An administrator needs to power down an AHV node in order to replace a failed DIMM?
Which step should the administrator take after placing the node into maintenance mode?
A Nutanix administrator needs to replace a self-signed SSL certificate with a CA generated certificate in Prism.
Which three files are required to install the CA generated certificate in Prism? (Choose three)
An administrator needs to bring down a host in a Nutanix Cluster for maintenance reasons. The administrator puts the host in maintenance mode.
What should the administrator do to perform an orderly shutdown of the CVM?
An administrator is configuring data protection and DR for a multi-tier application. All VMs must be protected at the same time.
What must the administrator do to meet this requirement?
An administrator has set up a local web server accessible to the Nutanix clusters.
Which two steps are required to set up LCM for an environment without Internet access? (Choose two.)
An administrator adds a node with older generation processors to an existing AHV cluster with newer generation processors. What is the effect on live migration?
Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?
AHV IPAM assigns an IP address from the address pool when creating a managed VM NIC.
At which two instances does the address release back to the pool? (Choose two)
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic regardless of direction, between two groups of VMs identified by their category.
Which policy should be used to meet this requirement?
A cluster has RF2. The cluster loses two drives on different nodes in the same storage tier.
What is the effect on the replicas of the VMs?
The administrator wants a container to be displayed and limited to 1TB in the hypervisor.
What advanced container setting must the administrator set?
Which two capabilities does IPAM provide in a Nutanix networking configuration? (Choose two.)
An administrator is reviewing performance of a core banking system that routinely has 20,000 concurrent users. During, business hours, the CPU on the applications servers runs at close to 100%. The administrator needs to determine if there is a performance issue specific to the app servers, the database servers, or all servers on the cluster.
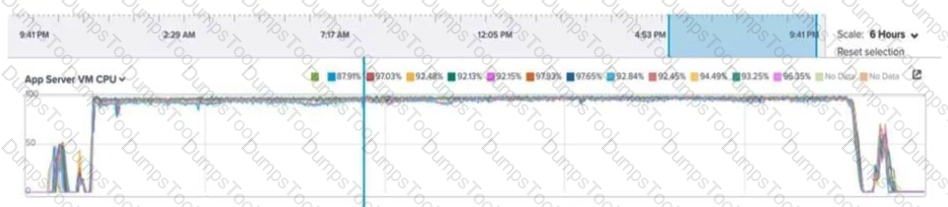
Which metrics should the administrator review in Prism Analysis Graphs?
An Administrator is working on a one-node ROBO cluster configurations
Which statement is true for this configuration?
Which two private key types are supported by the Nutanix SSL certificate implementation? (Choose two.)
Refer to the exhibit.
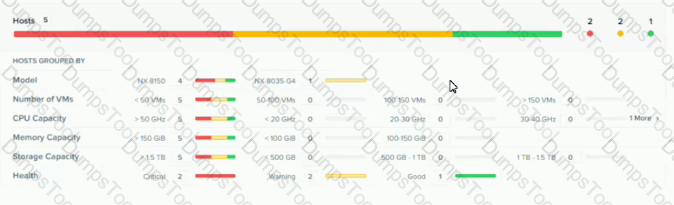
System Non-Root Partition Usage shows a warning or critical alert The administrator needs to change the frequency of checks and alerts to respond more quickly.
Where in Prism Element should the administrator change the frequency of checks and alerts?
Which two methods are available when migrating a VM from a legacy 3-tier solution using VMware ESXi to AHV? (Choose two.)
An administrator wants to be able to manage their application from prism central.
Which feature must the administrator enable to allow for application management?
An Administrator wants to present storage to an external non-Nutanix host via iSCSI.
Which construct should the administrator in configure to create the iSCSI volume?
An administrator wants to configure key based SSH access for an AOS 5.5 Implementation
Which three components can be secured using this method?
An administrator is implementing a VDI solution. The workload will be a series of persistent desktops in a dedicated storage container within a four-node cluster Storage optimizations should be set on the dedicated storage container to give optimal performance including during a node failure event
Which storage optimizations should the administrator set to meet the requirements?
What is the maximum number of tested and supported vDisks (including snapshots) that is a Nutanix cluster can maintain?
An administrator has just executed a maintenance window for some applications running on their nutanix cluster. After completing the maintenance, they want to assess the health of the cluster and make sure that there is no impact during the maintenance.
Which three dashboards in prism will assist the administrator in making this determination? (Choose Three)
An Engineer logs into a CVM to troubleshoot connectivity loss between two CVMs and find the following interfaces subnets and WLANs configured.
-eth0 – VLAN10-10.1.10.0/24
eth01–No VLAN-192.168.5.0/24
eth2 – LAN20-10.1.20.0/24
Which two Nutanix networking features are being utilized? (Choose two)
An administrator has configured a VM with affinity to a single host. Which AOS feature will this impact?
An administrator wants to secure an application running on an AHV cluster by limiting incoming and outgoing traffic destinations. The administrator creates a security policy for the application.
What is the next step?
When installing Nutanix Guest Tools (NGT) on an ESXi-hosted VM, which port should be enabled on the VM to allow communication with the NGT-Controller VM service?
A customer creates a new AHV network within the cluster to provide VM connectivity for VLAN1001. Network traffic to VMs connected to it is inconsistent.
What should be validated as part of the customer´s troubleshooting process?
Which options are available when a live migration is performed on a VM in an AOS 5.5 implementation?
An administrator is preparing to migrate VMs from a legacy ESXi cluster to a new AHV cluster.
Which action must be the administrator perform on the AHV cluster to migrate VM data?
In a managed network, in which scenario will AHV use the last network IP address for the DHCP server?
An administrator has a 4-node Nutanix cluster running on Hyper-V. The administrator create a new storage container and makes that available to all hosts.
Which storage protocol should be administrator use for the hosts to gain access to the storage container?