized IP address. Shortly after, sensitive customer records are accessed without authorization. The company suspects a breach and calls in the forensic investigation team. During evidence collection, the forensic team creates a detailed record that tracks every individual who handled the evidence, its storage location, and timestamps of transfers. What is this process called?
Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads.
What does thisindicate?
During a threat intelligence briefing, a SOC analyst comes across a classified report detailing a sophisticated cybercrime syndicate targeting executives of high-profile financial institutions. These adversaries rarely leave digital footprints and seem to anticipate security measures. Several breaches began with seemingly innocent conversations: a foreign journalist requesting an interview with a CEO and a “security consultant” offering free risk assessments. Further investigation reveals attackers socially engineered employees, manipulated trust, and extracted critical security details long before launching technical attacks. The analyst decides to focus on intelligence involving deception detection and psychological profiling to uncover true intent and methods. Which type of intelligence is the analyst leveraging?
Which of the following technique involves scanning the headers of IP packets leaving a network to make sure
thatthe unauthorized or malicious traffic never leaves the internal network?
Which of the following is a report writing tool that will help incident handlers to generate efficientreports on detected incidents during incident response process?
Which of the following data source will a SOC Analyst use to monitor connections to the insecure ports?
John, a threat analyst at GreenTech Solutions, wants to gather information about specific threats against the organization. He started collecting information from various sources, such as humans, social media, chat room, and so on, and created a report that contains malicious activity.
Which of the following types of threat intelligence did he use?
An organization is implementing and deploying the SIEM with following capabilities.
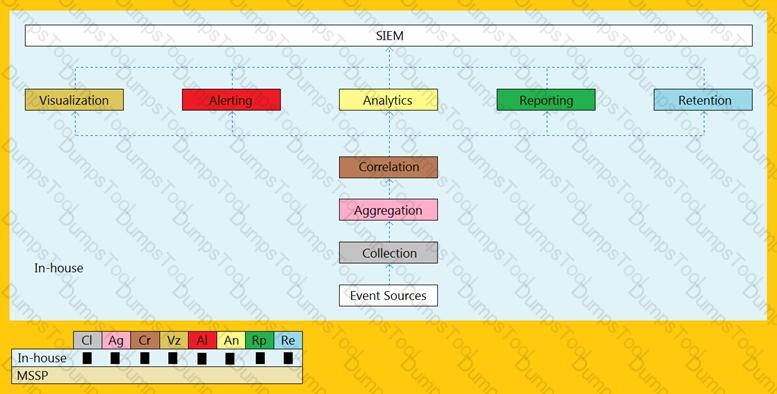
What kind of SIEM deployment architecture the organization is planning to implement?
Following a high-priority security incident, you, as an Incident Responder at a Cyber Incident Response firm, initiate an internal investigation after reports confirm a serious data breach in which sensitive customer data, including payment details and personal information, was stolen from a critical web server. You begin analyzing the server logs to reconstruct the attack timeline and identify how the attacker gained access. During your investigation, you discover suspicious activity in the logs, including repeated requests attempting to access files and directories outside of the web server’s root directory. Some of these requests appear to be manipulating URL paths to navigate into restricted system files—a behavior that is often associated with web-based exploits. You suspect that a vulnerability in the web server was exploited to bypass security restrictions and access unauthorized directories, potentially exposing sensitive configurations and credentials. However, you still need to confirm the exact technique used. Which type of web application attack might have caused this incident?
A mid-sized healthcare organization is facing frequent phishing and ransomware attacks. They lack an internal SOC and want proactive threat detection and response capabilities. Compliance with HIPAA regulations is essential. The organization seeks a solution that includes both monitoring and rapid response to incidents. Which service best meets their needs?
You are working as a SOC analyst for a cloud-based service provider that relies on PostgreSQL databases to store critical customer data. During a security review, you discover that logs are not being generated for failed authentication attempts, slow queries, or database errors. This lack of visibility is making it difficult to detect threats and investigate suspicious activity. To ensure PostgreSQL captures and stores logs for centralized monitoring and forensic analysis, which configuration parameter should you enable?
Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure below.
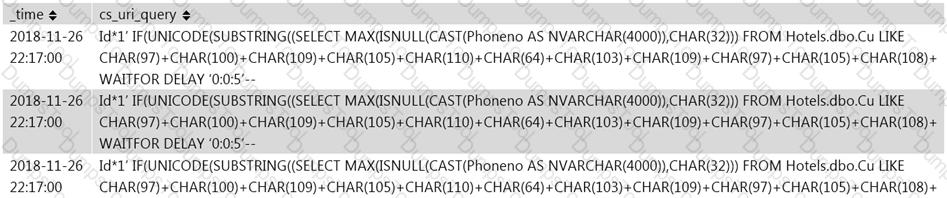
What does this event log indicate?
A large financial services company has experienced increasing sophisticated threats targeting critical assets. The SOC primarily focuses on log collection and basic monitoring, but incidents revealed gaps in detecting and responding to advanced threats proactively. Management decides to adopt the SOC Capability Maturity Model (CMM). The initial assessment indicates the SOC is at Level 1, and the organization aims to reach Level 3 by enhancing incident response procedures, improving threat intelligence integration, establishing KPIs, automating triage, implementing behavior-based analytics, and creating continuous training. Based on the SOC CMM, what should be the first priority in transitioning from Level 1 to Level 3?