You implement the planned changes for SSPR.
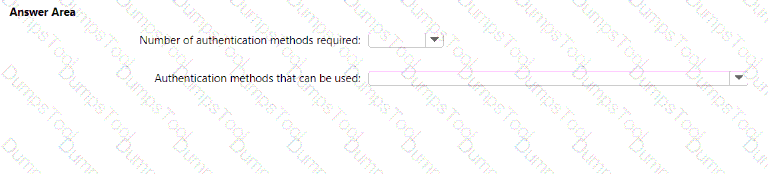
What occurs when User3 attempts to use SSPR? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to locate licenses to the A. Datum users. The solution must need the technical requirements.
Which type of object should you create?
You need to meet the planned changes and technical requirements for App1.
What should you implement?
You need to sync the ADatum users. The solution must meet the technical requirements.
What should you do?
You create a Log Analytics workspace.
You need to implement the technical requirements for auditing.
What should you configure in Azure AD?
You need to resolve the recent security incident issues.
What should you configure for each incident? To answer, drag the appropriate policy types to the correct issues. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You need to implement the planned changes for Package1. Which users can create and manage the access review?
You need implement the planned changes for application access to organizational data. What should you configure?
You need to resolve the issue of the guest user invitations. What should you do for the Azure AD tenant?
You have an Azure Ad tenant that contains the users show in the following table.
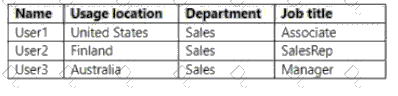
You create a dynamic user group and configure the following rule syntax.

Which users will be added to the group?
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users.
From the Groups blade in the Azure Active Directory admin center, you assign Microsoft 365 Enterprise E5 licenses to the users.
You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort.
What should you use?
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com. The company has a business partner named Fabrikam, Inc.
Fabrikam uses Azure AD and has two verified domain names of fabrikam.com and litwareinc.com. Both domain names are used for Fabrikam email addresses.
You plan to create an access package named package1 that will be accessible only to the users at Fabrikam.
You create a connected organization for Fabrikam.
You need to ensure that the package1 will be accessible only to users who have fabrikam.com email addresses.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription.
You purchase the app governance add-on license.
You need to enable app governance integration.
Which portal should you use?
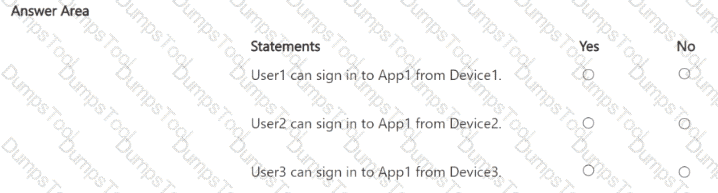
You have a Microsoft 365 subscription that contains three users named User1, User2, and User3 and an enterprise app named Appl. The subscription contains the devices shown in the following table.
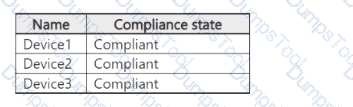
The subscription contains the groups shown in the following table.
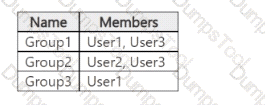
You create two Conditional Access policies that have the following settings:
• Name: Policy1
• Users:
o Include: Group1
o Exclude: Group3
• Target resources:
o Include: All resources
• Access controls: Block access
• Name: Policy2
• Users:
o Include: Group2
• Target resources:
o Include: App1
• Access controls:
° Grant access: Require device to be marked as compliant
For each of the following statements select Yes if the statement is true Otherwise select No.
NOTE: Each correct selection is worth one point.
You have an Azure AD tenant that contains an access package named Package1 and a user named User1. Package1 is configured as shown in the following exhibit.
