A hardware compatibility list recommends striping with double parity as storage for an application. In a test environment, a technician realizes that a different RAID level can be used to compensate for a limited number of available disks. Which of the following is the closest RAID level the technician should deploy while minimizing the number of disks and maintaining fault tolerance?
An auditor wants to reduce the server footprint in a company’s remote datacenter to decrease hosting costs. Regarding life-cycle management, which if the following is the auditor MOST likely to look for in reviewing the company’s asset data?
A junior systems administrator wants to know which components on a server are normally hot-swappable. Which of the following components are usually hot-swappable? (Select TWO).
Which of the following involves finding and correcting the MOST important reason for performance issues?
A server technician is connecting a server to a switch in the server room. Both the server and the switch are equipped with 10 Gigabit Ethernet adapters. Which of the following cable choices would produce the BEST throughput?
Which of the following components found in a legacy server has a 16-bit bus?
Which of the following can occur if the maximum rated load is exceeded on an uninterruptible power supply (UPS)?
Which of the following server types can be configured and joined to the existing network as a read-only server for user account verification to external websites?
An IT manager noticed that specific directories’ permissions are being changed by users. Which of the following will prevent this from occurring?
A technician is implementing a RAID 10 array on a server. Which of the following is the MINIMUM number of disks needed for this array?
While reviewing a network connectivity issue to a Linux server, the systems administrator issues the ifconfig command with the following results:
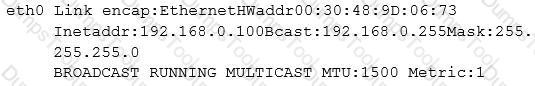
According to the output above, which of the following is the problem?
A systems administrator is installing a new software package on a server. The software has many dependencies. Which of the following would be the BEST solution for the systems administrator to take to ensure there is no downtime with the installation of this software package?
An administrator has just upgraded a server from non-hot plug storage to all hot plug storage.
The administrator powers up the server, during POST the RAID controller is recognized but none of the drive lights flash.
Which of the following should the administrator do FIRST to troubleshoot the problem?
An administrator is decommissioning a company’s old accounting system and will be sending all the hardware to an off-site recycler. Which of the following is the BEST method for the administrator to ensure no company data will be exposed before sending drives to the recycler?
A datacenter customer reports the servers are having hardware failures at an unusual rate. A server technician is dispatched to the datacenter floor and notices several racks have condensation on their cold-side doors. Which of the following is the technician likely to report as the MOST likely cause of the hardware failures?
Which of the following is used in a server to ensure proper cooling and airflow when components are removed?
A user is unable to save an image file to the home directory on a server. The server technician checks the disk space and ACL on the user’s home directory and finds that the user has enough space and required access to write to the directory. Which of the following is the MOST likely reason why the user is unable to save the file?
After installing a 1 TB hard drive, a technician notices the OS is reporting significantly less unformatted capacity than was expected. Which of the following is the root cause?
A server has two power supplies. If power is lost to the second power supply, which of the following will occur?
A small office has installed a server inside a writing closet. Users report losing connectivity to the server at various times throughout the day. Which of the following should have been considered before installing the server to prevent this issue from occurring?
An administrator is setting up LDAP in the environment to allow directory services authentication and login, and wants to allow secure connection only. Which of the following network ports should be allowed on the internal and external firewalls?
An administrator is asked to change a configuration using a GUI on a Windows server, but does not have access to a KVM. Which of the following is BEST to make the change?
In order for a server to fully function as a web server, which of the following default ports should be open? (Select TWO).
Network devices between two firewalls are included in which of the following?
Which of the following are required characteristics of database servers in high transaction environments? (Select THREE).
An administrator is tasked with deploying a server in a telephone switching station. Which of the following voltages will MOST likely be available at the facility?
An administrator is updating the server infrastructure at a company's disaster recovery site. Currently, an enormous amount of effort is required by the administrator to replicate operations. Which of the following types of site is the administrator currently using?
Which of the following methods should a technician perform to properly clear a hard drive before disposal?
