Application developers are reporting Access Denied errors when trying to list the contents of an Amazon S3 bucket by using the IAM user “arn:aws:iam::111111111111:user/application”. The following S3 bucket policy is in use:
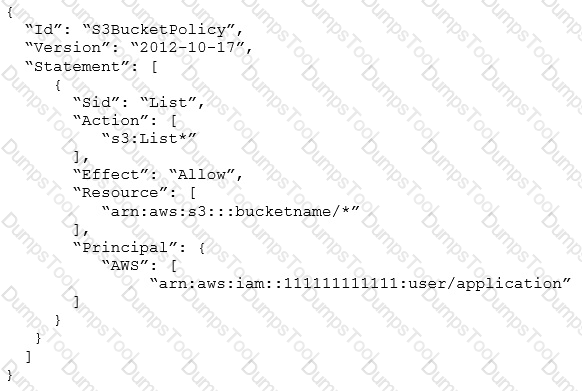
How should a SysOps Administrator modify the S3 bucket policy to fix the issue?
A SysOps Administrator working on an Amazon EC2 instance has misconfigured the clock by one hour. The EC2 instance is sending data to Amazon CloudWatch through the CloudWatch agent. The timestamps on the logs are 45 minutes in the future.
What will be the result of this configuration?
A company uses multiple accounts for its applications. Account A manages the company’s Amazon Route 53 domains and hosted zones. Account B uses a load balancer fronting the company’s web servers.
How can the company use Route 53 to point to the load balancer in the MOST cost-effective and efficient manner?
A SysOps Administrator has been asked to configure user-defined cost allocation tags for a new AWS account. The company is using AWS Organizations for account management.
What should the Administrator do to enable user-defined cost allocation tags?
A company has centralized all its logs into one Amazon CloudWatch Logs log group. The SysOps Administrator is to alert different teams of any issues relevant to them.
What is the MOST efficient approach to accomplish this?
Which component of an Ethernet frame is used to notify a host that traffic is coming?
An Applications team has successfully deployed an AWS CloudFormation stack consisting of 30 t2-medium Amazon EC2 instances in the us-west-2 Region. When using the same template to launch a stack in us-east-2, the launch failed and rolled back after launching only 10 EC2 instances.
What is a possible cause of this failure?
A company wants to icrease the availability and vulnerability of a critical business application. The appliation currently ueses a MySQL database running on an Amazon EC2 instance. The company wants to minimize application changes.
How should the company these requirements?
A SysOps Administrator is responsible for a large fleet of EC2 instances and must know whether any
instances will be affected by upcoming hardware maintenance.
Which option would provide this information with the LEAST administrative overhead?
After a network change, application servers cannot connect to the corresponding Amazon RDS MySQL database.
What should the SysOps Administrator analyze?
A SysOps administrator needs to register targets for a Network Load Balancer (NL8) using IP addresses Which prerequisite should the SysOps administrator validate to perform this task?
An organization has been running their website on several m2 Linux instances behind a Classic Load Balancer for more than two years. Traffic and utilization have been constant and predictable.
What should the organization do to reduce costs?
A SysOps Administrator at an ecommerce company discovers that several 404 errors are being sent to one IP address every minute. The Administrator suspects a bot is collecting information about products listed on the company’s website.
Which service should be used to block this suspected malicious activity?
A SysOps Administrator is creating additional Amazon EC2 instances and receives an InstanceLimitExceeded error.
What is the cause of the issue and how can it be resolved?
An application running on Amazon EC2 instances in an Auto Scaling group across multiple Availability Zones was deployed using an AWS CloudFormation template. A sysops administrator has patched the Amazon Machine Image (AMI) version and must update all the EC2 instances to use the new AMI.
How should Ihe administrator use CloudFormation to apply the new AMI while maintaining a minimum level of active instances to ensure service continuity?
A company has a multi-tier web application. In the web tier, all the servers are in private subnets inside a VPC. The development team wants to make changes to the application that requires access to Amazon S3.
What should be done to accomplish this?
A sysops administrator created an AWS Lambda function within a VPC with no access to the internet. The Lambda function pulls messages from an Amazon SOS queue and stores them in an Amazon RDS instance in the same VPC. After executing the Lambda function, the data is not showing up on the RDS instance.
Which of the following are possible causes for this? (Select TWO.)
