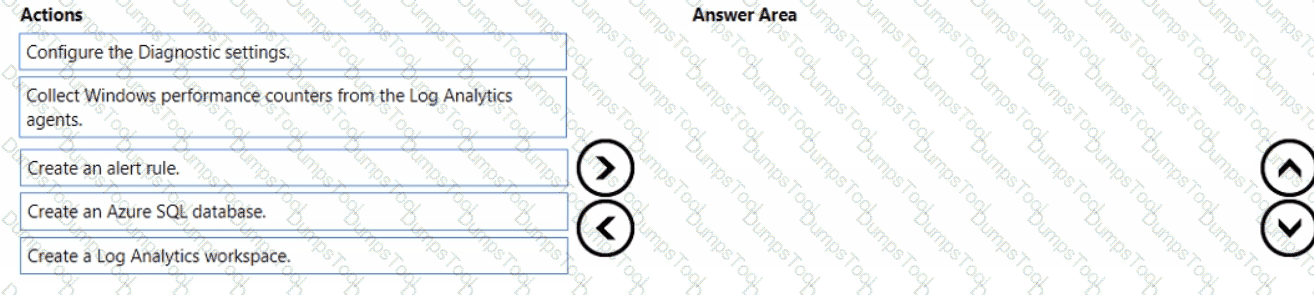
You need to configure the alerts for VM1 and VM2 to meet the technical requirements.
Which three actions should you perform in sequence? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
You need to ensure that you can grant Group4 Azure RBAC read-only permissions to all the A2ure file shares. What should you do?
You implement the planned changes for NSG1 and NSG2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You need to recommend a solution for App1. The solution must meet the technical requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to add VM1 and VM2 to the backend poo! of LB1. What should you do first?
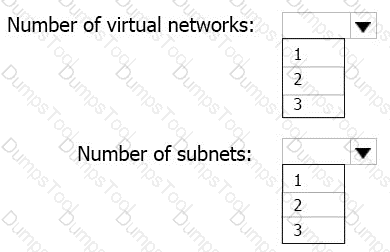
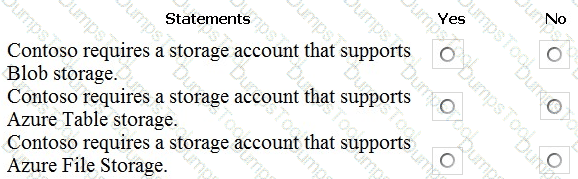
You need to identify the storage requirements for Contoso.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You need to resolve the licensing issue before you attempt to assign the license again.
What should you do?
You need to prepare the environment to ensure that the web administrators can deploy the web apps as quickly as possible.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You need to prepare the environment to meet the authentication requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE Each correct selection is worth one point.
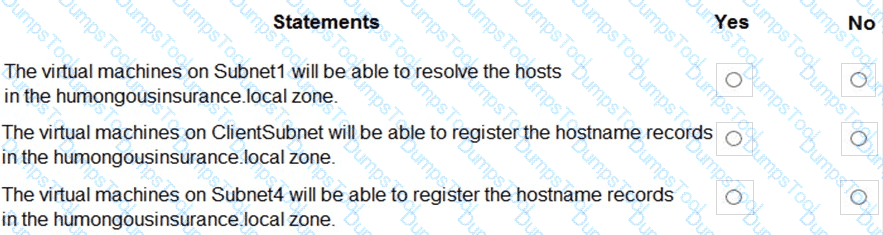
You are evaluating the name resolution for the virtual machines after the planned implementation of the Azure networking infrastructure.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You need to prepare the environment to meet the authentication requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to define a custom domain name for Azure AD to support the planned infrastructure.
Which domain name should you use?
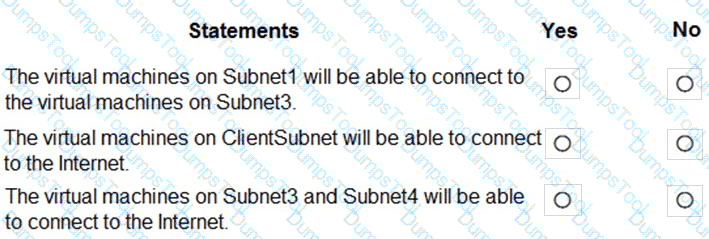
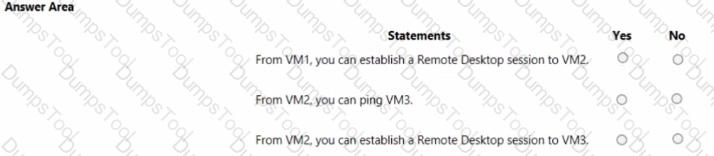
You are evaluating the connectivity between the virtual machines after the planned implementation of the Azure networking infrastructure.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You need to define a custom domain name for Azure AD to support the planned infrastructure.
