Service Mapping provides visibility to the Operator in Agent Workspace without leaving the Workspace UI. This visibility includes what items associated with the CI? (Choose two.)
The application stack is as follows: IIS Web Server with an inclusion connection to an IIS Virtual Directory, and an outbound connection from the IIS Virtual Directory to an MSSQL database.
Which describes the correct number of Discovery Pattern Identification and Connection Sections that evaluate to true when Service Mapping discovers a service with this application stack?
Which of the following are potential benefits when implementing Service Mapping? (Choose four.)
Which one of the following Regular Expressions could be used to parse "San Diego" from the string "Location San Diego"?
Which one of the following Identification Rule (CI Identifier) fields, when selected, determines CMDB update/inserts based on the configuration item's (CI) own attributes, without taking other CIs or relationships into consideration?
In Event Management, which of the following rules allows for automatic task creation?
To begin the configuration of tag-based services, tag values must be defined where?
Which omitted action will keep changes to a discovery pattern connection section from taking effect?
Which one of the following statements best explains the following URL: https://
SaCmdManager.do?ip=198.51.100.66?
In Event Management, if a Message key is not passed from an Event, which of the following Alert fields combine to populate the Message key on an Alert?
Which one of the following in the CMDB Identification and Reconciliation application allows a CMDB administrator to specify authorized data sources that can update a CMDB table or a set of table attributes?
When a Windows Server is reclassified from the Server [cmdb_ci_server] table to the Windows Server [cmdb_ci_win_server] table, which one of the following describes the process that occurred?
During ServiceNow Discovery, which one of the following is the approximate number of host IPs that are port scanned with a Discovery Schedule configured with an IP network as shown?
180.181.0.0/16
In ServiceNow Discovery, which one of the following phases is the server RAM value discovered?
Using Pattern Designer, which one of the following Delimited Text Parsing Strategies could be used to parse CO from the string:
Location, Denver,CO
During Service Mapping discovery, which one of the following is used to uniquely identify a configuration item to determine updates or inserts into the CMDB?
Which one of the following Regular Expressions could be used to parse the value 5.2.0 from the string?
Version 5.2.0
Which one of the following Regular Expressions could be used to parse the value 5.2.0 from the string:
Version 5.2.0?
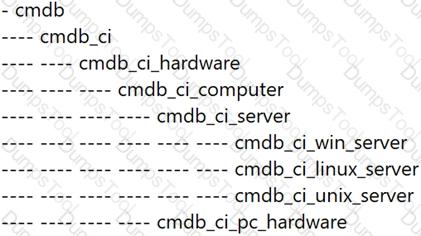
Given the CMDB class structure shown, which types of Configuration Items (CIs) will be included in a report run against the Server [cmdb_ci_server] table?
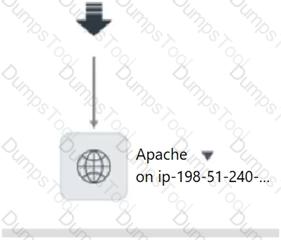
You have run Service Mapping discovery against a customer service and discovered the CI in the image. The customer indicates that Apache should have an outgoing connection to Tomcat. Which one of the following could be the issue?
In order for Service Mapping to successfully discover UNIX targets, which SSH credential can be granted with limited privileges to a user?
When planning for a Service Mapping engagement and deploying MID Servers into a customer environment, which outbound port must be open from the customer environment to allow the MID Server(s) to communicate to the customer ServiceNow instance hosted in the ServiceNow cloud?
In Service Mapping, which one of the following must be available or created in advance, in order to be able to create a Discovery Pattern?
Assuming the Apache Web Server Identification Rule (CI Identifier) is configured as shown with the following
Criterion attributes:
Class
Configuration file
Version
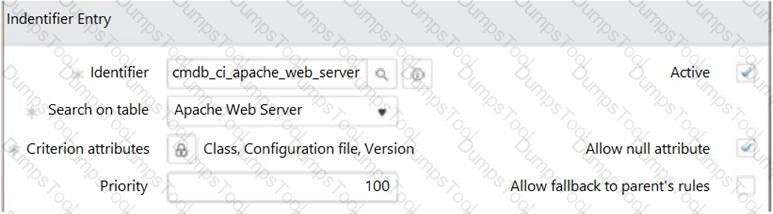
Yesterday, an Apache Web Server CI was discovered as part of Service Mapping. Today, the application owner upgraded the Apache Web Server to a different version and reran discovery of the service. What will happen in the CMDB?
Which represents the skills needed that a Service Mapping administrator or implementer should have?
Choose 4 answers