A server administrator needs to configure a server on a network that will have no more than 30 available IP addresses. Which of the following subnet addresses will be the MOST efficient for this network?
Which of the following is a method that is used to prevent motor vehicles from getting too close to building entrances and exits?
An administrator is configuring a host-based firewall tor a server. The server needs to allow SSH, FTP, and LDAP traffic. Which of the following ports must be configured so this traffic will be allowed? (Select THREE).
A server administrator has connected a new server to the network. During testing, the administrator discovers the server is not reachable via server but can be accessed by IP address. Which of the following steps should the server administrator take NEXT? (Select TWO).
A server administrator wants to run a performance monitor for optimal system utilization. Which of the following metrics can the administrator use for monitoring? (Choose two.)
A company is reviewing options for its current disaster recovery plan and potential changes to it. The security team will not allow customer data to egress to non-company equipment, and the company has requested recovery in the shortest possible time. Which of the following will BEST meet these goals?
A large number of connections to port 80 is discovered while reviewing the log files on a server. The server is not functioning as a web server. Which of the following represent the BEST immediate actions to prevent
unauthorized server access? (Choose two.)
A data center employee shows a driver's license to enter the facility Once the employee enters, the door immediately doses and locks, triggering a scale that then weighs the employee before granting access to another locked door. This is an example of.
A server administrator needs to harden a server by only allowing secure traffic and DNS inquiries. A port scan reports the following ports are open:
A server technician is installing a new server OS on legacy server hardware. Which of the following should the technician do FIRST to ensure the OS will work as intended?
Alter rack mounting a server, a technician must install four network cables and two power cables for the server. Which of the following is the MOST appropriate way to complete this task?
A server administrator receives a report that Ann, a new user, is unable to save a file to her home directory on a server. The administrator checks Ann’s home directory permissions and discovers the following:
dr-xr-xr-- /home/Ann
Which of the following commands should the administrator use to resolve the issue without granting unnecessary permissions?
A technician has been asked to check on a SAN. Upon arrival, the technician notices the red LED indicator shows a disk has failed. Which of the following should the technician do NEXT, given the disk is hot swappable?
Which of the following backup types only records changes to the data blocks on a virtual machine?
Which of the following server types would benefit MOST from the use of a load balancer?
A company stores extremely sensitive data on an alt-gapped system. Which of the following can Be Implemented to increase security against a potential insider threat?
Which of the following actions should a server administrator take once a new backup scheme has been configured?
A technician is working on a Linux server. The customer has reported that files in the home directory are missing. The /etc/ f stab file has the following entry:
nfsserver:/home /home nfs defaults 0 0
However, a df -h /home command returns the following information:
/dev/sda2 10G 1G 9G 10% /home
Which of the following should the technician attempt FIRST to resolve the issue?
A company’s IDS has identified outbound traffic from one of the web servers coming over port 389 to an outside address. This server only hosts websites. The company’s SOC administrator has asked a technician to harden this server. Which of the following would be the BEST way to complete this request?
A server technician is configuring the IP address on a newly installed server. The documented configuration specifies using an IP address of 10.20.10.15 and a default gateway of 10.20.10.254. Which of the following subnet masks would be appropriate for this setup?