Which domain name should you use?
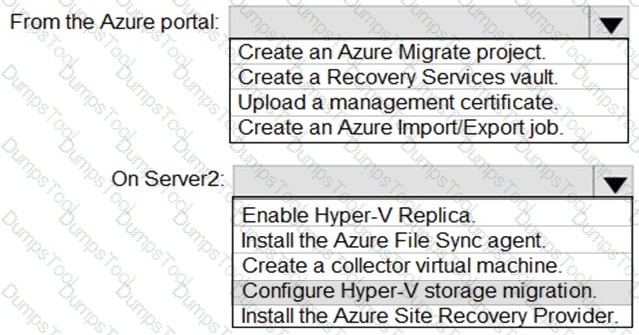
You need to the appropriate sizes for the Azure virtual for Server2.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to automate the configuration for the finance department users. The solution must meet the technical requirements.
What should you include in the recommended?
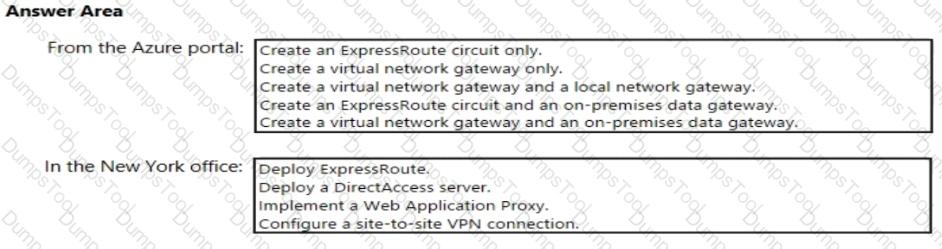
You need to meet the connection requirements for the New York office.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to ensure that VM1 can communicate with VM4. The solution must minimize administrative effort.
What should you do?
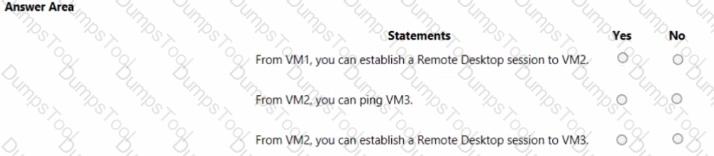
You implement the planned changes for NSG1 and NSG2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirement for VM4.
What should you create and configure?
You discover that VM3 does NOT meet the technical requirements.
You need to verify whether the issue relates to the NSGs.
What should you use?
You have an Azure Active Directory (Azure AD) tenant.
You plan to delete multiple users by using Bulk delete in the Azure Active Directory admin center.
You need to create and upload a file for the bulk delete.
Which user attributes should you include in the file?
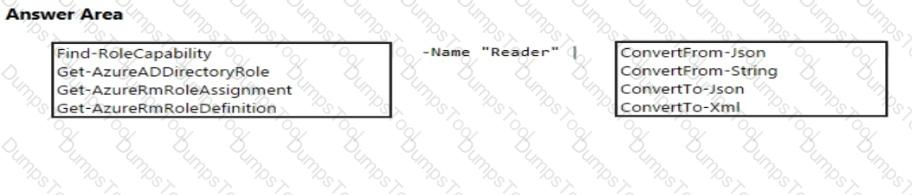
You need to implement Role1.
Which command should you run before you create Role1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a storage account.
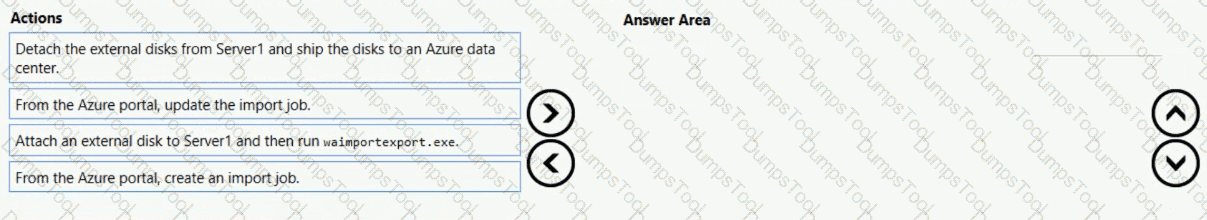
You have an on-premises server named Server1 that runs Window Server 2016. Server1 has 2 TB of data.
You need to transfer the data to the storage account by using the Azure Import/Export service.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
You have an Azure subscription that contains The storage accounts shown in the following table.
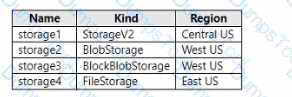
You deploy a web app named Appl to the West US Azure region.
