An administrator is trying to correct high cluster IOPs and Cluster Controller Latency. Networking is the suspected issue.
Which networking parameters should be configured in the Nutanix cluster?
After deployment of a Nutanix cluster, a customer has requested to validate the peak performance of the cluster.
Which tool can a consultant use to satisfy this request?
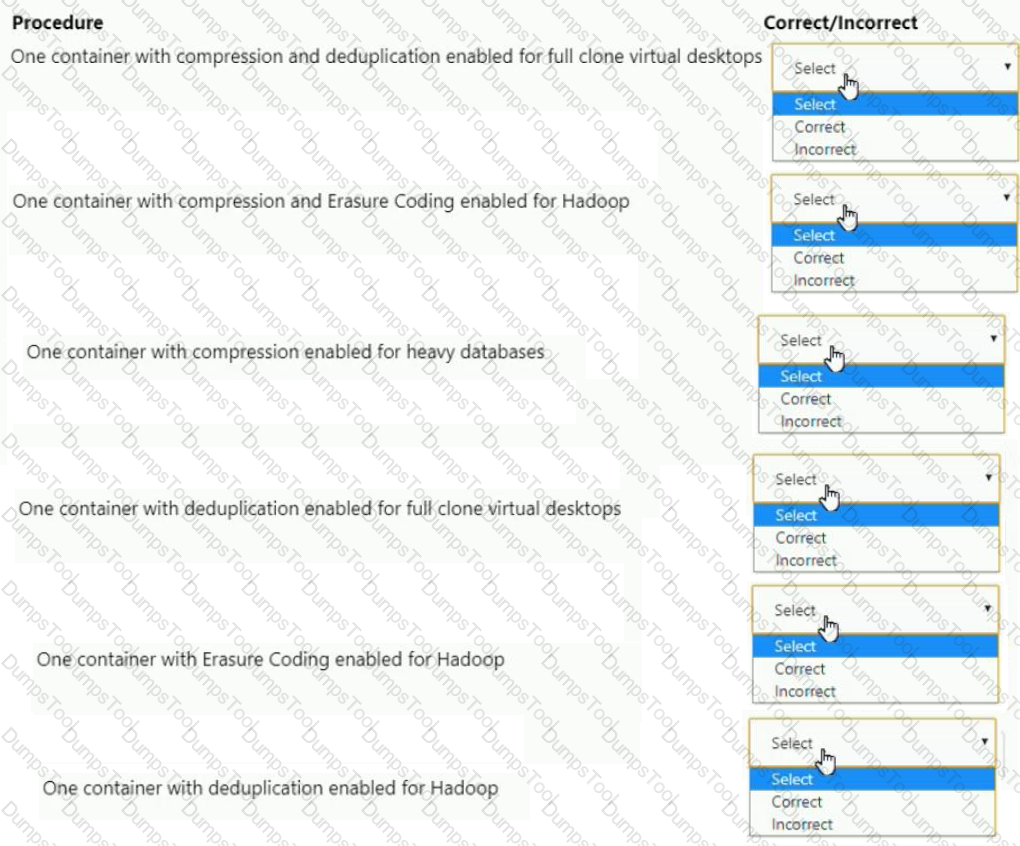
An administrator is configuring an All Flash cluster to support the following workloads:
• Full clone virtual desktops
• Hadoop
• Write heavy databases
Which three correct configuration options should the administrator use to meet the item requirements? (Choose three.)
For each procedure, indicate whether it is a correct or incorrect procedure that must be configured to meet the item requirements using the drop-down option.
Based on customer requirements, a consultant conducted an AHV cluster deployment. Each node is configured with four NICs.
Which two components should the consultant manually update in the As-Built Guide? (Choose two.)
An administrator configures authentication in Prism Central (PC) for the NTNX-Admins group. Users report that they are unable to log in. The administrator confirms that the Active Directory (AD) settings in PC are correct.
Which condition could result in this behavior?
While creating an image placement policy on the organizations AOS 5.15-based Nutanix cluster, the administrator wants to ensure there are no restrictions on using the selected images on clusters outside of the identified set.
What type of Policy Enforcement must the administrator choose?
A consultant is preparing to foundation over a customer network that has the following criteria:
* VLAN segmented network
* VLAN tags on the nodes must be imaged prior to starting the foundation process.
For each node, the consultant has done the following:
* Connected to the Network Crash Cart of the Node
* Logged in using “root” credentials
What should the consultant do next?
