You are planning the data share migration to support the on-premises migration plan.
What should you use to perform the migration?
You are planning the deployment of Microsoft Sentinel.
Which type of Microsoft Sentinel data connector should you use to meet the security requirements?
You are planning the migration of Archive1 to support the on-premises migration plan.
What is the minimum number of IP addresses required for the node and cluster roles on Cluster3?
You are planning the www.fabrikam.com website migration to support the Azure migration plan.
How should you configure WebApp1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

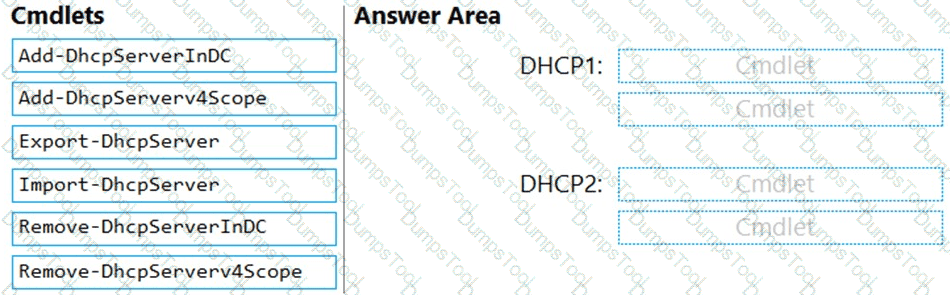
You are planning the DHCP1 migration to support the DHCP migration plan.
Which two PowerShell cmdlets should you run on DHCP1, and which two PowerShell cmdlets should you run on DHCP2? To answer, drag the appropriate cmdlets to the correct servers. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Your network contains an on-premises Active Directory Domain Services (AD DS) domain. The domain contains two virtual machines named VM1 and VM2 that run Windows Server.
You plan to implement a failover cluster named Cluster1 that will use VM1 and VM2 as nodes.
You need to ensure that Cluster1 can use floating IP addresses.
Which two components should you deploy? Each correct answer presents part-of the solution.
NOTE: Each correct selection is worth one point.
You have two servers named Host1 and Host2 that run Windows Server 2022 and are members of a workgroup named Contoso. Both servers have the Hyper-V server role installed and are identical in hardware and configuration.
Host1 contains three virtual machines. Each server is located in a separate site that connect by using a high-speed WAN link.
You need to replicate the virtual machines from Host1 to Host2 for a disaster recovery solution.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
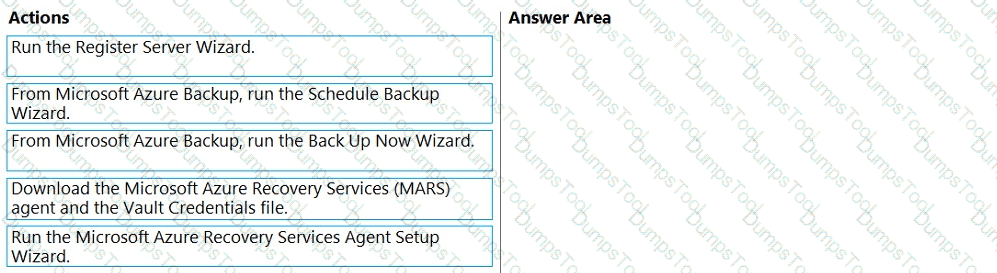
You have a server that runs Windows Server.
You plan to back up the server to an Azure Recovery Services vault once per week starting on the next Saturday.
You need to schedule the weekly backup and perform the initial backup as soon as possible.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer are and arrange them in the correct order.
Your network contains an Active Directory Domain Services (AD DS) domain that contains the servers shown in the following table.
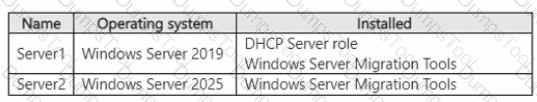
Server1 and Server2 are authorized as DHCP servers in the domain. You need to migrate the DHCP Server role from Server1 to Server2. Which five actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Your network contains an Active Director/ Domain Services {AD DS) domain named contoso.com. The domain contains two sites named Site1 and Site2 and servers that run Windows Server and are configured as shown in the following table.
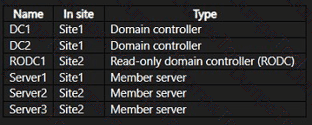
The domain contains a group named Group1 that contains Server3.
