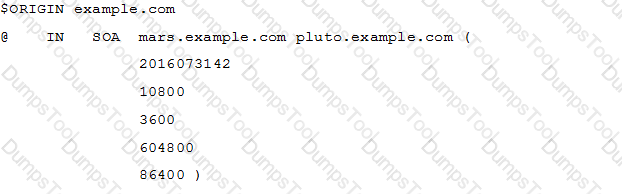
According to the configuration below, what is the full e-mail address of the administrator for this domain?
A company is transitioning to a new DNS domain name and wants to accept e-mail for both domains for all of its users on a Postfix server.
Which configuration option should be updated to accomplish this?
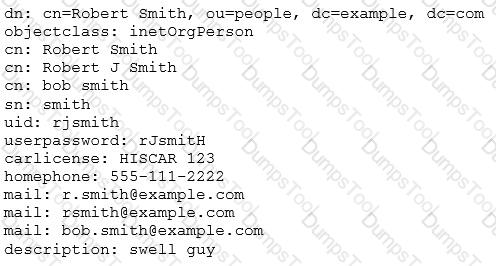
According to this LDIF excerpt, which organizational unit is Robert Smith part of? (Specify only the organizational unit.)
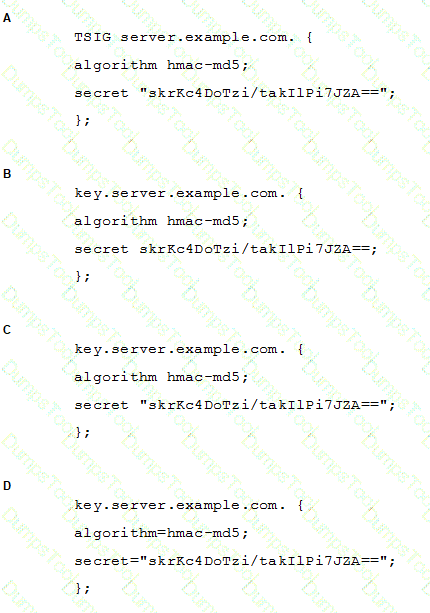
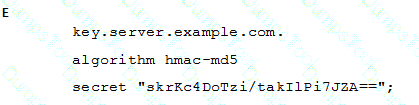
A BIND server should be upgraded to use TSIG. Which configuration parameters should be added if the server should use the algorithm hmac-md5 and the key skrKc4DoTzi/takIlPi7JZA==?
In order to protect a directory on an Apache HTTPD web server with a password, this configuration was added to an .htaccess file in the respective directory:
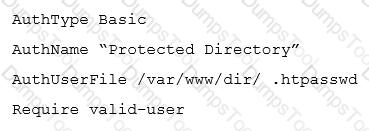
Furthermore, a file /var/www/dir/ .htpasswd was created with the following content:
usera:S3cr3t
Given that all these files were correctly processed by the web server processes, which of the following statements is true about requests to the directory?
Which Postfix command can be used to rebuild all of the alias database files with a single invocation and without the need for any command line arguments?
Which option within a Nginx server configuration section defines the file system path from which the content of the server is retrieved?
With Nginx, which of the following directives is used to proxy requests to a FastCGI application?
Which OpenLDAP client command can be used to change the password for an LDAP entry? (Specify ONLY the command without any path or parameters.)
Which of the following actions are available in Sieve core filters? (Choose three.)
When using mod_authz_core, which of the following strings can be used as an argument to Require in an Apache HTTPD configuration file to specify the authentication provider? (Choose three.)
How must Samba be configured such that it can check CIFS passwords against those found in /etc/passwd and /etc/shadow?
Which of the following lines is valid in a configuration file in /etc/pam.d/?
Which directive in a Nginx server configuration block defines the TCP ports on which the virtual host will be available, and which protocols it will use? (Specify ONLY the option name without any values.)
The Samba configuration file contains the following lines:
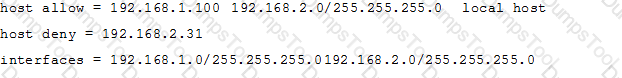
A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server.
Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?
Which of the following Samba services handles the membership of a file server in an Active Directory domain?
Which of the following types of IPv6 address assignments does DHCPv6 support? (Choose three.)
Which netfilter table contains built-in chains called INPUT, OUTPUT and FORWARD?
Which of the following sshd configuration should be set to no in order to fully disable password based logins? (Choose two.)
Which of the following Samba configuration parameters is functionally identical to the parameter read only=yes?
Which command is used to configure which file systems a NFS server makes available to clients?
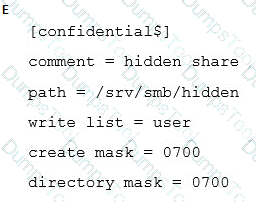
A user requests a “hidden” Samba share, named confidential, similar to the Windows Administration Share. How can this be configured?