A customer has a four-node cluster and is using Volume Groups to provide storage services to a SQL cluster.
In the event of a CVM failure in the cluster, what is the expected IO path of the volume group’s iSCSI targets?
In preparing to install a new cluster for a company, a consultant needs to complete an installation worksheet.
Which values must be documented prior to initial base system setup?
A consultant is deploying a new Nutanix cluster. The nodes have the following network interfaces.
◦ 2x 10G NICS
◦ 2x 25G NICS
The consultant is using the default virtual switch configurations for AHV. After creating 10 VMs, the consultant observes inconsistent network speeds from the VMs on the AHV host.
What should the consultant do to resolve this issue?
An administrator of a Nutanix Enterprise Cloud has microsegmentation enabled and a firewall VM installed. The security team notifies the administrator that one of the VMs hosted in the environment has been exhibiting suspect network activity. The administrator wants to isolate the VM from the production network, but must still be able to access it to perform diagnostics.
What should the administrator do to meet the requirement?
A consultant has deployed a Nutanix cluster with AOS 5.10.x, then discovers the customer’s environment is running on AOS 5.6.x. The consultant decides to re-image the cluster using the foundation Java applet. During the Foundation discovery, all cluster nodes display a status of Unavailable.
What should the consultant do to resolve the issue?
A customer has the following requirement for a Nutanix cluster:
How should the customer optimize networking?
An administrator needs to replace the self-signed certificate on a cluster. Which two requirements must be met as part of the process? (Choose two.)
An administrator manages the following two Nutanix AOS 5.15 cluster environment:
• Corp-cluster-01
• Corp-cluster-02
The VM images must be available only on Corp-cluster-01, but cannot be checked out to cluster Corp-cluster-02. The images also cannot be checked out to any other clusters that are registered with Prism Central in the future.
Which two configuration settings must the administrator choose when creating the image placement policy that satisfies the stated requirements? (Choose two.)
A VM is exhibiting one or more of the following baseline values based on the past 30 days:
• CPU usage < 20%
• CPU ready time < 5%
• Memory usage < 50% (moderately) or < 20% (severely)
• Memory swap rate = 0 Kbps
Which type of VM is being described?
A consultant is showing the Prism Element Web Console to a customer and wants to check that cluster health is OK. During validation, the Health menu raises critical alerts about components using default passwords.
The cluster is based on ESXi as hypervisor, where Prism Central and Nutanix Files are deployed. Passwords have already been changed for a few components, but some of them have been left by default.
How can the consultant check and handle that situation?
An administrator needs to replace an aging SAN and move to a hyper-converged infrastructure. The existing environment consists of the following hosts that are connected to the SAN:
• 5xAIX hosts
• 3x Hyper-V hosts
• 9xESXi hosts
• 2x physical SQL Clusters (Windows Server 2012R2 hosts)
After deploying a Nutanix AHV cluster, which two actions should the administrator take to meet the requirements? (Choose two.)
Refer to the exhibit.
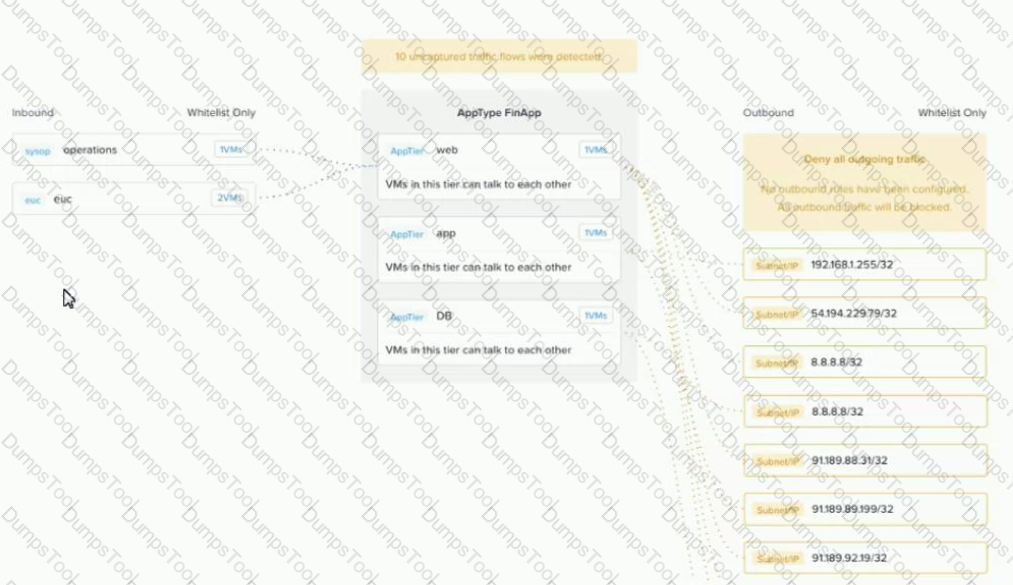
An administrator creates a security policy that isolates their financial application from accessing the Internet When viewing the policy in Prism Central, several connections from the application are outbound to the Internet.