RODC1 has the Password Replication Policy shown in the following exhibit.
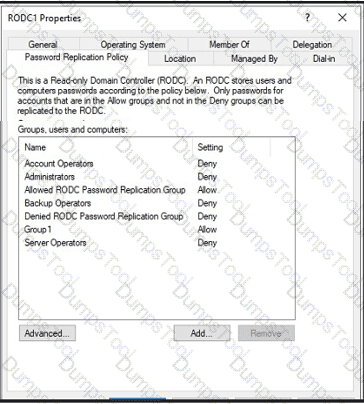
You have a server that runs Windows Server and hosts an app named Appl.
You need to prevent App1 from accessing external SMTP servers. The solution must meet the following requirements:
• Minimize the impact on AppVs access to external HTTP servers.
• Minimize the impact on other apps on (he server.
• Minimize administrative effort
What should you implement in Windows Defender Firewall?
You have 200 Azure virtual machines.
You create a recovery plan in Azure Site Recovery to fail over all the virtual machines to an Azure region. The plan has three manual actions.
You need to replace one of the manual actions with an automated process.
What should you use?
You have a server that runs Windows Server 2025 Standard and has the Hyper-V role installed. You need to upgrade the server to Windows Server 2025 Datacenter. The solution must minimize downtime. What should you run?
Your network contains an on-premises Active Directory Domain Services (AD DS) domain.
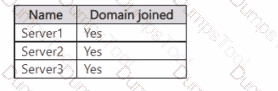
The domain contains the servers shown in the following table.
Server1 has the connection security rule as shown in the Server1 exhibit. (Click the Server1 tab.)
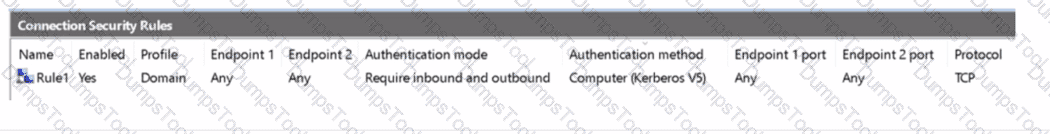
Server2 has the connection security rule as shown in the Server2 exhibit. (Click the Server2 tab.)
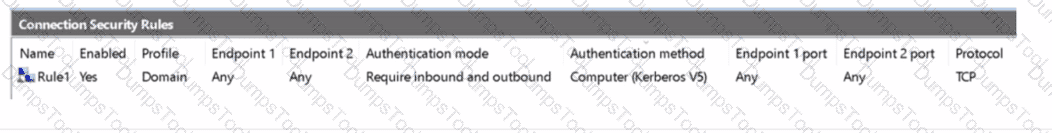
Server1 has the inbound firewall rules as shown in the Server1 inbound rules exhibit. (Click the Server1 inbound rules tab.)
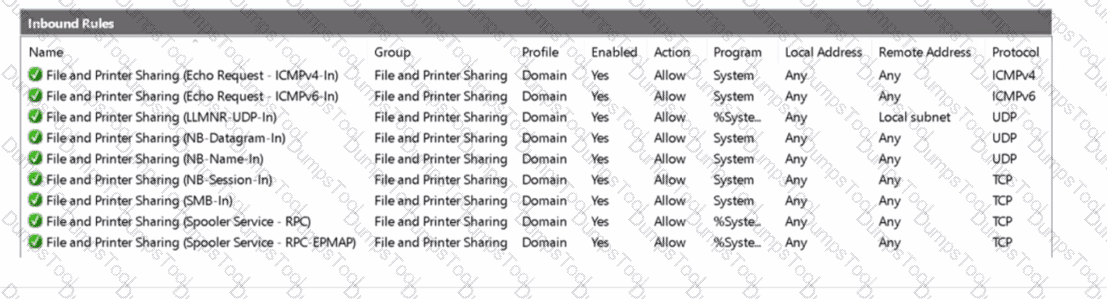
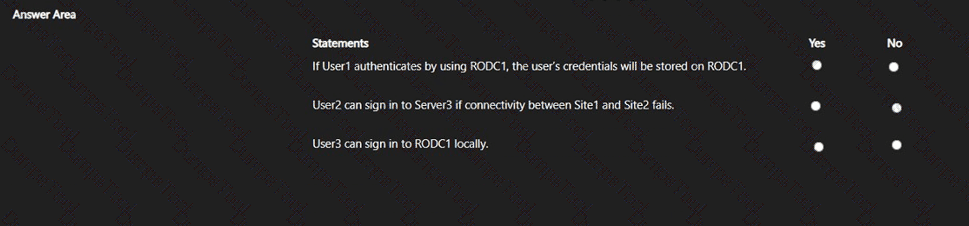
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You have a server named Server1 that runs Windows Server and contains two volumes named C and D.
