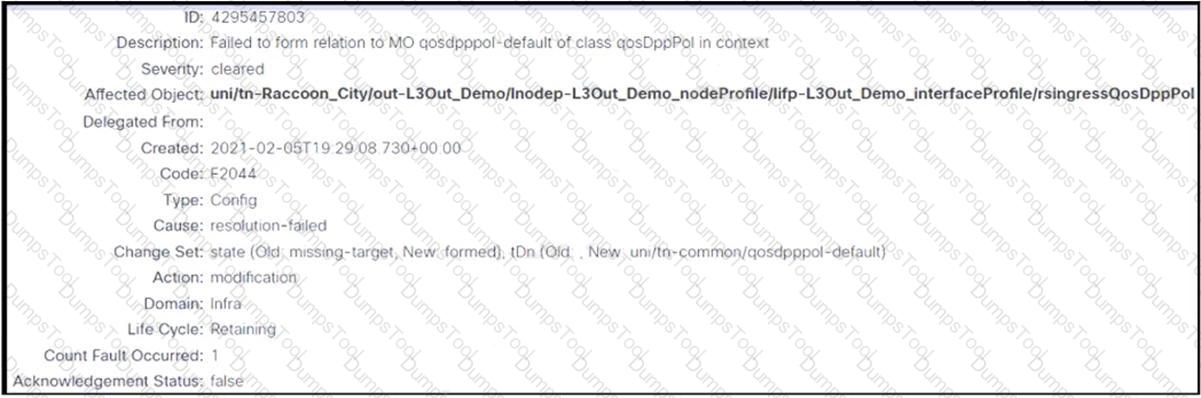
Refer to the exhibit. An engineer configures an L3Out but receives the error presented. Which action clears the fault?
An engineer associates EPG-A with a VMM domain and sets the Deployment and Resolution preferences to Immediate. The host that will generate endpoints for EPG-A is attached to Leaf-and Leaf-102 using etht1/1. However, no configuration for EPG-A appears to have been pushed to the leaf switches. Which action must be taken for the configuration to be pushed to f-101 and Leaf-102?
An engineer is in the process of discovering a new Cisco ACI fabric consisting of two spines and four leaf switches. The discovery of leaf 1 has just been completed. Which two nodes are expected to be discovered next? (Choose two.)
A bridge domain for a new endpoint group in the Cisco ACI fabric must meet these requirements:
The bridge domain must function as the default gateway for the subnet so that routing remains within the Cisco ACI fabric.
ARP requests must be managed via Layer 3 unicast packets or be dropped to reduce excessive broadcast traffic.
The impact of misconfigured virtual machines must be kept to a minimum by preventing IP addresses outside of the configured subnet from being routed.
Which set of actions must be taken?
Which attribute should be configured for each user to enable RADIUS for external authentication in Cisco ACI?
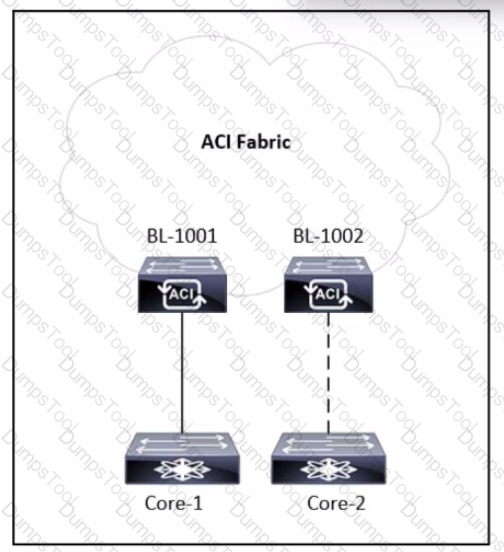
Refer to the exhibit. A tenant is configured with a single L30ut and a single-homed link to the core router called Core-1. An engineer must add a second link to the L30ut that connects to Core-2 router. Which action allows the traffic from Core-2 to BL-1002 to have the same connectivity as the traffic from Core-1 to BL-1001?
The engineer notices frequent MAC and IP address moves between different leaf switch ports. Which action prevents this problem from occurring?
Refer to the exhibit.