A server administrator is configuring a new server for an organization. The server will function as a firewall and proxy server, as well as provide NAT services for other devices on the network. Which of the following BEST describes how the network hardware on the server should be configured?
A system administrator needs to directly control a server that has no network connectivity. Which of the following should be used to accomplish this?
Maintaining operations in the event of a complete power outage requires a tested and established:
A systems administrator is troubleshooting a server that will not turn on. The LED lights are not blinking, and no status light indicators are available. The administrator has checked the PDU and UPS to verify proper functionality. Which of the following components is the MOST likely cause of this problem?
Which of the following file types can Microsoft servers package for remote installation by default?
A technician has traveled to a company's alternate site to assess current operations of the network infrastructure. Following the assessment, the technician has informed management that everything is operational, with all applications and data mirrored. Which of the following types of site does the company have?
A technician receives an error message when trying to boot the server stating the operating system was not found. Change management logs indicate a new hard drive backplane was installed in the server last night. Which of the following should the technician do FIRST when troubleshooting the issue?
A server administrator is setting up a new set of hosts for an application that requires communication between all the hosts on a dedicated private subnet. Initially, the configuration consists of four hosts and is expected to grow to 48 total as the application is implemented for the entire company. When configuring the private subnet, which of the following CIDR netmasks would allow for the full number of hosts once the application is fully in production with the least number of unused addresses allocated?
When troubleshooting a failed backup, a technician runs the backup using the same tape but on a different tape drive in the same tape library. The backup fails again. Which of the following should be the FIRST item the technician should examine as a failure?
Two new applications have been added to a working server. The server response is now very slow. An appropriate plan of action is to:
Which of the following is an example of the principle of least privilege and is the MOST secure when granting access to a shared network drive used by the Accounting department?
Which of the following is the MOST secure method of storing critical and sensitive system information (e.g., administrative passwords, trusted signing keys)?
An organization has agreed on the software that will be used to virtualize the company's web servers. Which of the following should the administrator reference prior to purchasing physical servers to be deployed as hosts in the new virtual architecture?
A technician is experiencing overheating on a rack mounted server. After powering off and removing the cover of the server, a large amount of dust is noticed on one of the fans. After cleaning out the dust and powering the server back on, the server is still overheating. Which of the following would BEST explain this issue?
Clients cannot connect to the network. A technician determines that port 68 is not open. Which of the following protocols is being blocked?
An IT manager needs to purchase client access licenses for servers. The network has ten workstations and 100 on-site users. Which of the following licensing models should the systems administrator recommend ?
A manager notices the administrators spend a lot of time running power cords and network cables when installing new servers. The manager wants to reduce the amount of time administrators spend doing the power and network cabling. Which of the following will best allow staff to reduce that time?
An administrator receives an alert of a failed hardware component in a virtualization host running critical services. Which of the following should the administrator perform BEFORE replacing the failed component?
An administrator wants to harden the security on a web server used for e-commerce. A security scanner provides a brief summary of the web server:
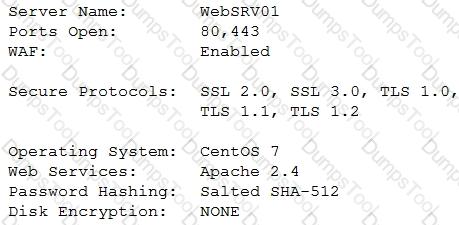
The administrator wans to provide better security for data in transit. Which of the following would BEST accomplish this?
An administrator has been given a CIDR/22 IP address block and needs to assign addresses to a multiple of virtual workstations. Which of the following servers will MOST likely perform this task?
A new server comes with four CPU sockets. Which of the following describes how many dual-core microprocessors will fit on this server?
A systems administrator wishes to improve security in a datacenter. The administrator wants to be alerted whenever a hard drive is removed from the server room. Which of the following security measures would BEST accomplish this?
A Unix server completes POST successfully. The server starts to boot but crashes and halts on a transport error. Which of the following components should a technician check FIRST?
