when a customer submits a credit card dispute, the application connects to an external service to retrieve all transactions made by the customer. the external service returns transactions ordered by date of transaction, in a descending, chronological order. when a case worker reviews the dispute, the application displays the 10 most recent transactions.
if the case worker does not see the disputed transaction in the list, the case worker can search for additional transactions. the case. the case worker can filter search results on transaction date, the transaction amount or the merchant name the search results display the 10 most recent transactions that satisfy the filter criteria. the case worker cannot paginate through the results.
how do you configure the data page to satisfy all the requirements in the scenario?
To access a property from an unconnected component, you use the______________.
A Citizen Developer working on a Claims case type wants to validate the BenefitType property value. This property is located on a Clipboard page named ClaimBenefit of the MyCo-Data-ClaimBenefit class, which is inherited from Data-.
As a Lead System Architect, what do you recommend to make this validation available to the Citizen Developer?
A Pega COE team is building a reusable component for a functionality that will be mandatory for all Pega applications that are built for the different departments of a company.
The component functionality is documented and published in a common SharePoint file, so that it is accessible by all Pega developers within the company.
Which one of the following approaches will work best for this use case?
A user report poor application performance at 5:00 pm yesterday. which two tools do you use to review the user's session to identify the cause of the poor performance ?
A health plan application includes a process for surgical procedure requests. Currently, there is an evaluation subprocess in which a physician reviews the diagnosis and enters the recommended procedure and its urgency. The request then advances to a medical director who analyzes the feedback and approves the appropriate procedure. The health care organization has created a new requirement, which states that three physicians can perform the evaluation independently. Only two evaluations are necessary to advance the case to the medical director.
In order to allow the three physicians to review the orders in parallel, how would you configure the process?
U+ Bank follows all engagement policy best practices to present credit card offers on their website. The bank has introduced a new credit card offer, the Rewards card. Anna, an existing customer, currently holds a higher value card, Premier Rewards, and does not see the new Rewards card offer.
What condition possibly prevents Anna from seeing the new Rewards card offer?
Using the information shown in the Class structure, select the correct statement.
While extracting transactional data from the Pega Platform database to external data store with the Business Intelligence Exchange (BIX) rueset, how do you avoid recalculating declarative properties from its source properties?
In a product management application, the configuration of a flow rule must be different for two products from the hundreds
of other products.
A Pega COE team has been evaluating the specialization design considerations for this requirement.
Which of the following approaches is best suited to this scenario?
An application contains cases which transition though different statuses throughout their life cycle which typically lasts 3 months.
Design a reporting strategy to display the number of cases by status at the end of each month for a 12-month period.
Inconsistent formatting of phone numbers is causing, usability issues. You hnvo been asked to enh interface to ensure all phone numbers are automatically reformatted consistently.
Which two options incorporate best practices for applying the required formatting? (Choose Two)
U+ Bank uses Pega Customer Decision Hub™ to approve credit card limit changes requested by customers automatically. A scorecard model determines the customer credit score. The automatic approval of credit card limits are processed based on the following criteria set by the bank.
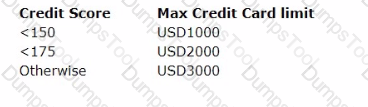
The bank wants to change the threshold value for the USD2000 credit limit from <175 to <200. How do you implement this change?
You isolated the problem to node ! of the cluster. Y see node 1 goes down shortly «ift What is the likely cause of the out of-memory error?
You need to create custom workspaces for the manager and for the Customer service representative (CSR), Also, you are asked to display some properties in custom formats that arc not supported by Pega.
Which approach satisfies these requirements?
As a Customer Service Representative, you present an offer to a customer who called to learn more about a new product. The customer rejects the offer.
What is the next step that Pega Customer Decision Hub takes?
U+ Bank implemented a customer journey for its customers. The journey consists of three stages. The first stage raises awareness about available products, the second stage presents available offers, and in the last stage, customers can talk to an advisor to get a personalized quote. The bank wants to actively increase offers promotion over time.
What action does the bank need to take to achieve this business requirement?
You are working on an insurance claims application that receives claims through email. The company receives 500 emails per hour. the insurance company promises a 24-hour response time to receives and verify the clain. After the claim is verified. The system automatically responds with email containing the claim ID.
The application is developed in the Pega cloud environment. The production environment is currently running on premises.