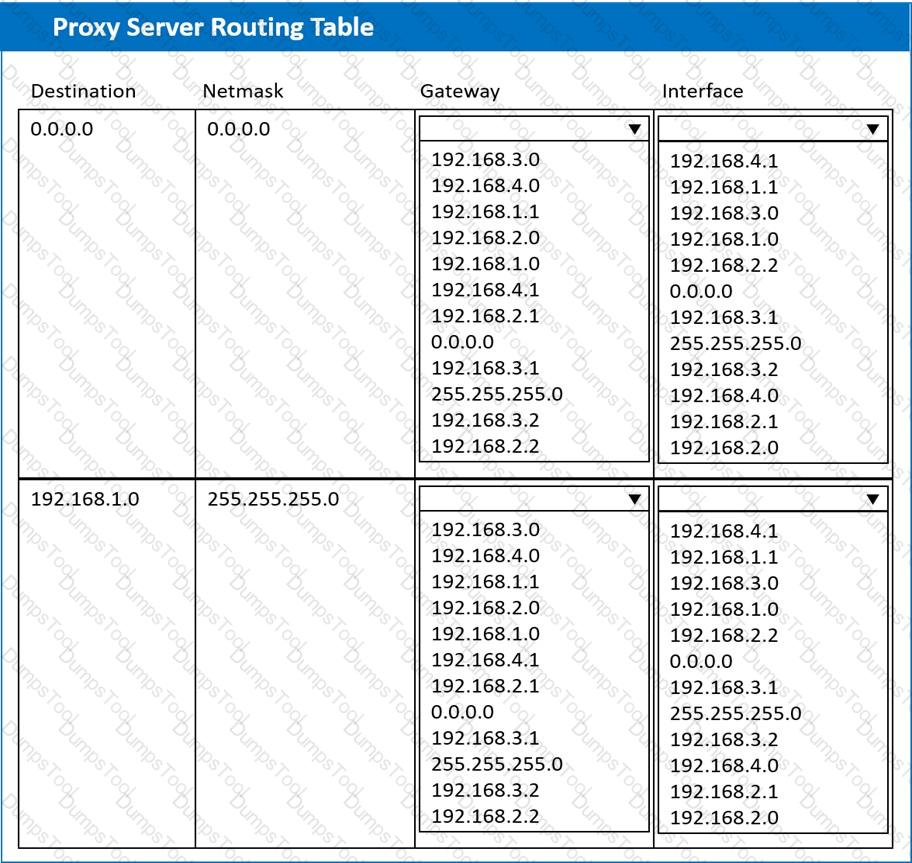
A systems administrator deployed a new web proxy server onto the network. The proxy server has two interfaces: the first is connected to an internal corporate firewall, and the second is connected to an internet-facing firewall. Many users at the company are reporting they are unable to access the Internet since the new proxy was introduced. Analyze the network diagram and the proxy server’s host routing table to resolve the Internet connectivity issues.
INSTRUCTIONS
Perform the following steps:
1. Click on the proxy server to display its routing table.
2. Modify the appropriate route entries to resolve the Internet connectivity issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A technician is deploying a single server to monitor and record me security cameras at a remote site, which of the following architecture types should be used to minimize cost?
A global organization keeps personnel application servers that are local to each country. However, a security audit shows these application servers are accessible from sites in other countries. Which of the following hardening techniques should the organization use to restrict access to only sites that are in the same country?
A company is running an application on a file server. A security scan reports the application has a known vulnerability. Which of the following would be the company’s BEST course of action?
A company wants to deploy software to all users, Out very few of men will be using the software at any one point in time. Which of the following licensing models would be BEST lot the company?
A systems administrator has noticed performance degradation on a company file server, and one of the disks on it has a solid amber light. The administrator logs on to the disk utility and sees the array is rebuild ing. Which of the following should the administrator do NEXT once the rebuild is finished?
Which of the following should an administrator use to transfer log files from a Linux server to a Windows workstation?
A server administrator was asked to build a storage array with the highest possible capacity. Which of the following RAID levels should the administrator choose?
A server that recently received hardware upgrades has begun to experience random BSOD conditions. Which of the following are likely causes of the issue? (Choose two.)
Winch of the following is a type of replication in which all files are replicated, all the time?
A server administrator must respond to tickets within a certain amount of time. The server administrator needs to adhere to the:
A technician is attempting to update a server’s firmware. After inserting the media for the firmware and restarting the server, the machine starts normally into the OS. Which of the following should the technician do
NEXT to install the firmware?
A server administrator has configured a web server. Which of the following does the administrator need to install to make the website trusted?
