Which Linux OS command will manually load Docker images onto the Cortex XSOAR server in an air-gapped environment?
A Cortex XSOAR customer wants to send a survey to users asking them to input their manager's email for a training use case so the manager can receive status reports on the employee's training. However, the customer is concerned users will provide incorrect information to avoid sending status updates to their manager.
How can Cortex XSOAR most efficiently sanitize user input prior to using the responses in the playbook?
Why is it important to document notes from the Proof of Value (POV) for post-sales hand off?
Which attack method is a result of techniques designed to gain access through vulnerabilities in the code of an operating system (OS) or application?
The customer has indicated they need EDR data collection capabilities, which Cortex XDR license is required?
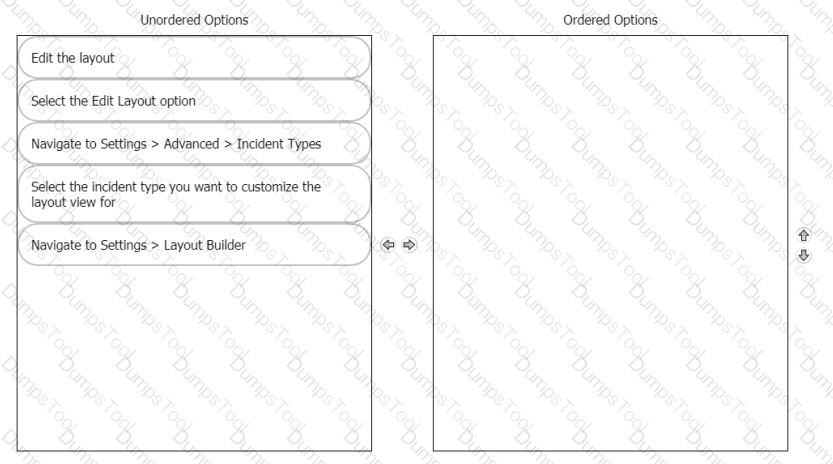
Rearrange the steps into the correct order for modifying an incident layout.
When initiated, which Cortex XDR capability allows immediate termination of the process-or entire process tree-on an anomalous process discovered during investigation of a security event?
Which feature in Cortex XSIAM extends analytics detections to all mapped network and authentication data?
In addition to incident volume, which four critical factors must be evaluated to determine effectiveness and ROI on cybersecurity planning and technology?
Which deployment type supports installation of an engine on Windows, Mac OS. and Linux?
Which statement applies to the malware protection flow in Cortex XDR Prevent?
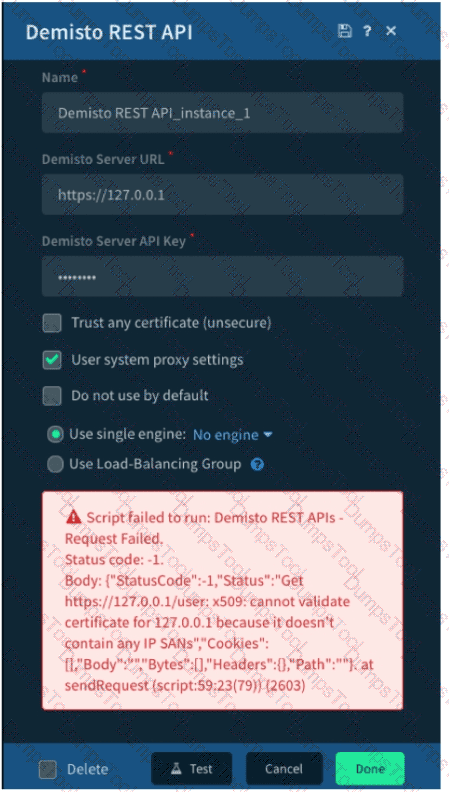
Given the exception thrown in the accompanying image by the Demisto REST API integration, which action would most likely solve the problem?
Which two playbook functionalities allow looping through a group of tasks during playbook execution? (Choose two.)
Which two areas of Cortex XDR are used for threat hunting activities? (Choose two.)
An antivirus refresh project was initiated by the IT operations executive. Who is the best source for discussion about the project's operational considerations'?
An administrator has a critical group of systems running Windows XP SP3 that cannot be upgraded The administrator wants to evaluate the ability of Traps to protect these systems and the word processing applications running on them
How should an administrator perform this evaluation?
Which two Cortex XSOAR incident type features can be customized under Settings > Advanced > Incident Types? (Choose two.)
Which two items are stitched to the Cortex XDR causality chain'' (Choose two)
Which statement applies to the differentiation of Cortex XDR from security information and event management (SIEM)?
Which consideration should be taken into account before deploying Cortex XSOAR?
Which Cortex XDR capability allows for the immediate termination of a process discovered during investigation of a security event?
Which feature of Cortex XSIAM helps analyst reduce the noise and false positives that often plague traditional SIEM systems?
What is the function of reputation scoring in the Threat Intelligence Module of Cortex XSIAM?
An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
Which feature of Cortex XSIAM displays an entire picture of an attack, including the originating process or delivery point?
What are two ways a customer can configure user authentication access Cortex Xpanse? (Choose two.)
Which product enables the discovery, exchange, and contribution of security automation playbooks, built into Cortex XSOAR?
Cortex XDR can schedule recurring scans of endpoints for malware. Identify two methods for initiating an on-demand malware scan (Choose two )
Which integration allows searching and displaying Splunk results within Cortex XSOAR?
In Cortex XDR Prevent, which three matching criteria can be used to dynamically group endpoints? (Choose three )
In addition to migration and go-live, what are two best-practice steps for migrating from SIEM to Cortex XSIAM? (Choose two.)
In an Air-Gapped environment where the Docker package was manually installed after the Cortex XSOAR installation which action allows Cortex XSOAR to access Docker?
What is a benefit of user entity behavior analytics (UEBA) over security information and event management (SIEM)?
If an anomalous process is discovered while investigating the cause of a security event, you can take immediate action to terminate the process or the whole process tree, and block processes from running by initiating which Cortex XDR capability?
When running a Cortex XSIAM proof of value (POV), why is it important to deploy the Cortex XDR agent?
What is the result of creating an exception from an exploit security event?
Which playbook functionality allows grouping of tasks to create functional building blocks?