What is causing this issue with the policy?
A consultant is setting up a new install of Nutanix Files for a customer, but receives this error when attempting to join the customer's Active Directory domain:
File Server
The consultant has already verified the domain credentials provided by the customer are valid and have the correct permissions.
What is the most likely cause in this scenario for a domain-join failure when setting up Nutanix Files?
A consultant is planning to use a flat switch for installation.
What is the network requirement for Foundation VM, CVM, Hypervisor, and IPMI
An administrator knows that the disks in a cluster are out of date and a new firmware is available. For security reasons, these clusters do not have access to the Internet.
Which two steps must be completed to update the firmware? (Choose two.)
An administrator deletes a large amount of data from a Volume Group presented to a Linux VM. The administrator notices that the deleted data has not been reclaimed as usable storage.
What action should be taken to reclaim the storage capacity?
A consultant is unable to ping the CVM from the hypervisor using the external interface. The customer's network is configured with the 10.3.12.0/24 subnet without VLAN tagging. The CVM and hypervisor are using the same address space.
What is causing this issue?
An administrator is using Nutanix Move to migrate a Windows VM from ESXi to AHV. Automated guest preparation is failing with an error:
Account has UAC enabled error
The administrator is using the local built-in administrator account for the Windows VM Admin approval mode must remain enabled.
What should the administrator do to continue with the migration with Nutanix Move?
A consultant will be doing an install for an enterprise customer. The consultant has racked up, powered on, and connected their Foundation software to the new nodes. The Foundation VM is not discovering the hardware.
What should the consultant do to resolve this issue?
The installation process stops before imaging any of the nodes and an error message is displayed notifying the IPMI IP address is unreachable.
What should consultant do to fix the issue?
A consultant is performing a Nutanix Cluster installation on Dell XC Core hardware. The consultant decides to use Foundation Portable for Mac to perform the installation. When the consultant arrives onsite, Foundation Portable is unable to locate the new nodes.
Which log should the consultant check to troubleshoot this issue?
To ensure VM availability when a service outage has occurred, a customer has requested that automatic VM failovers must occur as part of the DR strategy for their environment.
Which failover operation is within an Unplanned Failover option?
An administrator needs to maximize storage potential in a six-node cluster. The container is configured with the following:
What should the administrator configure to increase space savings?
A customer has a mail server and needs Nutanix to send email notifications about errors that might occur in Prism. The following information is included under SMTP Server Settings
◦IP Address of mail server
◦Port Security Mode
◦From email address
What should the consultant set up before arriving onsite?
An administrator is managing multiple Windows and Linux VMs connected to Nutanix Volumes. The Linux VMs are experiencing intermittent connectivity issues. The Windows VMs do not experience the same issue.
Which option should the administrator use to resolve this issue?
A customer has a G6 AHV cluster with 4x10GbE NICs on each node and the following configuration:
* Networking is set to default
* Only two NICs are connected
The customer receives the following critical message:
The NIC is disconnected from the switch, or the switchport is failing.
What should the consultant verify to resolve the issue?
As a part of a cluster deployment test plan, a customer asks the consultant for some additional performance and resiliency tests.
How should the consultant best satisfy this request?
A consultant completes a new cluster installation and tries to update the firmware using LCM. The update fails with the following.
operation failed, Reason: Failed to run LCM operation, error: ReadError('not a grip file',).
Which log should the consultant view to get more info?
At which prompt should a consultant execute the command nanage_ovs —bridge_nawe brO show_uplinks in a Nutanix cluster?
In a Nutanix cluster, a Protection Domain contains 50 entities that are replicated to a remote Single Node Replication Target.
The current schedule configuration is as follows:
• Repeat every 6 hours
• Local Retention Policy 1
• Remote Retention Policy 8
• Starting time 12 am
At 8 am on Monday, the administrator discovers that a protected VM is corrupted. The latest good state was Sunday 2 pm. The administrator needs to maintain current protection.