A systems administrator is setting up a server on a LAN that uses an address space that follows the RFC 1918 standard. Which of the following IP addresses should the administrator use to be in compliance with the standard?
A server administrator has noticed that the storage utilization on a file server is growing faster than planned. The administrator wants to ensure that, in the future, there is a more direct relationship between the number of users using the server and the amount of space that might be used. Which of the following would BEST enable this correlation?
A systems administrator needs to configure a new server and external storage for a new production application environment. Based on end-user specifications, the new solution needs to adhere to the following basic requirements:
1. The OS must be installed in a separate disk partition. In case of hard drive failure, it cannot be affected.
2. Application data IOPS performance is a must.
3. Data availability is a high priority, even in the case of multiple hard drive failures.
Which of the following are the BEST options to comply with the user requirements? (Choose three.)
Which of the following steps in the troubleshooting theory should be performed after a solution has been implemented? (Choose two.)
An organization recently experienced power outages. The administrator noticed the server did not have enough time to shut down properly. After the outages, the administrator had additional batteries installed in the UPS. Which of the following best describes the solution the administrator implemented?
An administrator is configuring a new server for use as a database server. It will have two mirrored drives to hold the operating system, and there will be three drive bays remaining for storage Which of the following RAID levels will yield the BEST combination of available space and redundancy?
The HIDS logs on a server indicate a significant number of unauthorized access attempts via USB devices at startup. Which of the following steps should a server administrator take to BEST secure the server without limiting functionality?
A server administrator needs to ensure all Window-based servers within a data center have RDP disabled. There are thousands of servers performing various roles. Which of the following is the best way to meet this requirement?
Which of the following concepts is in use when dual power supplies are connected to different power sources?
A server shut down after an extended power outage. When power was restored, the system failed to start. A few seconds into booting, the Num Lock, Scroll Lock, and Caps Lock LEDs flashed several times, and the system stopped. Which of the following is the MOST likely cause of the issue?
A server administrator is taking advantage of all the available bandwidth of the four NICs on the server. Which of the following NIC-teaming technologies should the server administrator utilize?
While running a local network security scan an administrator discovers communication between clients and one of the web servers is happening in cleartext. Company policy requires all communication lo be encrypted. Which of the following ports should be closed to stop the deartext communication?
A security manager is concerned that a rogue employee could boot a server from an outside USB drive. Which of the following actions can be taken to reduce this risk? (Select TWO).
An administrator is troubleshooting an application performance issue on a virtual server with two vCPUs. The application performance logs indicate CPU contention. The administrator adds more vCPU cores to the VM, yet the issue persists. Which of the following is the most likely reason for this issue?
A technician has moved a data drive from a new Windows server to an orderWindows server. The hardware recognizes the drive, but the data is not visible to the OS. Which of the following is the MOST Likely cause of the issue?
An administrator notices nigh traffic on a certain subnetand wouldlike to identify the source of the traffic. Which of the following tools should the administrator utilize?
An administrator has been asked to disable CPU hyperthreading on a server to satisfy a licensing issue. Which of the following best describes how the administrator will likely perform this action?
An administrator is able to ping the default gateway and internet sites by name from a file server. The file server is not able to ping the print server by name. The administrator is able to ping the file server from the print server by both IP address and computer name. When initiating an initiating from the file server for the print server, a different IP address is returned, which of the following is MOST Likely the cause?
A systems administrator is attempting to install a package on a server. After downloading the package from the internet and trying to launch it, the installation is blocked by the antivirus on the server. Which of the following must be completed before launching the installation package again?
An application server's power cord was accidentally unplugged. After plugging the cord back in the server administrator notices some transactions were not written to the disk array. Which of the following is the MOST likely cause of the issue?
Which of the following is a system that scans outgoing email for account numbers, sensitive phrases, and other forms of Pll?
A technician learns users are unable to tog in to a Linux server with known-working LDAP credentials. The technician logs in to the server with a local account and confirms the system is functional can communicate over the network, and is configured correctly However, the server log has entries regarding Kerberos errors. Which of the following is the MOST likely source of the issue?
