You have been hired to create a Layer 2 network design solution to allow a company to transition their Spanning tree Protocol to Multiple Spanning Tree The company is currently tunning a network core with a vPC switch pair and Rapid PVST+ If the company must avoid downtime in the network core, which step will be included in the design solution?
Which function is performed at the access layer of the three-layer hierarchical network design mode?
VPLS is implemented in a Layer 2 network with 2000 VLANs What is the primary concern to ensure successful deployment of VPLS?
In a VPLS design solution, why would you use BGP instead of LDP for signaling?
You are designing an 802.1x solution for a customer where the network supports a large number of IP phones and printers. You plan to configure MAC address bypass for the phones and printers. What is your primary concern related to authentication?
Which description of the RPF check in the multicast forwarding traffic is true?
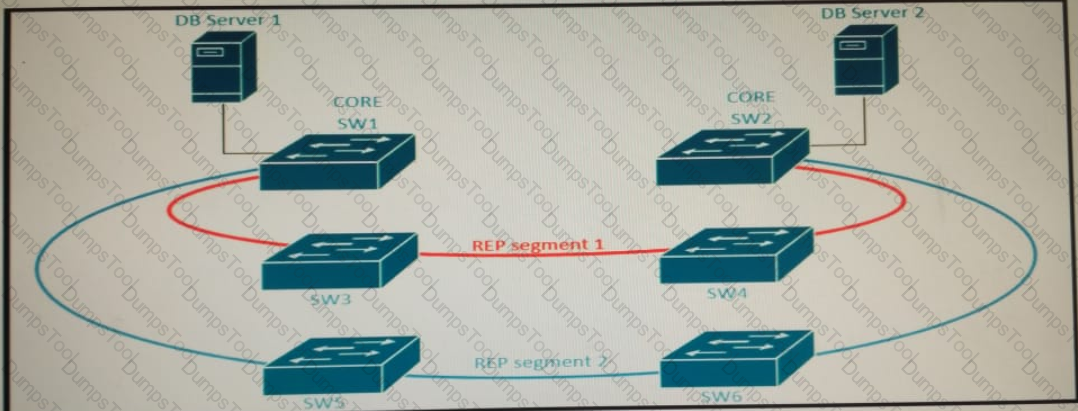
Refer to the exhibit. A new high availability DB sever cluster is installed in the network . these two servers require high bandwidth and low latency Layer 2 connectivity for database replication. Which solution supports these requirements?
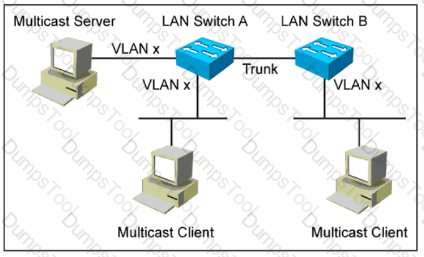
Refer to the exhibit Assume that no multicast optimization is done on LAN switches A and B Which two solutions can be used to optimize multicast traffic forwarding in this situation? (Choose two )
OSPF is implemented over a pseudowire Layer2 VPN Which statement about this design implementation is true?
Which two fast reroute technologies provide the highest level of protected path converge in a ring topology? (Choose two)
Company ABC wants to minimize the risk of users plugging unauthorized switches and hubs into the network Which two features can be used on the LAN access ports to support this design requirement? (Choose two.)
A retail company has 250 branches connected to the core via MPLS Layer 3 VPN The company is migrating from traditional telephony services to a VoIP solution Which two primary concerns when implementing a VoIP solution are true? (Choose two)
You want to add 900 VLANs to the existing 90 VLANs on a data center. Which two spanning-tree concerns must you consider? (Choose two)
Your network operations team is deploying Access Control Lists (ACLs) across your Internet gateways They wish to place an ACL inbound on the Internet gateway interface facing the core network (the "trusted" interface). Which IP address would the ACL need for traffic sourced from the inside interface, to match the source address of the traffic?
How can EIGRP topologies be designed to converge as fast as possible in the event of a point-to-point link failure?
Which two design solutions ensure sub 50 msec of the convergence time after a link failure in the network? (Choose two)
Refer to the exhibit.