You connect a disk to Server 1 that is encrypted by using BitLocker and contains a volume named E.
You need to ensure that after a restart, the data on volume E can be accessed without providing a password or a recovery key.
Which three actions should you perform on Server1 in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You have an Azure virtual machine named VM1 that runs Windows Server.
You plan to deploy a new line-of-business (LOB) application to VM1.
You need to ensure that the application can create child processes.
What should you configure on VM1?
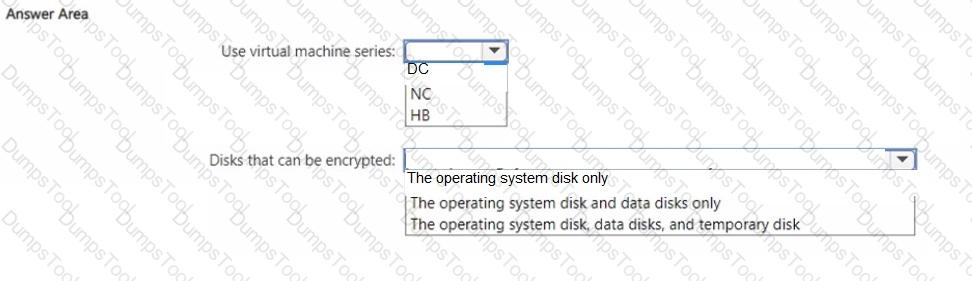