Which of the following protocols utilize SSH and TCP over port 22 for secure communication? (Choose two.)
An administrator needs to install two hard drives in a server and configure the system for maximum
redundancy. Which of the following RAID levels would be BEST suited for the administrator?
A USB drive has been purchased to move files between Windows, *nix, and Macintosh servers. Which of the following filesystems is the BEST choice to ensure the drive can read and be written to by all of the servers?
A technician is configuring switches with SFP ports on multiple floors in a building. A switch on the first floor must be connected to a switch on the second floor for trunking VLAN traffic. Which of the following would be the MOST appropriate cable type for the technician to use?
A server technician needs to access a remote Unix server for administration. The technician has requested that ports 23, 25, and 161 be opened on the router. After the ports are opened, the technician is still unable to connect to the Unix server. Which of the following ports should be opened on the server to allow for remote administration?
When looking at an organization's file server configuration, an IT manager determines that several outages are tied to a lack of redundancy in the disk controller configuration. Which of the following features would the IT manager look for in a new configuration to correct this?
A technician needs to install six blade servers. Which of the following MUST a technician install along with the blades?
Which of the following is a reason to have a remote cold site readily available in case of a disaster in the primary datacenter?
An administrator needs to control servers locally via a console. The administrator wants a rack mounted solution for easy access. Which of the following should be installed?
A technician performs monthly backups on a file server to a NAS device that can hold 1TB of data. The size of the monthly backups has been as follows:
Month 1 = 50GB
Month 2 = 65GB
Month 3 = 80GB
Starting with Month 1, based on the current rate of growth, in how many months will the NAS run out of available storage space?
Which of the following is the MOST secure to erase data before disposal of server hard drives?
The last available backup is from 12 months ago. Which of the following should an administrator perform prior to applying a critical application patch to a guest OS? (Choose two.)
A server technician has changed a hard disk in a RAID 5 array. The array status is now reported as being in a
“degraded” state. Given this scenario, which of the following should the technician do NEXT?
A security administrator is investigating strange network behavior on a single VLAN that is used only by vendors. Which of the following tools would BEST allow the administrator to look at network traffic and investigate specific packets?
A server technician is troubleshooting an issue regarding users who are not able to access a reporting server. The reporting server has a static IP address and is connected to a Windows domain. The technician attempts steps to narrow down the issue:
Which of the following should the technician do NEXT?
An administrator attempts to install the latest security patches for an older server. When the administrator runs the patch installer, the install fails. The administrator tries again, and the installer fails again. Which of the following is the MOST likely reason for this?
A server administrator is gathering full datacenter inventory of all the server hardware to submit to the IT manager for next year’s budget for a technology refresh project. Which of the following life-cycle management stages is this?
A systems administrator is tasked to add an existing user to an existing group on a local Linux system. Which of the following files should be edited to accomplish this task?
A company has a corporate office building that is used by 50 to 100 unique visitors each day for meetings. Users routinely report that they are unable to access the network with their laptops when visiting this location.
The help desk reports that these users are not getting IP addresses automatically assigned.
After an investigation, the server administrator has determined that the DHCP service is functioning, but a minimal number of addresses are available for lease.
The building is on its own class C subnet and has 250 addresses in the scope. Which of the following represents a long term solution tothe problem?
A server with a large amount of storage but not necessarily a very fast CPU would be BEST suited for which of the following applications?
A technician troubleshooting a mail server determines that the server is low on available hard drive space and needs an additional hard drive installed. The server will need to be offline for the hardware installation. Which of the following troubleshooting steps should the technician do NEXT?
Which of the following methods should be used when classified or sensitive data is stored on a server?
Which of the following server types stores the list of network usernames and passwords required for authentication?
A company has 700 servers installed in 50 server racks in the datacenter. The Chief Technology Officer issued a memorandum to the IT department with a directive to reduce power and cooling consumptions by 50% in the datacenters. Which of the following should the system administrators recommend?
Which of the following protocols is used primarily for monitoring and managing network devices?
