What is the maximum number of computers that could be adequately managed for an "on-box" installation of the Microsoft SQL Server with Notification Server
While processing instructions, whether received through a policy, job or task, the SMA may be required to does information back to the NS. How is this process accomplished?
Which action does the Symantec Management Agent perform when it receives a tickle packet?
Which installation package should an administrator use to install the Cloud-enabled Management services on an Internet-facing server?
The Symantec agent is currently communicating with the notification server via https.
Which additional prerequisite must be met for the Symantec management agent to communicate over the internet?
Which option is considered a container and is the primary method of organizing and managing resources such as computers and users in IT Management Suite 8.5?
Which two (2) plug-ins are used by Inventory Solution to gather and monitor application-related data? (Select two.)
What task, if completed, will likely fix many of the performance related issues an administrator may experience in an IT Management Suite implementation, when solving a database performance related issues?
Which reason should an administrator consider using Microsoft SQL server clusteringd when implementing IT Management Suite 8.5?
Which two (2) elements can an administrator include when building a resource target in the Computers blade of the IT Management Views? (Select two.)
An admin for a hospital system is tasked with tracking electrocardiogram (EKG) devices. The admin decides to base the custom EKG resource type on the computer
What does basing this custom resource type on the existing resource type allow?
Which component of the Symantec Management Platform attempts to choose a new communication path when the default communication method with the Notification Server is unavailable?
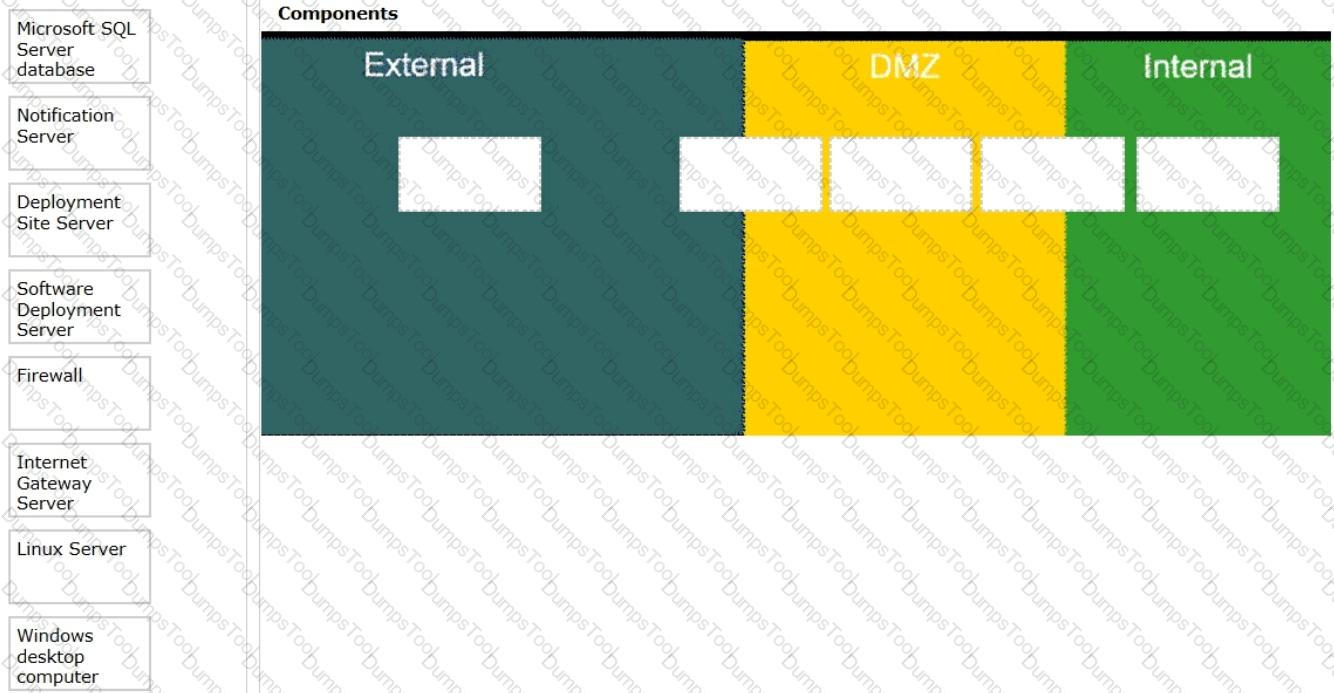
How should an administrator configure the components on the left in order to inventory computers that are connected only through the Internet?
Drag and drop the components on the left into the correct zones on the right.
An administrator lacks permissions to a subset of resources by a filter due to role and scope-based security settings. The administrator selects the filter in the console.
What will the administrator see in the list pane of this filter?