A Symantec Endpoint Protection (SEP) administrator is remotely deploying SEP clients, but the clients are failing to install on Windows XP.
What are two possible reasons for preventing installation? (Select two.)
A financial company enforces a security policy that prevents banking system workstations from connecting to the Internet.
Which Symantec Endpoint Protection technology is ineffective on this company's workstations?
An administrator receives a browser certificate warning when accessing the Symantec Endpoint Protection Manager (SEPM) Web console.
Where can the administrator obtain the certificate?
Which protection engine should an administrator enable in order to drop malicious vulnerability scans against a client system?
An administrator needs to configure Secure Socket Layer (SSL) communication for clients. In the httpd.conf file, located on the Symantec Endpoint Protection Manager (SEPM), the administrator removes the hashmark (#) from the text string displayed below.
#Include conf/ssl/sslForcClients.conf<
Which two tasks must the administrator perform to complete the SSL configuration? (Select two.)
An administrator uses the search criteria displayed in the image below.
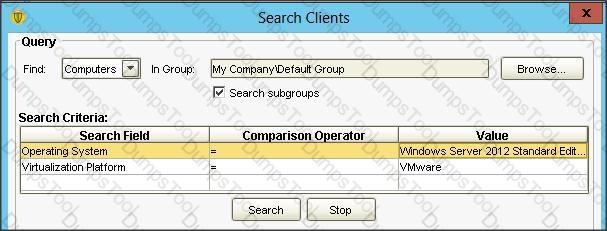
Which results are returned from the query?
Which Symantec Endpoint Protection component enables access to data through ad-hoc reports and charts with pivot tables?
A user is unknowingly about to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client's system.
In which feature set order must the threat pass through to successfully infect the system?
Administrators at a company share a single terminal for configuring Symantec Endpoint Protection. The administrators want to ensure that each administrator using the console is forced to authenticate using their individual credentials. They are concerned that administrators may forget to log off the terminal, which would easily allow others to gain access to the Symantec Endpoint Protection Manager (SEPM) console.
Which setting should the administrator disable to minimize the risk of non-authorized users logging into the SEPM console?
An administrator plans to implement a multi-site Symantec Endpoint Protection (SEP) deployment. The administrator needs to determine whether replication is viable without needing to make network firewall changes or change defaults in SEP.
Which port should the administrator verify is open on the path of communication between the two proposed sites?
Which package type should an administrator use to reduce a SEP environment’s footprint when considering that new SEP 14 clients will be installed on point of sale terminals?
A system running Symantec Endpoint Protection is assigned to a group with client user interface control settings set to mixed mode with Auto-Protect options set to Client. The user on the system is unable to turn off Auto-Protect.
What is the likely cause of this problem?
Refer to the exhibit.
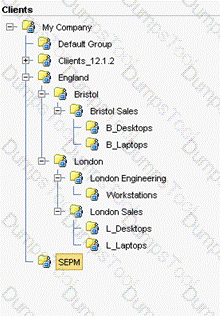
A manufacturing company runs three shifts at their Bristol Sales office. These employees currently share desktops in the B_Desktops group. The administrators need to apply different policies/configurations for each shift.
Which step should the administrator take in order to implement shift policies after switching the clients to user mode?