You plan to deploy an Azure confidential virtual machine named VM1. You need to ensure that you can implement confidential disk encryption for VM1. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
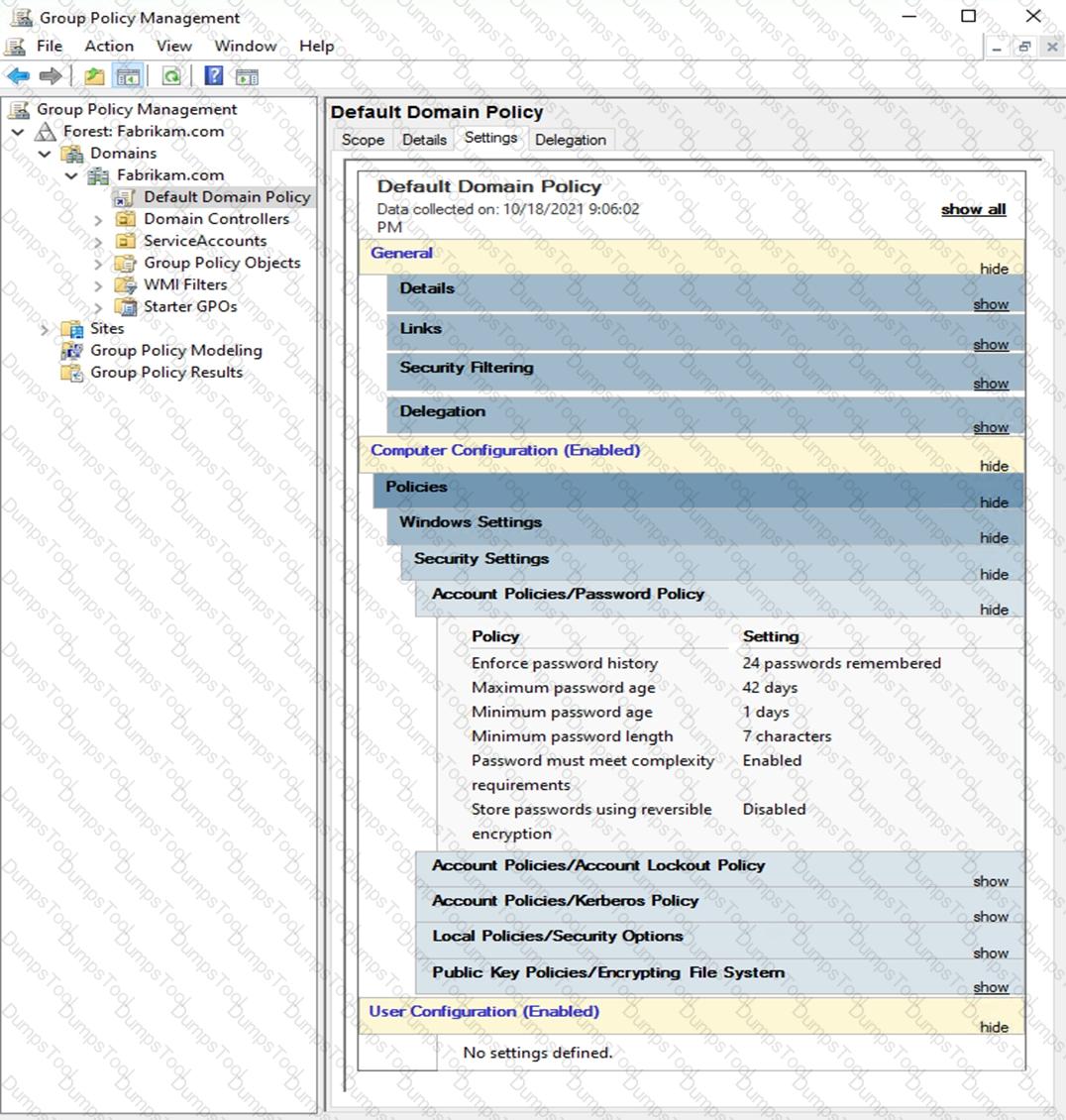
The Default Domain Policy Group Policy Object (GPO) is shown in the GPO exhibit. (Click the GPO tab.)
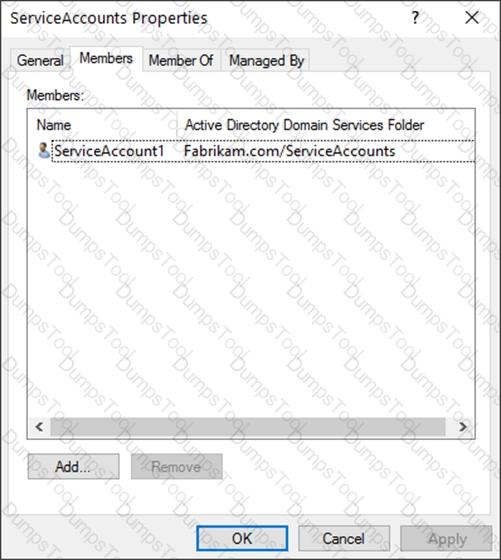
The members of a group named Service Accounts are shown in the Group exhibit. (Click the Group tab.)
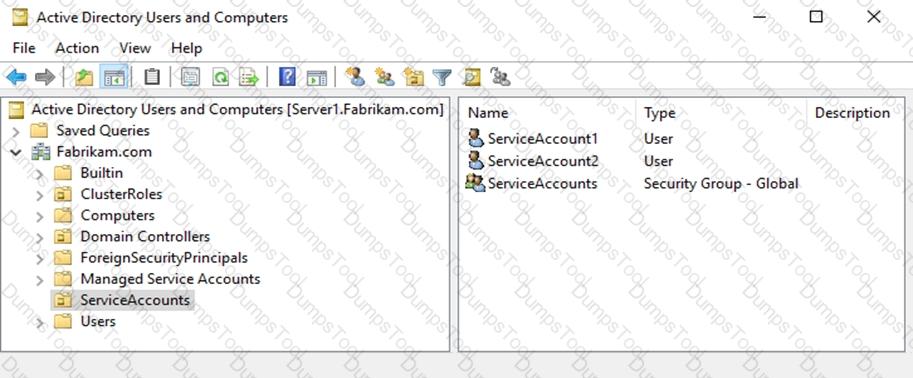
An organizational unit (OU) named ServiceAccounts is shown in the OU exhibit. (Click the OU tab.)
You create a Password Settings Object (PSO) as shown in the PSO exhibit. (Click the PSO tab.)
