During the firmware upgrade of a web server, a power outage occurred. The outage caused a failure within the upgrade. Which of the following plans must be implemented to revert back to the most recent version of the firmware?
Joe. an end user, just changed his network password A pop-up box appears a few minutes later, prompting him to enter his password. Joe enters his new network password and is able to continue working. A few minutes later, the same pop-up box appears again, asking him to enter his network password. Which of the following Control Panel utilities can Joe use to help with this situation?
A technician is attempting to repair a Windows computer that is infected with malware. The machine is quarantined but still cannot boot into a standard desktop. Which of the following is the most likely NEXT step?
Joe, a customer, has informed a Tier 2 help desk technician that a computer will not boot up. After about ten minutes of troubleshooting, Joe is increasingly concerned and claims that the technician is wasting his time because he has already tried everything that has been suggested.
Which of the following should the technician do?
An administrator created a documents that shows network equipment connections, including endpoints, server, routers, and switches. Which of the following documents did the administrator create?
A user receives the following error message while browsing the Internet on a PC: The connection is not private. Upon inspection, a technician discovers the issue only occurs on the user’s banking website, and the issue can be duplicated on another PC. The function to view the certificate shows it is valid and has yesterday’s date as the expiration. Which of the following should the technician do NEXT?
Which of the following physical security measures is intended to mitigate tailgating?
An end user is browsing the Internet when multiple browser pages open by themselves. The user notices the PC is running slowly, even while not browsing the internet. Which of the following actions should the user take?
A small business has an open wireless network so vendors can connect to the network without logging in. The business owners are concerned that a nearby company is connecting and using the wireless connection without permission. If the small business requires that the network remain open, which of the following configuration settings should be changed to address these concerns?
A user’s computer is displaying a black screen. The technician restarts the computer, but the OS still does not load. The technician discovers the OS was patched the previous evening.
Which of the following should the technician attempt NEXT?
A technician is troubleshooting a home WiFi router that is used by a small company of 30 employees. The business is experiencing intermittent wireless connectivity issues. Which of the following is the MOST likely cause of the issues'?
Which of the following may include the use of a password and a rotating PIN lo access a wireless network?
A user’s login screen does not look normal when booting the computer. A technician states the computer was showing the company’s workstation imaging system screen, but it has since been fixed. Which of the following did the technician update?
A technician performs a risk assessment and determines a requested change has low risk and low impact. Which of the following best practices should the technician follow to proceed with implementing the change?
Ann, an employee at a company, calls the help disk to report issues logging on to a vendor’s website. Joe, the technician, is able to log in successfully with his credentials before going to Ann’s office. However, when he attempts to log in from Ann’s office, Joe experiences the same issue. Ann asks Joe questions about the new software installed on the laptop from the pop-up notification.
Which of the following are the NEXT steps Joe should take to resolve the issue? (Select two.)
A SOHO customer has recently experienced a major hurricane. The customer has no backups and has lost all data and hardware associated with the company. The customer calls a contractor to assist in the rebuilding process and needs suggestions on the best way to prevent this from happening again. Which of the following recommendations should the contractor give to the customer? (Select two.)
A technician has set up a new computer for a customer and needs to add a login with administrative privileges. Which of the following tools should the technician use?
Following instructions from the help desk, a company employee turns off a workstation that has a suspected ransomware infection. A technician is dispatched later to investigate the workstation Which of the following should the technician perform FIRST?
A user in a SOHO wants to allow Joe, a remote technician, to connect securely to the user's workstation Joe informs the user that the VPN was successful, but he still cannot connect. Which of the following settings in the SOHO router MOST likely need to be adjusted?
Which of the following is a community supported, open source OS used for both services and workstations?
An end user’s PC is taking a long time to boot. Which of the following operations would be the BEST to resolve this issue with minimal expense? (Select two.)
A manager requests remote access to a server after hours and on weekends to check data. The manager insists on using the server. Before granting the access, which of the following is the MOST important step a technician can take to protect against possible infection?