Which of the following cloud models is BEST described as running workloads on resources that are owned by the company and hosted in a company-owned data center, as well as on rented servers in another company's data center?
A change in policy requires a complete backup of the accounting server every seven days and a backup of modified data every day. Which of the following would be BEST to restore a full backup as quickly as possible in the event of a complete loss of server data?
A data center has 4U rack servers that needto be replaced using VMsbutwithout losingany data. Whichofthefollowingmethodswill MOST likelybe used to replace these servers?
An administrator is troubleshooting a failure in the data center in which a server shut down/turned off when utility power was lost The server had redundant power supplies. Which of the following is the MOST likely cause of this failure?
An administrator has been asked to verify that all traffic egressing from a company is secured. The administrator confirms all the information that is sent over the network is encrypted. Which of the following describes the type of traffic being encrypted?
A storage administrator needs to implement SAN-based shared storage that can transmit at 16Gb over an optical connection. Which of the following connectivity options would BEST meet this requirement?
Which of the following script types would MOST likely be used on a modern Windows server OS?
A technician installed a kernel upgrade to a Linux server. The server now crashes regularly. Which of the following is the most likely cause?
A technician has beer tasked to install a new CPU. Prior to the retaliation the server must be configured. Which of the following should the technician update?
A server administrator just installed a new physical server and needs to harden the applications on the server. Which of the following best describes a method of application hardening?
An administrator discovers a misconfiguration that impacts all servers but can be easily corrected. The administrator has a list of affected servers and a script to correct the issue. Which of the following scripting principles should the administrator use to cycle through the list of servers to deliver the needed change?
Which of the following environmental controls must be carefully researched so the control itself does not cause the destruction of the server equipment?
A server administrator wants to ensure a storage array can survive the failure of two drives without the loss of data. Which of the following RAID levels should the administrator choose?
In which of the following media rotation schemes are daily, weekly, and monthly backup media utilized in a first-in, first-out method?
An administrator needs to increase the size of an existing RAID 6 array that is running out of available space. Which of the following is the best way the administrator can perform this task?
The accounting department needs more storage and wants to retain the current data for quick read-write access. The accounting server does not have any internet drive bays available to keep both disks however the server does have USB 3 0 and eSATA ports available. Which of the following is the BEST way to accomplish the department's goals?
The management team has mandated the use of data-at-rest encryption on all corporate servers. Using this encryption paradigm will ensure:
A VLAN needs to be configured within a virtual environment for a new VM. Which of the following will ensure the VM receives a correct IP address?
A security administrator ran a port scanning tool against a virtual server that is hosting a secure website. A list of open ports was provided as documentation. The management team has requested that non-essential ports be disabled on the firewall. Which of the following ports must remain open?
An administrator is investigating several unexpected documents and video files that recently appeared in a network share. The administrator checks the properties of the files and sees the author's name on the documents is not a company employee. The administrator questions the other users, but no one knows anything about the files. The administrator then checks the log files and discovers the FTP protocol was used to copy the files to the server. Which of the following needs to be done to prevent this from happening again?
A server technician arrives at a data center to troubleshoot a physical server that is not responding to remote management software. The technician discovers the servers in the data center are not connected to a KVM switch, and their out-of-band management cards have not been configured. Which of thefollowing should the technician do to access the server for troubleshooting purposes?
A backup application is copying only changed files each time it runs. During a restore, however, only a single file is used. Which of the following backup methods does this describe?
Users report they ate unable to access an application after a recent third-party patch update. The physical server that is hosting the application keeps crashing on reboot. Although the update was installed directly from the manufacturer's support website as recommended it has now been recalled and removed from the website as the update unintentionally installed unauthorized software after a reboot. Which of the following steps should the administrator perform to restore access to the application while minimizing downtime? (Select TWO)
An organization purchased six new 4TB drives for a server. An administrator is tasked with creating an efficient RAID given the minimum disk space requirement of 19TBs. Which of the following should the administrator choose to get the most efficient use of space?