You need to back up Appl. The solution must minimize costs.
Which storage account should you use as the target for the backup?
You have an Azure App Services web app named App1.
You plan to deploy App1 by using Web Deploy.
You need to ensure that the developers of App1 can use their Azure Active Directory (Azure AD) credentials to deploy content to App1. The solution must use the principle of least privilege.
What should you do?
You have an Azure subscription that contains a resource group named RG1.
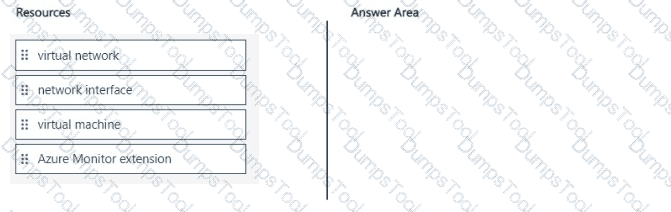
You plan to create an Azure Resource Manager (ARM) template to deploy a new virtual machine named VM1. VM1 must support the capture of performance data.
You need to specify resource dependencies for the ARM template.
In which order should you deploy the resources? To answer, move all resources from the list of resources to the answer area and arrange them in the correct order.
You have an Azure subscription that contains a storage account named storage1. The storage1 account contains a blob that stores images.
Client access to storage1 is granted by using a shared access signature (SAS).
You need to ensure that users receive a warning message when they generate a SAS that exceeds a seven-day time period.
What should you do for storage1?
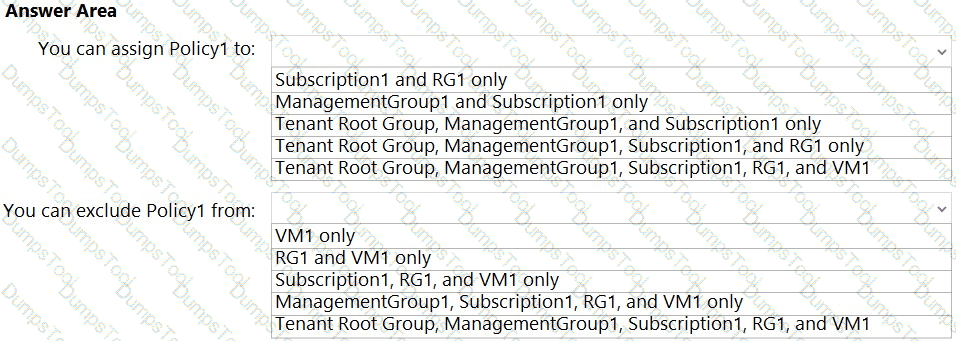
You have an Azure subscription that contains the hierarchy shown in the following exhibit.

You create an Azure Policy definition named Policy1.
To which Azure resources can you assign Policy and which Azure resources can you specify as exclusions from Policy1? To answer, select the appropriate options in the answer
NOTE Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You assign a built-in policy definition to the subscription.
Does this meet the goal?
You have an Azure subscription that contains 20 virtual machines, a network security group (NSG) named NSG1, and two virtual networks named VNET1 and VNET2 that are peered.
You plan to deploy an Azure Bastion Basic SKU host named Bastion1 to VNET1.
You need to configure NSG1 to allow inbound access from the internet to Bastion1.
Which port should you configure for the inbound security rule?
You have two Azure virtual networks named VNet1 and VNet2. VNet1 contains an Azure virtual machine named VM1. VNet2 contains an Azure virtual machine named VM2.
VM1 hosts a frontend application that connects to VM2 to retrieve data.
Users report that the frontend application is slower than usual.
You need to view the average round-trip time (RTT) of the packets from VM1 to VM2.
Which Azure Network Watcher feature should you use?
You have an Azure subscription that contains the Azure virtual machines shown in the following table.
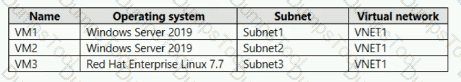
You configure the network interfaces of the virtual machines to use the settings shown in the following table
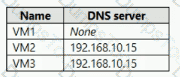
From the settings of VNET1, you configure the DNS servers shown in the following exhibit.
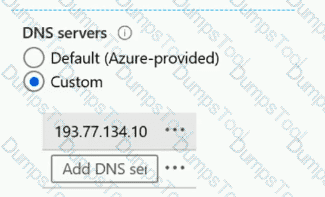
The virtual machines can successfully connect to the DNS server that has an IP address of 192.168.10.15 and the DNS server that has an IP address of 193.77.134.10.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.