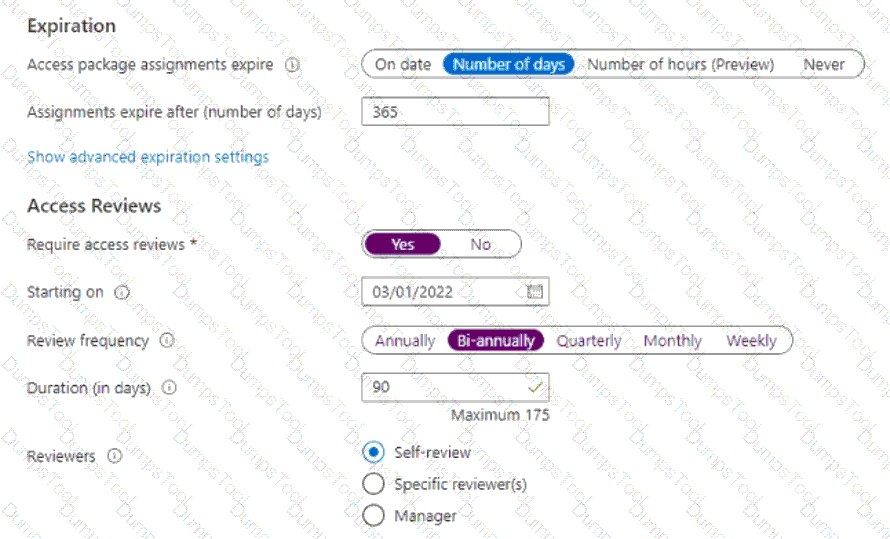
You need to ensure that User1 can modify the review frequency of Package1. The solution must use the principle of least privilege.
Which role should you assign to User1?
You have a Microsoft 365 tenant.
All users have mobile phones and laptops.
The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity. While working from the remote locations, the users connect their laptop to a wired network that has internet access.
You plan to implement multi-factor authentication (MFA).
Which MFA authentication method can the users use from the remote location?
You configure Azure Active Directory (Azure AD) Password Protection as shown in the exhibit. (Click theExhibittab.)
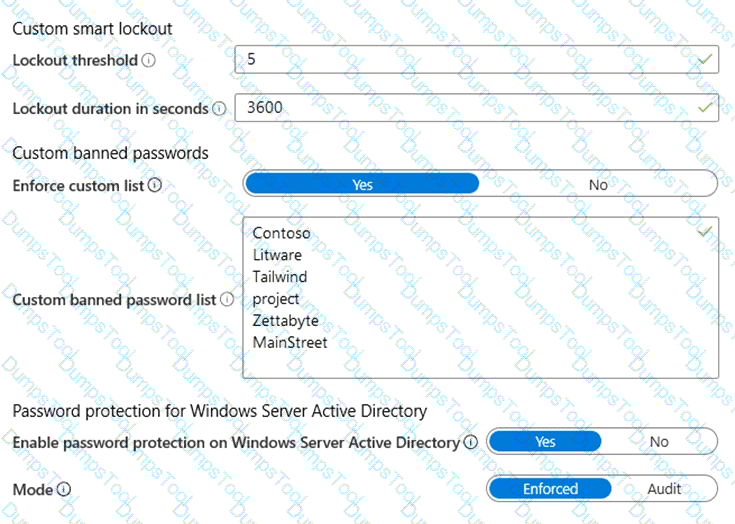
You are evaluating the following passwords:
Pr0jectlitw@re
T@ilw1nd
C0nt0s0
Which passwords will be blocked?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) whenaccessing Microsoft 365 services.
Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request.
You need to block the users automatically when they report an MFA request that they did not initiate.
Solution: From the Azure portal, you configure the Notifications settings for multi-factor authentication (MFA).
Does this meet the goal?
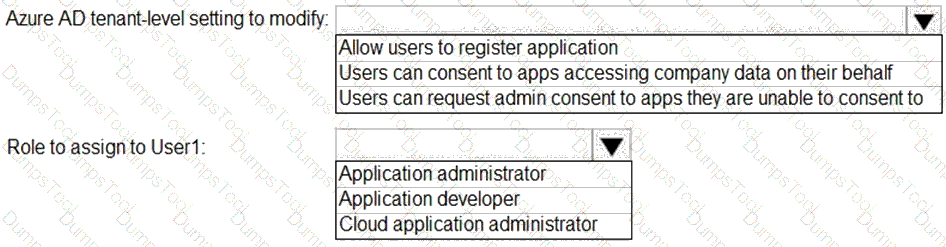
You need to configure app registration in Azure AD to meet the delegation requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
You have an Azure subscription named Sub1 that contains a virtual machine named VM1.
You need to enable Microsoft Entra login for VM1 and configure VM1 to access the resources in Sub1.
Which type of identity should you assign to VM1?
You need to configure the MFA settings for users who connect from the Boston office. The solution must meet the authentication requirements and the access requirements.