A technician has received tickets responding a server is responding slowly during business hours. Which of the following should the technician implement so the team will be informed of this behavior in real time?
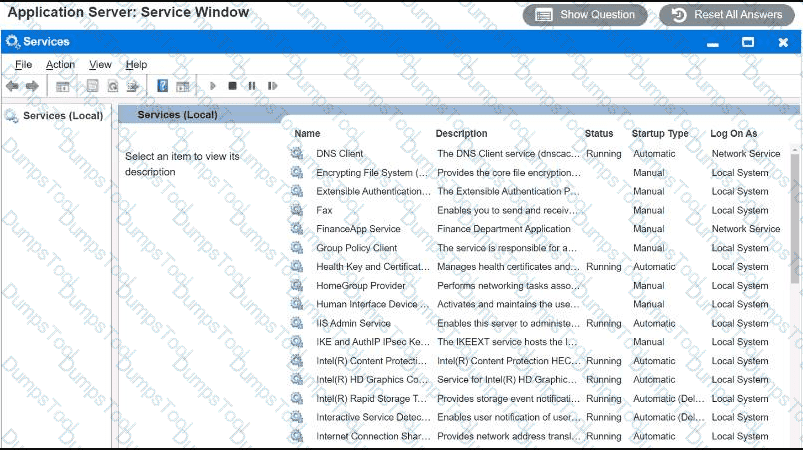
Users report that the FinanceApp software is not running, and they need immediate
access. Issues with the FinanceApp software occur every week after the IT team
completes server system updates. The users, however, do not want to contact the
help desk every time the issue occurs. The users also report the new MarketApp
software is not usable when it crashes, which can cause significant downtime. The
technician who restarted the MarketApp software noticed it is running under a test
account, which is a likely cause of the crashes.
INSTRUCTIONS
Using the Services menu provided, modify the appropriate application services to
remedy the stated issues.
A server administrator is building a pair of new storage servers. The servers will replicate; therefore, no redundancy is required, but usable capacity
must be maximized. Which of the following RAID levels should the server administrator implement?
Users are able to connect to the wireless network, but they are unable to access the internet. The network administrator verifies connectivity to all network devices, and there are no ISP outages. The server administrator removes the old address leases from the active leases pool, which allows users to access the internet. Which of the following is most likely causing the internet issue?
A systems administrator recently upgraded the memory in a server, and now the server does not turn on, and nothing is displayed on the screen.
Which of the following is the next step the administrator should take to diagnose the error without opening the machine?
A server administrator is racking new servers in a cabinet with multiple connections from the servers to power supplies and the network. Which of the following should the administrator recommend to the organization to best address this situation?
A user is unable to access the database server from a workstation. All other workstations are able to access the database server. The technician issues the following command to check the workstation:
userGhost:!# nmap localhost
Nmap scan report for localhost (127.0.0.1)
Host is up (0.001 ms latency).
Not shown: 1023 closed ports
PORT STATE SERVICE
3306 open mysql
Which of the following should the technician perform next to allow access?
A server administrator is replacing a faulty PSU. The management team has asked for a solution that prevents further downtime in the future. Which of the following can the server administrator implement?
A server recently started sending error messages about running out of memory while in use. After a maintenance period during which more memory was added, the server is still unable to consistently remain powered on. Which of the following should the technician check first?
A junior administrator reported that the website used for anti-malware updates is not working. The senior administrator then discovered all requests to the anti-malware site are being redirected to a malicious site. Which of the following tools should the senior administrator check first to identify the potential cause of the issue?
A technician is setting up a repurposed server. The minimum requirements are 2TB while ensuring the highest performance and providing support for one drive failure. The technician has the following six drives available:
500GB, 10,000rpm
600GB, 10,000rpm
500GB, 7,200rpm
500GB, 10,000rpm
600GB, 15,000rpm
600GB, 10,000rpm
Which of the following drive selections should the technician utilize to best accomplish this goal?