A company recently implemented an Amazon S3 lifecycle rule that accidentally deleted objects from one of its S3 buckets. The bucket has S3 versioning enabled.
Which actions will restore the objects? (Choose two.)
A sysops administrator is writing an AWS Cloud Formation template. The template will create a new Amazon S3 bucket and copy objects from an existing Amazon S3 bucket into the new bucket. The objects include data files, images, and scripts.
How should the CIoudFormation template be configured to perform this copy operation?
A SysOps Administrator is required to monitor free space on Amazon EBS volumes attached to Microsoft Windows-based Amazon EC2 instances within a company’s account. The Administrator must be alerted to potential issues. What should the Administrator do to receive email alerts before low storage space affects EC2 instance performance?
A SySOps Administrator is managing an AWS account where Developers are authorized to launch Amazon EC2 instances to test new code. To limit costs, the Administrator must ensure that the EC2 instances in the account are terminated 24 hours after launch.
How should the Administrator meet these requirements?
A SysOps Administrator is deploying a test site running on Amazon EC2 instances. The application requires both incoming and outgoing connectivity to the Internet.
Which combination of steps are required to provide internet connectivity to the EC2 instances? (Choose two.)
A SysOps Administrator has been notified that some Amazon EC2 instances in the company’s environment might have a vulnerable software version installed.
What should be done to check all of the instances in the environment with the LEAST operational overhead?
A company's application running on Amazon EC2 Linux recently crashed because it ran out ot available memory. Management wants to be alerted if this ever happens again. Which combination of steps will accomplish this? (Select TWO.)
A medical imaging company needs lo process large amounts of imaging data in real time using a specific instance type. The company wants to guarantee sufficient resource capacity for 1 year
Which action will meet these requirements in the MOST cost-effective manner?
A sysops administrator runs a web application that is using a microservices approach whereby different responsibilities of the application have been divided in a separate microservice running on a different Amazon EC2 instance The administrator has been tasked with reconfiguring the infrastructure to support this approach
How can the administrator accomplish this with the LEAST administrative overhead?
A company is using an AWS KMS customer master key (CMK) with imported key material. The company references the CMK by its alias in the Java application to encrypt data. The CMK must be rotated every 6 months
What is the process to rotate the key?
A company has deployed a fleet of Amazon EC2 web servers for the upcoming release of a new product. The SysOps Administrator needs to test the Amazon CloudWatch notification settings for this deployment to ensure that a notification is sent using Amazon SNS if the CPU utilization of an EC2 instance exceeds 70%.
How should the Administrator accomplish this?
A company has a sales department and a marketing department. The company uses one AWS account. There Is a need to determine what charges are incurred on the AWS platform by each department. There is also a need to receive notifications when a specified cost level is approached or exceeded.
Which actions must a SysOps administrator take to achieve both requirements with the LEAST amount of administrative overhead? (Select TWO.)
A company has an AWS account for each department and wants to consolidate billing and reduce overhead. The company wants to make sure that the finance team is denied from accessing services other than Amazon EC2: the security team is denied from accessing services other than AWS CloudTrail. and IT can access any resource.
Which solution meets these requirements with the LEAST amount of operational overhead''
An application running on Amazon EC2 allows users to launch batch jobs for data analysis. The jobs are run asynchronously, and the user is notified when they are complete. While multiple jobs can run concurrently, a user’s request need not be fulfilled for up to 24 hours. To run a job, the application launches an additional EC2 instance that performs all the analytics calculations. A job takes between 75 and 110 minutes to complete and cannot be interrupted.
What is the MOST cost-effective way to run this workload?
A company’s static website hosted on Amazon S3 was launched recently, and is being used by tens of thousands of users. Subsequently, website users are experiencing 503 service unavailable errors.
Why are these errors occurring?
A company uses AWS CloudFormation to deploy its application infrastructure. Recently, a user accidentally changed a property of a database in a CloudFormation template and performed a stack update that caused an interruption to the application. A SysOps Administrator must determine how to modify the deployment process to allow the DevOps team to continue to deploy the infrastructure, but prevent against accidental modifications to specific resources.
Which solution will meet these requirements?
A security audit revealed that the security groups in a VPC have ports 22 and 3389 open to all. introducing a possible threat that instances can be stopped or configurations can be modified. A SysOps administrator needs to automate remediation.
What should the administrator do to meet these requirements?