Which Hyperledger Fabric ordering mechanism is recommended for production use?
When designing a client application it is important to note that queries are defined in a query file (.qry).
Where is this .qry file stored?
What is the best description of how Kafka is utilized for consensus approach in Hyperledger Fabric?
The security module works in conjunction with the ________________________ module to provide access control service to any data recorded and business logic deployed on a chain network.
You are starting to understand the needed package dependencies for chaincode. What are the two required packages? (Select two.)
What type of node commits transactions & keeps the data in sync across the ledger?
In Hyperledger Composer resources are declared which three ways? (Choose three.)
Hyperledger Fabric essentially implements a private validator network protocol.
Which of the following statements are true?
Voting-based algorithms are advantageous in that they provide a benefit but a tradeoff. (Select two.)
Smart contracts are created by computer programmers through the help of smart contract development tools and are entirely digital. These programs are usually written using programming code languages.
Which of the following languages would not be ideal for use in smart contracts?
Exhibit.
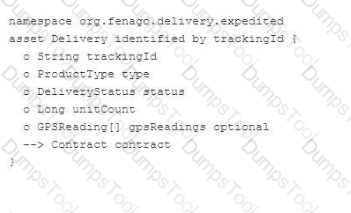
Based on the code snippet, the unique identifier for the Delivery is:
REST (Representational State Transfer) Server is often used to proxy requests to Hyperledger chaincode.
What value does using REST APIS provide?
Which of the following is the best answer when reviewing a "Code Invoking Transaction" in Hyperledger Fabric?
Which Hyperledger Tool brings on demand as-a-service deployment model into the blockchain ecosystem in order to reduce the effort required to create, manage, and terminate blockchains?
In Hyperledger Fabric channels are used to ensure privacy and confidentiality. Which of the following is not correct about channels?
Exhibit.
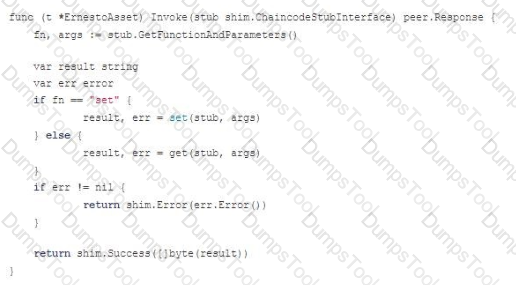
Based on the code snippet displayed, if fn Is nil - what are the possibilities
The CA (Certificate Authority) in Hyperledger Fabric issues the certificates. These certificates are used for identity validation and for transmission of encrypted data that only the owner (person, organization or software) of a specific certificate is able to decrypt and read.
What types of certificates are issued by the CA?
A business wants only certain parties using the DLT to have visibility/access to their data. This refers to the______challenge
The gossip data dissemination protocol performs which three functions? (Choose three.)
Hyperledger Fabric allows multiple certification authorities to be setup for a business network application.
E.g., it there are 3 members using the network application, all 3 members can issue certificates to their employees so they can initiate transactions on the network
application.