A company’s security policy does not allow USB drives to be available in workstations. However, an exception needs to be made for a user. The network administrator changes the policy for the user. Which of the following commands should the administrator run on the user’s workstation?
A project team is organized to implement a new wireless solution for a school. The team has already done the network diagrams and knows the locations that will need to be addressed in the project. The team is in the process of creating an SOW for the project as a whole and needs to add the critical pieces to the SOW to complete it and move to the next stage.
Which of the following would the project team MOST likely add to the SOW?
A technician is troubleshooting a computer that may have some corrupt operating system files. Which of the following command line tools should the technician use to check these files?
A corporate fileshare holds files for multiple departments. Individual users in each department create reports
that are meant to be read by the rest of the company. Recently, a user ran a malicious executable that
encrypted all of the documents on the fileshare. The software asked for money to be transferred via
cryptocurrency in order to decrypt the files; however, the files were not decrypted after the company paid the
ransom. Which of the following would MOST likely minimize the damage to a fileshare in this type of situation?
A technician is troubleshooting an issue affecting all company laptops. All the laptops have exactly the same hardware. The screens present glitches every time the users move their mouse pointers over the screen. The technician discovers there was a recent OS update deployed throughout the company, which includes new versions for video drivers. Restarting the laptop in safe mode will not present the issue. Which of the following should the technician do NEXT?
A user recently connected a Windows laptop to a free WiFi hot-spot. After returning to the office, the user cannot access network shares. Which of the following is the MOST likely cause?
Which of the following operating systems has versions for servers, workstations, and phones?
A user's smartphone began experiencing decreased performance after the user watched some videos, browsed the web, and accessed the application store. The user states the phone was.
working fine beforehand. Which of the following should be done FIRST to resolve the issue?
A Microsoft application will not open when a user clicks on it. Instead, the following error message pops up: This application has crashed. Would you like to send an error report to Microsoft? Which of the following should the user try FIRST
Joe, a user, returns his computer to the technician who performed a virus removal on it the week before. Joe states that several symptoms have returned.
Which of the following should the technician have covered previously as part of the original repair?
Ann, a user, has purchased a new Android phone and is attempting to access a public hot-spot. When she gets a message indicating the page cannot be displayed. She notices there is a “?” in the radio icon in the toolbar.
She has verified Bluetooth is active, airplane mode is off, and tethering is turned on. She uses the cell phone to call a technician for assistance. Which of the following is the MOST likely issue Ann is experiencing?
A user’s corporate email is missing the shared inbox folders that were present before the user went on vacation. The technician verifies the user is connected to the domain and can still send and receive email. Which of the following is MOST likely causing the missing folders issue?
A technician is working at a help-desk form and receives a call from a user who has experienced repeated BSODs. The technician is scheduled to take a break just after the call comes in. Which of the following is the
BEST choice for the technician to make?
A SOHO technician needs to upgrade two computers quickly and is not concerned about retaining user settings. The users currently have Windows 8 and want to upgrade to Windows 10.
Which of the following installation methods would the technician MOST likely use to accomplish this quickly?
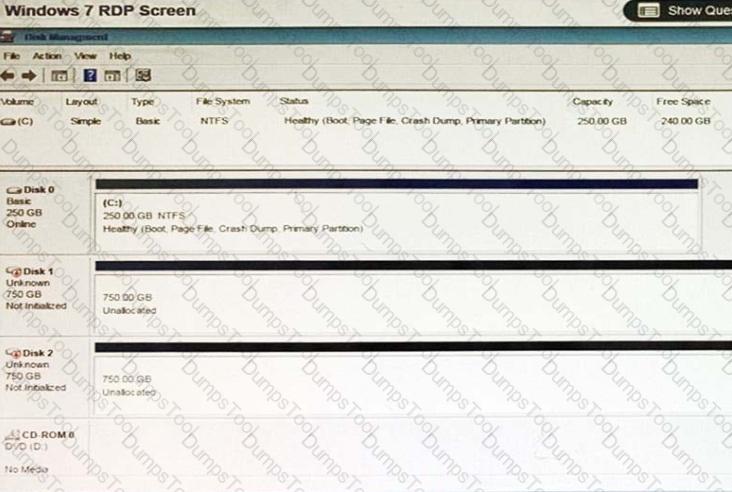
A user has installed two new drives in one of the computers in the computer lab and has been unable to format Disk1 from the command prompt.
The lab requires that Disk1 be a dynamic disk configured with two partitions. The first partition must be 256,000 MB in size and mapped to drive F. The second partition must be 512,000 MB in size and mapped to drive G.
The new partitions must be formatted to ensure that user’s files can be secured from other users and that the disk must be configured to account for future redundancy.
Make sure to maintain a consistent file system.
INSTRUCTIONS:
Conduct the necessary steps within the Disk Manager to accomplish these tasks.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A user tries to open a client/server application, but a prompt appears for the username and password The user is able to open and use the email client with no issues. The user's workstation is a loaner laptop Everyone at the company is given administrator rights on their individual workstations. Which of the following is MOST likely preventing the user from running this program?
Ann, an end user, is working with highly regulated data and often notices the high volume of traffic in her work area. Ann requests help with limiting the exposure of data as people walk by.
Which of the following security measures should be used?
A client wants a technician to create a PC naming convention that will make the client’s PCs easier to track and identify while in use. Which of the following naming convention formats should the technician follow?
A technician performs a virus cleaning on a computer that has been redirecting all browsers to a phishing website. System Restore was turned off before the cleaning. The technician runs the machine through several scanners, and then tests for redirection. A smaller number of sites are still redirecting to the phishing website. The antivirus software correctly blocks the website. Which of the following should the technician do NEXT?
Which of the following is the maximum RAM limit of a Windows 32-bit version?
A technician is repairing a computer. Which of the following should the technician do to protect the computer from accidental voltage spikes?
An employee contacts the help desk because the battery in a company-provided smartphone lasts only a short period of time when the worker is in the office. Which of the following would MOST likely reduce this symptom? (Select TWO).
Joe. a customer, requests to have a technician rename his laptop to the name of his favorite sports team. Which of the following documents MUST the technician consider before performing this action?
A large corporation wants to secure its wireless network so only employees can connect. Which of the following technologies should be used to control access by user account?
A technician is setting up a SOHO wireless network for a healthcare office that does not have a server. The user requires the highest level of wireless security and various levels of desktop authentication to access cloud resources.
Which of the following protocols and authentication methods should the technician implement? (Select two.)
A technician wants to write a script that will check data line by line until the end of the file. Which of the following elements will perform the check?
A technician is deploying a PXE installation of a new OS onto a small group of company workstations. Which
of the following should the technician monitor during the installation?
A company needs to destroy several SSDs that contain sensitive information. Which of the following methods
is BEST suited for the total destruction of the SSDs?
A user wants to see the workstations present on the LAN in a workgroup environment. Which of the following
settings must be enabled to make this possible?
A technician wants to deploy a solution to manage a computer remotely. The technician is not allowed to modify any network configuration and is not able to forward any ports on the router to internal devices. Which of the following remote access technologies would be BEST suited for this situation?
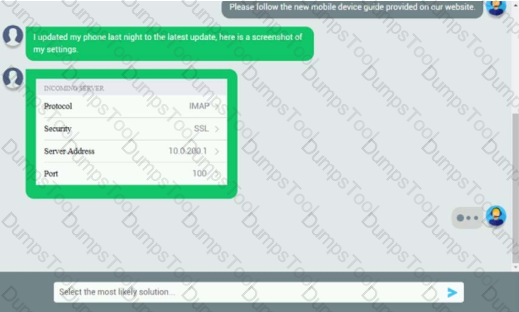
An executive has contacted you through the help-desk chat support about an issue with a mobile device.
Assist the executive to help resolve the issue.
INSTRUCTIONS
Select the MOST appropriate statement for each response.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Let’s take a look at your phone settings.
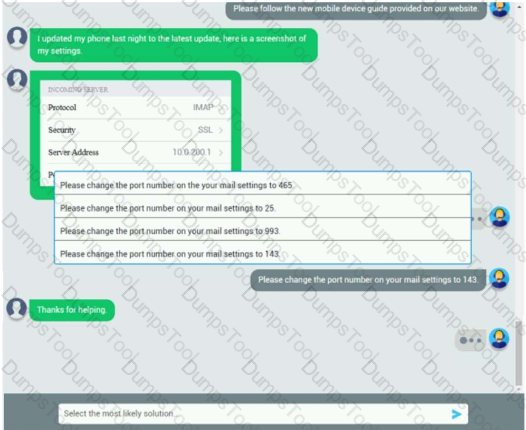
Please change the port number on your mail settings to 993.
Which of the following should be done NEXT?
A user is surprised that a newly installed third-party smartphone application requires permissions to access the camera, location, and microphone. Unaware of a reason why permissions are needed for the application to function as advertised, the user contacts the help desk for assistance. Which of the following should the help desk team recommend the user do in this situation?
A technician needs to manage a Linux workstation remotely. This workstation contains highly sensitive data, and therefore, it must be accessed in the most secure method possible Which of the following technologies should the technician use to manage this system?
A technician is having issues with the WiFi connection while working on a Mac. The technician wants to check which SSID the computer is connected to and some statistics about the connection. Which of the following terminal commands should the technician use?
Which of the following key and mouse combinations can be used to run an application as a different user?
Company policy states that users must secure their laptops before leaving the office for the evening Which of the following physical security measures should be used?
A customer is having issues with an Android-based smartphone after a recent application update. The application becomes unresponsive immediately after attempting to open it. Auto-sync is not enabled, and no recent backups exist for the smartphone. Without losing any critical information, which of the following should be performed NEXT to further troubleshoot the issue? (Choose two.)
A user has changed the MAC address of a laptop to gain access to a network. This is an instance of:
Several mobile users are reporting issues connecting to the WLAN within a warehouse. A technician tests wireless connectivity in the lobby and is able to connect successfully. Mobile users can connect to the Internet using cellular service, but they cannot access any internal resources on the WLAN The technician received alerts of devices failing throughout the network due to a power outage Which of the following is MOST likely causing the wireless issues?
A Linux user wants to use the grep command to identify every file name in the current directory that contains the word "mandatory." Which of the following commands would BEST accomplish this?
A technician is using a CLI to perform tasks on a Windows OS. The technician needs to determine which ports are being utilized for TCP listening. Which of the following commands should the technician use?
Which of the following operating systems utilizes the web browser named Edge, replacing its older browser software?
After a virus outbreak due to USB usage, a technician must deny users access to removable hard drives via USB ports as soon as possible. The technician has been asked to avoid interrupting any users Which of the following is the BEST way for the technician to perform this security feature?
A user brings in a home desktop computer for cleaning. Upon opening the computer, a technician finds large amounts of dust and dirt inside. Which of the following should the technician use to remove the excess dust and dirt?
A user receives an email on a company smartphone. When trying to open the email, the user gets a message stating the email is encrypted, and the user cannot open it. The user forwards the email to a personal email account and receives the same message. The user calls the IT department to ask for help. To decrypt the message, the technician tells the user to contact the sender of the message to be able to exchange:
During a network server outage, the administrators computer received an IP address of 169.254.0.10 and had no access to internal or external resources. Which of the following should be configured to ensure the administrator's computer retains network access?
A network support technician takes a call from an office manager who wants to change the wireless security
key on the access point in that particular office. The office manager explains that a label on the access point
indicates it has an IP address of 10.0.100.2. Which of the following should the technician use to connect
securely to the access point to make the change?
Joe, a user, believes his computer is infected with malware. The device is having difficulty accessing some
websites, and web services are not responding from any of the web browsers, although Joe can access these
services from his smartphone without issue. The computer’s malware scanner has the latest definitions
installed. Which of the following would BEST explain why the computer is functioning this way?
A Mac user needs to configure a network device using a serial connection to enable a remote network connection. Which of the following utilities would MOST likely be used to make the necessary changes?
While installing a hard drive in a server, the administrator installs an extra physical hard disk Which of the following technologies will allow the administrator to extend an existing volume onto the extra disk?
An administrator is investigating intermittent, slow performance of a web server. The administrator performs a virus scan on the server but finds there is no infection present. Which of the following should the administrator do NEXT to mitigate the issue?
A home user reports slow computer performance and application crashes after clicking a "repair" button on a pop-up warning while browsing the Internet Which of the following are the FIRST steps a technician should take to identify and resolve the issue? (Select TWO).
Which of the following would BEST support an 8TB hard drive with one partition?
A user is trying to access a popular email website but is being redirected to a different website that asks for login credentials. The user calls a technician, who promptly notices a security issue. Which of the following should the technician do to remove the threat from the system?
A technician receives a security alert stating a vendor has left a Keylogger on certain systems that shipped configured from the factory. The technician needs to research the system model numbers to determine if any production computers are affected. II the technician finds vulnerable systems, which of the following is the BEST method to remove the Keylogger?
Which of the following would MOST likely be used by an attacker to identify the hash value of a strong password quickly?
Which of the following wireless encryption standards uses 802.1X In its process to secure a wireless network?
A user downloaded a program from a website. After saving the file, the user cannot find the executable. Which of the following is MOST likely the cause?
A new security policy stores all remote access to network devices must be performed using secure connections whenever possible. Which of the following remote access technologies would a technician MOST likely use to manage a Windows-based device remote without using a CLI?
Ann, a user, is attempting to log in to her email service form a third-party email client on her phone. When Ann enters her usual username and password, she receives an error message saying the credentials are invalid.
Ann then decides to reset her email password, but after the reset, the new credentials still do not work in the third-party email client.
Which of the following settings or features is responsible for the problems Ann is experiencing?
Joe, a systems administrator, is setting up a risk management plan for the IT department. Part of the plan is to take daily backups of all servers. The server backups will be saved locally to NAS.
Which of the following can Joe do to ensure the backups will work if needed?
A folder has the share permissions of everyone - change, while the folder's NTFS permissions are Set to everyone - read. Which of the following would be the MOST effective permissions for someone who is accessing
the folder via the share?
A technician is implementing a change to a piece of production environment. The change is causing other several other problem to occur. Which of the following should the technician do NEXT?
A user is working with the command line interface on a Linux computer To show the contents of the current directory, which of the following commands should be used'
A technician is updating a network switch at a location facility. The technician needs to ensure the data is not sent in plaintext over untrusted networks. Which of the following should the technician use? (Choose two.)
A user's PC has become infected with malware that has a known remediation, Which of the fallowing would MOST likely prevent this from happening again?
A network administrator audited applications on a user's desktop and noticed a program used to sync a mobile device to the desktop's calendar To ensure corporate data is not exchanged to cloud servers, which of the following mobile security methods should be implemented?
A security learn recommends a disaster recovery plan with the following requirements:
* Recent backups should be readily available.
* Only long-term backups should be stored off premises
* There should be minimum expenditure on hardware.
Which of the following satisfies all of these requirements?
After purchasing an Ultrabook. Ann. a home user, has a technician come to her home and install an operating system. Which of the following OS retaliation methods will the technician MOST likely use?
After installing an application on a smartphone, a user starts receiving pop-up ads for recently visited physical stores. The user also receives prompts to install other applications. Which of the following permissions should be revoked to disable the unwanted notifications?
Which of the following filesystem types has native read/write support on all desktop operating systems?
A user opens a phishing email and types logon credentials into a fake banking website. The computer's antivirus software then reports it has several
from the network. Which of the following should the technician perform NEXT?
A Have the user change the password.
B. Update the antivirus software and run scans.
C. Disable the user's local computer account.
D. Quarantine the phishing email.