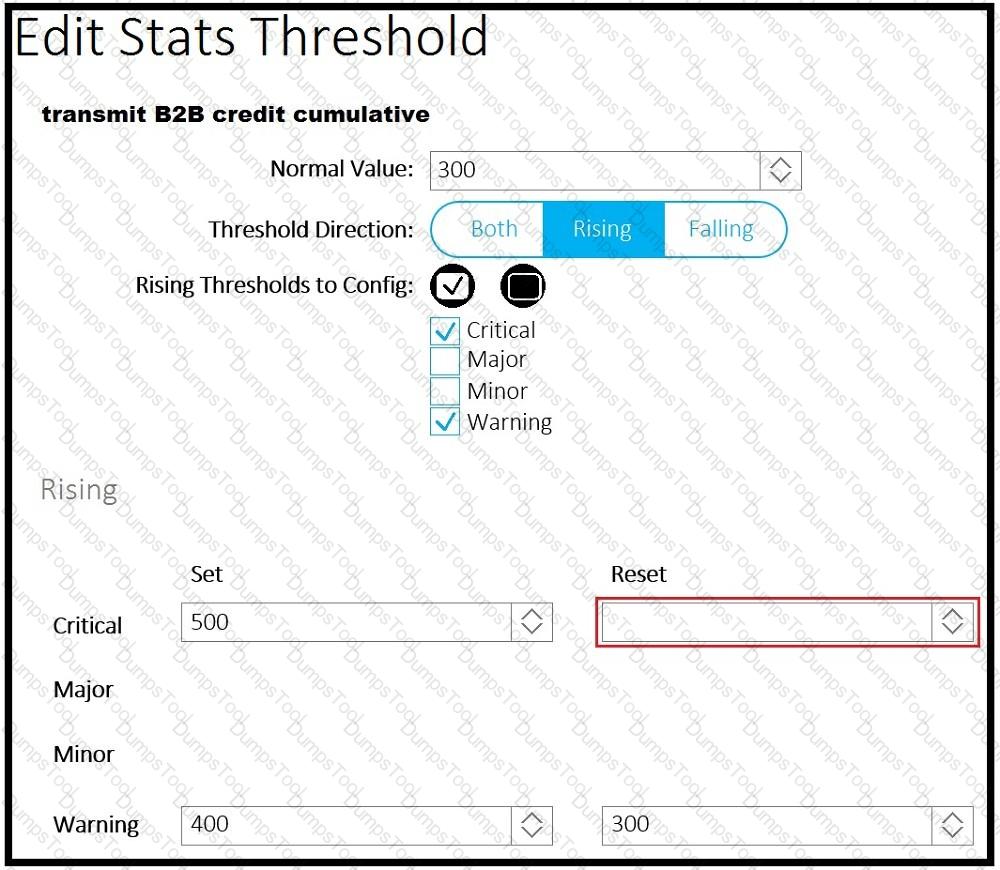
A client reports that the ACI domain connectivity to the fiber channel storage is experiencing a B2B credit oversubscription. The environment has a SYSLOG server for state collection messages. Which value should be chosen to clear the critical fault?
Cisco ACI fabric contains 10 standalone leaf switches. An engineer must configure only the first two leaf switches in a VPC. Which VPC protection type must be configured to accomplish goal?
An organization deploys active-active data centers and active-standby firewalls in each data center. Which action should be taken in a Cisco ACI Multi-Pod to maintain traffic symmetry through the firewalls?
An engineer is configuring ACI VMM domain integration with Cisco UCS-B Series. Which type of port channel policy must be configured in the vSwitch policy?
