You are designing a network running both IPv4 and IPv6 to deploy QoS. Which consideration is correct about the QoS for IPv4 and IPv6?
You are designing the QoS policy for a company that is running many TCP-based applications. The company is experiencing tail drops for these applications. The company wants to use a congestion avoidance technique for these applications. Which QoS strategy can be used?
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
Sometimes SDN leverages various overlay networking technologies to create layer(s) of network abstraction. What describes an overlay network?
Company XYZ has two routing domains (EIGRP and OSPF). They want full reachability and need OSPF to see link costs added to external routes. How must redistribution be designed?
How can EIGRP topologies be designed to converge as fast as possible in the event of a point-to-point link failure?
Refer to the exhibit.
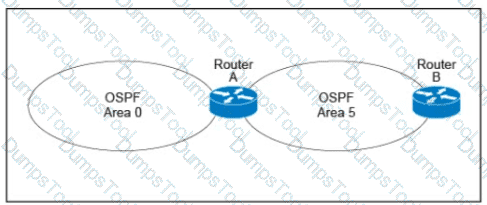
A customer runs OSPF with Area 5 between its aggregation router and an internal router. When a network change occurs in the backbone, Area 5 starts having connectivity issues due to the SPF algorithm recalculating an abnormal number of times in Area 5. You are tasked to redesign this network to increase resiliency on the customer network with the caveat that Router B does not support the stub area. How can you accomplish this task?
Router R1 is a BGP speaker with one peering neighbor over link "A". When link "A" fails, routing announcements are terminated, which results in the tearing down of the state for all BGP routes at each end of the link. What is this a good example of?
Which solution component helps to achieve rapid migration to the cloud for SaaS and public cloud leveraging SD-WAN capabilities?
You have been tasked with designing a data center interconnect as part of business continuity. You want to use FCoE over this DCI to support synchronous replication. Which two technologies allow for FCoE via lossless Ethernet or data center bridging? (Choose two.)
Hybrid cloud computing allows organizations to take advantage of public and private cloud models. Which best practice should organizations follow to ensure data security in the private cloud?
A customer asks you to perform a high-level review of their upcoming WAN refresh for remote sites. The review is specially focused on their retail store operations consisting of 500+ locations connected via multipoint IPsec VPN solution. Which routing protocol would be valid but would also be the most restrictive for the expansion of this deployment model?
IPFIX data collection via standalone IPFIX probes is an alternative to flow collection from routers and switches. Which use case is suitable for using IPFIX probes?
While reviewing an existing network design, you are discussing the characteristics of different STP versions. Which protocol minimizes unicast flooding during a Topology Change Notification in a Layer 2 switched network with many VLANs?
Refer to the exhibit.

The enterprise customer wants to stream one-way video from their head office to eight branch offices using multicast. Their current service provider provides a Layer 3 VPN solution and manages the CE routers, but they do not currently support multicast. Which solution quickly allows this multicast traffic to go through while allowing for future scalability?
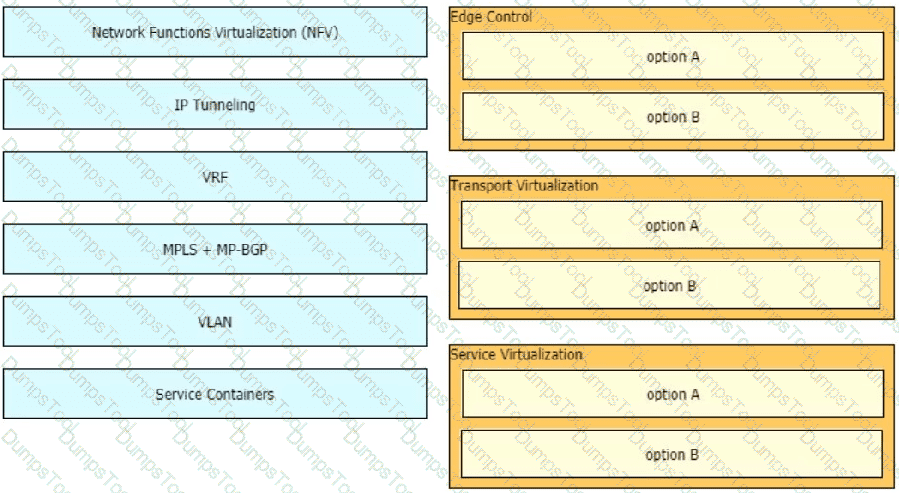
Drag and drop the end-to-end network virtualization elements from the left onto the correct network areas on the right.