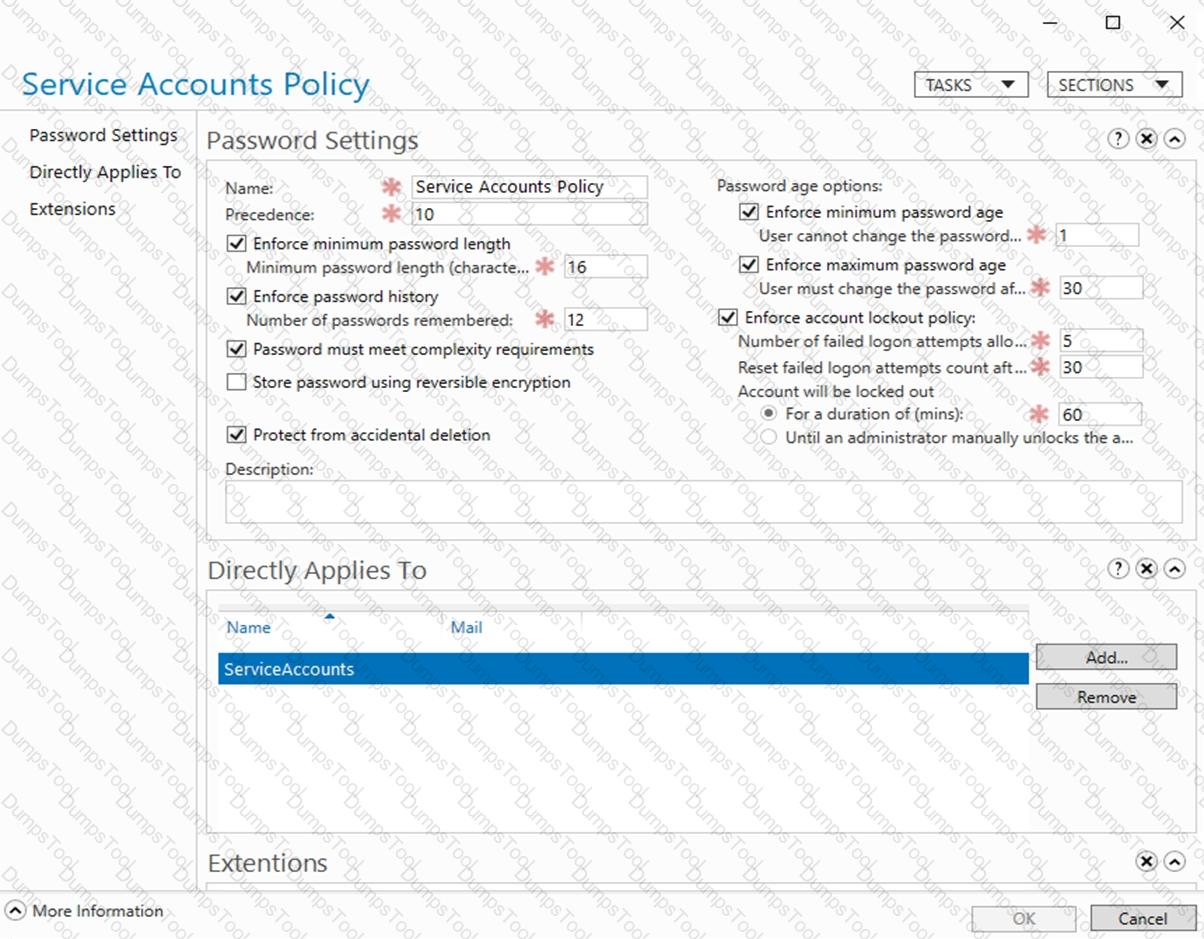
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You are evaluating the technical requirements tor Cluster2.
What is the minimum number of Azure Site Recovery Providers that you should install?
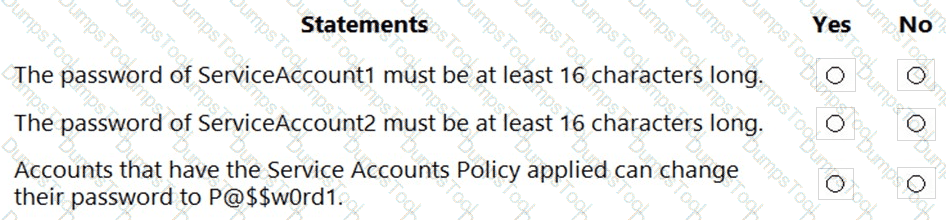
With which servers can Server1 and Server3 communicate? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Which domain controller should be online to meet the technical requirements for DC4?