Which strategy should the administrator use to meet these requirements?
While trying to upgrade AOS in a cluster, a consultant receives a warning message that there are two powered-on VMs that need to be powered off for the upgrade to proceed.
What would cause this warning to be issued?
During the knowledge transfer on Prism GUI, a customer asked about AHV best practices for VM High Availability on a five-node cluster and the safest configuration. The consultant informed the customer that best practices dictate that all storage containers are configured with a replication factor of 3.
What will be the behavior if the non-default Guarantee mode is selected on Prism with two AHV host failures?
A consultant successfully installs the Foundation VM on a laptop and needs to ensure the VM can communicate externally.
Which two configuration changes should the consultant make next? (Choose two.)
An administrator needs to deploy an application with a large amount of data connected via Nutanix Volumes.
Which two actions should the administrator take when designing the Volume Group? (Choose two.)
A customer recently set up Async Replication between Site A and Site B. The customer wants to conduct a planned failover and clicks Activate on Site B.
The customer then runs the following command on Site A:
ncli pd deactivate_and__destroy_vms name=
What does this do to the customer environment?
During the cluster deployment, a consultant conducts operational tests on a vCenter-managed ESXi hypervisor.
As a part of tests, vCenter must place the host into maintenance mode, however, the task is stuck and the CVM is not shutting down automatically.
What should the consultant do to resolve the issue?
A consultant is using a customer’s switch for installation. Although the 10GbE ports for each of the hosts are connected to the switch, the nodes fail to be discovered.
What is causing the issue?
During Foundation using a customer-provided network switch, a consultant is facing time-out issues.
What action should the consultant take to resolve this issue?
As a consultant concludes the project for deploying a new cluster, the customer expresses plans to repeat the process in-house for one of the company's dark site locations.
What three items can the consultant deliver in closing to help ensure customer's success in deploying and supporting Nutanix clusters?
A consultant deploys a new ESXi-based Nutanix cluster and migrates a sphere deployment to the cluster, After completing the deployment, the customer states they are experiencing VM performance issues.
Upon observing logs and performance data, the consultant identified the following symptoms.
◦ Excessive read/write 1/Os on CVMs
◦ Excessive Motion of VMs
What is causing this issue?
A VM does not have enough resources for the demand, which leads to performance bottlenecks. The VM is exhibiting one or more of following baseline values, based on the past 30 days:
• CPU usage > 90% (moderate), 95% (high)
• CPU ready time > 5%, 10%
• Memory usage > 90%, 95%
• Memory swap rate > 0 Kbps (no moderate value)
Which type of VM is being described?
A customer wants to validate the Microsoft SQL workload performance for a CRM application before migration to the new Nutanix cluster.
Which activity must the consultant add as part of the test plan to fulfill this requirement?
An administrator is deploying a three-tier application on a Nutanix Enterprise Cloud consisting of web, application, and database VMs. Traffic between the servers must be limited to specific services/ports. There is an application layer firewall VM deployed on one host in the cluster.
In which way should the administrator meet this requirement?
Refer to the exhibit.
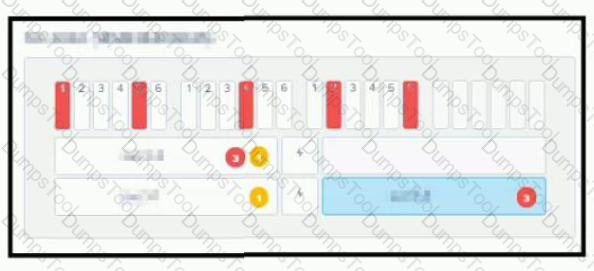
An administrator logs in to Prism and sees the status shown in the exhibit within the Hardware Diagram section.
What should the administrator do?
An administrator is implementing a VDI solution. The workload will be a series of persistent desktops in a dedicated storage container within a four-node cluster. Storage optimizations should be set on the dedicated storage container to give optimal performance including during a node failure event.
Which storage optimizations should the administrator set to meet the requirements?
Which subnet should a consultant be aware is reserved for internal connectivity within a Nutanix cluster?
After the successful creation of clusters, the customer wants to ensure that alerts are sent automatically to Nutanix support.
Which Nutanix feature should the consultant ensure is enabled?
An organization is running a Nutanix Cluster based on AOS 5.10.x and VMware vSphere 6.7. Currently, the CVM network is segmented and Storage only nodes not present.
