Which policy set should be used to ensure that a policy is applied just before the default security rules?
You must configure which firewall feature to enable a data-plane interface to submit DNS queries on behalf of the control plane?
Which stage of the cyber-attack lifecycle makes it important to provide ongoing education to users on spear phishing links, unknown emails, and risky websites?
What are the two main reasons a custom application is created? (Choose two.)
Refer to the exhibit. A web server in the DMZ is being mapped to a public address through DNAT.

Which Security policy rule will allow traffic to flow to the web server?
The firewall sends employees an application block page when they try to access Youtube.
Which Security policy rule is blocking the youtube application?
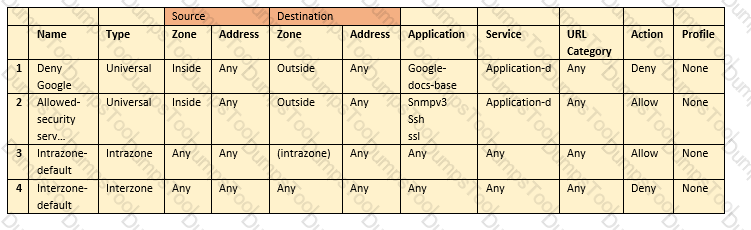
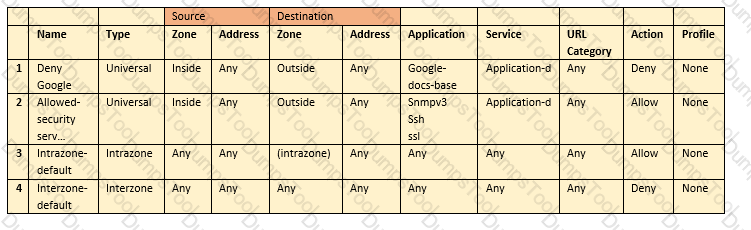
Which type security policy rule would match traffic flowing between the inside zone and outside zone within the inside zone and within the outside zone?
Which two types of profiles are needed to create an authentication sequence? (Choose two.)
Where within the URL Filtering security profile must a user configure the action to prevent credential submissions?
Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choices to block the sameURL then which choice would be the last to block access to the URL?
Which Security profile would you apply to identify infected hosts on the protected network using DNS traffic?
Which firewall feature do you need to configure to query Palo Alto Networks service updates over a data-plane interface instead of the management interface?
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
How does the Policy Optimizer policy view differ from the Security policy view?
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
Files are sent to the WildFire cloud service via the WildFire Analysis Profile. How are these files used?
What are three Palo Alto Networks best practices when implementing the DNS Security Service? (Choose three.)
Choose the option that correctly completes this statement. A Security Profile can block or allow traffic ____________.
A network administrator is required to use a dynamic routing protocol for network connectivity.
Which three dynamic routing protocols are supported by the NGFW Virtual Router for this purpose? (Choose three.)
An administrator manages a network with 300 addresses that require translation. The administrator configured NAT with an address pool of 240 addresses and found that connections from addresses that needed new translations were being dropped.
Which type of NAT was configured?
A systems administrator momentarily loses track of which is the test environment firewall and which is the production firewall. The administrator makes changes to the candidate configuration of the production firewall, but does not commit the changes. In addition, the configuration was not saved prior to
making the changes.
Which action will allow the administrator to undo the changes?
Which Palo Alto networks security operating platform service protects cloud-based application such as Dropbox and salesforce by monitoring permissions and shared and scanning files for Sensitive information?
Which two security profile types can be attached to a security policy? (Choose two.)
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
Which service protects cloud-based applications such as Dropbox and Salesforce by administering permissions and scanning files for sensitive information?
Which license must an administrator acquire prior to downloading Antivirus updates for use with the firewall?
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
In which section of the PAN-OS GUI does an administrator configure URL Filtering profiles?
Which type of security policy rule will match traffic that flows between the Outside zone and inside zone, but would not match traffic that flows within the zones?
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
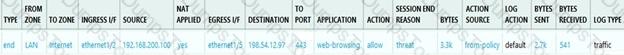
An administrator is reviewing the Security policy rules shown in the screenshot below.
Which statement is correct about the information displayed?

An administrator creates a new Security policy rule to allow DNS traffic from the LAN to the DMZ zones. The administrator does not change the rule type from its default value.
What type of Security policy rule is created?
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?
Which Security policy action will message a user's browser thai their web session has been terminated?
In order to attach an Antivirus, Anti-Spyware and Vulnerability Protection security profile to your Security Policy rules, which setting must be selected?
What are three configurable interface types for a data-plane ethernet interface? (Choose three.)
You receive notification about new malware that is being used to attack hosts The malware exploits a software bug in a common application
Which Security Profile detects and blocks access to this threat after you update the firewall's threat signature database?
Which CLI command will help confirm if FQDN objects are resolved in the event there is a shadow rule?
By default, what is the maximum number of templates that can be added to a template stack?
The Palo Alto Networks NGFW was configured with a single virtual router named VR-1 What changes are required on VR-1 to route traffic between two interfaces on the NGFW?
What are three valid information sources that can be used when tagging users to dynamic user groups? (Choose three.)
Which path in PAN-OS 11.x would you follow to see how new and modified App-IDs impact a Security policy?
Which System log severity level would be displayed as a result of a user password change?