What is your recommendation to ensure that insurance company can meet the 24-hour response time requirement for claims submitted by email?
your application uses a page type property named customerinfo to store the customer's first and last
names.which two approaches ensure that the customer's first and last names are stored in upper case?(choose two)
You are implementing a paga customer service application and are integrating the system of record data for account information?
select the three tasks required to implement this integation
What two recommendations do you provide to the development team to ensure the performance of the Pega application does not degrade over time? (Choose Two)
Customer information is captured in an application. Corporate policy states that private information be secured and only visible to a limited users.
Which configuration do you recommend?
You are a decisioning architect on a next-best-action project and are responsible for designing and implementing decision strategies Select each component on the left and drag it to the correct requirement on the right.

An application allows users to manage Account cases. You need to configure security so that users are allowed to view and update account only if they are the primary or secondary owner
how do you implement this requirement?
How do you improve performance during synchronization for users of an offline-enable mobile app.
XYZ Corp requires employees to designate alternate operators to perform their work while they are on vacation. Work vacationing operators should be visible to alternate operators.
How do you configure the application to handle this requirement?
Your application is deployed to the cloud. A data source outside your application populates a data page by using your data access pattern configuration. You receive complaints that the system takes a long time to fetch data each time the case worker accesses information for a different customer.
Which approach solves this performance issue?
Identify the two correct statements regarding Localization wizard capabilities. (Choose Two)
What does a dotted line from a "Group By" component to a "Filter" component mean?
Case Type A and Case Type B capture information about multiple line items. Each line item is an Instance erf the same Line Item data type. Separate work pool classes are used for Case Types A and B.
What is the optimal data model design to meet these requirements?
you are writing a report that needs to compute the sum of multipul columns and display the result.
The number of columns to sum varies from report to report but does not exceed five.
which two options can you use to implement this requirement? (choose two)
A recent review of the audit polices log show that a specific IP address has made a large number of failed login attempts within a few minutes you suspect that it is an internet bot attack
Select two options you can configure to prevent the bot from accessing you application
You oversee a medium-size development team, and some of the team members are new to
pega. What are the most efficient ways to ensure that the rules the team creates adhere to
best practices? (choose two)
You deplyed a pega web mashup implementation into production and are using IACAuthentication.
which two action ensure that the external authentication module, and not another source, has validated the user?
An end user of the application experienced a browser crash while working on a highly available system. Crash recovery is enabled. Does the user to be reauthenticated?
A software training company wants to hold a webinar on a particular subject if a sufficient number of people express an interest in attending. An instructor is tasked with developing the webinar presentation, if they get enough people to register. There is no limit on the number of attendees.
Which case design pattern is the best solution in this scenario?
What are two valid reasons for defining a case type within a case type-specific ruleset? (Choose two)
How do you configure an application to monitor changes made to delegated Decision Table in a production environment?
BiyCo has two development projects currently in progress developed by independent teams. One team builds the Quoting application. Another team builds the Policy Administration application. Development takes place on different servers with separate rulebases.
The Quoting application is built on the Policy Administration application.
The Policy Administration application requires enhancements to support other areas of the business.
The Quoting team is notified when the Policy Administration application is versioned. The Quoting team responds by importing a HAP containing the new version.
Select the two best practices to minimize potential development conflicts and work with the most current version of the Policy Administration application. (Choose Two)
An external application calls a Pega REST service, which takes a significant amount of time to respond. Pega Platform returns a unique identifier instantly and runs the service without the application waiting.
Which configuration implements this functionality?
You are working with BigCo to create an application for insurance quoting. BigCo is a multinational corporation that has traded on the NASDAQ as BCO. BigCo headquarters is located in the UK, and the company has division for each geographical location.
You expect the application to contain two types of work: Quote and Policy.
The Quote guides the sales preventative through one or more quote with the customer. Each quote must be retained by the system and visible to the sales representative and the manager, any data captured during the quoting process must be available to the Policy case. The Policy represents the accepted insurance quote.
For the next year, BigCo intends to use the insurance quoting application only for the personal insurance business in the United Kingdom, Joe the business experts (SMEs) to understand the quoting process. Joe uses Pega Express to develop the quoting application with the SMEs.
Default application settings are shown in the image.
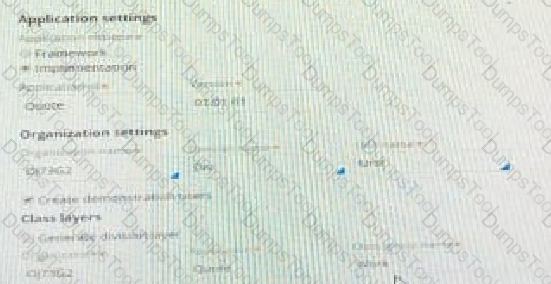
What two edits do you make to the advanced configuration based on information in the reading passage? (Choose Two).