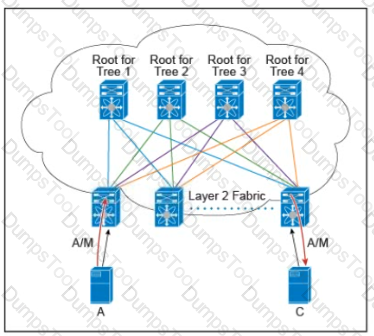
There are multiple trees in the Cisco FabricPath All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two )
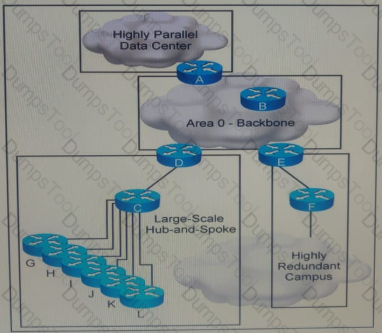
Refer to the exhibit. This OSPF network has just been deployed with four areas, but the hub and spoke area frequently flaps you must fix this design failure which two reasons describe why the implementation of link-state summarization will minimize the effect of the instability in this network? (Choose two)
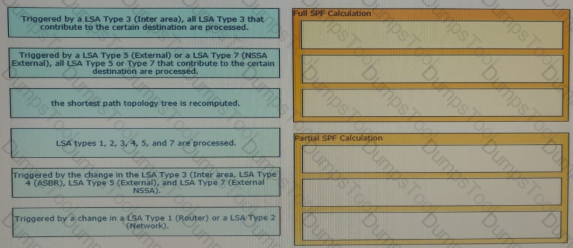
Drag and drop the natures of the network events from the left onto the OSPF-SPF calculation types on the right.
As part of a new network design documentation, you are required to explain the reason for choosing cisco FabricPath for Layer 2 loop avoidance. Which two elements help Cisco FabricPath mitigate Layer 2 loops if they happen in the Layer 2 MP network? (Choose two)
A green data center is being deployed and a design requirement is to be able to readily scale server virtualization Which IETF standard technology can provide this requirement?
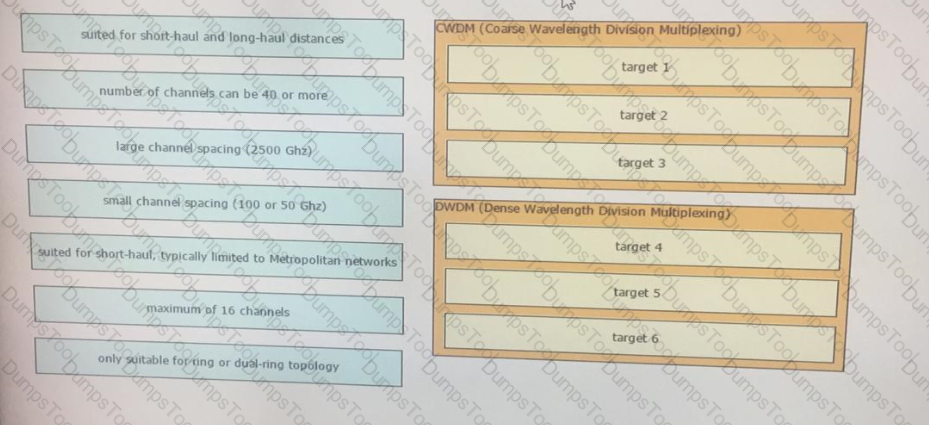
Drag and drop the optical technology design characteristics on the left to the correct optical technologies on the right. Not all options are used
Your organization is working on a design solution for a new Internet-based remote access virtual private network that has 1000 remote sites A network administrator recommends GETVPN as the model because the network of today uses DMVPN, which results in a lot of background NHRP control traffic What is a potential problem with using GETVPN for this design solution?
What must you consider when designing IPsec networks using Authentication Header?
Which three terms describe an OS-level virtualization method for deploying and running distributed applications? (Choose three)
You have been tasked with designing a data center interconnect to provide business continuity You want to encrypt the traffic over the DCI using IEEE 802 1AE MACsec to prevent the deployment of any firewall or IPS. Which two interconnect technologies support MACsec? (Choose two.)
Which effect of designing a Layer 2 network using the PortFast feature with PVST+ is true?
You have been asked to design a remote access VPN solution to support up to 2000 devices. You must ensure that only corporate assets are allowed to connect to the VPN, and users must authenticate to gain access of their based on their user role. Users must use a password that they are already using to access existing applications . A user may not always use the same device to access the VPN. Which two options combined meet the requirements? (Choose two)
Which two mechanisms avoid suboptimal routing in a network with dynamic mutual redistribute OSPFv2 and EIRGP boundaries?
An IPsec VPN WAN network has a new requirement for passing multicast traffic between sites. Which two technologies must be added to the design to pass the multicast traffic? (Choose two)
Which two effects of using ingress filtering to prevent spoofed address on a network design are true? (Choose two)
You are designing a GET VPN solution consisting of 30 group members. Which measure helps product encrypted user traffic from replay attacks?