Two enterprise networks must be connected together. Both networks are using the same private IP addresses. The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload feature to save IP addresses from the NAT pools. Which design addresses this requirement using only one Cisco IOS NAT router for both directions?
Company XYZ is in the process of identifying which transport mechanism(s) to use as their WAN technology. Their main two requirements are:
A technology that could offer DPI, SLA, secure tunnels, privacy, QoS, scalability, reliability, and ease of management.
A technology that is cost-effective.
Which WAN technology(ies) should be included in the design of company XYZ?
In an OSPF network with routers connected together with Ethernet cabling, which topology typically takes the longest to converge?
Company XYZ asks for design recommendations for Layer 2 redundancy. The company wants to prioritize fast convergence and resiliency elements. In the design, which two technologies are recommended? (Choose two.)
Refer to the exhibit.
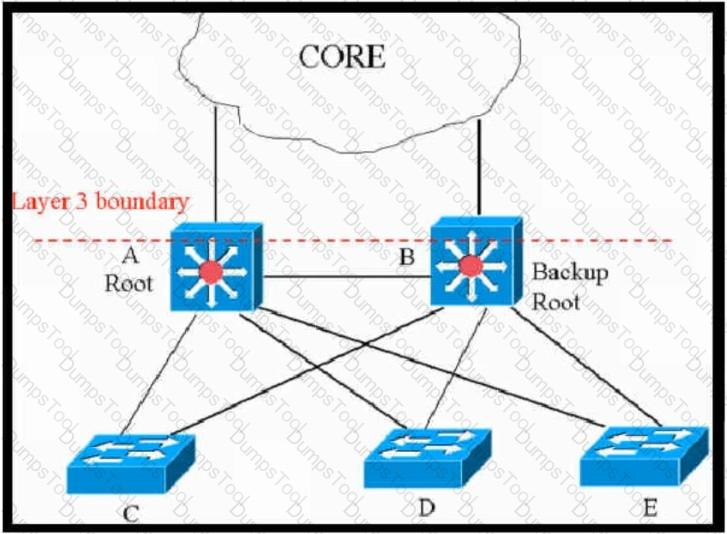
This network is running legacy STP 802.1d. Assuming "hello_timer" is fixed to 2 seconds, which parameters can be modified to speed up convergence times after single link/node failure?
Which two features control multicast traffic in a VLAN environment? (Choose two)
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. What is the final migration step after hosts have physically migrated to have traffic flowing through the new network without changing any host configuration?
An attacker exploits application flaws to obtain data and credentials. What is the next step after application discovery in Zero Trust networking?
Refer to the exhibit.
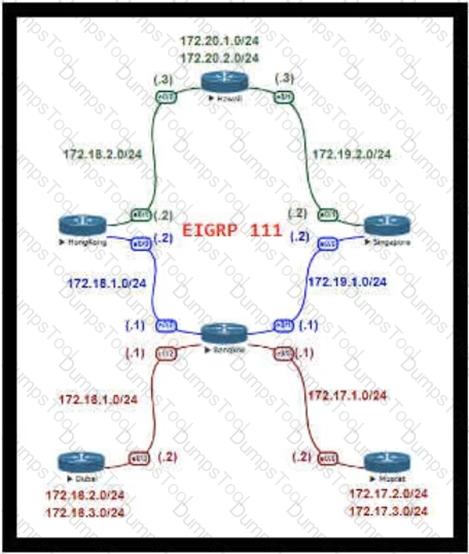
For Company XYZ, Bangkok is using ECMP to reach the 172.20.2.0/24 network. The company wants a design that would allow them to forward traffic from 172.16.2.0/24 toward 172.20.2.0/24 via the Singapore router as the preferred route. The rest of the traffic should continue to use ECMP. Which technology fulfills this design requirement?
Two routers R1 and R2 are directly connected through an Ethernet link. Both routers are running OSPF over the Ethernet link and OSPF has been registered with BFD. R1 has been set up to transmit BFD at a 50 ms interval, but R2 can receive only at a 100 ms rate due to platform limitations. What does this mean?
A company uses equipment from multiple vendors in a data center fabric to deliver SDN, enable maximum flexibility, and provide the best return on investment. Which YANG data model should be adopted for comprehensive features to simplify and streamline automation for the SDN fabric?
What is the most important operational driver in building a resilient and secure modular network design?
An enterprise solution team is analyzing multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface. Which requirement addresses this ability on a multicontroller platform?
A key to maintaining a highly available network is building in the appropriate redundancy to protect against failure. This redundancy is carefully balanced with the inherent complexity of redundant systems. Which design consideration is relevant for enterprise WAN use cases when it comes to resiliency?
Refer to the exhibit.
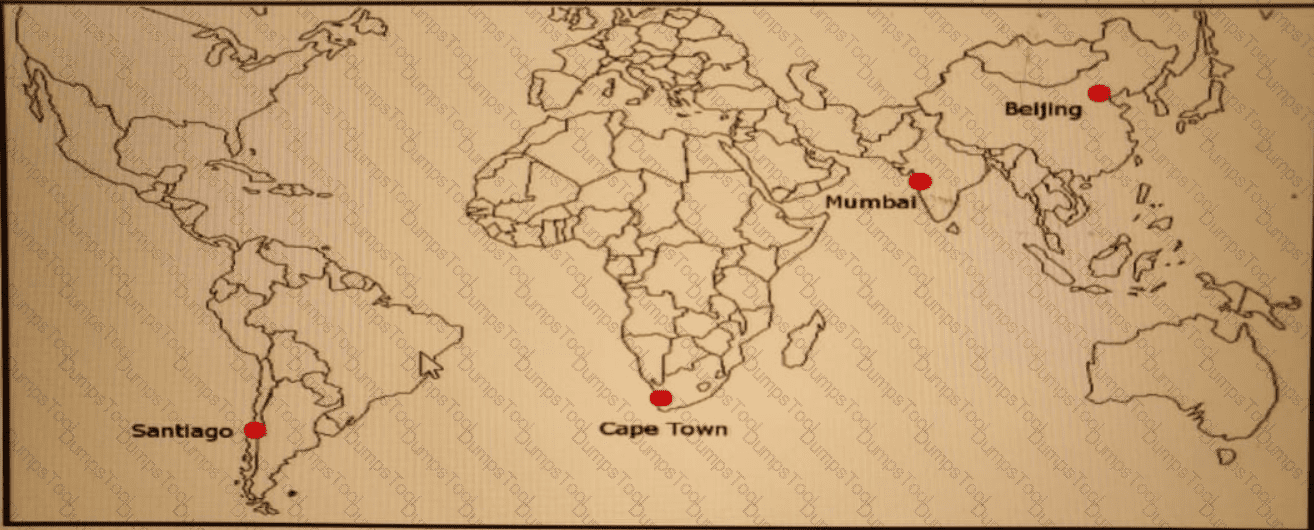
ACME Mining has four data centers in Santiago. Cape Town. Mumbai, and Beijing, full-mesh connected via a 400 Mb/s EVP-LAN They want to deploy a new mission-critical application with these
requirements:
clusterheartbeat2Mb/s continuous (250 KB/s)
cluster heartbeat one-way maximum latency 100 ms
These are the current ping tests results between the four data centers:
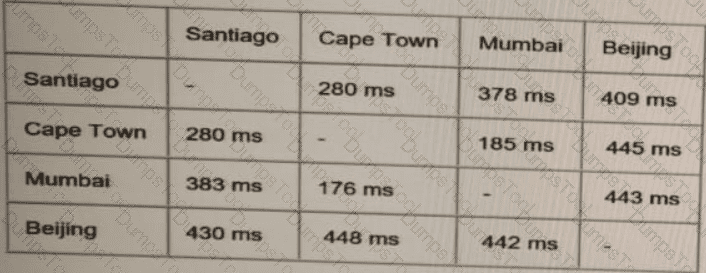
Which hosting data center pair can host the new application?
Which two possible drawbacks should you consider when introducing Network Functions Virtualization in a network design? (Choose two.)
When an SDN-based model is used to transmit multimedia traffic, which aspect should an architect consider while designing the network?
Which two foundational aspects of IoT are still evolving and being worked on by the industry at large? (Choose two)
A business invests in SDN and develops its own SDN controller that, due to budget constraints, runs on a single controller. The controller actively places an exclusive lock on the configuration of the devices to ensure it is the only source of changes to the environment. What is the result if the controller fails?
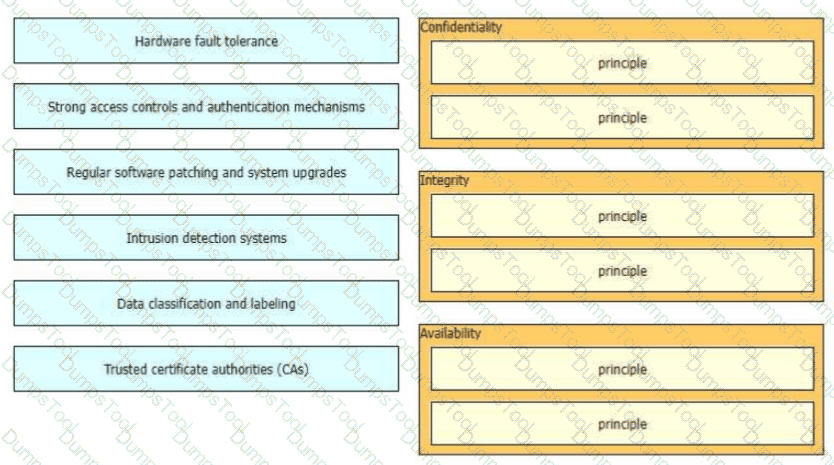
The CIA triad is foundational to information security, and one can be certain that one or more of the principles within the CIA triad has been violated when data is leaked or a system is attacked Drag and drop the countermeasures on the left to the appropriate principle section on the right in any order
Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits. Which two domains should be covered under Zero Trust initiatives? (Choose two)
Which optimal use of interface dampening on a fast convergence network design is true?
Which design consideration is valid when you contrast FabricPath and TRILL?
A network security team observes phishing attacks on a user machine from a remote location. The organization has a policy of saving confidential data on two different systems using different types of authentication. What is the next step to control such events after the security team verifies all users in Zero Trust modeling?
Company XYZ is planning to deploy primary and secondary (disaster recovery) data center sites. Each of these sites will have redundant SAN fabrics and data protection is expected between the data center sites. The sites are 100 miles (160 km) apart and target RPO/RTO are 3 hrs and 24 hrs, respectively. Which two considerations must Company XYZ bear in mind when deploying replication in their scenario? (Choose two.)
Which two characteristics apply to firewall transparent mode operations in a firewall solution design? (Choose two.)
Identity and access management between multiple users and multiple applications has become a mandatory requirement for Company XYZ to fight against ever-increasing cybersecurity threats. To achieve this, federated identity services have been deployed to provide Single Sign-On and Multi-Factor Authentication. Which protocol can be used by Company XYZ to provide authentication and authorization services?
Company XYZ has implemented policy-based routing in their network. Which potential problem must be kept in mind about network reconvergence and PBR?
Company XYZ must design a strategy to protect their routers from DoS attacks, such as traffic destined to the router's own route processor, using separate control plane categories. Which two capabilities can be used to achieve this requirement? (Choose two.)
Refer to the exhibit.
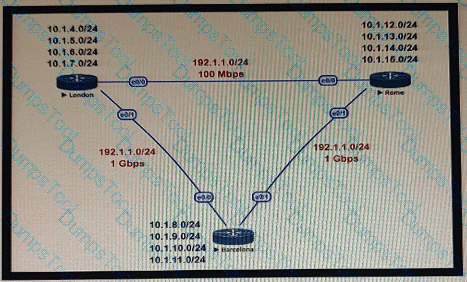
This network is running OSPF as the routing protocol. The internal networks are being advertised in OSPF. London and Rome are using the direct link to reach each other although the transfer rates are better via Barcelona. Which OSPF design change allows OSPF to calculate the proper costs?
An enterprise campus is adopting a network virtualization design solution with these requirements:
• It must include the ability to virtualize the data plane and control plane by using VLANs and VRFs
• It must maintain end-to-end logical path transport separation across the network
• Resources available grouped at the access edge
Which two primary models can this network virtualization design be categorized? (Choose two)
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. Which activity should be completed each time a legacy network is migrated?
Enterprise XYZ wants to implement fast convergence on their network and optimize timers for OSPF. However, they also want to prevent excess flooding of LSAs if there is a constantly flapping link on the network. Which timers can help prevent excess flooding of LSAs for OSPF?
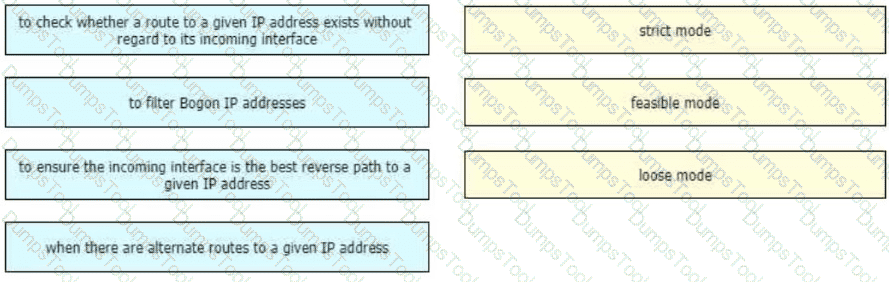
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks Not all options are used.
Company XYZ has 30 sites using MPLS L3 VPN and is concerned about data integrity. They want a centralized configuration model and minimal overhead. Which technology can be used?
What are two design constraints in a standard spine and leaf architecture? (Choose two.)
Your network operations team is deploying Access Control Lists (ACLs) across your Internet gateways. They wish to place an ACL inbound on the Internet gateway interface facing the core network (the "trusted" interface). Which IP address would the ACL need for traffic sourced from the inside interface, to match the source address of the traffic?
Refer to the exhibit.
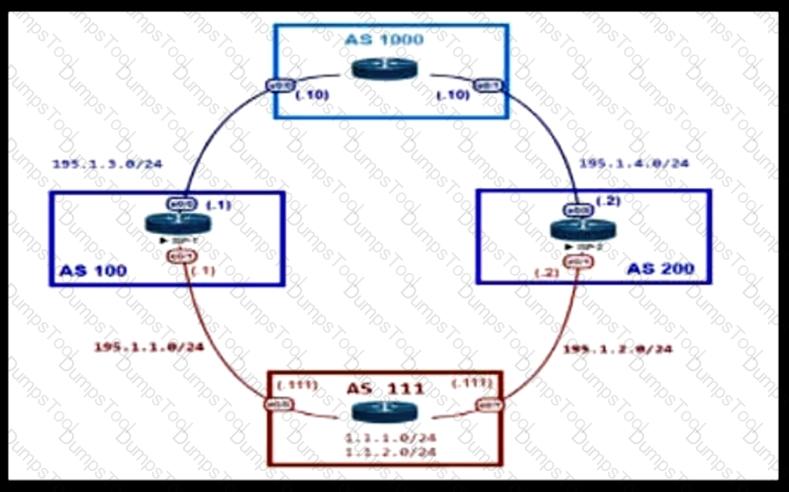
An engineer is designing the network for a multihomed customer running in AS 111. The AS does not have any other ASs connected to it. Which technology is more comprehensive to use in the design to make sure that the AS is not being used as a transit AS?
VPLS is implemented in a Layer 2 network with 2000 VLANs. What is the primary concern to ensure successful deployment of VPLS?
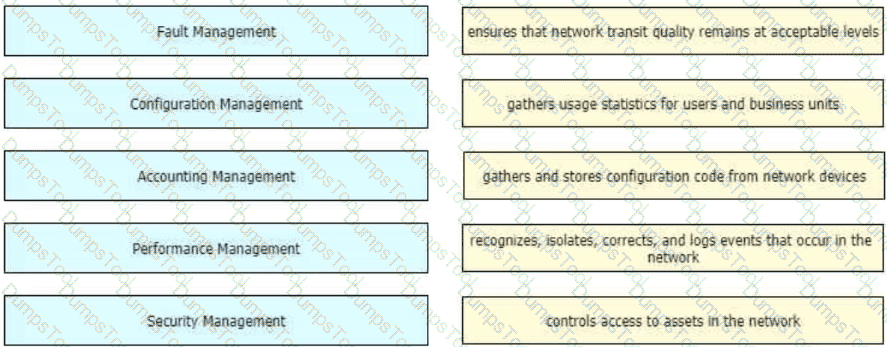
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
The SD-WAN architecture is composed of separate orchestration, management, control, and data planes. Which activity happens at the orchestration plane?
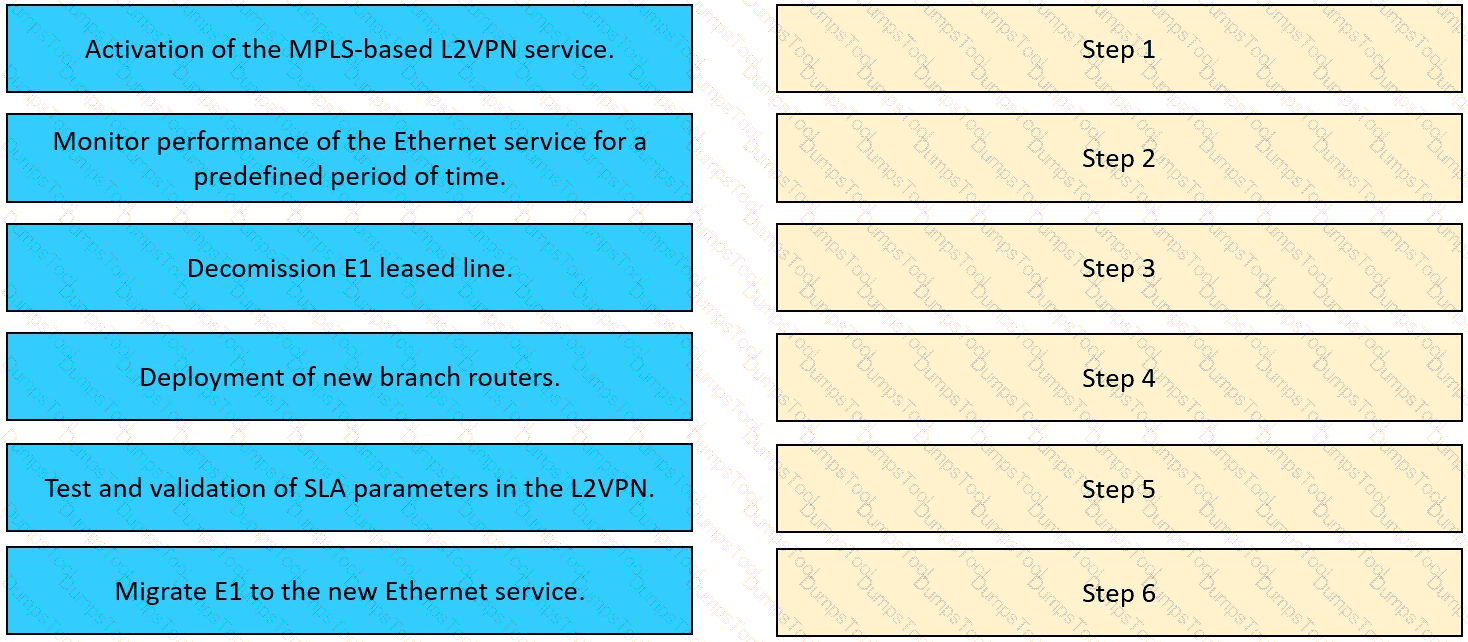
The network team in XYZ Corp wants to modernize their infrastructure and is evaluating an implementation and migration plan to allow integration MPLS-based, Layer 2 Ethernet services managed by a service provider to connect branches and remote offices. To decrease OpEx and improve
response times when network components fail, XYZ Corp decided to acquire and deploy new routers. The network currently is operated over E1 leased lines (2 Mbps) with a managed CE service provided by the telco.
Drag and drop the implementation steps from the left onto the corresponding targets on the right in the correct order.
Company XYZ, a global content provider, owns data centers on different continents. Their data center design involves a standard three-layer design with a Layer 3-only core. HSRP is used as the FHRP. They require VLAN extension across access switches in all data centers, and they plan to purchase a Layer 2 interconnection between two of their data centers in Europe. In the absence of other business or technical constraints, which termination point is optimal for the Layer 2 interconnection?
Company XYZ is running BGP as their routing protocol. An external design consultant recommends that TCP Path MTU Discovery be enabled. Which effect will this have on the network?
Which three tools are used for ongoing monitoring and maintenance of a voice and video environment? (Choose three.)
Company XYZ wants to use the FCAPS ISO standard for network management design, focusing on minimizing outages through detection, isolation, and corrective actions. Which layer accomplishes this design requirement?
Refer to the table.
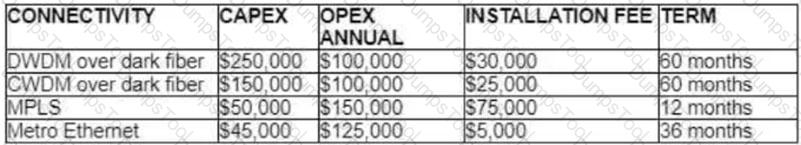
A customer investigates connectivity options for a DCI between two production data centers. The solution must provide dual 10G connections between locations with no single points of failure for Day 1 operations. It must also include an option to scale for up to 20 resilient connections in the second year to accommodate isolated SAN over IP and isolated, dedicated replication IP circuits. All connectivity methods are duplex 10 Gbps. Which transport technology costs the least over two years, in the scenario?
Which two advantages of using DWDM over traditional optical networks are true? (Choose two.)
An architect designs a multi-controller network architecture with these requirements:
Achieve fast failover to control traffic when controllers fail.
Yield a short distance and high resiliency in the connection between the switches and the controller.
Reduce connectivity loss and enable smart recovery to improve the SDN survivability.
Improve connectivity by adding path diversity and capacity awareness for controllers.
Which control plane component of the multi-controller must be built to meet the requirements?
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
Company XYZ has a new network based on IPv6. Some of the subnets that they are planning to use will be confidential and need an addressing scheme that confines them to the local campus network. Which type of IPv6 addresses can be used for these networks in the IPv6 addressing design?
Which two conditions must be met for EIGRP to maintain an alternate loop-free path to a remote network? (Choose two.)
Company XYZ is migrating their existing network to IPv6. Some access layer switches do not support IPv6, while core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used?
The controller has a global view of the network, and it can easily ensure that the network is in a consistent and optimal configuration. Which two statements describe a centralized SDN control path? (Choose two.)
A network hacker introduces a packet with duplicate sequence numbers to disrupt an IPsec session. During this, high-priority traffic is transmitted. What design parameter helps mitigate this?
With virtualization applied throughout the network, every physical link may carry one or more virtual links. What is a key drawback of this?
Which undesired effect of increasing the jitter compensation buffer is true?
A company requires an RPO of less than 10 seconds to ensure business continuity. Which technology should be deployed?
An engineer is designing the QoS strategy for Company XYZ. A lot of scavenger traffic is traversing the 20Mb Internet link. The new design must limit scavenger traffic to 2 Mbps to avoid oversubscription during congestion. Which QoS technique can be used?
Refer to the exhibit.
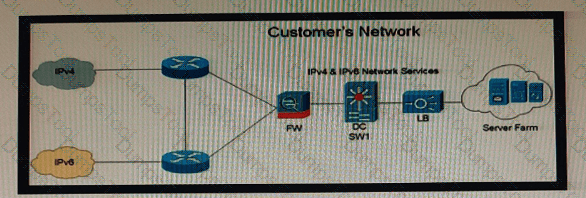
Company XYZ is currently running IPv4 but has decided to start the transition into IPv6. The initial objective is to allow communication based on IPv6 wherever possible, and there should still be support in place for devices that only support IPv4. These devices must be able to communicate to IPv6 devices as well. Which solution must be part of the design?
What advantage of placing the IS-IS Layer 2 flooding domain boundary at the core layer in a three-layer hierarchical network is true?
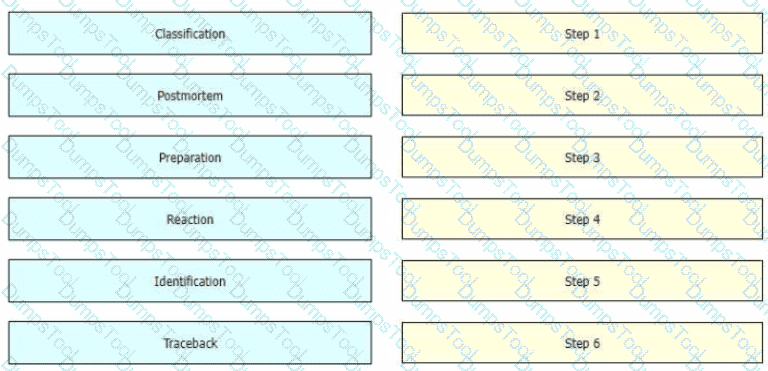
While computer networks and sophisticated applications have allowed individuals to be more productive the need to prepare for security threats has increased dramatically A six-step methodology on security incident handling has been adopted by many organizations including service providers enterprises, and government organizations to ensure that organizations are aware of significant security incidents and act quickly to stop the attacker, minimize damage caused, and prevent follow on attacks or similar incidents in the future Drag and drop the actions on the left to the targets on the right in the correct order.
You are tasked with the design of a high available network. Which two features provide fail closed environments? (Choose two.)
Which feature must be part of the network design to wait a predetermined amount of time before notifying the routing protocol of a change in the path in the network?
Company XYZ is running a redundant private WAN network using OSPF as the underlay protocol. The current design accommodates for redundancy in the network, but it is taking over 30 seconds for the network to reconverge upon failure. Which technique can be implemented in the design to detect such a failure in a subsecond?
A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. They want to extend the existing IP CCTV network to a new branch without routing changes or IP address changes. What is the best approach?
Which parameter is the most important factor to consider when deciding service placement in a cloud solution?
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two.)
Refer to the exhibit.
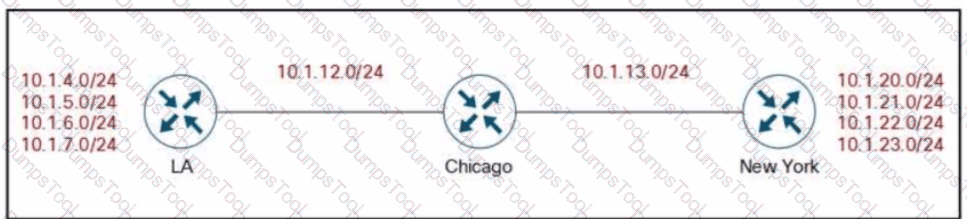
Company XYZ’s BGP topology is as shown in the diagram. The interface on the LA router connected toward the 10.1.5.0/24 network is faulty and is going up and down, which affects the entire routing domain. Which routing technique can be used in the routing policy design so that the rest of the network is not affected by the flapping issue?
A Service Provider is designing a solution for a managed CE service to a number of local customers using a single CE platform and wants to have logical separation on the CE platform using Virtual Routing and Forwarding (VRF) based on IP address ranges or packet length. Which is the most scalable solution to provide this type of VRF Selection process on the CE edge device?
A network engineering team is in the process of designing a lab network for a customer demonstration. The design engineer wants to show that the resiliency of the MPLS Traffic Engineering Fast Reroute solution has the same failover/failback times as a traditional SONET/SDH network (around 50 msec). In order to address both link failure and node failure within the lab topology network, which type of the MPLS TE tunnels must be considered for this demonstration?
An enterprise organization currently provides WAN connectivity to their branch sites using MPLS technology, and the enterprise network team is considering rolling out SD-WAN services for all sites.
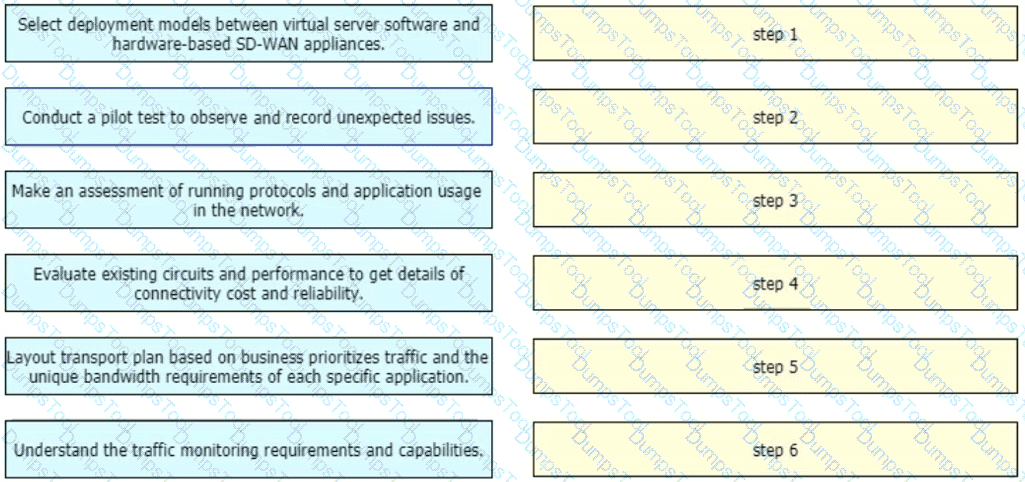
With regards to the deployment planning, drag and drop the actions from the left onto the corresponding steps on the right.
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?
Which methodology is the leading lifecycle approach to network design and implementation?
Refer to the diagram.
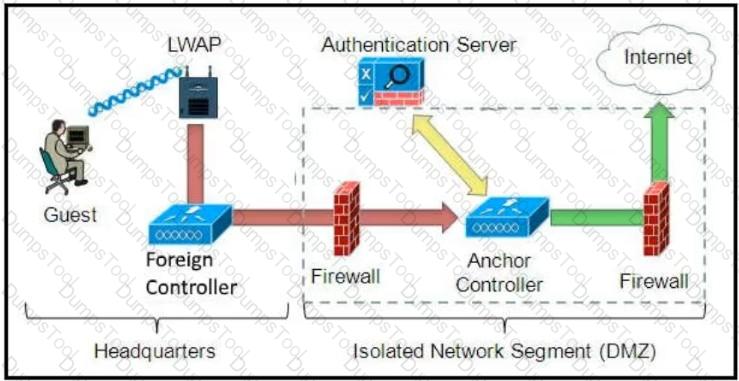
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
Which component of the SDN architecture automatically ensures that application traffic is routed according to policies established by network administrators?
You are tasked to design a QoS policy for a service provider so they can include it in the design of their MPLS core network. If the design must support an MPLS network with six classes, and CEs will be managed by the service provider, which QoS policy should be recommended?
What are two examples of components that are part of an SDN architecture? (Choose two.)