Fill in the blank to complete the statement with the correct technology.
Cisco_________Investigate provides access to data that pertains to DNS security events and correlations collected by the Cisco security team.
When the URI "/api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f/policy/accesspolicies" is used to make a POST request, what does "e276abec-e0f2-11e3-8169-6d9ed49b625f" represent?
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
Refer to the exhibit.
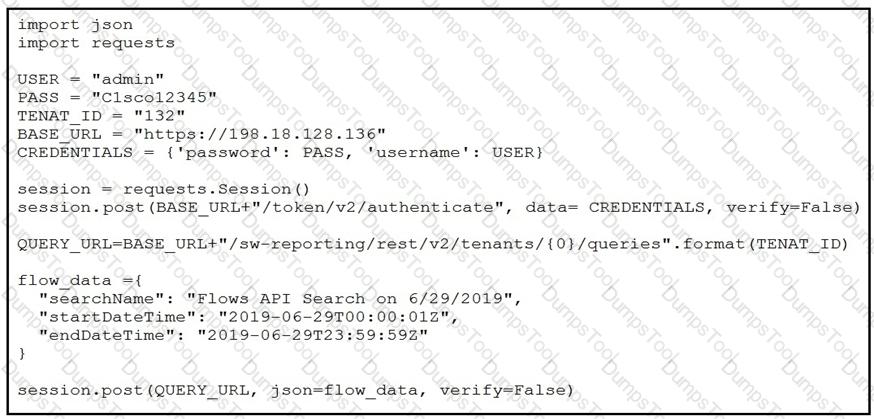
A network operator must generate a daily flow report and learn how to act on or manipulate returned data. When the operator runs the script, it returns an enormous amount of information.
Which two actions enable the operator to limit returned data? (Choose two.)