A server technician is installing application updates on a Linux server. When the technician tries to install a MySQL update, the GUI displays the following error message: AVC denial. Which of the following should the technician do for the MySQL update to install?
Which of the following backup types only backs up files that have changed since the last full backup?
A college is planning for disaster recovery and needs to have access at all times to student data, which contains PII (Personally Identifiable Information). Which of the following would be the most appropriate for the college?
A database developer recently requested a 4TB SATA drive utilizing spinning disks be added to an existing system for a new, heavily used database. The storage administrator turned down the request after reviewing it. Which of the following is the most likely reason the administrator did that?
A server administrator is connecting a new storage array to a server. The administrator has obtained multiple IP addresses for the array. Which of the following connection types is the server most likely using to connect to the array?
A company needs a media server set up that provides the highest availability with a minimum requirement of at least 10TB. The company purchased five HDDs, each with a 4TB
capacity. Which of the options would provide the highest fault tolerance and meet the requirements?
A server administrator is reviewing the following specifications:
VM01 Host:
CPU: 2 Physical, 4 Cores
RAM: 16GB
Storage: 16TB
Server 1 on VM01:
CPU: 1 virtual socket, 1 core per socket
RAM: 4GB
Storage: 8TB
Server 2 on VM01:
CPU: 2 virtual sockets, 2 cores per socket
RAM: 8GB
Storage: 10TB
Which of the following is described given these specifications?
An administrator has been asked to deploy a database server that provides the highest performance with fault tolerance. Which of the following RAID levels will fulfill this request?
A newly hired systems administrator is concerned about fileshare access at the company. The administrator turns on DLP for the fileshare and lets it propagate for a week. Which of the following can the administrator perform now?
Which of the following describes the concept of allocating more resources than what is available on a hypervisor?
A recently deployed server is experiencing significant connection issues after being plugged into the network switch. An administrator was asked to review the server configuration and finds the following:
10Gb server NIC with 50-micron optic installed
10m single-mode fiber patch cable to the switch
10Gb switch interface with short-range optic installed
Which of the following steps should the administrator take next?
A server administrator needs to set up active-passive load balancing for an environment with multiple network paths. The traffic should be directed to one path and switched only in the event that the original path becomes unavailable. Which of the following describes this scenario?
Three new servers that use similar types of resources need to be set up, installed with the same OS, and ready within a short time frame. Which of the following installation types would most likely be used?
Which of the following documents would explain the consequences of server downtime?
A security team must ensure that unauthorized individuals are unable to tailgate through the data center's entrance. Which of the following should be implemented to stop this type of breach from happening?
Due to a disaster incident on a primary site, corporate users are redirected to cloud services where they will be required to be authenticated just once in order to use all cloud services.
Which of the following types of authentications is described in this scenario?
After a technician upgrades the firmware on a database server that is connected to two external storage arrays, the server prompts the technician to configure RAID. The technician knows the server had several configured RAID sets and thinks the firmware upgrade cleared the RAID configurations. Which of the following should the technician do to troubleshoot this issue?
An administrator is setting up a new server and has been asked to install an operating system that does not have a GUI because the server has limited resources. Which of the
following installation options should the administrator use?
A server administrator is tasked with ensuring that information stored on company database systems is secure from bad actors. Which of the following security practices would accomplish this task?
An administrator is troubleshooting a performance issue with an application. The application performs many small reads and writes in its operation. The administrator determines that the underlying storage is currently configured to use a general-purpose array with RAID 5. Which of the following should the administrator consider doing in order to offer higher application performance yet still retain data protection?
An upper management team is investigating a security breach of the company's filesystem. It has been determined that the breach occurred within the human resources department. Which of the following was used to identify the breach in the human resources department?