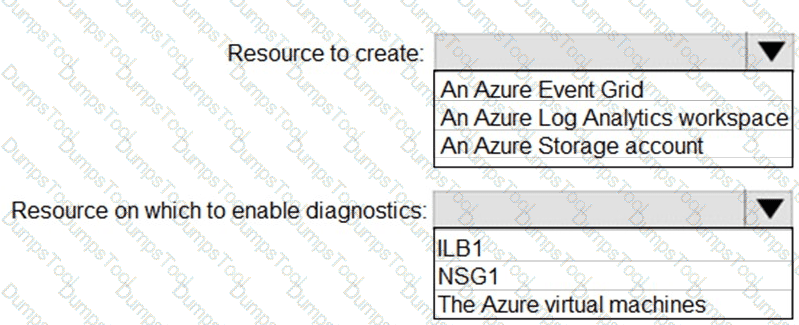
You have an Azure virtual network named VNet1 that connects to your on-premises network by using a site-to-site VPN. VMet1 contains one subnet named Subnet1.
Subnet1 is associated to a network security group (NSG) named NSG1. Subnet1 contains a basic internal load balancer named ILB1. ILB1 has three Azure virtual machines in the backend pool.
You need to collect data about the IP addresses that connects to ILB1. You must be able to run interactive queries from the Azure portal against the collected data.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement the planned changes for DCR1. Which type of query should you use?
You implement the planned changes for cont2.
What is the maximum number of additional access policies you can create for cont2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure virtual machine named VM1. VM1 was deployed by using a custom Azure Resource Manager template named ARM1.json.
You receive a notification that VM1 will be affected by maintenance.
You need to move VM1 to a different host immediately.
Solution: From the Overview blade, you move the virtual machine to a different resource group.
Does this meet the goal?
You need to configure encryption for the virtual machines. The solution must meet the technical requirements.
Which virtual machines can you encrypt?
You need to configure WebApp1 to meet the technical requirements.
Which certificate can you use from Vault1?
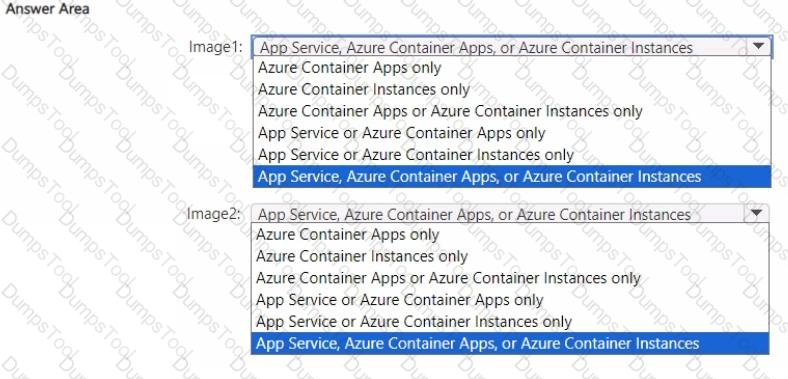
You need to implement the planned changes for the new containers.
Which Azure services can you use for each image? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
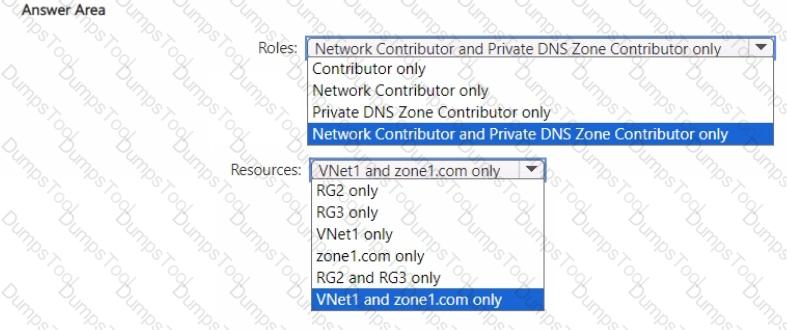
You need to implement the planned changes for User1.
Which roles should you assign to User1, and for which resources? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement the planned changes for the storage account content. Which containers and file shares can you use to organize the content?
You implement the planned changes for Scope1.
You need to ensure that Scope1 meets the technical requirements.
What can you encrypt by using Scope1?
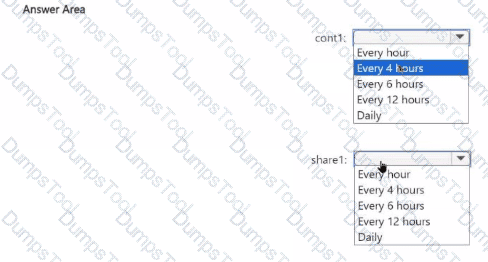
You need to configure Azure Backup to meet the technical requirements for cont1 and share1.
To what should you set the backup frequency for each resource? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.