What should you configure?
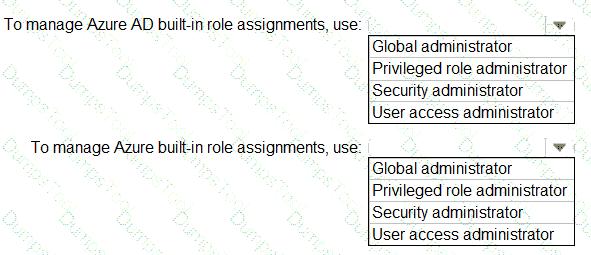
You need to identify which roles to use for managing role assignments. The solution must meet the delegation requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
You need to create the LWGroup1 group to meet the management requirements.
How should you complete the dynamic membership rule? To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You many need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You have a Microsoft Entra tenant.
You need to implement smart lockout with a lockout threshold of 10 failed sign-ins. What should you configure in the Microsoft Entra admin center?
You need to implement password restrictions to meet the authentication requirements.
You install the Azure AD password Protection DC agent on DC1.
What should you do next? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to track application access assignments by using Identity Governance. The solution must meet the delegation requirements.
What should you do first?
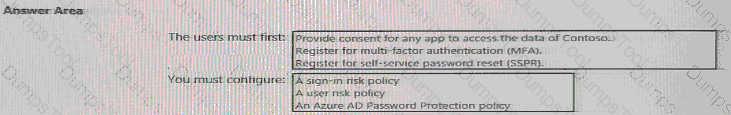
You need to meet the authentication requirements for leaked credentials.
What should you do?
You need to configure the detection of multi-staged attacks to meet the monitoring requirements.
What should you do?
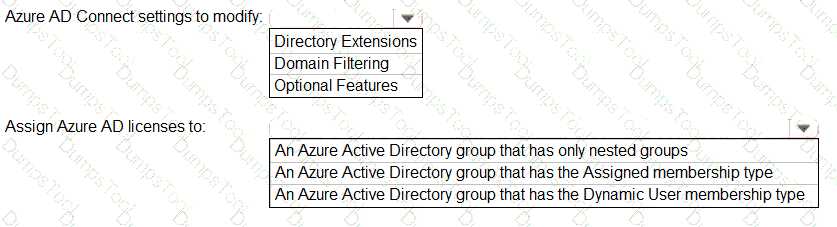
You need to configure the assignment of Azure AD licenses to the Litware users. The solution must meet the licensing requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
You need to implement the planned changes and technical requirements for the marketing department.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
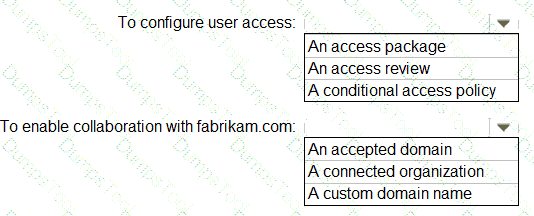
You need to meet the technical requirements for the probability that user identifies were compromised.
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to allocate licenses to the new users from A. Datum. The solution must meet thetechnical requirements.
Which type of object should you create?
You need to meet the technical requirements for the probability that user identities were compromised.
What should the users do first, and what should you configure? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.

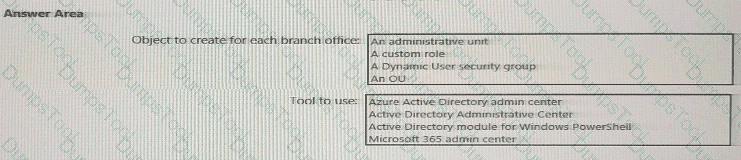
You need to meet the technical requirements for license management by the helpdesk administrators.
What should you create first, and which tool should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Task 1
You need to deploy multi factor authentication (MFA). The solution must meet the following requirements:
• Require MFA registration only for members of the Sg-Finance group.
• Exclude Debra Berger from having to register for MFA.
• Implement the solution without using a Conditional Access policy.
Task 2
You need to implement a process to review guest users who have access to the Salesforce app. The review must meet the following requirements:
• The reviews must occur monthly.
• The manager of each guest user must review the access.
• If the reviews are NOT completed within five days, access must be removed.
• If the guest user does not have a manager, Megan Bowen must review the access.