A new security project based on NSX is coming. VMware Distributed Virtual Switches are required. The administrator needs to prepare the environment for the new project.
Which step should the administrator use to initiate the project?
An administrator is configuring software only. Data-at-Rest Encryption on their Nutanix cluster. They are planning to deploy a third-party key management server (KMS).
Where should this server be hosted?
A consultant is onsite with a customer to expand an existing eight-node cluster with four new GPU nodes. The consultant plugs the nodes into the network switch and follows the procedure to expand the cluster in Prism Element, but the new nodes cannot be found.
Which issue is preventing the new nodes from being discovered?
An administrator needs to initiate a new VDI project within a couple of months. Prism Central reports there are no storage resources to accommodate such workloads.
The administrator sees many powered-off VMs and has the authority to delete test VMs powered off at least for 30 days. Test VMs belong to the Test category.
Using Prism Central, which steps are required to identify the correct VMs to be deleted?
During a technical call with a customer, it is identified that this installation will be software only on Dell servers. The out-of-band management interfaces will not be given IP addresses until the consultant is onsite.
Which Foundation method should be used for this type of installation?
An administrator recently added VLAN 205 CRM in Prism Element. The workloads attached to the associated NICs are unable to establish network connectivity.
Which Layer 2 protocol allows the administrator to troubleshoot this issue from Prism Element?
A consultant creates three storage containers (container-1, container-2, container-3). The customer requires that only container-1, which will be utilized as an NFS datastore, be presented to external hosts.
However, users are able to mount all three containers.
What is causing this problem?
A customer needs a DR solution designed around the following requirements:
• There are 8 ms of latency between Sites A and B
• The administrator needs the shortest RPO/RTO possible
• Application consistent snapshots are required
• Use of Nutanix VSS
Which Data Protection Method should be used?
What is the default password shipped on new NX hardware from the factory for the ADMIN user on IPMI?
Refer to the exhibit.
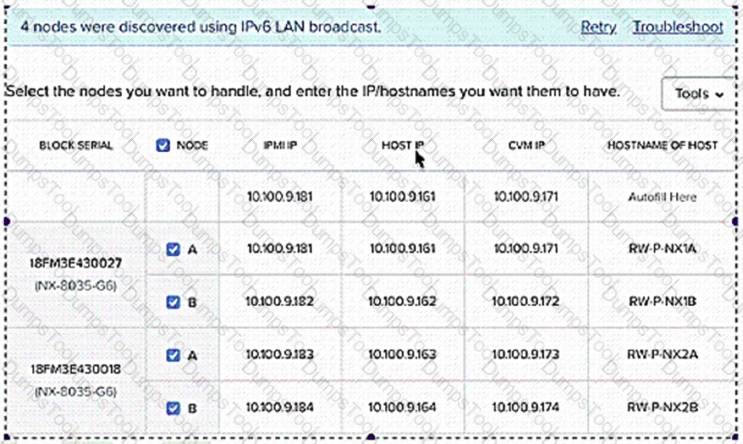
A system administrator is using Range-Autofill tool to assign IP addresses to setup a multi-block cluster based on the following configuration:
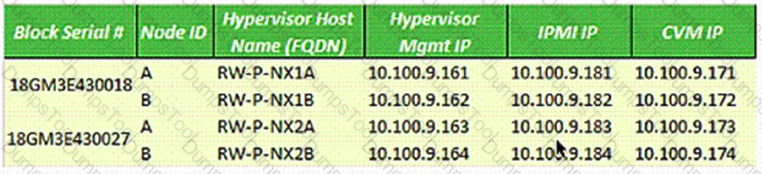
Which additional changes must be made during the Foundation process to configure the cluster correctly?
A consultant is working with a customer on a new cluster deployment.
While reviewing the customer questionnaire, the consultant notices that the customer has documented their DNS servers as follows:
•CompanyDNSI 192.168.5.10
•CompanyDNS2 192.1685.20
What should the consultant consider regarding this deployment?
A consultant configures an ESXi cluster which will utilize a vSphere Distributed Switch (vDS). The consultant has just migrated the first host to the dvSwitch when several alerts appear within Prism Element regarding Host-to-CVM connectivity.
What is causing these alerts?
A customer wants to use NIC teaming on an ESXi host using a vSphere Standard Switch configured with the Route based on physical NIC load load balancing option. The customer does not see the option when editing the Teaming and Failover settings for the switch.