The BigCo quoting application is currently on-premise. BigCo plans to move the application to Pega Cloud What factor do you need to consider for environment setup?
An application processes stock market trades.
which two requirement are best implemented by an advanced agent?
Six weeks after you deliver your application to production, your users report that the application slows down in the afternoon. The application is almost completely unresponsive for some users shortly after
3:00 P.M. Other users do not experience this problem until later in the day.
You do not have access to the Production environment, but you do have access to AES. The production environment has three nodes and a load balancer.
You need to resolve this issue because a new division of the organization will start using the application next month.
How do you begin your research to diagnose the cause of the reported performance issue?
MyCo, a telecom company, developed a new data plan group to suit the needs of its customers. The following table lists the three data plan actions and the criteria that customers must satisfy to qualify for the offer:

How do you configure the engagement policies to implement this requirement? Choose the engagement policy level that is best-suited for each criterion
Using the information shown in the case structure below, which option is always true?
Which two tools and/or methods support continuous integration practices? (Choose Two)
A Pega developer working on customizing GetNextWork functionality has overridden the
GetNextWork_WorkBasketUrgencyThreshold application settings rule, because they want to define a minimum cutoff value for assignment urgency.
Overriding this value can speed things up by changing the order in which assignment candidates are examined.
As an LSA, which one of the following would you recommend as a best practice in this situation?
You are configuring a new version of a data transform that is partially complete. During testing, you want to be able to use previous of the rule.
select the rule configuration that enable you to save ans check in the record with validation error and allows previous versions of the rule to execute.
which two of the following action are required to configure your application to support SSO authentication ?
A healthcare company decides to use Pega Foundation for Healthcare (PFH) for all of their new Pega Platform"" applications, because the data model that PFH provides can accommodate all of their needs. However, some new fields and new data classes need to be created to suit the company's specific processes.
What is the recommended approach to extending the foundation data model?
MyHealth Corporation wants to use the age of the claim to increase the urgency of the assignment so that persons processing the claims work on the most urgent claims first. The claim assignment urgency increases by 1 each day the claim remains in an Unresolved status. At any time, MyHealth has up to 10,000 claims that are in process. Claims in the PendingProcessing workbasket are subject to this calculation. The application updates the claim urgency daily before the work day begins. All claims are processed within 30 days.
Which approach satisfies the claim urgency requirement and provides the best experience for the user who processes the claims?
An organization has two sets of users: Manager and Vice President, with no role dependencies. The organization wants to introduce a new set of users called Senior Manager that has Manager access and a subset of Vice President access.
What is the recommended approach to add the Senior Manager role to meet this requirement?
When implementing a Next-Best-Action, the customer Lifetime value Threshold is used to __________ for an offer
Select three operations that Elasticsearch queries can support when using a report definition. (Choose Three)
U+ Bank is facing an unforeseen technical issue with its customer care system. As a result, the bank wants to share the new temporary contact details with all customers over an SMS.
Which type of outbound interaction do you configure to implement this requirement?
U+ Bank currently uses a Pega Platform'" application to automate its internal operations. The bank wants to add independent tax processing functionality to its application. This work should be routed to tax consultants in the application.
To support this new feature, the bank has appointed country-specific tax consultants because tax processing is handled differently in different countries.
Which one of the following options is the best approach to add tax processing to the bank's existing Pega Platform application?
XYZ corp sells products that can be researched and ordered within a single screen. After the user submits the order, only the ID for each ordered product is propagated to a product child case. An additional property within the product child case reference a data page that displays product detail. XYZ wants you to define a report that shows detail about each product associated within a given order case.
In which class do you optimize the detail properties for the product?
Review the following classes and properties:

A field group list is defined at the MyCo-Lending-Work work pool level. The find group list name is Loans: the specified data type is MyCo-Data-Loan.
Which three statements are valid? (Choose Three)
What is the primary reason for developing a set of unit test cases and automated testing suites in a continuous integration and continuous deployment (CI/CD) model?
Consider the following requirement:
case worker must be able to add a work party when creating a case
select the configuration option that fulfills this requirement
Given the following classes and properties:
myco-data-shape (abstract)
area
color
myco-data-shape-rectangle
length
width
myco-data-shape-circle
radius
a page list property .shapes is defined as being of the abstract class myco-data-shape.
select two correct statements. (choose two)