You need to back up Server 4 to meet the technical requirements.
What should you do first?
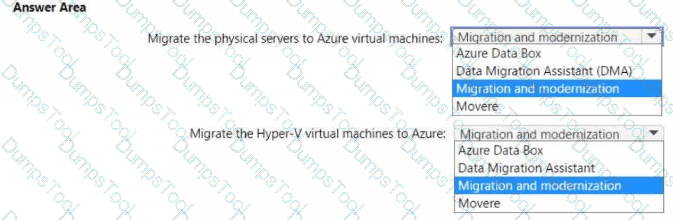
Your on-premises datacenter contains physical servers and Hyper-V virtual machines.
You have an Azure subscription.
You plan to use Azure Migrate to perform the following tasks:
• Migrate the physical servers to Azure virtual machines.
• Migrate the Hyper-V virtual machines to Azure.
What should you use for each task? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for Cluster3.
What should you include in the solution?
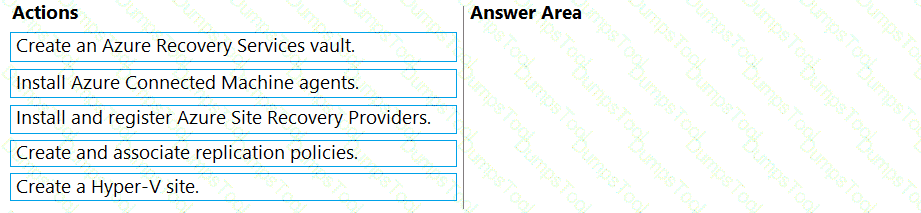
You need to meet the technical requirements for Cluster2.
Which four actions should you perform in sequence before you can enable replication? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
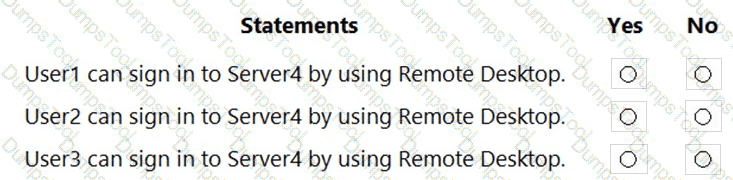
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for User1.
To which group in contoso.com should you add User1?
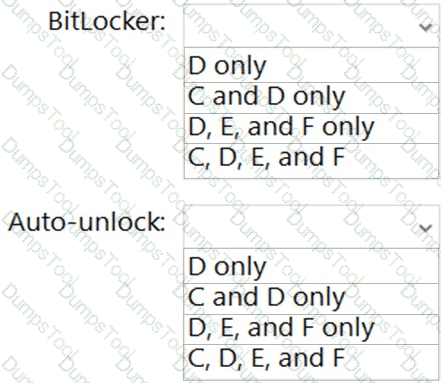
You need to configure BitLocker on Server4.
On which volumes can you turn on BitLocker, and on which volumes can you turn on auto-unlock? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
What is the effective minimum password length for User1 and Admin1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

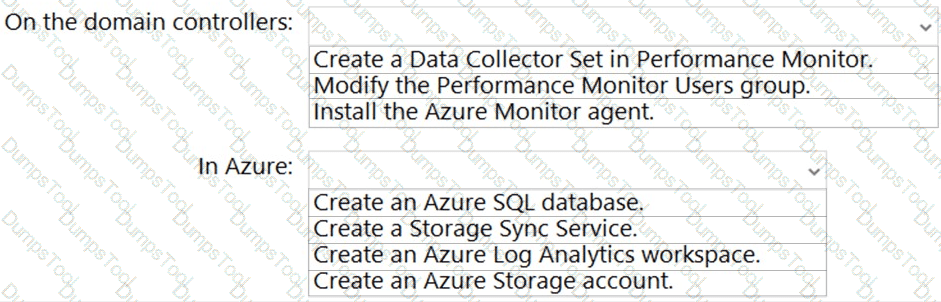
You need to implement alerts for the domain controllers. The solution must meet the technical requirements.
What should you do on the domain controllers, and what should you create on Azure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.