How should the consultant resolve this issue?
After the migration, some SQL queries take longer to execute than prior to migration.
The following SQL best practices were applied while creating the SQL VM on Nutanix:
•8 vDisks per SQL server VM
•Database and Log files on separate vDisk
•2 TempDB database drives and 1 TempDB log drive
What should the administrator to do improve the SQL Server performance?
A customer’s security team has a policy prohibiting a consultant’s laptop from connecting within the corporate datacenter.
In which two ways should the consultant complete the customer deployment on the factory-prepared nodes? (Choose two.)
Refer to the exhibit.
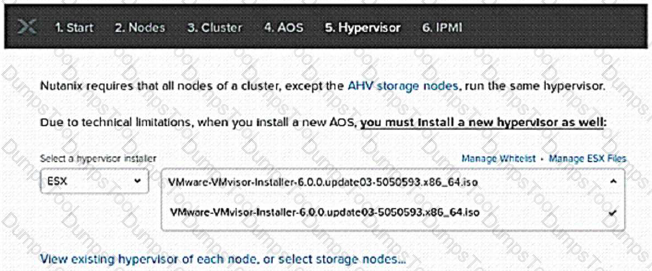
A consultant is installing AOS 5.10 and ESXi 6.5 on three nodes. During the Foundation process, ESXi 6.5 is not available as one of the choices for hypervisor.
Which solution should the consultant use?
For a new AHV cluster installation, a customer has 20 NX-8155 nodes with quad port NICs. The customer wants to meet the following guidelines:
◦Take advantage of all available 10G links
◦Achieve maximum throughput per VM
◦Use of redundant ToR switches
◦Fastest reconvergence during link failure
How should the load balancing be configured on the host?
A consultant configures a Nutanix cluster and integrates the hosts into vCenter using VMware best practices. The customer has requested that the Nutanix cluster only have a single datastore.
Upon configuring the cluster per the customer requirements, vCenter displays an alert regarding the heartbeat datastore. The consultant adds the das.ignoreInsufficientHbDatastore value = true rule. The container can be seen from each host, but the alert remains active.
What should the consultant do to resolve this issue?
An administrator needs to configure snapshots for DR scenarios. The databases get refreshed on Friday nights regularly. The search service application re-indexes the new application on Saturday nights regularly. The remaining front-end and middle tier VMs are static but do get minor version updates weekly.
The administrator needs to have 2 weeks of daily snapshots for all the VMs in an app group and 2 weeks application consist local snapshots only on Fridays, Saturdays and Sundays on the same group of VMs.
Which two options should the administrator use to configure snapshots?
A consultant creates a Windows VM after installing a new Nutanix cluster running AHV. The consultant has statically assigned an IP address to the VM but it is unable to communicate on the network.
Which action should the consultant take to resolve this issue?
An existing Nutanix customer has several clusters in production and is adding a new cluster. The customer wants to create an AHV cluster that has already been racked and powered on remotely, with the factory image, using Prism Central.
Which step should the consultant take next?
A consultant installs a new AHV cluster and moves the cluster into the customer's environment. Alter the move, the consultants notice that traffic is not being balanced across the physical NICs. The ToR switches have been configured with LACP.
Within Prism Element, which AHV network option should be set to resolve the issue?
Refer to the exhibit.

A Microsoft SQL 2016 deployment is shown in the exhibit. The administrator receives user reports that database queries take too long to return.
Which optimization should be made to this configuration to improve performance?
An administrator is monitoring the Nutanix v5.15-based AOS cluster performance logs and notices that a SQL server VM is greatly exceeding its intended maximum IOPS. The administrator has confirmed that a QoS policy was previously created for the group of VMs this server is a member of.
What are two reasons that this VM would exceed its maximum configured IOPS from the QoS Policy? (Choose two.)
When utilizing the Nutanix cluster As Built Document generator, which two configuration elements should a consultant provide when running the run_as_built.exe command? (Choose two.)
After uploading a hypervisor ISO during the Foundation process, a consultant sees a message that the MD5 sum for the hypervisor is not found in the Whitelist file.
Which step should the consultant take next to resolve this issue?
A customer has a Nutanix cluster with 10Gb connectivity via switch fabric extenders. The administrator receives NCC health check errors of latency greater than 200ms.
Which action should the administrator take to resolve the NCC errors?
In which two ways can the IPMI address be set on a Nutanix hardware installation? (Choose two.)