An application server cannot communicate with a newly installed database server. The database server, which has static IP information, is reading the following output from ipconf ig:
The application server is reading the following output from ipconf ig:
Which of the following most likely contains an error?
An employee who was dismissed did not return company-issued equipment. Which of the following is the most important information the IT department needs to give to the legal department?
Which of the following actions should the server administrator perform on the server?
A technician is sizing a new server and, for service reasons, needs as many hot-swappable components as possible. Which of the following server components can most commonly be replaced without downtime? (Select three).
A server administrator is tasked with resolving an issue with the server's local storage. The administrator turns on the server and only two out of the four drives are found. After several reboots, an additional hard drive connects and disconnects randomly. Which of the following is most likely the cause?
A technician needs to replace two RAID controllers on a database server as part of an upgrade. The server has six external storage arrays and eight internal disks that are controlled by the two RAID controllers. The technician completes the replacement and powers the systems back on, but the server OS detects several missing disks in the configuration. Which of the following steps should the technician take first to resolve this issue?
An administrator receives an alert that one of the virtual servers has suddenly crashed. The administrator confirms the data center does not have any power failures and then connects to the remote console of the crashed server After connecting to the server console, which of the following should the administrator complete first?
A software developer is unable to reach an internal website. The developer's attempt to ping the FQDN returns the following IP address: 104.18.17.32. Which of the following is the most likely reason for this result?
A technician is installing an OS on ten servers. Which of the following media installation types would allow for the fastest installation time?
Which of the following types of asset management documentation is commonly used as a reference when processing the replacement of a faulty server component?
A server administrator is trying to determine the cause of a slowdown on a database server. Upon investigation, the administrator determines the issue is in the storage subsystem. Which of the following will most likely resolve this issue?
Which of the following should a server administrator configure to ensure access to motherboard software is restricted?
Which of the following symbols is used to write a text description per line within a PowerShell script?
A server in a remote datacenter is no longer responsive. Which of the following is the BEST solution to investigate this failure?
An administrator is unable to get server updates from a WSUS server. However, the administrator was able to patch the server successfully last month. Which of the following should the administrator check first?
A systems administrator is setting up a second VLAN for end users. Which of the following should be provisioned for a DHCP server to be able to receive client requests from a different subnet?
The management team has mandated the use of data-at-rest encryption for all data. Which of the following forms of encryption best achieves this goal?
Drive
Database
Folder
A storage administrator is configuring a new array to provide storage to a virtual cluster. The array has a built-in backup agent to allow data that is stored on the array to be backed up. The storage administrator wants the virtual cluster to use a file-based storage protocol so the backup agent can just back up the files that change and not the whole data store. Which of the following storage protocols should the administrator use?
A company recently implemented VolP across a multicampus environment with ten locations. The company uses many network technologies, including fiber,
copper, and wireless. Users calling between three of the locations have reported that voices sound strange. Which of the following should be monitored to
narrow down the issue?
A server administrator needs to implement load balancing without purchasing any new hardware or implementing any new software. Which of the following will the administrator most likely implement?
A systems administrator notices the fans are running at full speed in a newly upgraded server. Which of the following should be done to address this issue?
The internal IT department policy for monitoring server health requires that evidence of server reboots be collected and reviewed on a regular basis. Which of the following should be monitored to best provide this evidence?
A technician is connecting a server’s secondary NIC to a separate network. The technician connects the cable to the switch but then does not see any link lights on the NIC. The technician confirms there is nothing wrong on the network or with the physical connection. Which of the following should the technician perform NEXT?
A server administrator is deploying a new server that has two hard drives on which to install the OS. Which of the following RAID configurations should be used to provide redundancy for the OS?
Which of the following describes the installation of an OS contained entirely within another OS installation?
A technician wants to limit disk usage on a server. Which of the following should the technician implement?
A server technician has received reports of database update errors. The technician checks the server logs and determines the database is experiencing synchronization errors. To attempt to correct the errors, the technician should FIRST ensure: