A technician is troubleshooting a user’s PC that is displaying pop-up windows, which are advertising free software downloads. When the technician tries to open a document, the system displays an error message that reads: Not enough memory to perform this operation. Which of the following should be the technician's next step to resolve this issue?
A technician needs to update the software on several hundred Mac laptops. Which of the following is the best method to complete the task?
Which of the following operating systems were designed for smartphones? (Select two).
Multiple users routinely record log-in information in readily accessible areas. Which of the following is the best way to mitigate this issue?
A technician is doing a bare-metal installation of the Windows 10 operating system. Which of the following prerequisites must be in place before the technician can start the installation process?
A company downloads a large number of files over the internet daily. The company needs a way to ensure the files have not been modified or corrupted during the download process. Which of the following should the company do to verify the files?
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users' audio issues are
resolved using best practice procedures.
Multiple devices may be selected for quarantine.
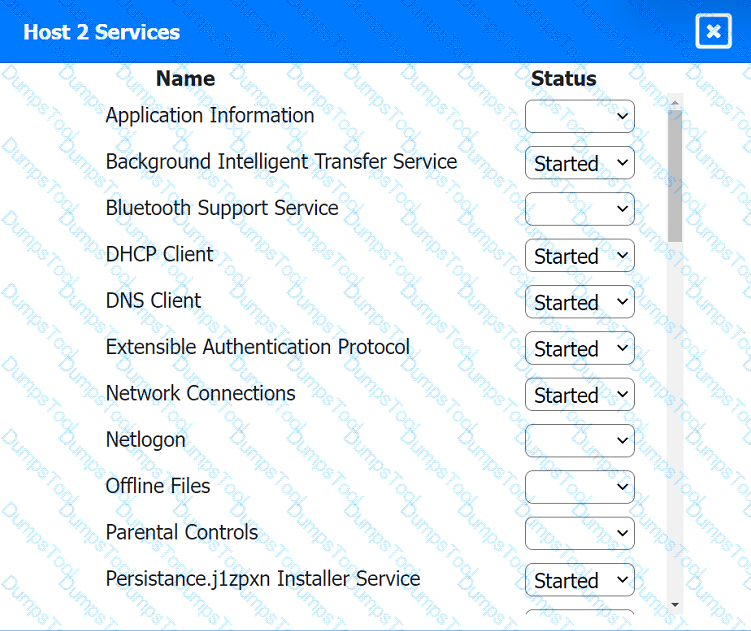
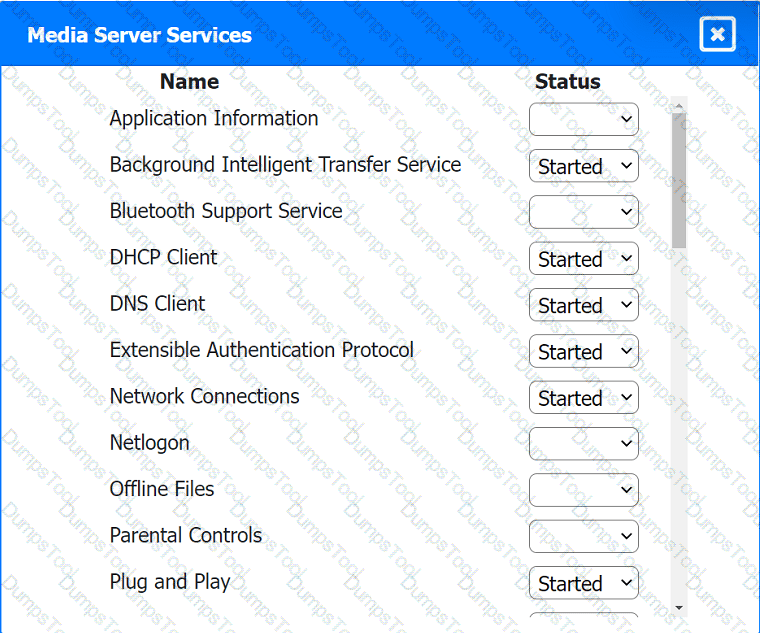
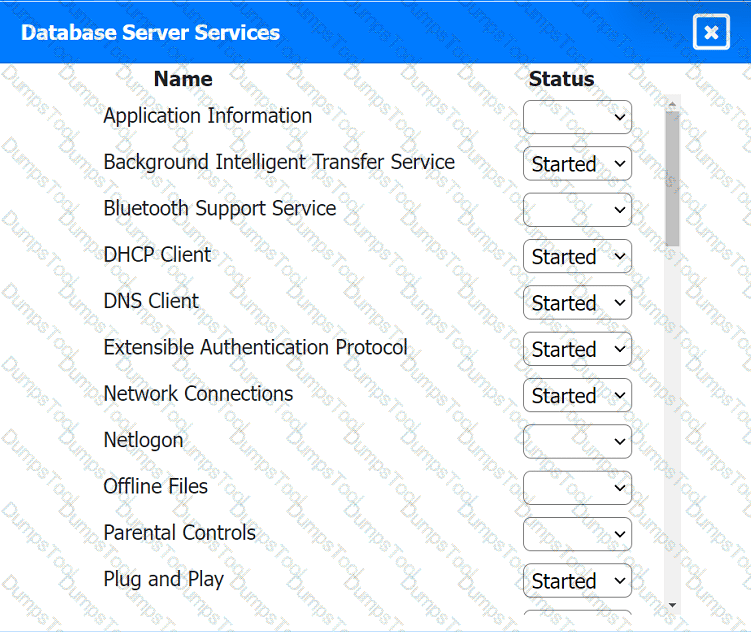
Click on a host or server to configure services.
A workstation's hard drive is making loud noises, applications are running slowly, and the workstation is rebooting unexpectedly. Which of the following should the technician do first to begin troubleshooting the issue?
A company discovered that numerous computers from multiple geographic locations are sending a very high number of connection requests which is causing the company’s web server to become unavailable to the general public. Which of the following attacks is occurring?
A technician is troubleshooting a customer's PC and receives a phone call. The technician does not take the call and sets the phone to silent. Which of the following BEST describes the technician's actions?
A technician is working to resolve a Wi-Fi network issue at a doctor's office that is located next to an apartment complex. The technician discovers that employees and patients are not the only people on the network. Which of the following should the technician do to BEST minimize this issue?
A network administrator is deploying a client certificate to be used for Wi-Fi access for all devices in an organization. The certificate will be used in conjunction with the user's existing username and password. Which of the following BEST describes the security benefits realized after this deployment?
A user is attempting to browse the internet using Internet Explorer. When trying to load a familiar web page, the user is unexpectedly redirected to an unfamiliar website. Which of the following would MOST likely solve the issue?
A Microsoft Windows PC needs to be set up for a user at a targe corporation. The user will need access to the corporate domain to access email and shared drives. Which of the following versions of Windows would a technician MOST likely deploy for the user?
A macOS user reports seeing a spinning round cursor on a program that appears to be frozen. Which of the following methods does the technician use to force the program to close in macOS?
A user is being directed by the help desk to look up a Windows PC's network name so the help desk can use a remote administration tool to assist the user. Which of the following commands would allow the user to give the technician the correct information? (Select TWO).
A new spam gateway was recently deployed at a small business However; users still occasionally receive spam. The management team is concerned that users will open the messages and potentially
infect the network systems. Which of the following is the MOST effective method for dealing with this Issue?
A user receives a notification indicating the data plan on the user's corporate phone has reached its limit. The user has also noted the performance of the phone is abnormally slow. A technician discovers a third-party GPS application was installed on the phone. Which of the following is the MOST likely cause?
A mobile phone user has downloaded a new payment application that allows payments to be made with a mobile device. The user attempts to use the device at a payment terminal but is unable to do so successfully. The user contacts a help desk technician to report the issue. Which of the following should the technician confirm NEXT as part of the troubleshooting process?
A user is unable to access a website, which is widely used across the organization, and receives the following error message:
The security certificate presented by this website has expired or is not yet valid.
The technician confirms the website works when accessing it from another computer but not from the user's computer. Which of the following should the technician perform NEXT to troubleshoot the issue?
Which of the following is a data security standard for protecting credit cards?
A bank would like to enhance building security in order to prevent vehicles from driving into the building while also maintaining easy access for customers. Which of the following BEST addresses this need?
The web browsing speed on a customer's mobile phone slows down every few weeks and then returns to normal after three or four days. Restarting the device does not usually restore performance. Which of the following should a technician check FIRST to troubleshoot this issue?
A company is deploying mobile phones on a one-to-one basis, but the IT manager is concerned that users will root/jailbreak their phones. Which of the following technologies can be implemented to prevent this issue?
A technician is setting up a new laptop. The company's security policy states that users cannot install virtual machines. Which of the following should the technician implement to prevent users from enabling virtual technology on their laptops?
A user in a corporate office reports the inability to connect to any network drives. No other users have reported this issue. Which of the following is the MOST likely reason the user is having this issue?
A technician needs to manually set an IP address on a computer that is running macOS. Which of the following commands should the technician use?
A user received the following error upon visiting a banking website:
The security presented by website was issued a different website' s address .
A technician should instruct the user to:
A systems administrator is setting up a Windows computer for a new user Corporate policy requires a least privilege environment. The user will need to access advanced features and configuration settings for several applications. Which of the following BEST describes the account access level the user will need?
A user reports a computer is running slow. Which of the following tools will help a technician identity the issued
A technician has spent hours trying to resolve a computer issue for the company's Chief Executive Officer (CEO). The CEO needs the device returned as soon as possible. Which of the following steps should the technician take NEXT?
Upon downloading a new ISO, an administrator is presented with the following string:
59d15a16ce90cBcc97fa7c211b767aB
Which of the following BEST describes the purpose of this string?
A technician found that an employee is mining cryptocurrency on a work desktop. The company has decided that this action violates its guidelines. Which of the following should be updated to reflect this new requirement?
A wireless network is set up, but it is experiencing some interference from other nearby SSIDs. Which of the following can BEST resolve the interference?
A user reports that text on the screen is too small. The user would like to make the text larger and easier to see. Which of the following is the BEST way for the user to increase the size of text, applications, and other items using the Windows 10 Settings tool?
The network was breached over the weekend System logs indicate that a single user's account was successfully breached after 500 attempts with a dictionary attack. Which of the following would BEST mitigate this threat?
A technician has been tasked with installing a workstation that will be used tor point-of-sale transactions. The point-of-sale system will process credit cards and loyalty cards. Which of the following encryption technologies should be used to secure the workstation in case of theft?
An incident handler needs to preserve evidence for possible litigation. Which of the following will the incident handler MOST likely do to preserve the evidence?
An organization is centralizing support functions and requires the ability to support a remote user's desktop. Which of the following technologies will allow a technician to see the issue along with the user?
A change advisory board just approved a change request. Which of the following is the MOST likely next step in the change process?
A user reports that a workstation is operating sluggishly Several other users operate on the same workstation and have reported that the workstation is operating normally. The systems administrator has validated that the workstation functions normally. Which of the following steps should the systems administrator most likely attempt NEXT?
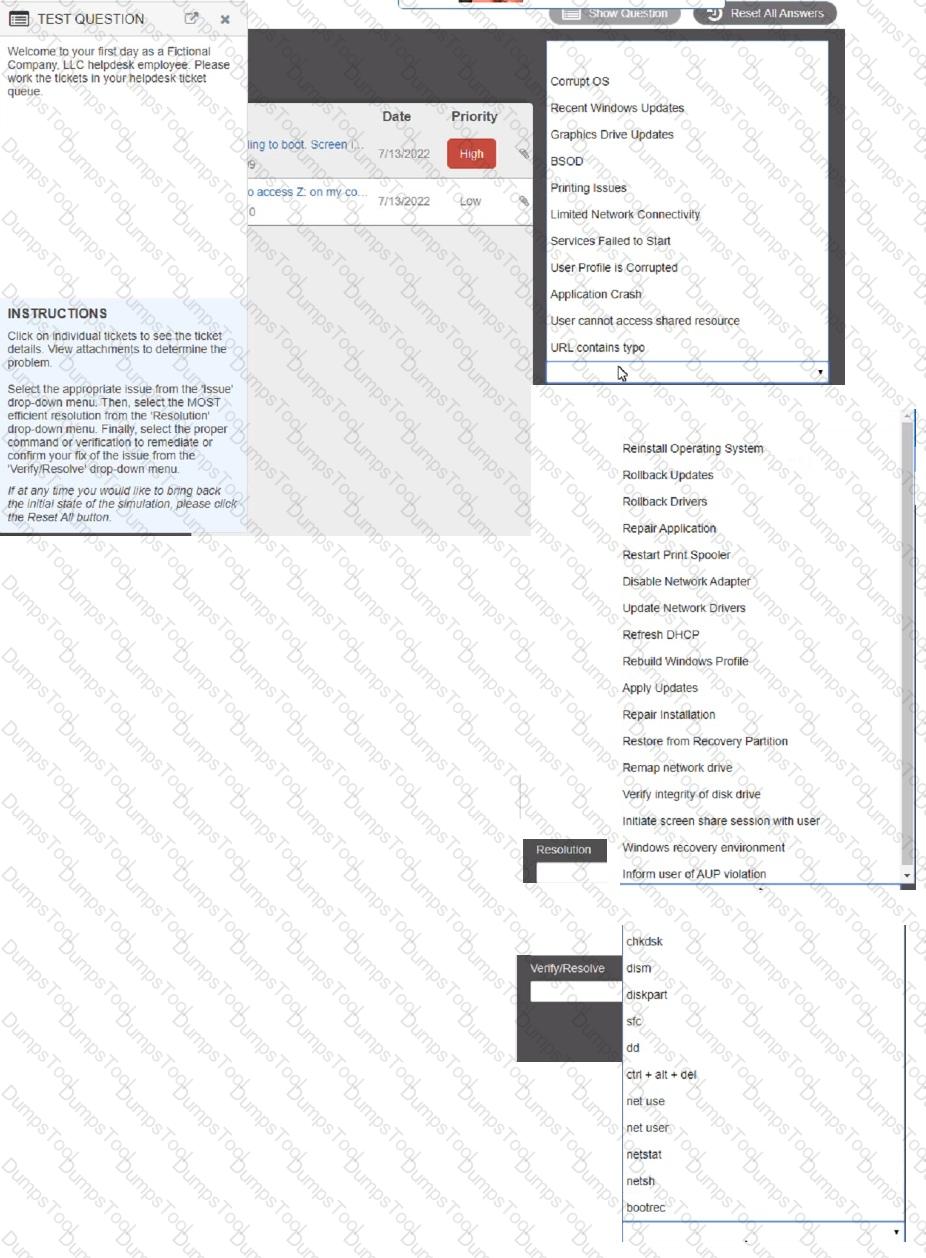
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.
A technician is replacing the processor in a desktop computer prior to opening the computer, the technician wants to ensure the internal components are protected. Which of the following safety procedures would BEST protect the components in the PC? (Select TWO).
A technician receives a ticket indicating the user cannot resolve external web pages However, specific IP addresses are working. Which of the following does the technician MOST likely need to change on the workstation to resolve the issue?
A technician has been tasked with using the fastest and most secure method of logging in to laptops. Which of the following log-in options meets these requirements?
Which of the following OS types provides a lightweight option for workstations thai need an easy-to-use browser-based interface?
A user contacted the help desk to report pop-ups on a company workstation indicating the computer has been infected with 137 viruses and payment is needed to remove them. The user thought the company-provided antivirus software would prevent this issue. The help desk ticket states that the user only receives these messages when first opening the web browser. Which of the following steps would MOST likely resolve the issue? (Select TWO)
A technician needs to document who had possession of evidence at every step of the process. Which of the following does this process describe?
A technician is unable to join a Windows 10 laptop to a domain Which of the following is the MOST likely reason?
A company needs to securely dispose of data stored on optical discs. Which of the following is the MOST effective method to accomplish this task?
A customer reported that a home PC with Windows 10 installed in the default configuration is having issues loading applications after a reboot occurred in the middle of the night. Which of the following is the FIRST step in troubleshooting?
A technician is installing new software on a macOS computer. Which of the following file types will the technician MOST likely use?
Which of the following is the MOST important environmental concern inside a data center?
A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message and no changes have been made within the company. Which of the following has infected the computer?
Which of the following Linux commands would be used to install an application?
A network administrator is deploying a client certificate lo be used for Wi-Fi access for all devices m an organization The certificate will be used in conjunction with the user's existing username and password Which of the following BEST describes the security benefits realized after this deployment?
A technician needs to formal a USB drive to transfer 20GB of data from a Linux computer to a Windows computer. Which of the following filesystems will the technician MOST likely use?
The command cac cor.ptia. txt was issued on a Linux terminal. Which of the following results should be expected?
A technician is asked to resize a partition on the internal storage drive of a computer running macOS. Which of the followings tools should the technician use to accomplish this task?
An Android user reports that when attempting to open the company's proprietary mobile application it immediately doses. The user states that the issue persists, even after rebooting the phone. The application contains critical information that cannot be lost. Which of the following steps should a systems administrator attempt FIRST?
A technician suspects the boot disk of a user's computer contains bad sectors. Which of the following should the technician verify in the command prompt to address the issue without making any changes?
A company is Issuing smartphones to employees and needs to ensure data is secure if the devices are lost or stolen. Which of the following provides the BEST solution?
Which of the following operating systems is most commonly used in embedded systems?
A Chief Executive Officer has learned that an exploit has been identified on the web server software, and a patch is not available yet. Which of the following attacks MOST likely occurred?
Which of the following Windows 10 editions is the most appropriate for a single user who wants to encrypt a hard drive with BitLocker?
A user's company phone was stolen. Which of the following should a technician do next?
A technician requires graphical remote access to various Windows, Linux, and macOS desktops on the company LAN. The security administrator asks the technician to utilize a single software solution that does not require an external internet connection. Which of the following remote access tools is the technician most likely to install?
A network technician is deploying a new machine in a small branch office that does not have a DHCP server. The new machine automatically receives the IP address of 169.254.0.2 and is unable to communicate with the rest of the network. Which of the following would restore communication?
Static entry
Which of the following should be documented to ensure that the change management plan is followed?
A help desk technician needs to remotely access and control a customer's Windows PC by using a secure session that allows the technician the same control as the customer. Which of the following tools provides this type of access?
A branch office suspects a machine contains ransomware. Which of the following mitigation steps should a technician take first?
A technician wants to install Developer Mode on a Windows laptop but is receiving a "failed to install package" message. Which of the following should the technician do first?
A student is setting up a new Windows 10 laptop for the upcoming semester. The student is interested in customizing the wallpaper. Which of the following should the student use to change the wallpaper?
Which of the following file types would be used in the Windows Startup folder to automate copying a personal storage table (.pst file) to a network drive at log-in?
Which of the following involves sending arbitrary characters in a web page request?
Which of the following is the best way to limit the loss of confidential data if an employee's company smartphone is lost or stolen?
Which of the following items require special e-waste recycling? (Select two).
Solid-state drive
Which of the following file extensions should a technician use for a PowerShell script?
A user reports a hardware issue to the help desk. Which of the following should the help desk technician do first when responding to the user?
An IT technician is attempting to access a user's workstation on the corporate network but needs more information from the user before an invitation can be sent. Which of the following command-line tools should the technician instruct the user to run?
A large company is changing its password length requirements. The Chief Information Officer is mandating that passwords now be at least 12 characters long, instead of 10. Which of the following should be used to adjust this setting?
Group Policy
A technician is troubleshooting a PC because the user has reported strange pop-up windows and computer performance issues. Which of the following actions should the technician take next?
A technician needs to track evidence for a forensic investigation on a Windows computer. Which of the following describes this process?
A technician is creating a location on a Windows workstation for a customer to store meeting minutes. Which of the following commands should the technician use?
A technician receives an invalid certificate error when visiting a website. Other workstations on the same local network are unable to replicate this issue. Which of the following is most likely causing the issue?
Which of the following would allow physical access to a restricted area while maintaining a record of events?
A remote user's smartphone is performing very slowly. The user notices that the performance improves slightly after rebooting but then reverts back to performing slowly. The user also notices that the phone does not get any faster after connecting to the company's corporate guest network. A technician sees that the phone has a large number of applications installed on it. Which of the following is the most likely cause of the issue?
An organization is creating guidelines for the incorporation of generative Al solutions. In which of the following would these guidelines be published?
Standard operating procedure
A user reports that an air-gapped computer may have been infected with a virus after the user transferred files from a USB drive. The technician runs a computer scan with Windows Defender but does not find an infection. Which of the following actions should the technician take next? (Select two).
A remote user contacts the help desk about an email that appears to be distorted. The technician is unsure what the user means and needs to view the email to assist with troubleshooting. Which of the following should the technician use to assist the user?
A technician is partitioning a hard disk. The five primary partitions should contain 4TB of free space. Which of the following partition styles should the technician use to partition the device?
A technician needs administrator access on a Windows workstation to facilitate system changes without elevating permissions. Which of the following would best accomplish this task?
A company-owned mobile device is displaying a high number of ads, receiving data-usage limit notifications, and experiencing slow response. After checking the device, a technician notices the device has been jailbroken. Which of the following should the technician do next?
Which of the following operating systems would most likely be used to run the inventory management system at a factory?
Which of the following commands can a technician use to get the MAC address of a Linux distribution?
net use
Which of the following environments allows for the testing of critical systems without the risk of them being negatively impacted by changes?
A user recently purchased a second monitor and wants to extend the Windows desktop to the new screen. Which of the following Control Panel options should a technician adjust to help the user?
Color Management
A customer calls desktop support and begins yelling at a technician. The customer claims to have submitted a support ticket two hours ago and complains that the issue still has not been resolved. Which of the following describes how the technician should respond?
Place the customer on hold until the customer calms down.
An application user received an email indicating the version of the application currently in use will no longer be sold. Users with this version of the application will no longer receive patches or updates either. Which of the following indicates a vendor no longer supports a product?
An employee has repeatedly contacted a technician about malware infecting a work computer. The technician has removed the malware several times, but the user's PC keeps getting infected. Which of the following should the technician do to reduce the risk of future infections?
Which of The following refers to the steps to be taken if an Issue occurs during a change Implementation?
A user wants to back up a Windows 10 device. Which of the following should the user select?
A technician is concerned about a large increase in the number of whaling attacks happening in the industry. The technician wants to limit the company's risk to avoid any issues. Which of the following items should the technician implement?
A technician sees a file that is requesting payment to a cryptocurrency address. Which of the following should the technician do first?
A technician is investigating options to secure a small office's wireless network. One requirement is to allow automatic log-ins to the network using certificates instead of passwords. Which of the following should the wireless solution have in order to support this feature?
A company's assets are scanned annually. Which of the following will most likely help the company gain a holistic view of asset cost?
A technician is trying to encrypt a single folder on a PC. Which of the following should the technician use to accomplish this task?
A new employee is having difficulties using a laptop with a docking station The laptop is connected to the docking station, and the laptop is closed. The external monitor works for a few seconds, but then the laptop goes to sleep. Which of the following options should the technician configure in order to fix the Issue?
A company is looking lot a solution that provides a backup for all data on the system while providing the lowest impact to the network. Which of the following backup types will the company MOST likely select?
A system drive is nearly full, and a technician needs lo tree up some space. Which of the following tools should the technician use?
Which of the following threats will the use of a privacy screen on a computer help prevent?
A workstation is displaying a message indicating that a user must exchange cryptocurrency for a decryption key. Which of the following is the best way for a technician to return the device to service safely?
A systems administrator is configuring centralized desktop management for computers on a domain. The management team has decided that all users' workstations should have the same network drives, printers, and configurations. Which of the following should the administrator use to accomplish this task?
A technician discovers user input has been captured by a malicious actor. Which of the following malware types is MOST likely being used?
An administrator responded to an incident where an employee copied financial data to a portable hard drive and then left the company with the data. The administrator documented the movement of the evidence. Which of the following concepts did the administrator demonstrate?
A technician is working on a Windows 10 PC that has unwanted applications starting on boot. Which of the following tools should the technician use to disable applications on startup?
Which of the following protects a mobile device against unwanted access when it is left unattended?
A user is unable to access files on a work PC after opening a text document. The text document was labeled "URGENT PLEASE READ.txt - In active folder, .txt file titled urgent please read". Which of the following should a support technician do FIRST?
A user connected an external hard drive but is unable to see it as a destination to save files. Which of the following tools will allow the drive to be formatted?
A help desk technician determines a motherboard has failed. Which of the following is the most logical next step in the remediation process?
Which of the following helps ensure that a piece of evidence extracted from a PC is admissible in a court of law?
During a network outage, a technician discovers a new network switch that was not listed in the support documentation. The switch was installed during a recent change window when a new office was added to the environment. Which of the following would most likely prevent this type of mismatch after next month's change window?
Which of the following common security vulnerabilities can be mitigated by using input validation?
A technician is setting up a newly built computer. Which of the following is the fastest way for the technician to install Windows 10?
A company is experiencing a ODDS attack. Several internal workstations are the source of the traffic Which of the following types of infections are the workstations most likely experiencing? (Select two)
Which of the following would cause a corporate-owned iOS device to have an Activation Lock issue?
Users access files in the department share. When a user creates a new subfolder, only that user can access the folder and Its files. Which of the following will MOST likely allow all users to access the new folders?
A user attempts to install additional software and receives a UAC prompt. Which of the following is the BEST way to resolve this issue?
Which of the following Is used to identify potential issues with a proposed change poor lo implementation?
A technician is installing RAM in a new workstation and needs to protect against electrostatic discharge. Which of the following will best resolve this concern?
A technician needs to ensure that USB devices are not suspended by the operating system Which of the following Control Panel utilities should the technician use to configure the setting?
A hard drive that previously contained PI I needs to be repurposed for a public access workstation. Which of the following data destruction methods should a technician use to ensure data is completely removed from the hard drive?
A technician has been tasked with troubleshooting audiovisual issues in a conference room. The meeting presenters are unable to play a video with sound. The following error is received:
The Audio Driver is not running.
Which of the following will MOST likely resolve the issue?
A systems administrator installed the latest Windows security patch and received numerous tickets reporting slow performance the next day. Which of the following should the administrator do to resolve this issue?
A user is trying to limit the amount of time their children spend on the internet. Which of the following Windows 10 settings should be enabled to accomplish this objective?
A user opened an infected email. A security administrator responded to the malicious event, successfully mitigated the situation, and returned the machine to service Which of the following needs to be completed before this event is considered closed?
A customer, whose smartphone's screen was recently repaired, reports that the device has no internet access through Wi-Fi. The device shows that it is connected to Wi-Fi, has an address of 192.168.1.42. and has no subnet mask. Which of the following should the technician check next?
Which of the following languages is used for scripting the creation of Active Directory accounts?
An organization wants to deploy a customizable operating system. Which of the following should the organization choose?
Which of the following features can be used to ensure a user can access multiple versions of files?
Which of the following features can a technician use to ensure users are following password length requirements?
A customer who uses a Linux OS called the help desk to request assistance in locating a missing file. The customer does not know the exact name of the file but can provide a partial file name. Which of the following tools should the technician use? (Select two).
A technician is configuring a SOHO router and wants to only allow specific computers on the network. Which of the following should the technician do?
A company installed WAPs and deployed new laptops and docking stations to all employees. The docking stations are connected via LAN cables. Users are now reporting degraded network service. The IT department has determined that the WAP mesh network is experiencing a higher than anticipated amount of traffic. Which of the following would be the most efficient way to ensure the wireless network can support the expected number of wireless users?
A company was recently attacked by ransomware. The IT department has remediated the threat and determined that the attack method used was email. Which of the following is the most effective way to prevent this issue from reoccurring?
A user received an alert from a Windows computer indicating low storage space. Which of the following will best resolve this issue?
A technician is troubleshooting a Windows system that is having issues with the OS loading at startup. Which of the following should the technician do to diagnose the issue?
A technician is installing software on a user's workstation. The installation fails due to incompliance with the HCL. Which of the following components is most likely causing the installation to fail? (Select two).
When a user is in the office, web pages are loading slowly on the user's phone. Which of the following best explains this issue?
A user in a SOHO asks an off-site, remote technician to connect securely to the user’s laptop. The technician is able to connect to the VPN but is unable to connect to the user’s laptop. Which of the following settings should the technician review?
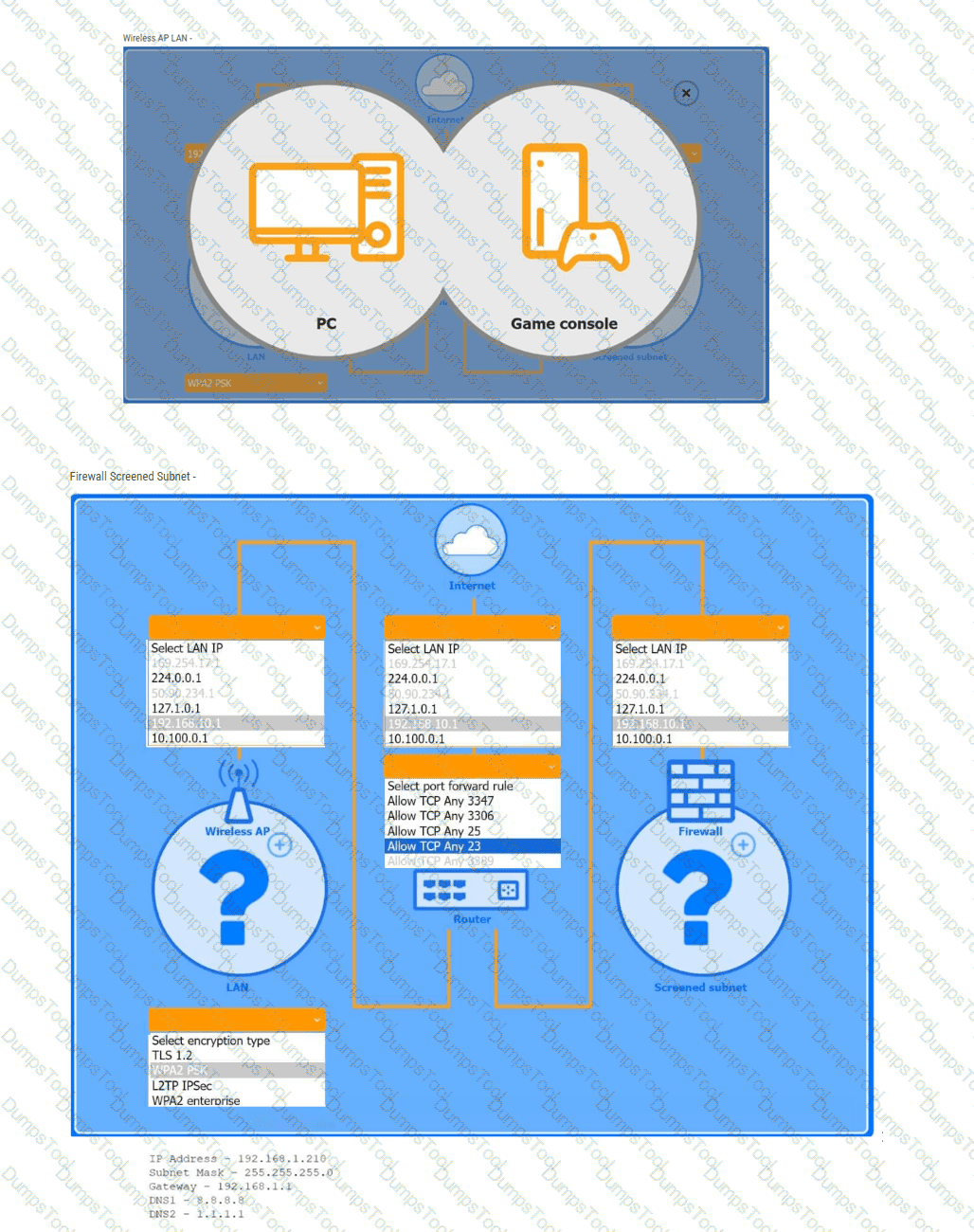
You are configuring a home network for a customer. The customer has requested the ability to access a Windows PC remotely, and needs all chat and optional functions to work in their game console.
INSTRUCTIONS
Use the drop-down menus to complete the network configuration for the customer. Each option may only be used once, and not all options will be used. Then, click the + sign to place each device
in its appropriate location. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
The user often hosts meetings from a Windows desktop, and meeting participants ask the user to make the text larger when the user shares the computer screen. When not in meetings, the user wants the text be smaller for work tasks. Which of the following is the most efficient way to change text font size?
A technician needs to join a Windows client to a domain. Which of the following is required?
A network administrator is showing an email application on a personal cell phone to a coworker. The cell phone is enrolled in the company's MDM program. When launching the application store to download the email application, the coworker receives a security warning stating the device violates company policies due to root-level access. Which of the following should the coworker perform next to resolve the issue?
Which of the following filesystems is most likely to be used for the boot volume on a Linux desktop?
Which of the following types of malware is designed to enable administrative access to a computer?
A user's smartphone screen is not rotating. The technician confirms the rotation lock is deactivated. Which of the following steps should the technician perform next?
A systems administrator needs to access a hypervisor that went offline. After doing a port scan, the administrator notices that company policy is blocking the RDP default port. Which of the following ports should the administrator use to access the machine?
An employee utilizes a personal smartphone to work remotely. The employee is unable to reach the portal using the company-provided VPN service. Which of the following describes the cause of the issue?
Which of the following commands should be used to display current processor activity on a Linux workstation?
A user reports that a system is performing unusually and is sending requests to an unfamiliar IP address every five minutes. Which of the following should the technician check first to troubleshoot the issue?
Due to special job responsibilities, an end user needs the ability to edit the properties of Windows system files. The user has already been granted local administrator privileges. Which of the following Control Panel utilities should be used to provide easy access to the files?
Which of the following languages would a technician most likely use to automate the setup of various services on multiple systems?
A technician is working at a client office site and the technician's family member repeatedly calls and texts about a non-emergency situation. Which of the following should the technician do?
A user is unable to log in to a workstation. The user reports an error message about the date being incorrect. A technician reviews the date and verifies it is correct, but the system clock is an hour behind. The technician also determines this workstation is the only one affected. Which of the following is the most likely issue?
Which of the following should be enabled on a mobile device to prevent unauthorized access to data in case the device is lost or stolen? (Select two).
A user's company phone has several pending software updates. A technician completes the following steps:
•Rebooted the phone
•Connected to Wi-Fi
•Disabled metered data
Which of the following should the technician do next?
After a user upgraded the Windows operating system to the latest feature release, the user notices that one of the legacy applications that was running correctly before the upgrade does not open some windows and is only partially functional. Which of the following actions should the user take to troubleshoot the issue?
A technician is performing hardware maintenance on a desktop PC. Which of the following is the most important safety precaution the technician should take?
A user calls a technician and asks for help with setting up a connection to a printer application. The technician has never dealt with secure print but has directions that will help guide the user. Which of the following techniques should the technician use?
A technician has been unable to remediate a persistent malware infection on a user's workstation. After the technician reinstalled the OS. the malware infection returned later that day. Which of the following is the most likely source?
A technician wants to harden Windows workstations after a recent security audit indicated the company is vulnerable to brute-force attacks. Which of the following features should the technician implement to mitigate such attacks?
A technician needs to strengthen security controls against brute-force attacks. Which of the following options best meets this requirement?
While browsing the internet, a customer sees a window stating antivirus protection is no longer functioning Which of the following steps should a technician take next? (Select two).
Which of the following will automatically map network drives based on Group Policy configuration?
A Windows 10 computer is not installing updates and continues to receive errors even during manual update installations. Which of the following should a technician do to fix the issues? (Select two).
A technician is configuring a specific NTP server for all company-issued laptops. These Windows 10 machines are not joined to an Active Directory domain. Which of the following setting areas would be used for this adjustment?
While testing a new computer, a technician hears a loud buzzing sound, smells smoke, and sees a flame inside the power supply. Which of the following actions should the technician take first?
A technician receives a help desk ticket regarding a software issue on a workstation. The workstation provides the only access to a corporate database, and the technician needs to recover the workstation quickly. Which of the following actions should the technician take?
A technician is assisting a customer who is having difficulty accessing the company’s website. Which of the following should the technician do first?
A company uses shared drives as part of a workforce collaboration process. To ensure the correct access permissions, inheritance at the top-level folder is assigned to each department. A manager's team is working on confidential material and wants to ensure only the immediate team can view a specific folder and its subsequent files and subfolders. Which of the following actions should the technician most likely take?
Which of the following environmental controls is most important to maintain the safety of a data center?
A network administrator is setting up the security for a SOHO wireless network. Which of the following options should the administrator enable to secure the network?
A technician wants to improve password security after several users admitted to using very simple passwords. Which of the following is the best way to resolve this issue?
An administrator needs to select a method to dispose of SSDs containing sensitive data. Which of the following are the most appropriate methods? (Select two).
A user recently downloaded a free game application on an Android device. The device then began crashing frequently and quickly losing its battery charge. Which of the following should the technician recommend be done first to remediate these issues? (Select two).
A user accidentally deleted an important presentation from the desktop of a workstation. The presentation was created after the most recent daily corporate backup. As a result, the technician is unable to restore the presentation. Which of the following should the technician enable to prevent this issue from occurring in the future?
An administrator received a new shipment of mobile devices. Per company policy, all enterprise-issued devices must have two authentication methods, and the organization has already enforced the use of PIN codes as one method. Which of the following device features should the administrator enable?
Which of the following macOS file types requires mounting before installation?
A systems administrator at a small company wants to discretely access user machines and verify patch levels without users noticing. Which of the following remote access technologies should the administrator use?
Which of the following security threats requires a phone call to launch the attack?
A technician is an administrator on a messaging application for a private work group of mixed departments. One of the technician’s colleagues discloses to the group that their employer recently suffered a major security breach and shared details about the breach to the group Which of the following should the technician do first7
A technician is upgrading the backup system for documents at a high-volume law firm. The current backup system can retain no more than three versions of full backups before failing. The law firm is not concerned about restore times but asks the technician to retain more versions when possible. Which of the following backup methods should the technician MOST likely implement?
Which of the following features allows a technician to configure policies in a Windows 10 Professional desktop?
A user updates a mobile device's OS. A frequently used application becomes consistently unresponsive immediately after the device is launched. Which of the following troubleshooting steps should the user perform FIRST?
An IT security team is implementing a new Group Policy that will return a computer to the login after three minutes. Which of the following BEST describes the change in policy?
A technician is troubleshooting a mobile device that was dropped. The technician finds that the screen (ails to rotate, even though the settings are correctly applied. Which of the following pieces of hardware should the technician replace to resolve the issue?
A user receives the following error while attempting to boot a computer.
BOOTMGR is missing
press Ctrl+Alt+Del to restart
Which of the following should a desktop engineer attempt FIRST to address this issue?
An organization implemented a method of wireless security that requires both a user and the user's computer to be in specific managed groups on the server in order to connect to Wi-Fi. Which of the following wireless security methods BEST describes what this organization implemented?
A customer called the help desk to report that a machine that was recently updated is no longer working. The support technician checks the latest logs to see what updates were deployed, but nothing was
deployed in more than three weeks. Which of the following should the support technician do to BEST resolve the situation?
A technician is editing the hosts file on a few PCs in order to block certain domains. Which of the following would the technician need to execute after editing the hosts file?
Which of the following default system tools can be used in macOS to allow the technician to view the screen simultaneously with the user?
A user is no longer able to start the OS on a computer and receives an error message indicating there is no OS found. A technician reviews the audit logs and notes that the user's system posted a S.M.A.R.T. error just days before this issue. Which of the following is the MOST likely cause of this issue?
A company implemented a BYOD policy and would like to reduce data disclosure caused by malware that may infect these devices. Which of the following should the company deploy to address these concerns?
A technician needs to add an individual as a local administrator on a Windows home PC. Which of the following utilities would the technician MOST likely use?
A user notices a small USB drive is attached to the user's computer after a new vendor visited the office. The technician notices two files named grabber.exe and output.txt. Which of the following attacks is MOST likely occurring?
A technician is securing a new Windows 10 workstation and wants to enable a Screensaver lock. Which of the following options in the Windows settings should the technician use?
A user rotates a cell phone horizontally to read emails, but the display remains vertical, even though the settings indicate autorotate is on. VT1ich of the following will MOST likely resolve the issue?
A user tries to access commonly used web pages but is redirected to unexpected websites. Clearing the web browser cache does not resolve the issue. Which of the following should a technician investigate NEXT to resolve the issue?
A large company is selecting a new Windows operating system and needs to ensure it has built-in encryption and endpoint protection. Which of the following Windows versions will MOST likely be selected?
A technician receives a call from a user who is unable to open Outlook. The user states that Outlook worked fine yesterday, but the computer may have restarted sometime overnight. Which of the following is the MOST likely reason Outlook has stopped functioning?
A technician receives a call (rom a user who is having issues with an application. To best understand the issue, the technician simultaneously views the user's screen with the user. Which of the following would BEST accomplish this task?
A company is retiring old workstations and needs a certificate of destruction for all hard drives. Which of the following would be BEST to perform on the hard drives to ensure the data is unrecoverable? (Select TWO).
A technician needs to access a Windows 10 desktop on the network in a SOHO using RDP. Although the connection is unsuccessful, the technician is able to ping the computer successfully. Which of the following is MOST likely preventing the connection?
A technician installed a new application on a workstation. For the program to function properly, it needs to be listed in the Path Environment Variable. Which of the following Control Panel utilities should the technician use?
Which of the following would MOST likely be used to change the security settings on a user's device in a domain environment?
A systems administrator is creating a new document with a list of the websites that users are allowed to access. Which of the following types of documents is the administrator MOST likely creating?
A Windows workstation that was recently updated with approved system patches shut down instead of restarting. Upon reboot, the technician notices an alert stating the workstation has malware in the root OS folder. The technician promptly performs a System Restore and reboots the workstation, but the malware is still detected. Which of the following BEST describes why the system still has malware?
A user added a second monitor and wants to extend the display to it. In which of the following Windows settings will the user MOST likely be able to make this change?
A homeowner recently moved and requires a new router for the new ISP to function correctly. The internet service has been installed and has been confirmed as functional. Which of the following is the FIRST step the homeowner should take after installation of all relevant cabling and hardware?
A user contacts a technician about an issue with a laptop. The user states applications open without being launched and the browser redirects when trying to go to certain websites. Which of the following is MOST likely the cause of the user's issue?
A customer calls a service support center and begins yelling at a technician about a feature for a product that is not working to the customer's satisfaction. This feature is not supported by the service support center and requires a field technician to troubleshoot. The customer continues to demand service. Which of the following is the BEST course of action for the support center representative to take?
A user reports that after a recent software deployment to upgrade applications, the user can no longer use the Testing program.
However, other employees can successfully use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve any issues discovered by selecting the:
Index number of the Event Viewer issue
First command to resolve the issue
Second command to resolve the issue
BSOD
Commands:
Event Viewer:
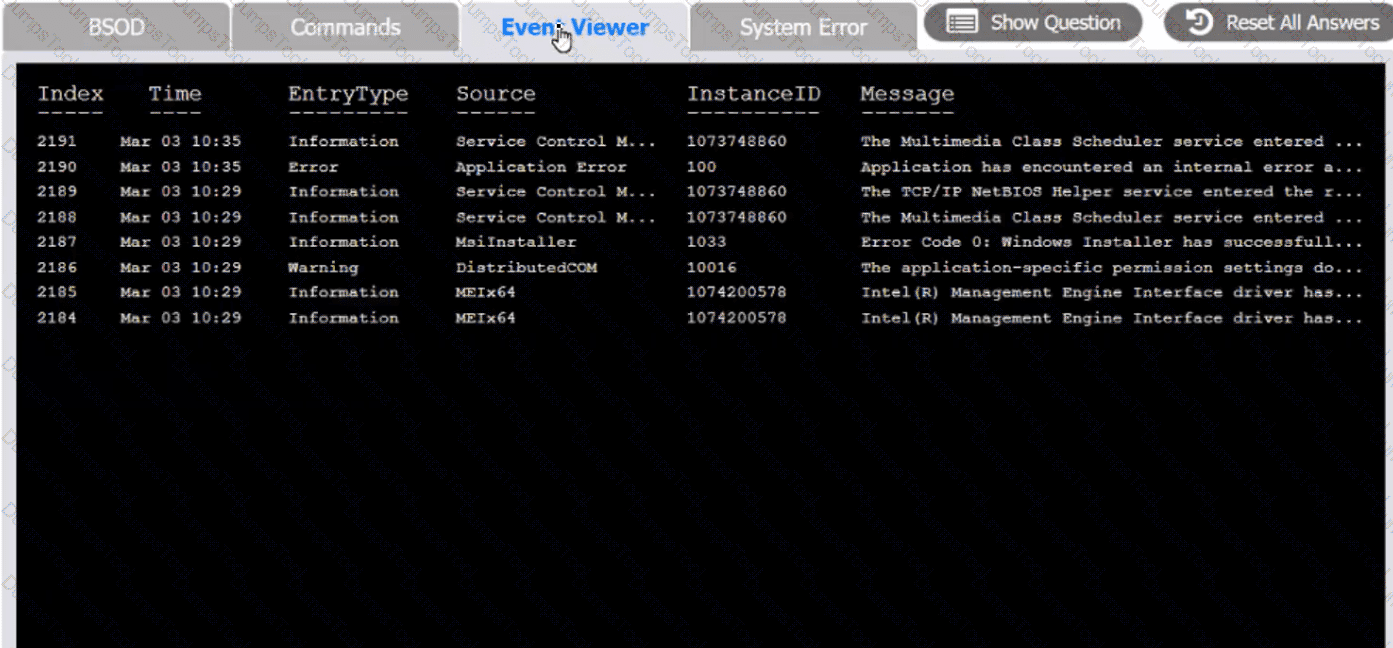
System Error:
Which of the following is MOST likely used to run .vbs files on Windows devices?
A technician is preparing to remediate a Trojan virus that was found on a workstation. Which of the following steps should the technician complete BEFORE removing the virus?
A technician is working on a way to register all employee badges and associated computer IDs. Which of the following options should the technician use in order to achieve this objective?
A technician, who is working at a local office, has found multiple copies of home edition software installed on computers. Which of the following does this MOST likely violate?
A user needs assistance changing the desktop wallpaper on a Windows 10 computer. Which of the following methods will enable the user to change the wallpaper using a Windows 10 Settings tool?
A technician has been asked to set up a new wireless router with the best possible security. Which of the following should the technician implement?
A new service desk is having a difficult time managing the volume of requests. Which of the following is the BEST solution for the department?
A user is having issues with document-processing software on a Windows workstation. Other users that log in to the same device do not have the same issue.
Which of the following should a technician do to remediate the issue?
A police officer often leaves a workstation for several minutes at a time. Which of the following is the BEST way the officer can secure the workstation quickly when walking away?
A macOS user needs to create another virtual desktop space. Which of the following applications will allow the user to accomplish this task?
A user reports a PC is running slowly. The technician suspects high disk I/O. Which of the following should the technician perform NEXT?
Sensitive data was leaked from a user's smartphone. A technician discovered an unapproved application was installed, and the user has full access to the device's command shell. Which of the following is the NEXT step the technician should take to find the cause of the leaked data?
An analyst needs GUI access to server software running on a macOS server. Which of the following options provides the BEST way for the analyst to access the macOS server from the Windows workstation?