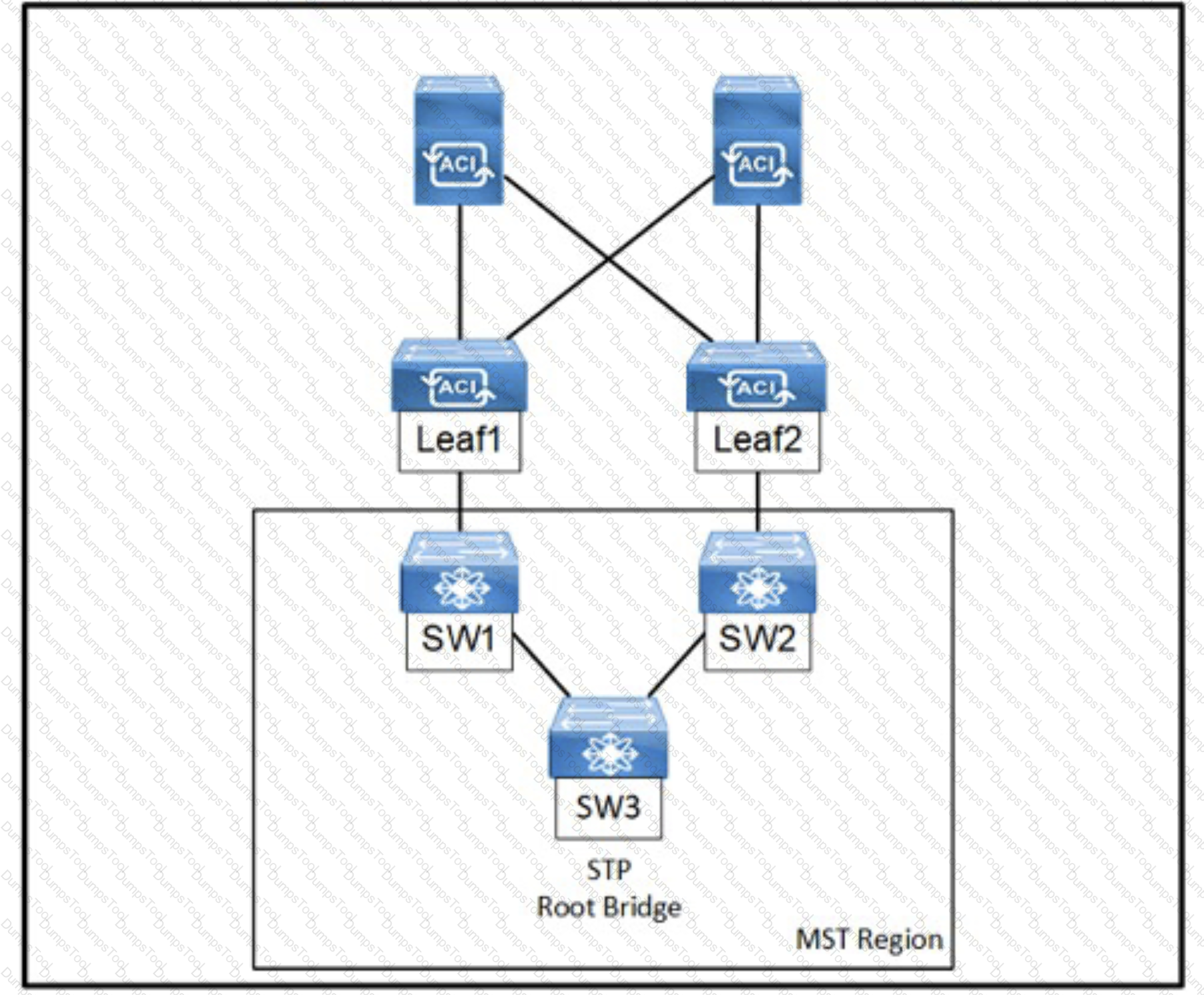
Refer to the exhibit, An engineer is deploying a Cisco ACI environment but experiences a STP loop between switch1 and switch2. Which configuration step is needed to break the STP loop?
Refer to the exhibit.
An engineer is implementing a BPDU filter on external switch interfaces That face the Cisco ACI fabric to prevent excessive TCNs from impacting the fabric. Which Configuration must be applied on Cisco ACI to avoid a Layer 2 loop?
The Application team reports that a previously existing port group has disappeared from vCenter. An engineer confirms that the VM domain association for the EPG is no longer present. Which action determines which user is responsible for the change?
An engineer configures port-12 on Leaf-101 and Leaf-102 to connect to a new server, SVR-12. The new server will belong to EPG-12 and use encap VLAN-1212. The engineer configured SVR-12 as a VPC member port and statically bound the VPC member port to EPG-12. Which additional step must the engineer take to configure connectivity?
A company is implementing a new security policy to track system access, configuration, and changes. The network engineer must enable the log collection to track user login and logout attempts. In addition, any configuration changes such as a fabric node failure must be collected in the logs. The syslog policy is configured to send logs to the company SEIM appliance.
Which two log types must be enabled to meet the security requirements? (Choose two.)
Which new construct must a user create when configuring in-band management?
Which type of policy configures the suppression of faults that are generated from a port being down?
An engineer configures a one-armed policy-based redirect service Insertion for an unmanaged firewall. The engineer configures these Cisco ACI objects:
a contract named All_Traffic_Allowed
a Layer 4 to Layer 7 device named FW-Device
a policy-based redirect policy named FW-1Arm-Policy-Based RedirectPolicy
Which configuration set redirects the traffic to the firewall?
What is the advantage of implementing an active-active firewall cluster that is stretched across separate pods when anycast services are configured?
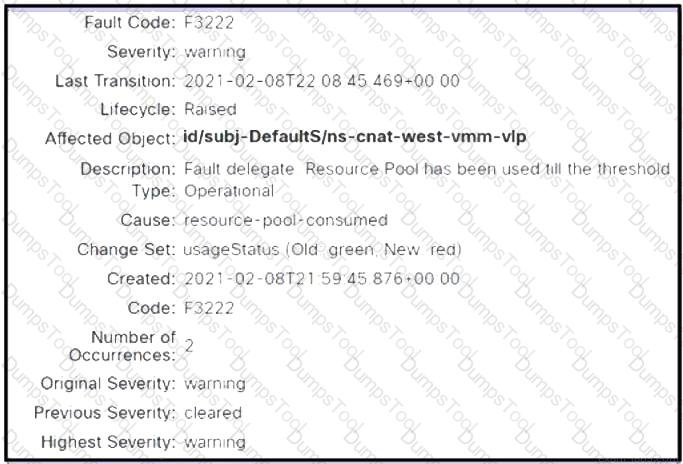
Refer to the exhibit. A Cisco APIC raises an error when the EPG must accept endpoints from a VMM domain created. Which action clears the fault?
How does Cisco ACI detect the IP address of a silent host that moved from one location to another without notifying a Cisco ACI leaf?
Engineer must configure SNMP inside a Cisco ACI fabric. The engineer has created an SNMP Policy, called SNMP-policy and an SNMP Monitoring Group called SNMP-group1 that Contains five trap receivers. Which configuration set completes the configuration?
An engineer must configure a group of servers with a contract that uses TCP port 80. The EGP that contains the web servers requires an external Layer 3 cloud to initiate communication. Which action must be taken to meet these requirements?
What is the result of selecting the On Demand attribute in the Deploy Immediacy feature during VMM domain association to an EPG?
An engineer created two interface protocol policies called Pol_CDP40275332 and Pol_LLDP46783451. The policies must be used together in a single policy. Which ACI object must be used?
Refer to the exhibit.
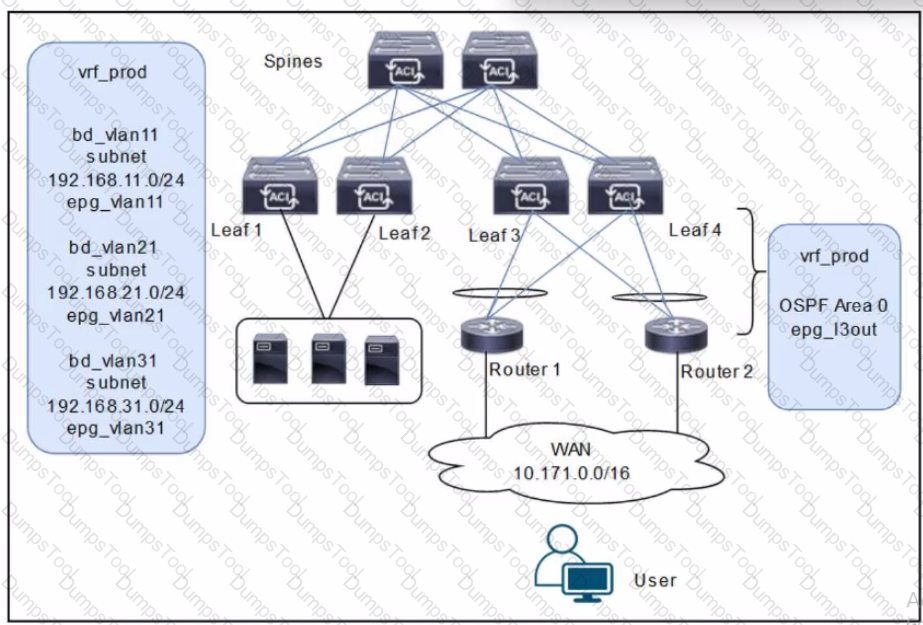
A customer is deploying a WAN with these requirements: •Routers 1 and 2 must receive only routes 192.168.11.0/24 and 192.168.21.0724 from the Cisco ACI fabric •Reachability to the WAN users must be permitted only for the servers that are located in vrf_prod.
Which settings must be configured to meet these objectives?
Refer to the exhibit.
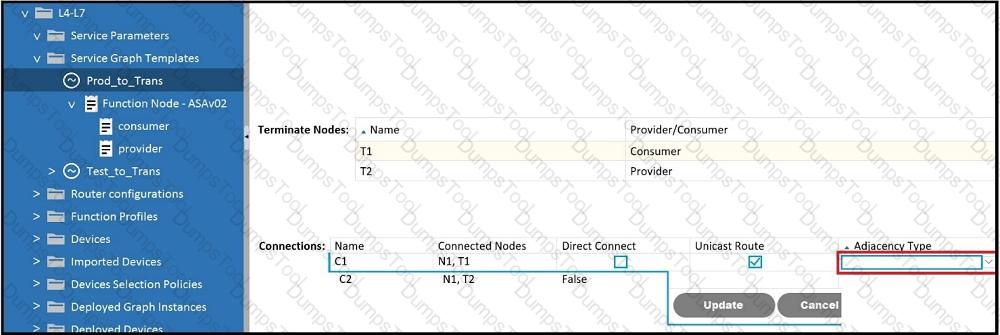
Which Adjacency Type value should be set when the client endpoint and the service node
interface are in a different subnet?
Which two dynamic routing protocols are supported when using Cisco ACI to connect to an external Layer 3 network? (Choose two.)
An engineer needs to avoid loops in the ACI network and needs an ACI leaf switch to error-disable an interface if the interface receives an ACI-generated packet. Which action meets these requirements?
What two actions should be taken to deploy a new Cisco ACI Multi-Pod setup? (Choose two.)
Which routing protocol is supported between Cisco ACI spines and IPNs in a Cisco ACI Multi-Pod environment?
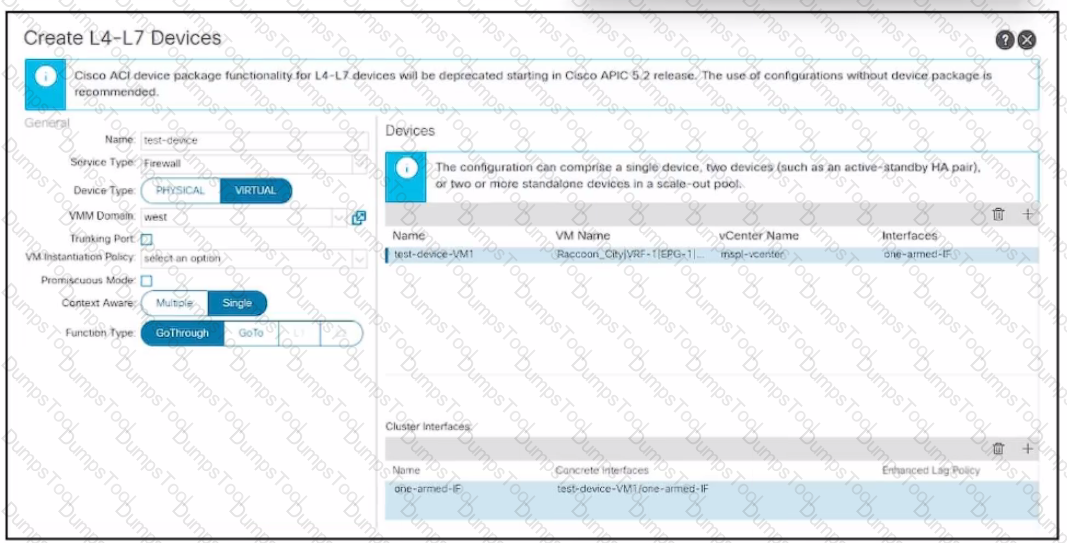
Refer to the exhibit. An engineer configures a Layer 4 to Layer 7 device object. The device is a virtual firewall with a single network adapter and it must be deployed in routed mode. Which .. completes the configuration of the device object?
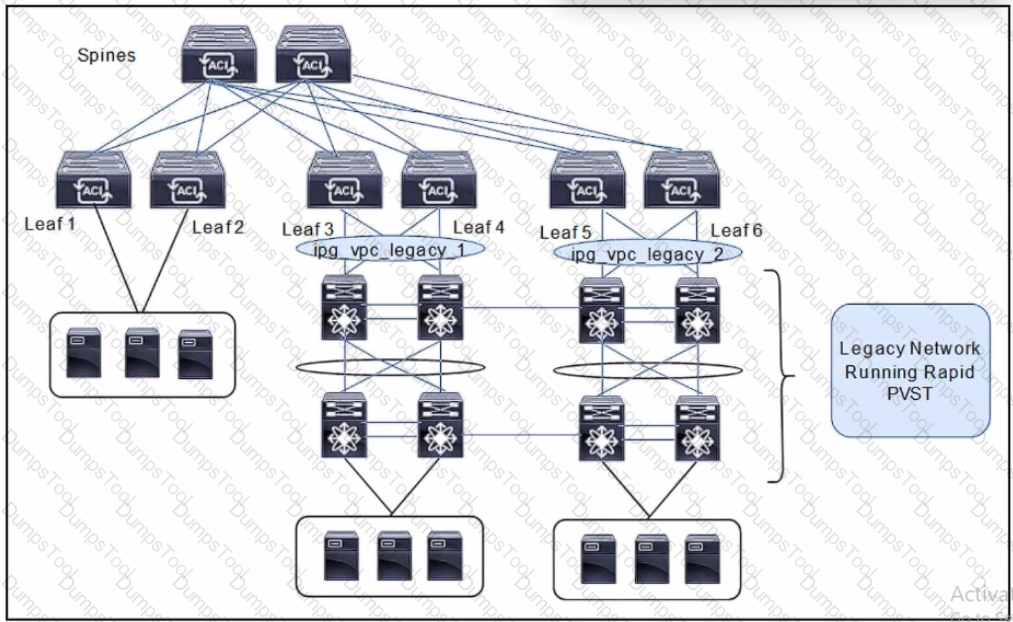
Refer to the exhibit. A client is configuring a new Cisco ACI fabric. All VLANs will be extended during the migration phase using the VPC connections on leaf switches 3. 4 and leaf switches toward the legacy network. The migration phase has these requirements;
* If The legacy switches must be able to transfer BPDUs through the ACI fabric.
* If the legacy switches fail to break a loop. Cisco ACI must break the loop.
Which group settings must be configured on VPC interface policy groups ipg_vpc-legacy_1 and ipg_vpc-legacy_2 to meet these requirements?
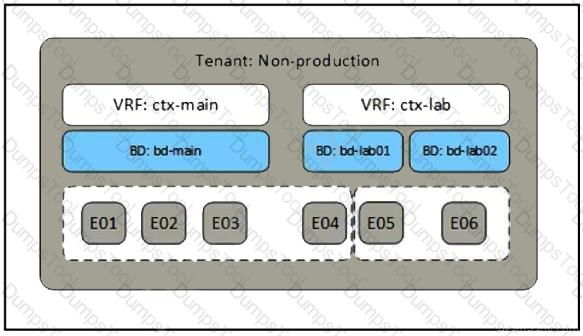
Refer to the exhibit. A network engineer must complete the Cisco ACI implementation based on the logical system design created by the systems architect. Which Cisco ACI object is required where the dotted line indicates to complete the task?
Which statement about ACI syslog is true or Which statement describes the ACI syslog?
An engineer is implementing a Cisco ACI environment that consists of more than 20 servers. Two of the servers support only Cisco Discovery Protocol with no order link discovery protocol. The engineer wants the servers to be discovered automatically by the Cisco ACI fabric when connected. Which action must be taken to meet this requirement?
Which components must be configured for the BGP Route Reflector policy to take effect?
Engineer resolves an underlying condition of a fault but notices that the fault was not deleted from the Faults view. Which two actions must be taken to remove the fault? (Choose two.)
An engineer configures an L30ut in VRF-1 that was configured for Import Route Control Enforcement. The L30ut uses OSPF to peer with a core switch. The L30ut has one external EPG, it has been configured with a subnet 10.1.0.0/24. Which scope must be set to force 10.1.0.0/24 to populate in the routing table for VRF-1?
How many ARP requests are sent from leaf switches to perform host tracking for local endpoints?
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
How is broadcast forwarded in Cisco ACI Multi-Pod after ARP flooding is enabled?
When Cisco ACI connects to an outside Layers 2 network, where does the ACI fabric flood the STP BPDU frame?
In a Cisco ACI Multi-Site fabric, the Inter-Site BUM Traffic Allow option is enabled in a specific stretched bridge domain. What is used to forward BUM traffic to all endpoints in the same broadcast domain?
A network administrator configures AAA inside the Cisco ACI fabric. The authentication goes through the local users if the TACACS+ server is not reachable. If the Cisco APIC is out of the cluster, the access must be granted through the fallback domain. Which configuration set meets these requirements?
Regarding the MTU value of MP-BGP EVPN control plane packets in Cisco ACI, which statement about communication between spine nodes in different sites is true?
The company ESXi infrastructure is hosted on the Cisco UCS-B Blade Servers. The company decided to take advantage of ACI VMM integration to enable consistent enforcement of policies across virtual and physical workloads. The requirement is to prevent the packet loss between the distributed virtual switch and the ACI fabric. Which setting must be implemented on a vSwitch policy to accomplish this goal?
A Cisco ACI fabric is integrated with a Cisco ASA firewall using a service graph under the tenant called Operations. The fabric must permit the firewall used on tenant Operations to be referenced by the tenant called Management. Which export action must be used to accomplish this goal?
What are two requirements for the IPN network when implementing a Multi-Pod ACI fabric? (Choose two.)
A Solutions Architect is asked to design two data centers based on Cisco ACI technology that can extend L2/ L3, VXLAN, and network policy across locations. ACI Multi-Pod has been selected. Which two requirements must be considered in this design? (Choose two.)
Which protocol is used in a Multi-Pod topology to synchronize reachability information across pods?
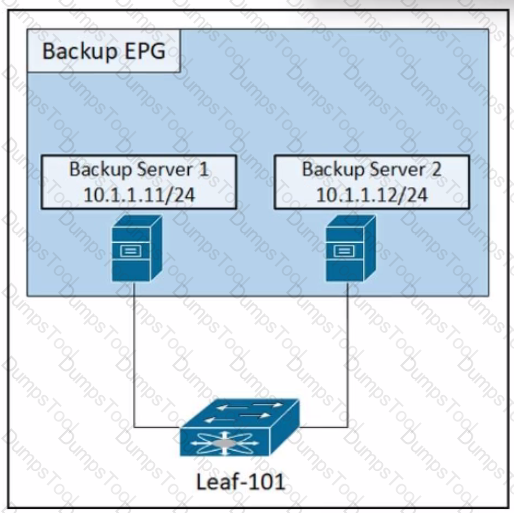
Refer to the exhibit. An engineer must disable the communication between the two backup servers in the backup EPG. Which action accomplishes this goal?
Which type of profile needs to be created to deploy an access port policy group?
A packet is routed between two endpoints on different Cisco ACI leaf switches. Which VXLAN VNID is applied to the packet?
A network engineer is integrating a new Hyperflex storage duster into an existing Cisco ACI fabric The Hyperflex cluster must be managed by vCenter so a new vSphere Distributed switch must be created In addition the hardware discovery must be performed by a vendor-neutral discovery protocol Which set of steps meets these requirements'?

A Cisco ACI bridge domain and VRF are configured with a default data-plane learning configuration. Which two endpoint attributes are programmed in the leaf switch when receiving traffic? (Choose two.)
A network engineer must configure a Cisco ACI system to detect network loops for untagged and tagged traffic The loop must be detected and slopped by disabling an interface within 4 seconds Which configuration must be used?

An engineer plans a Cisco ACI firmware upgrade. The ACI fabric consists of three Cisco APIC controllers, two spine switches, and four leaf switches. Two leaf switches have 1-Gb copper s for bare metal servers, and the other two leaf switches have 10-Gb SFP ports to connect storage. Which set of actions accomplishes an upgrade with minimal disruptions?
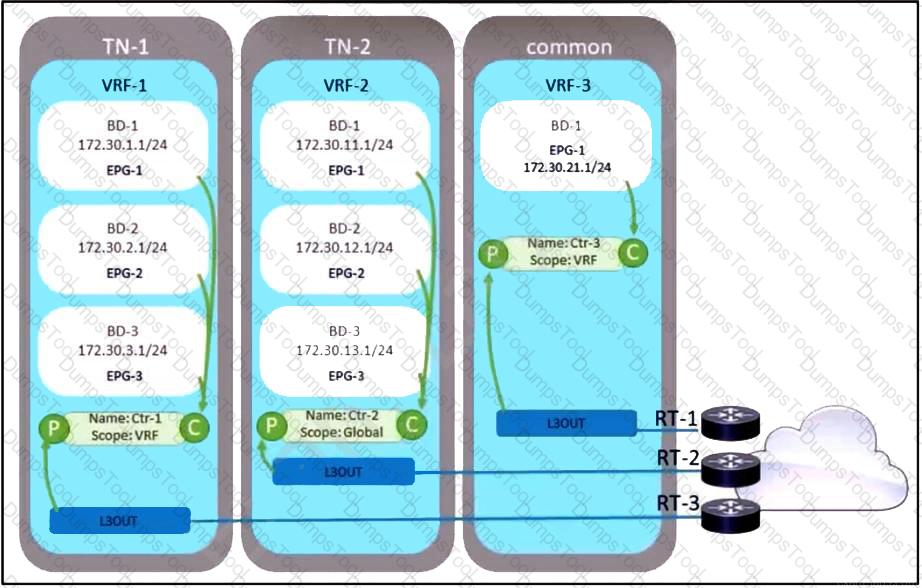
Refer to the exhibit. A company decided to decrease its routing footprint and remove RT-2 and RT-3 devices from its data center. Because of that, the exit point must be created from all the tenants by using the common tenant. Which two configuration tasks must be completed to meet these requirements? (Choose two.)
An engineer must securely export Cisco APIC configuration snapshots to a secure, offsite location The exported configuration must be transferred using an encrypted tunnel and encoded with a platform-agnostic data format that provides namespace support Which configuration set must be used?

A customer is deploying a new application across two ACI pods that is sensitive to latency and jitter. The application sets the DSCP values of packets to AF31 and CS6, respectively. Which configuration changes must be made on the APIC to support the new application and prevent packets from being delayed or dropped between pods?
An engineer is troubleshooting fabric discovery in a newly deployed Cisco ACI fabric and analyzes this output:
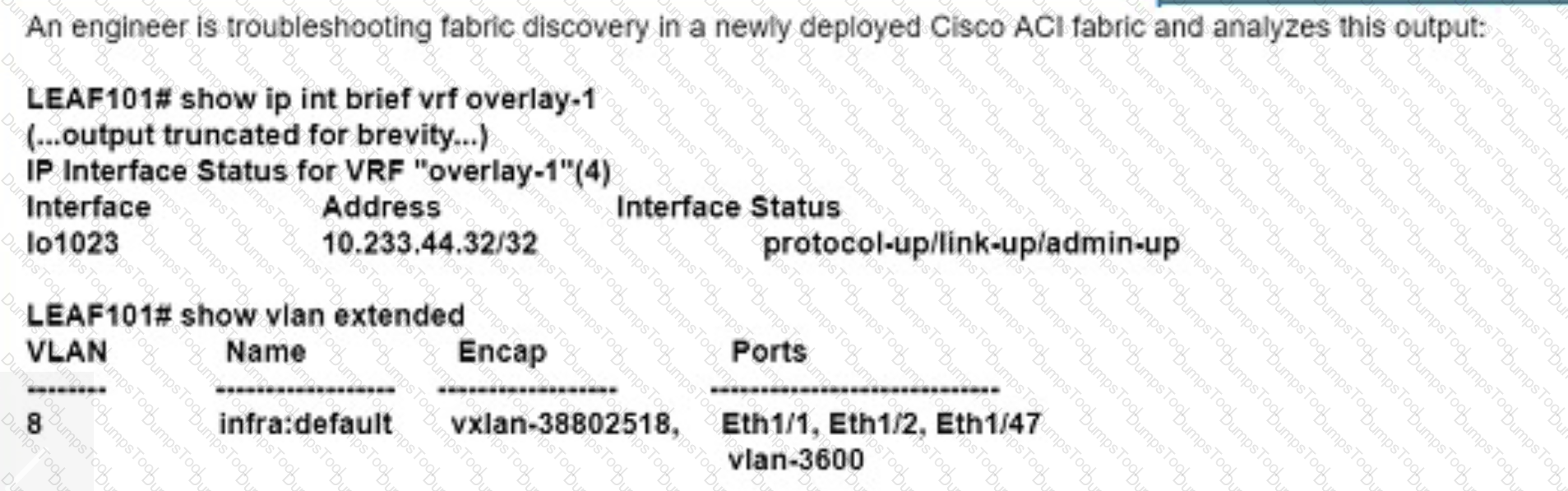
Which ACI fabric address is assigned to interface lo1023?
The company’s Cisco ACI fabric hosts multiple customer tenants. To meet a service level agreement, the company is constantly monitoring the Cisco ACI environment. Syslog is one of the methods used for monitoring. Only events related to leaf and spine environmental information without specific customer data should be logged. To which ACI object must the configuration be applied to meet these requirements?
An engineer configures a Cisco ACI Multi-Pod for disaster recovery. Which action should be taken for the new nodes to be discoverable by the existing Cisco APICs?