The administrator profile "SYS01 Admin" is configured with authentication profile "Authentication Sequence SYS01," and the authentication sequence SYS01 has a profile list with four authentication profiles:
• Auth Profile LDAP
• Auth Profile Radius
• Auth Profile Local
• Auth Profile TACACS
After a network outage, the LDAP server is no longer reachable. The RADIUS server is still reachable but has lost the "SYS01 Admin" username and password.
What is the "SYS01 Admin" login capability after the outage?
According to the best practices for mission critical devices, what is the recommended interval for antivirus updates?
At which point in the app-ID update process can you determine if an existing policy rule is affected by an app-ID update?
The compliance officer requests that all evasive applications need to be blocked on all perimeter firewalls out to the internet The firewall is configured with two zones;
1. trust for internal networks
2. untrust to the internet
Based on the capabilities of the Palo Alto Networks NGFW, what are two ways to configure a security policy using App-ID to comply with this request? (Choose two )
In which three places on the PAN-OS interface can the application characteristics be found? (Choose three.)
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?
In a File Blocking profile, which two actions should be taken to allow file types that support critical apps? (Choose two.)
Which Security policy set should be used to ensure that a policy is applied first?
Which objects would be useful for combining several services that are often defined together?
After making multiple changes to the candidate configuration of a firewall, the administrator would like to start over with a candidate configuration that matches the running configuration.
Which command in Device > Setup > Operations would provide the most operationally efficient way to accomplish this?
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
What is considered best practice with regards to committing configuration changes?
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
Which file is used to save the running configuration with a Palo Alto Networks firewall?
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?
Which three types of Source NAT are available to users inside a NGFW? (Choose three.)
What is a recommended consideration when deploying content updates to the firewall from Panorama?
Which two statements are true for the DNS security service introduced in PAN-OS version 10.0?
When HTTPS for management and GlobalProtect are enabled on the same interface, which TCP port is used for management access?
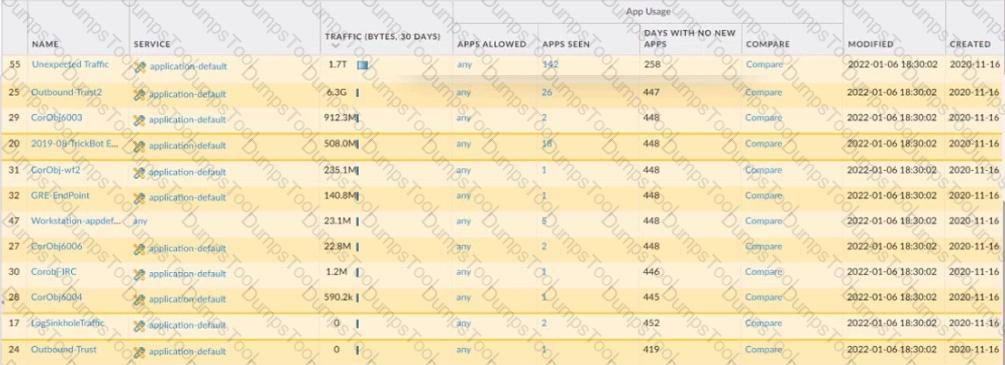
An administrator is updating Security policy to align with best practices.
Which Policy Optimizer feature is shown in the screenshot below?
Assume a custom URL Category Object of "NO-FILES" has been created to identify a specific website
How can file uploading/downloading be restricted for the website while permitting general browsing access to that website?
Which three types of entries can be excluded from an external dynamic list (EDL)? (Choose three.)
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?
What are the requirements for using Palo Alto Networks EDL Hosting Sen/ice?
What can be achieved by disabling the Share Unused Address and Service Objects with Devices setting on Panorama?
An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
Which interface type requires no routing or switching but applies Security or NAT policy rules before passing allowed traffic?
Which protocol used to map username to user groups when user-ID is configured?
The PowerBall Lottery has reached an unusually high value this week. Your company has decided to raise morale by allowing employees to access the PowerBall Lottery website (www.powerball.com) for just this week. However, the company does not want employees to access any other websites also listed in the URL filtering “gambling” category.
Which method allows the employees to access the PowerBall Lottery website but without unblocking access to the “gambling” URL category?
Which URL profiling action does not generate a log entry when a user attempts to access that URL?
What is the minimum timeframe that can be set on the firewall to check for new WildFire signatures?
Which two components are utilized within the Single-Pass Parallel Processing architecture on a Palo Alto Networks Firewall? (Choose two.)
An administrator is troubleshooting an issue with traffic that matches the intrazone-default rule, which is set to default configuration.
What should the administrator do?
Based on the security policy rules shown, ssh will be allowed on which port?
Which type of administrative role must you assign to a firewall administrator account, if the account must include a custom set of firewall permissions?
Which two features can be used to tag a user name so that it is included in a dynamic user group? (Choose two)
An administrator needs to add capability to perform real-time signature lookups to block or sinkhole all known malware domains.
Which type of single unified engine will get this result?
Given the screenshot, what are two correct statements about the logged traffic? (Choose two.)
Which action would an administrator take to ensure that a service object will be available only to the selected device group?
A website is unexpectedly allowed due to miscategorization.
What are two way-s to resolve this issue for a proper response? (Choose two.)
Which action can be set in a URL Filtering Security profile to provide users temporary access to all websites in a given category using a provided password?
Which Security profile should be applied in order to protect against illegal code execution?
An administrator needs to create a Security policy rule that matches DNS traffic within the LAN zone, and also needs to match DNS traffic within the DMZ zone The administrator does not want to allow traffic between the DMZ and LAN zones.
Which Security policy rule type should they use?