A server administrator is creating a design for a new datacenter. The servers should be configured for maximum availability and also provide caching for user information requests. Which of the following techniques should be used?
The logs on a server in a datacenter indicate that the server unexpectedly shut down minutes after the night cleaning crew started their shift. Which of the following is the MOST likely reason for the shut down?
A host server in a small business environment does not have virtual switching configured. The NIC on a guest is configured with an IP address that is on a different subnet from the host server. Which of the following would MOST likely happen in this case?
A user reports that a script \\Server\Share\Runme.bat, which is run on a daily basis, cannot be accessed. Which of the following is the FIRST step to take in resolving this issue?
A system administrator has just performed a backup. Which of the following should the administrator perform to easily identify the backup tape?
An administrator purchases a new server, which contains only one Xeon processor. This server is also known as a:
Users in the accounting department report that they are unable to access a shared network drive used by all departments. Upon troubleshooting, a technician determines that three users in the marketing department, two in sales, five in human resources, and ten in IT are all successfully accessing the shared network drive. Which of the following is MOST likely causing the issue?
Which of the following power plug types would MOST likely be found in a medical facility?
A server administrator is deploying a new database server and wishes to maximize the number of IOPS. Which of the following disk types would BEST accomplish this goal?
An administrator is installing a server to be used to dynamically assign IP addresses to the network devices. Which of the following server roles must be used?
A user cannot save a 2 GB file to a file server. A technician determines that permissions are correct and the file system has 10 MB of available space for new files. The technician wants to enable compression as a short-term fix. Which of the following should the technician do FIRST?
Which of the following memory technologies has the HIGHEST cost to implement?
A technician notices inlet temperatures to rack-mounted servers are significantly higher in the center of the rack as compared to the top and bottom of the rack. Which of the following is the MOST likely reason?
Which of the following are the MOST appropriate permissions to set on files required to be publicly accessible but only modified by the file’s original owner?
A new server has a battery-backed RAID controller built onto the motherboard. Which of the following will occur if the RAID controller fails?
An administrator has purchased monitoring software that can be configured to send alerts when hardware and applications are having issues. Which of the following must be installed on the monitoring server so that it can properly monitor details on vendor specific devices?
An administrator has been tasked with making recommendations for purchasing disks that will support a transactional database where performance is of greatest concern and budget is secondary. Which the following disk types should the administrator recommend?
A user is unable to save an image file to their home directory on a server. The server technician checks the disk space and ACL on the user's home directory and finds that the user has enough space and required access to write to the directory. Which of the following is the MOST likely reason why the user is unable to save the file?
A storage administrator needs to connect a server to a storage array shared by 12 other servers. Which of the following interface types could be used to accomplish this connection?
A new version of the primary OS used by a company has been released. Due to some significant changes in the OS, a system administrator wants to see which remotely accessible services are enabled by default to access the security risk prior to upgrading to the new version. Which of the following utilities should the administrator use?
An administrator receives multiple reports that users cannot access a secure website hosted on a server the administrator manages. The administrator investigates and discovers that the reason users cannot access the secure site is because:
A newly hired administrator is tasked to change the number of CPUs assigned to a VM. Which of the following if the FIRST step the administrator should do during a scheduled maintenance window?
An administrator thinks that a particular network connection is dropping packets. Which of the following tools would the administrator use to BEST identify where the packets are being dropped?
Multiple users report that an application attempting to open a file retrieved from a server reports that the file is corrupted. Which of the following applications can be used on the server to verify file integrity?
Which of the following MUST be configured to automate client deployment over PXE boot? (Choose two.)
An outside contractor is hired to perform a business impact analysis of a simulated disaster. The contractor asks stakeholders what they think a hurricane would do to the business. This is an inadequate method because:
Which of the following default ports should be open on a server for remote administration?
Which of the following troubleshooting methods would be performed after resolving an issue?
A technician needs to install another PCle NIC in a server. The server currently has four fully populated PCle slots. Which of the following must the technician install before installing the card?